10 Best Static Application Security Testing Tools Shortlist
Here's my pick of the 10 best software from the 24 tools reviewed.
Our one-on-one guidance will help you find the perfect fit.
Navigating the world of static application security testing, I've come to understand its indispensable nature in automating the identification of security vulnerabilities within lines of code. Such tools not only cover basics but delve into intricate cybersecurity areas, helping combat misconfigurations and offering comprehensive vulnerability management.
As a security expert, I've seen both on-premise solutions and plugins that work in tandem with dynamics application security testing to bolster defenses. Don't let your guard down; choose the right tool to strengthen your software's fortifications.
What Is a Static Application Security Testing Tool?
Static application security testing tools, often abbreviated as SAST, are specialized software tools designed to analyze source code, bytecode, or binary code of applications without executing them. Developers, security professionals, and organizations incorporate SAST into their software development lifecycle to preemptively address and mitigate security flaws, ensuring that their applications maintain a strong defensive posture against cyber threats.
It's more than just a tool – it's a crucial ally that helps development teams ensure secure code and address security issues during the code review stage, long before they escalate. By integrating these tools into your development cycle, you can shift left, diving deep with white-box testing to spot and fix vulnerabilities from buffer overflows to cross-site scripting, even in mobile applications.
Best Static Application Security Testing Tools Summary
| Tool | Best For | Trial Info | Price | ||
|---|---|---|---|---|---|
| 1 | Best for modern web app security | Free demo available | From $1000/user/year | Website | |
| 2 | Best for AI-powered vulnerability triage | Free plan available + free demo | From $350/month | Website | |
| 3 | Best for real-time threat detection | 15-day free trial + demo available | From $0.0001 | Website | |
| 4 | Best for integrated DevOps security | 30-day free trial + Free demo | From $19/user/month | Website | |
| 5 | Best for Java application testing | 14-day free trial | Pricing upon request | Website | |
| 6 | Best for open-source code insights | Free plan available | From $25/product/month | Website | |
| 7 | Best for in-depth Ada language analysis | Not available | Pricing upon request. | Website | |
| 8 | Best for unified security control | Not available | Pricing upon request. | Website | |
| 9 | Best for detecting sensitive data leaks | Not available | Pricing upon request. | Website | |
| 10 | Best for identifying anti-patterns | Not available | From $20/user/month (billed annually) | Website |
-

Docker
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.6 -

Pulumi
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.8 -

GitHub Actions
Visit Website
Best Static Application Security Testing Tools Reviews
HCL AppScan is a comprehensive software security solution that aids enterprises in identifying, fixing, and preventing vulnerabilities in their applications. As organizations grow, their need for scalable security solutions increases, positioning AppScan as a vital tool for large-scale businesses.
Why I Picked HCL AppScan: In comparing various security tools, I found that HCL AppScan offers robust features suitable for large enterprises. Its unique selling proposition lies in its ability to scale as the organization grows, ensuring security without impeding growth. I'm confident that it's 'best for scalable enterprise solutions' given its track record and capacity to handle expansive security demands.
Standout Features & Integrations:
HCL AppScan offers dynamic and static application security testing, ensuring that apps are safe at both the code and runtime levels. Additionally, its Interactive Application Security Testing (IAST) bridges the gap between static and dynamic testing.
For integrations, AppScan provides connections with CI/CD pipelines, thus promoting secure DevOps practices.
Pros and cons
Pros:
- Compatible with major web frameworks and platforms
- Offers real-time monitoring and detection
- Tailored solutions for current web app threats
Cons:
- Advanced features might be overwhelming for smaller teams
- Limited utility for non-web applications
- May require technical expertise for full utilization
New Product Updates from Mend.io
Multi-Organization Support, Microsoft Defender Integration, and Dashboard Enhancements
The latest Mend.io update introduces multi-organization support in the Mend for Jira Cloud plugin, integration with Microsoft Defender for Cloud, and enhancements to the Value Dashboard. For more details, visit Mend.io Release Notes.
Aikido Security is a platform that scans your source code to identify security vulnerabilities before they become issues. By analyzing your codebase, it detects weaknesses like SQL injection, cross-site scripting (XSS), and buffer overflows, providing clear guidance on how to address them.
