Cybersecurity refers to the practice and techniques used to protect systems, networks, and programs from digital attacks, unauthorized access, or damage. It encompasses a broad range of practices designed to safeguard data integrity, confidentiality, and availability across various digital platforms.
The goal of cybersecurity is to protect sensitive information from cyber threats such as hacking, phishing, malware, and ransomware, ensuring the safety and privacy of data in an increasingly connected world.
In this guide, we’ll explore key aspects of cybersecurity and how tech leaders can help their teams overcome common security challenges.
An Introduction to Cybersecurity
Cybersecurity involves implementing defensive measures like firewalls, anti-virus software, and intrusion detection systems, as well as employing strategies for risk management, data recovery, and user education.
It is already big business, and it’s growing rapidly. According to a survey conducted by KPMG, 18% of the CEOs questioned believe cybercrime will be the biggest threat to their organization’s growth in 2025.
While implementing the best security measures doesn't provide a guarantee against these incidents, adopting certain precautions can significantly reduce their likelihood. Selecting the best cybersecurity provider to protect your business is also paramount.
Common Cybersecurity Threats
Cyber threats come in many forms. Risks include the potential for malware to wipe out your entire system, an intruder accessing and modifying your files, your computer being used as a tool for launching attacks on others, or someone stealing your credit card details to make unauthorized transactions. Technical solutions such as cybersecurity software, firewalls, and access control systems still have a role to play. But it’s also essential to consider the human element. A pragmatic approach to cybersecurity covers both technical and human issues.

- Malware, a contraction of "malicious software," refers to any software or computer program deliberately designed to harm a computer system or its users. It's a common element in most contemporary cyberattacks. Malware is crafted and deployed by hackers and cybercriminals to illicitly access computer systems and sensitive information, remotely control computer systems, disrupt or damage them, or hold data and systems for ransom...
- Ransomware is malware that locks a victim's data or device, threatening to keep it inaccessible—or even worse—unless a ransom is paid. The IBM Security X-Force Threat Intelligence Index 2023 reports that ransomware attacks constituted 17% of all cyberattacks in 2022. Modern ransomware is more severe than its early versions. Initially, ransomware demanded a single ransom for decryption keys. However, current attacks often involve double extortion, demanding additional ransom to prevent the release or publication of the victim's data. Some even escalate to triple extortion, threatening a distributed denial of service attack (DDoS, explained below) if the ransom is not paid.
- Phishing involves deceptive emails, texts, or calls that lure users into downloading malware, divulging sensitive information, or sending money erroneously. Common are bulk phishing scams—widespread fraudulent messages from seemingly reputable brands, prompting recipients to update passwords or credit card details. More advanced phishing, like spear phishing and business email compromise (BEC), targets specific individuals or groups for high-value data or significant financial gains. Phishing is a form of social engineering where psychological manipulation is used to trick people into making harmful decisions.
- Insider Threats stem from authorized users (employees, contractors, business partners) who misuse their access intentionally or inadvertently or whose accounts are compromised by cybercriminals. Insider threats are more challenging to detect than external ones due to their appearance as legitimate activities and their invisibility to traditional security measures like antivirus software and firewalls.
- Distributed Denial of Service (DDoS) Attacks aim to shut down servers, websites, or networks by overwhelming them with traffic, typically from a botnet—a group of infected systems controlled remotely by cybercriminals. The frequency of DDoS attacks has surged during the COVID-19 pandemic. Attackers are increasingly combining DDoS with ransomware attacks or using the threat of a DDoS attack to extort ransom payments. DDoS protection software helps build digital immunity.
Why Cybersecurity Matters for SaaS
In recent years, cyberattacks have become more frequent and more costly. According to IBM, the average cost of a data breach in 2025 was $4.45 million, an increase of around 15% over the last three years. Ransomware attacks are even more expensive, with average costs of over $5 million, not including any ransom the victim chooses to pay.
As a tech leader, it’s crucial to consider your SaaS infrastructure when implementing cybersecurity policies. Cybercriminals often target SaaS platforms because of the potential for high returns. For example, Team TNT used malware to access some misconfigured Kubernetes clusters and compromised 50,000 IPs.