Why I Picked Aikido Security: Aikido's SAST engine focuses exclusively on security, filtering out non-security issues such as code readability and style. This means you'll only receive alerts that matter, reducing distractions and allowing your team to concentrate on genuine vulnerabilities. Additionally, Aikido supports all major programming languages, ensuring comprehensive coverage across diverse codebases.
Standout Features & Integrations:
Other features include an AI-powered auto-triage system that prioritizes vulnerabilities, dismisses false positives, and provides actionable advice. It also offers dependency scanning, integrated IDE support, runtime protection, cloud posture management, open source dependency scanning, secrets detection, and infrastructure as code scanning.
Integrations include Amazon Web Services (AWS), Google Cloud, Microsoft Azure Cloud, Drata, Vanta, AWS Elastic Container Registry, Docker Hub, Jira, Asana, and GitHub.
Pros and cons
Pros:
- Has a comprehensive dashboard and customizable reports
- Offers actionable insights
- Scalable for growing teams
Cons:
- Ignores vulnerabilities if no fix is available
- Only available in English
New Product Updates from Aikido Security
Aikido Security's New Security Features and Enhancements
Aikido Security's update includes secure-by-default hardened container images, autogenerated OpenAPI specs, inline SCA vulnerability detection, and additional Advanced Cloud Rules for improved security. More details at Aikido Changelog.
Dynatrace offers a sophisticated application performance and monitoring solution, designed not only to gauge performance but also to identify and address security threats in real time. The platform's commitment to instantaneous threat detection makes it a crucial asset for businesses aiming to maintain a secure digital environment without compromising on agility.
Why I Picked Dynatrace: When determining which tools to include on this list, the immediacy with which Dynatrace operates caught my attention. In comparing various platforms, I found that the real-time aspect of Dynatrace's threat detection was both unique and invaluable.
Considering the evolving nature of cyber threats and the need for businesses to respond promptly, I came to the conclusion that Dynatrace stands out as 'best for real-time threat detection.'
Standout Features & Integrations:
Dynatrace shines with features like full-stack monitoring, root cause analysis, and AI-assisted problem resolution, which not only detect but also aid in mitigating threats swiftly.
When it comes to integrations, Dynatrace offers compatibility with a host of cloud platforms, CI/CD tools, and container orchestration systems, ensuring security oversight across diverse environments.
Pros and cons
Pros:
- Robust integration capabilities with popular cloud and DevOps tools
- Comprehensive full-stack monitoring provides deep insights
- AI-assistance aids in quick threat mitigation
Cons:
- Pricing might not align with smaller budgets
- The vast array of features could pose an initial learning challenge
- Might be overkill for smaller-scale operations
GitLab is a comprehensive DevOps platform that consolidates source code management, continuous integration, and continuous delivery (CI/CD) into one interface. Its inclusion of built-in security functionalities ensures that the software development process remains safeguarded at every stage, making it ideal for teams desiring an integrated security solution.
Why I Picked GitLab: In my quest to find an all-encompassing DevOps tool with a keen emphasis on security, GitLab emerged as a frontrunner. Its unified approach to the software development lifecycle and inbuilt security components differentiate it from many standalone tools. The way GitLab merges development and security easily is the key reason I believe it's 'best for integrated DevOps security.'
Standout Features & Integrations:
GitLab offers automated security scans in its CI/CD pipelines, ensuring code is assessed for vulnerabilities before deployment. Additionally, its container security capabilities protect Docker containers and Kubernetes clusters.
As for integrations, GitLab supports a vast array of tools such as Jenkins, JIRA, and Kubernetes, allowing teams to preserve their existing tech stacks while leveraging GitLab's capabilities.
Pros and cons
Pros:
- Vast integration possibilities with popular development tools
- Robust container security features for modern application deployment
- Consolidated DevOps and security in a singular platform
Cons:
- Some advanced security features are restricted to higher pricing tiers
- Performance might vary depending on the scale of the projects
- Steeper learning curve due to its comprehensive feature set
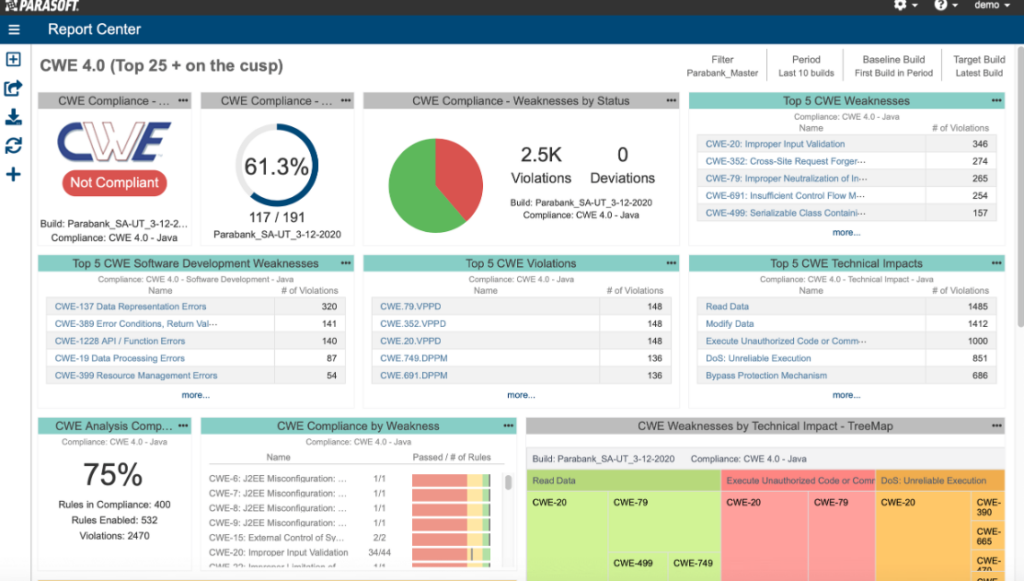
Parasoft Jtest is a dedicated Java testing tool, diligently designed to fortify the quality of Java applications. It offers an exhaustive suite of functionalities to ensure Java codes are not only error-free but adhere to best practices and standards, making it a prime choice for Java application testing.
Why I Picked Parasoft Jtest: I chose Parasoft Jtest after a thorough comparison with other Java testing tools. Its comprehensive feature set tailored specifically for Java, coupled with its reputation in the industry, set it apart.
My determination that it is 'best for Java application testing' stems from its unwavering focus on Java and its associated intricacies.
Standout Features & Integrations:
Parasoft Jtest excels with its static analysis, ensuring that codes align with the coding standards. Furthermore, it harnesses the power of unit testing and code coverage to ascertain that the Java applications are robust and resilient. On the integration front, Parasoft Jtest smoothly collaborates with popular CI/CD tools and also supports integration with version control systems.
Pros and cons
Pros:
- Strong integration capabilities
- Rich set of features from static analysis to code coverage
- Specialized in Java, ensuring meticulous testing
Cons:
- Initial setup might require a learning curve for some teams
- Focuses mainly on Java, limiting cross-language utility
- Might be overwhelming for novice Java developers
Snyk is a prominent security platform tailored to detect and resolve vulnerabilities in open-source libraries and containers. By focusing on the nuances of open-source codebases, Snyk provides teams with invaluable insights, ensuring safer application development and deployment.
Why I Picked Snyk: I chose Snyk after closely comparing several tools that cater to open-source security. Snyk distinctly stood out because of its in-depth vulnerability database and the clarity of its code insights. These unique features positioned Snyk as a tool that is undeniably 'best for open-source code insights.'
Standout Features & Integrations:
At the core of Snyk's offering is its expansive vulnerability database that is regularly updated, allowing for precise and timely threat detection. Additionally, Snyk offers license compliance checks and remediation advice, which are invaluable for open-source projects.
Integration-wise, Snyk supports a broad spectrum of platforms, from GitHub and Bitbucket to popular CI/CD pipelines, ensuring that security checks are easily incorporated into development workflows.
Pros and cons
Pros:
- Extensive integration capabilities streamline the development process
- License compliance features ensure legal protection
- Comprehensive vulnerability database tailored for open-source projects
Cons:
- Without clear pricing details, budgeting can be challenging
- The depth of insights might overwhelm newcomers
- Targeted primarily at open-source projects, which might not be suitable for all types of applications
CodePeer is a sophisticated static analysis tool tailor-made for the Ada programming language. Its adeptness in parsing and understanding the nuances of Ada underpins its reputation in the industry.