For your clients, the appeal of SaaS is that it frees them from worrying about maintenance and upgrades. A conscientious approach to cybersecurity is essential to live up to that promise.
Core Components of Cybersecurity
A good cybersecurity framework must cover five core areas. Familiarize yourself with these components and aim to cover them all as part of a holistic security approach.
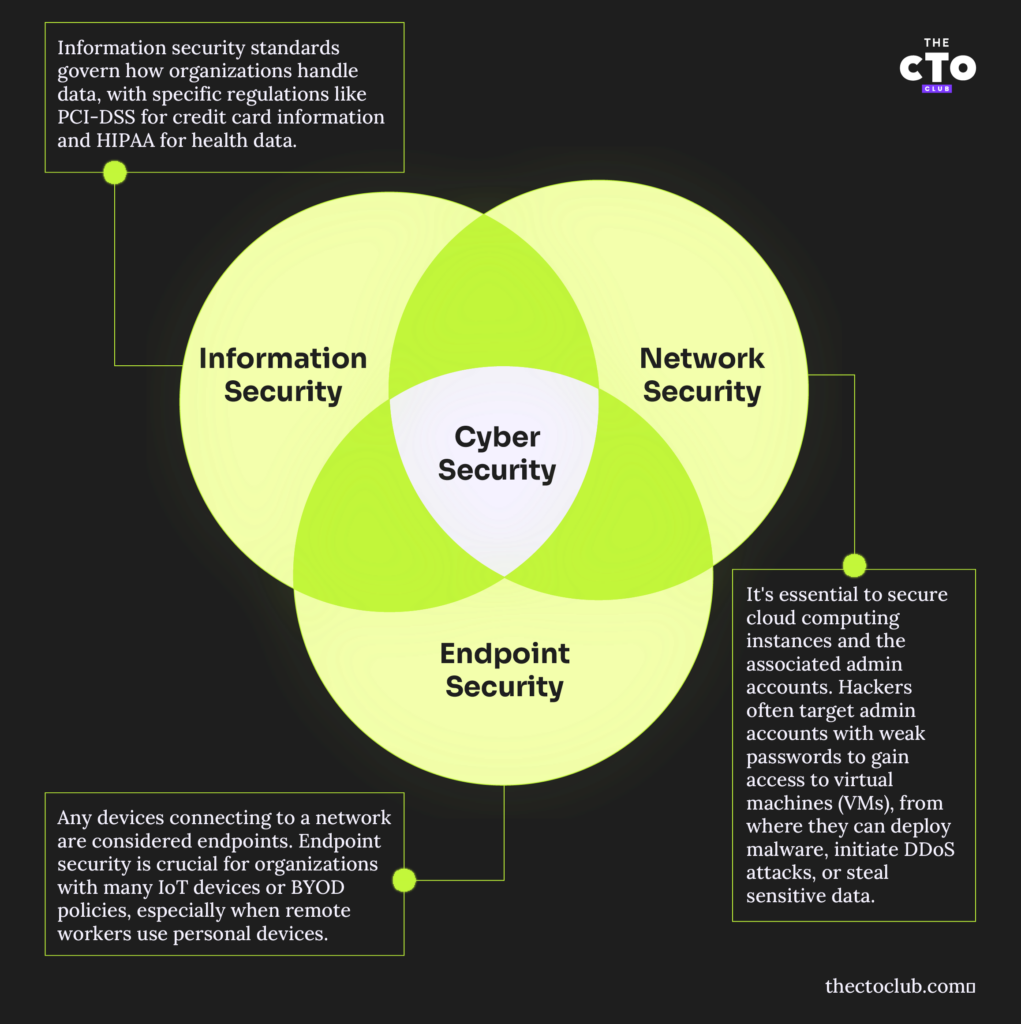
Network Security
Network security relates to your physical network and any devices that connect to it. This includes mobile devices, Internet of Things, servers, and laptops. Securing wireless networks, using VPNs or other forms of encrypted communication, and configuring firewalls are all fundamental parts of a network security policy.