Why I Picked CodePeer: In the process of selecting tools, I judged them on their core competencies and adaptability to specific programming languages. CodePeer was a clear frontrunner due to its singular focus on Ada and its superior analysis capabilities. This dedicated attention to Ada's constructs, in my opinion, justifies its position as 'best for in-depth Ada language analysis.'
Standout Features & Integrations:
CodePeer is renowned for identifying intricate runtime and logical errors that could otherwise remain undetected. Its utilization of formal methods to offer a thorough understanding of potential vulnerabilities sets it apart.
Integration capabilities extend to the GNAT Programming Studio (GPS) and GNATbench, offering Ada developers a harmonized experience.
Pros and cons
Pros:
- Works in tandem with GNAT tools
- Proficient in detecting intricate errors
- Exclusive focus on the Ada language
Cons:
- Dependency on GNAT ecosystem for optimal utility
- Potential complexity for beginners
- Limited utility for non-Ada projects
Legit Security offers a comprehensive approach to software security by integrating various tools and platforms under a single umbrella. Its ability to provide a unified platform ensures that businesses can streamline their security operations and maintain consistent controls across all aspects.
Why I Picked Legit Security: When determining which tools to add to this list, Legit Security caught my attention due to its ability to consolidate different security measures in one platform. By comparing it with other options in the market, I discerned that its unification of controls is what differentiates it.
Given the complexities businesses face in coordinating disparate security tools, I judged that Legit Security is truly 'best for unified security control.'
Standout Features & Integrations:
Legit Security boasts features that enable real-time threat detection, robust vulnerability assessment, and proactive security monitoring.
Integration-wise, the tool melds effortlessly with various IT infrastructures and can work in tandem with popular CI/CD tools, making security checks an integral part of the development process.
Pros and cons
Pros:
- Integrates with major CI/CD tools, ensuring continuous security checks
- Facilitates real-time threat detection and proactive monitoring
- Offers a centralized platform for various security tasks
Cons:
- Some features could be redundant for smaller businesses or specific use cases
- Potential for feature overlap with existing tools a company might use
- Might present a learning curve for those accustomed to decentralized security tools
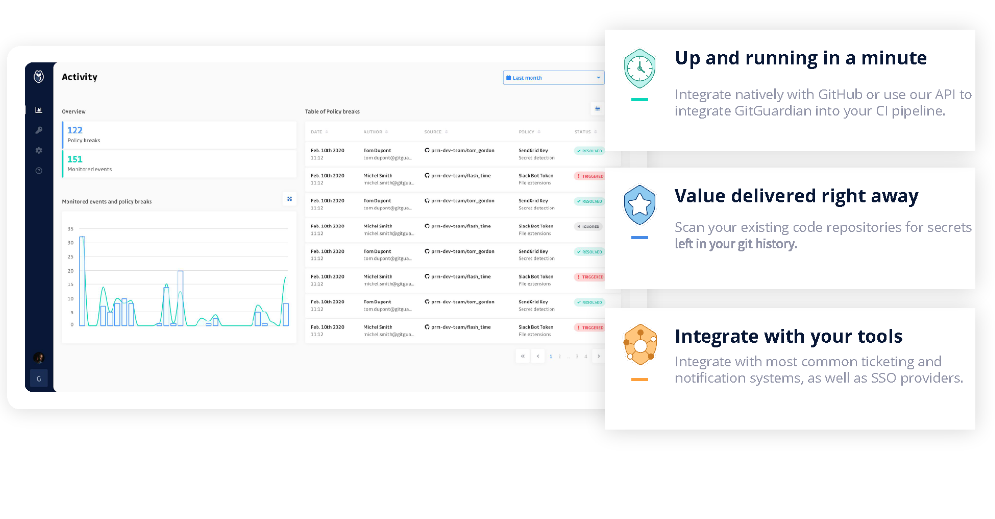
GitGuardian specializes in monitoring codebases and detecting inadvertent leaks of sensitive information, such as API keys or credentials. With an increasing number of breaches originating from exposed secrets in public repositories, GitGuardian serves as a critical line of defense for organizations.
Why I Picked GitGuardian: I selected GitGuardian after a meticulous examination of several tools aimed at safeguarding code repositories. GitGuardian's focused approach to identifying exposed secrets and its robust detection algorithms made it a clear front-runner. Its precision in pinpointing potential data leaks is why I believe it is 'best for detecting sensitive data leaks.'
Standout Features & Integrations:
One of GitGuardian's most crucial features is its ability to continuously scan public and private repositories for over 200 types of secrets. Furthermore, its incident response platform allows teams to act promptly on detected vulnerabilities.
In terms of integrations, GitGuardian smoothly connects with platforms like GitHub, GitLab, and Bitbucket, ensuring comprehensive coverage across various development environments.
Pros and cons
Pros:
- Swift incident response platform ensures timely action on vulnerabilities
- Supports both public and private repository scans
- Dedicated focus on detecting sensitive data leaks
Cons:
- Dependency on third-party integrations might affect detection efficacy in non-supported platforms
- Without transparent pricing, it may be challenging for teams to budget accurately
- The specificity of the tool may not cater to broader security needs
Embold is a powerful tool that delves deep into your code, unearthing problematic design patterns known as anti-patterns. Its strength lies not just in detection but in offering constructive insights to remediate these potentially troublesome code structures, making it aptly suited for identifying anti-patterns.
Why I Picked Embold: I chose Embold from a multitude of tools because of its sharp focus on design and structural flaws in the code. While many tools scan for vulnerabilities, Embold's distinct approach to identifying and addressing anti-patterns caught my attention. It is this specialization that convinced me of its status as 'best for identifying anti-patterns.'
Standout Features & Integrations:
Beyond identifying anti-patterns, Embold provides actionable insights to improve overall code quality. The platform uses AI-driven analytics to not just point out issues but to assist in refactoring.
Integration-wise, Embold is versatile, fitting into CI/CD pipelines and working in tandem with platforms like GitHub, GitLab, and Bitbucket.
Pros and cons
Pros:
- Extensive integration capabilities with CI/CD tools
- AI-backed analysis for better refactoring suggestions
- Precision in identifying anti-patterns
Cons:
- Over-reliance on AI could sometimes miss human nuances
- May generate verbose reports for larger codebases
- Steeper learning curve for beginners
Other Noteworthy Static Application Security Testing Tools
Below is a list of additional static application security testing tools that I shortlisted but did not make it to the top 12. They are definitely worth checking out.
- Appknox
Good for mobile app security checks
- DeepSource
Good for continuous analysis in CI/CD
- Fortify Static Code Analyzer
Good for extensive language support
- AppSpider DAST (Dynamic Application Security Testing) Tool
Good for modern web app assessments
- Checkmarx
Good for comprehensive vulnerability detection
- Contrast Security
Good for real-time code analysis
- Klocwork
Good for architectural risk analysis
- Qualys Web Application Scanning
Good for cloud-based web app scans
- Kiuwan Code Security
Good for actionable security insights
- Veracode Static Analysis (SAST)
Good for binary-based source code evaluation
Selection Criteria for Choosing the Best Static Application Security Testing Tools
In my pursuit of the best static application security testing tools, I didn't settle for superficial evaluations. I've dived deep, testing and researching numerous tools to ascertain the gems in this domain. From this extensive evaluation, I identified some pivotal criteria, with specific functionality at the forefront of my determination.
Here's a detailed breakdown of what I've concluded matters the most:
Core Functionality
- Vulnerability Detection: The primary purpose of any SAST tool. It should efficiently and accurately pinpoint potential security flaws in the source code.
- Codebase Compatibility: Ability to scan multiple programming languages and frameworks to ensure no part of your application remains unchecked.
- Continuous Integration: Easy integration into the CI/CD pipeline, enabling regular and automated code checks as part of the development process.
- Risk Prioritization: Not just finding vulnerabilities, but also ranking them based on severity to address the most critical ones first.
Key Features
- Custom Rule Creation: Enables users to define their own set of rules tailored to their application's specific needs.
- Binary Code Scanning: Some tools offer the ability to evaluate compiled applications, assessing them without the original source code.
- Real-time Feedback: Immediate feedback as developers write or commit code, fosters a proactive approach to security.
- Cloud-Based Scans: Offers flexibility and scalability, especially important for larger enterprises or those with distributed teams.
Usability
- Intuitive Dashboard: For a SAST tool, a visual representation of vulnerabilities, complete with file paths and severity charts, is crucial. This aids in quickly grasping the security posture of the application.