Information Security
The way your organization collects, stores, and transmits data is covered by information security standards, for example, PCI-DSS for credit card information or HIPAA for health-related data. It’s likely your organization has already given a lot of consideration to the relevant standards. A cybersecurity review may highlight any deficiencies in how the data is stored and transferred.
Endpoint Security
Any devices connecting to a network are considered endpoints. For organizations with a lot of IoT devices or have BYOD policies, endpoint security is a particularly pressing concern. Consider the example of an organization that allows remote workers to use their own laptops and smartphones. If an employee’s laptop becomes infected with ransomware, that ransomware may spread to network drives the employee has access to, causing significant disruption.
Cloud Security
Securing your cloud computing instances and the administrative accounts for the cloud platform is crucial. Hackers have been known to look for admin accounts with weak passwords and use those accounts to grant themselves access to the VMs running on them so they can later deploy malicious software, launch DDOS attacks, or look around for sensitive data to steal.
Zero Trust Security
Zero Trust Security is a cybersecurity framework that eliminates implicit trust and requires continuous verification of all users, devices, and applications. It enforces strict identity authentication, least privilege access, and real-time monitoring to minimize security risks and prevent lateral movement in case of a breach.
Key principles include multi-factor authentication (MFA), micro-segmentation, and automated risk assessments to detect and mitigate threats. As organizations shift to cloud and hybrid environments, Zero Trust enhances data security, regulatory compliance, and overall visibility across IT systems.
Application Security
Application security software covers zero-day vulnerabilities, poorly configured applications, or unpatched operating systems. Some common issues include:
- Improper access management (e.g., giving users more privileges than they need)
- Failure to take advantage of multi-factor authentication
- Failure to enforce strong passwords or policies to block an account after multiple failed/ unauthorized access attempts
- Taking too long to alter/revoke privileges for departing employees
If you’re integrating new applications or third-party cloud services into your workflows, review your policies to confirm you’re still covering each component.
Key Cybersecurity Technologies
- Firewalls: Act as a barrier between trusted internal networks and untrusted external networks, such as the Internet.
- Antivirus and Anti-malware Software: Detects, prevents, and removes malicious software like viruses, worms, and ransomware.
- Intrusion Detection and Prevention Systems (IDPS): Monitor network traffic for suspicious activity and known threats, alerting security personnel to potential breaches.
- Encryption: Protects data by converting it into unreadable code during transmission or storage, ensuring only authorized parties can access it.
- Virtual Private Networks (VPNs): Create a secure connection over the internet, enhancing privacy and security, especially for remote work.
- Multi-Factor Authentication (MFA): Requires multiple forms of verification before granting access, significantly reducing the risk of unauthorized access.
- Security Information and Event Management (SIEM): Provides real-time analysis of security alerts generated by applications and network hardware.
- Data Loss Prevention (DLP): Technologies that prevent sensitive data from leaving the network without authorization.
- Cloud Security Tools: Protect data and applications hosted in cloud environments, including access controls and threat intelligence.
- Endpoint Protection: Secures endpoints or entry points of end-user devices like desktops, laptops, and mobile devices from exploitation by malicious actors.
The Role of a Tech Leader in Cybersecurity
In your career as a cybersecurity leader, it’s your responsibility to ensure your teams understand the importance of cybersecurity, why your policies are the way they are, and that those policies align with business objectives.
Aligning Cybersecurity With Business Goals
Stakeholders often consider cybersecurity an inconvenience or something to pay lip service to. It’s easier to get those managers on board when you focus on the outcomes of your policy. For example, preventing attacks improves service uptime and increases productivity.
Efficient Resource Management for Security
Regular reviews of accounts and resources on a network can increase the speed with which breaches are detected. Removing unused applications or shutting down systems no longer in use reduces the number of attack vectors open to malicious actors.
Communicating Security Protocols and Risks
Awareness training is an invaluable tool for educating employees at all levels on your cybersecurity strategy. Staff who are knowledgeable about security risk assessment tools and have training regarding phishing, trojans, viruses, and ransomware better understand how to protect themselves against such threats and are less likely to fall victim to cybercriminals.