- Easy Integration Points: SAST tools should have plug-and-play integrations with popular IDEs and version control systems, reducing conflict in the development process.
- Role-Based Access: Ensures that access to scan results and configurations is limited to authorized personnel, bolstering the security within the security tool.
- Comprehensive Documentation: Given the technical nature of these tools, a comprehensive knowledge base, complete with common use cases and troubleshooting tips, is essential for user onboarding and ongoing support.
Most Common Questions Regarding Static Application Security Testing Tools (FAQ's)
What are the benefits of using a SAST tool?
Using a SAST tool offers several advantages:
- Early Detection: Identify vulnerabilities early in the development lifecycle, even before the code is run.
- Cost-Efficiency: Addressing issues earlier is typically less costly than fixing them after deployment.
- Improved Security Posture: Gain a comprehensive view of the application’s security, enabling better risk management.
- Developer Education: Real-time feedback educates developers about security best practices, enhancing coding standards.
- Regulatory Compliance: Many tools assist in meeting industry-specific security compliance requirements.
How much do these tools typically cost?
The cost of SAST tools can vary greatly depending on their functionality, scalability, and the target market (enterprise vs. individual developers). Prices can range from a few dollars per month for basic tools to several thousand dollars annually for enterprise-grade solutions.
What are the common pricing models for SAST tools?
There are several pricing models adopted by SAST providers:
- Per User/Developer: Pricing is based on the number of users or developers accessing the tool.
- Per Scan: Charge based on the number of scans conducted.
- Subscription-based: Monthly or yearly subscriptions offering unlimited scans within the period.
- Tiered Pricing: Different pricing tiers based on features, number of scans, or size of the codebase.
What is the typical pricing range for these tools?
The pricing range can be vast. For individual developers or small projects, prices might start as low as $10-$50 per month. For larger enterprises or more comprehensive tools, it can range from $1,000 to $5,000 per year or even more.
Which are some of the cheapest and most expensive software options?
Among the most affordable options are tools like Semgrep or DeepSource, which offer competitive pricing for individual developers or small teams. On the other hand, enterprise-grade solutions like Checkmarx or Veracode Static Analysis tend to be at the higher end of the spectrum due to their extensive features and scalability.
Are there any free SAST tool options available?
Yes, there are free SAST tools available, often as open-source projects. For instance, Semgrep offers a free tier, and there are other open-source options like FlawFinder or Brakeman for Ruby on Rails applications. However, free versions may have limitations in terms of features or the number of scans.
Is the pricing for these tools a one-time fee or recurring?
Most SAST tools adopt a recurring pricing model, be it monthly, quarterly, or annually. Some might offer one-time purchase options, but they are less common in the industry.
Do these tools typically offer trial periods or demos?
Yes, many SAST tools provide trial periods, allowing users to test their features and efficiency before making a purchase decision. This trial phase can range from a week to a month, depending on the tool.
Other Security Testing Software Reviews
Summary
Selecting the best static application security testing (SAST) tool is an essential step in ensuring the security of an application's source code. Through this guide, I've delved deep into the core functionalities, essential features, usability aspects, and critical criteria that matter most when choosing the right SAST solution.
Beyond just identifying vulnerabilities, the right tool can offer invaluable insights, foster better coding habits among developers, and ensure regulatory compliance.
Key Takeaways
- Early detection matters: The primary advantage of SAST tools is their ability to detect vulnerabilities early in the development lifecycle, making it cost-effective and enhancing the overall security posture.
- Usability and user experience: Beyond just functionality, consider the tool's design, ease of onboarding, interface, and customer support. An effective SAST tool should fit into a developer's workflow.
- Price vs. value: While pricing is an essential consideration, it's vital to weigh the cost against the value offered. Some tools might be expensive, but their comprehensive features, scalability, and accuracy can offer a higher return on investment.
What Do You Think?
While I've done extensive research and testing to curate this list, the realm of static application security testing is vast and ever-evolving. If there are other static application or software composition analysis tools you've found valuable that I didn't include, I'd love to hear from you. Please share your suggestions or experiences in the comments, and let's make this resource even more comprehensive for everyone. Your insights could be the key to helping others find their ideal SAST tool.