Emerging Trends in Cybersecurity
Cyber security is constantly evolving. To ensure your SaaS platform remains resilient against emerging threats, stay current with these trends.
Artificial Intelligence & Security
AI has the potential to streamline many areas of cybersecurity. Full automation probably isn’t a good idea, especially given how “confidently incorrect” the current generation of machine learning models can be. However, for monitoring logs and alerts and assisting your existing team of cybersecurity professionals, AI could be invaluable.
Blockchain's Role in Cybersecurity
Recording data to a decentralized, append-only ledger can be beneficial if you need the data to be immutable. However, many challenges are associated with distributed blockchains. For one, using a distributed, immutable ledger on a public blockchain for sensitive data may not be desirable. In addition, one mistake with private keys could present profound business continuity or security risks. Private, permissioned blockchains may address some of these issues, making them a potential compromise.
The Rise of Quantum Computing
Quantum computing could make many popular encryption algorithms obsolete overnight. It’s perhaps the most significant threat faced by the entire IT industry. NIST announced four quantum-resistant cryptographic algorithms in 2022, and others are being worked on. Start future-proofing your platforms today to avoid a crisis that could be closer than you think.
Extended Detection and Response (XDR)
Extended Detection and Response (XDR) is gaining traction as cyber threats become more sophisticated. Traditional security tools like SIEM and EDR often struggle with fragmented data and high alert volumes, making it harder to detect and respond to attacks. XDR streamlines security by integrating multiple layers, automating threat correlation, and consolidating data across endpoints, networks, and cloud environments.
This approach enhances visibility, reduces blind spots, and provides deeper context into potential threats. By prioritizing risks and improving incident response, XDR helps cybersecurity teams detect, mitigate, and prevent security incidents more effectively.
Expert Tips for Overcoming Common Cybersecurity Challenges
Promoting solid security solutions isn’t always easy, but addressing these challenges head-on will make it easier to achieve the interdepartmental collaboration required to make your policies a success.
Preventing System Failures & Firefighting
A proactive approach to preventing cybersecurity threats is more effective than firefighting. For example, investing in a CDN to prevent denial of service attacks is easier than recovering from any reputational damage caused by an outage.
De-siloing Security Protocols
Complex networks often lead to silos and information blind spots. Always aim to break down those silos, pulling together as much information as you can to get a good overview of any potential threats.
Achieving Stakeholder Alignment on Security Priorities
Your stakeholders likely understand you’re handling sensitive information on your computer systems. Focus on the benefits and why you’re implementing various policies to achieve buy-in with your security measures. Make them as easy and frictionless to follow as possible.
Best Practices
Want to significantly enhance your organization's cybersecurity posture, reducing the risk of cyberattacks and data breaches? Act on the following:
- Regular Software Updates: Keep all software up to date, including operating systems and applications, to patch security vulnerabilities.
- Strong Password Policies: Implement complex passwords or use password manager software and change them regularly to prevent unauthorized access.
- Employee Training and Awareness: Educate staff about common cyber threats like phishing and social engineering attacks.
- Regular Backups: Regularly back up data and ensure it can be restored to prevent loss in case of a cyberattack.
- Incident Response Planning: Create a plan for responding to security breaches effectively.
- Network Segmentation: Divide the network into smaller parts to limit the spread of attacks and manage access controls more effectively.
- Least Privilege Access: Grant users only the access needed to perform their job functions.
- Continuous Monitoring: Monitor network traffic and logs to detect and respond to threats promptly.
- Secure Configuration: Ensure all systems and applications are configured securely to minimize vulnerabilities.
- Regular Security Audits: Conduct periodic audits to identify and rectify security gaps or weaknesses.
Secure Your Brand
As a SaaS tech leader, you’re responsible for data security for your business and, indirectly, for the organizations that depend on your services. The world of cybersecurity is constantly evolving, and there are far more threats today than simple phishing attacks and spyware. What advice would you give someone looking to create more robust safeguards around their cybersecurity plan?
Want to learn more about cybersecurity? Subscribe to our newsletter for updates on the latest news in cybersecurity and beyond.