10 Best Multi Factor Authentication Software Shortlist
Here's my pick of the 10 best software from the 27 tools reviewed.
Our one-on-one guidance will help you find the perfect fit.
Navigating the complex world of user authentication, I've come to value multi factor authentication software. With rising data breaches, it's essential to secure online accounts beyond just passwords. This goes beyond the traditional username and password combination and can include something the user knows, something the user has, or something inherent to the user.
These tools not only ensure end-users receive secure access via passcodes and self-service provisioning but also enhance remote access, connecting web-based user identities more securely. The pain points? Managing multiple user authentications, identity and access management (IAM), and ensuring remote access without compromising security. But with the right software, these are addressed, fortifying your accounts against breaches.
What is a Multi Factor Authentication Software?
Multi factor authentication software provides an added layer of security by requiring users to provide two or more verification methods before granting access to an account or system. This software offers multiple authentication factors – from OTPs for Windows, Linux, and MAC/macOS to biometric authentication for mobile apps on Android and Apple iOS. With tools, you get push notifications, authenticator apps, and software tokens that work easily with the active directory.
Organizations and individuals leverage these tools to bolster security, particularly in an era where cyber threats are rampant. This approach minimizes the risk of unauthorized access, even if malicious actors obtain a user's password, ensuring that sensitive data and systems remain protected.
Best Multi Factor Authentication Software Summary
| Tool | Best For | Trial Info | Price | ||
|---|---|---|---|---|---|
| 1 | Best for adaptive MFA with multiple authentication factors | Free version available (up to 50 domain users) | From $595 (500 domain users) | Website | |
| 2 | Best for combining password management and MFA | Not available | From $3/user/month (billed annually) | Website | |
| 3 | Best for comprehensive endpoint protection | Not available | From $3/user/month (billed annually) | Website | |
| 4 | Best for achieving passwordless authentication | Free 14-Day Trial | From $8/user/month (billed annually) | Website | |
| 5 | Best for those already in the Salesforce environment | Free plan available | From $25/user/month (billed annually) | Website | |
| 6 | Best for scalable enterprise authentication | Free trial available | From $35/month | Website | |
| 7 | Best for users of Google's suite of services | Not available | Free for users | Website | |
| 8 | Best for users within the Microsoft ecosystem | Not available | From $6/user/month (billed annually) | Website | |
| 9 | Best for businesses in hybrid cloud scenarios | Not available | Pricing upon request | Website | |
| 10 | Best for ensuring mobile-based security | Not available | From $5/user/month (billed annually) | Website |
-

Docker
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.6 -

Pulumi
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.8 -

GitHub Actions
Visit Website
Best Multi Factor Authentication Software Reviews
Best for adaptive MFA with multiple authentication factors
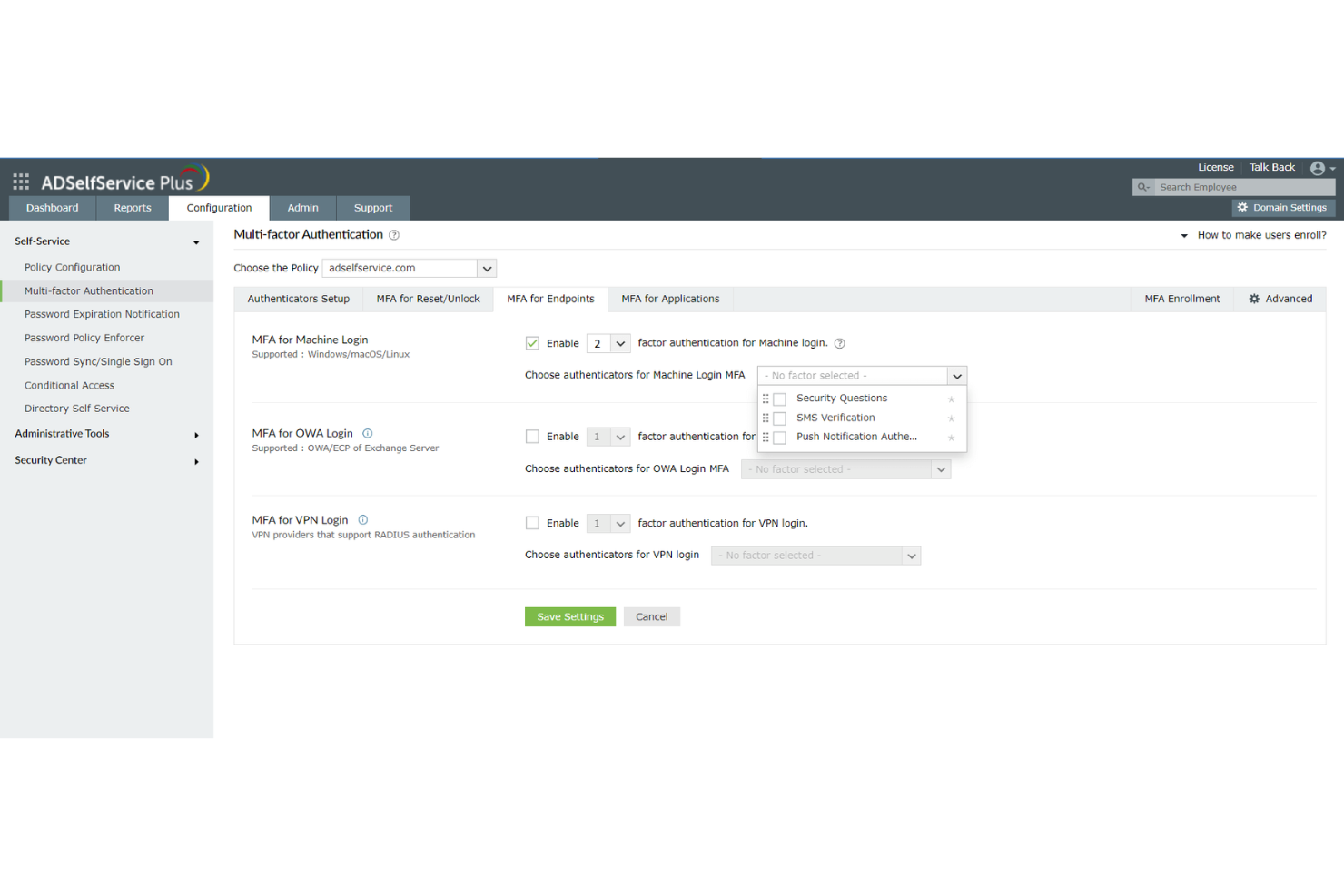
ManageEngine ADSelfService Plus is a comprehensive self-service password management and single sign-on (SSO) solution designed to streamline IT operations and enhance security. It caters to IT admins and end-users by providing functionalities such as password self-service, multi-factor authentication (MFA), and endpoint security.
Why I Picked ManageEngine ADSelfService Plus: ADSelfService Plus supports various authentication techniques such as biometrics, TOTP codes, push notifications, and security keys, which enhance the security landscape by adding multiple layers of verification beyond the traditional username and password. This adaptability in authentication methods ensures that organizations can tailor their security protocols to meet specific needs and compliance requirements. Furthermore, its adaptive MFA feature dynamically adjusts authentication requirements based on risk factors like user location and device type, providing a nuanced and context-aware security measure.
Standout features & integrations:
Other features include Single Sign-On (SSO), which integrates seamlessly with both on-premises and cloud-based applications, offering a unified and secure login experience across different environments. The tool also has self-service password management capabilities to allow users to reset passwords and unlock accounts independently. Integrations include Zendesk, Freshdesk, Splunk, syslog, and other ManageEngine applications like ManageEngine ADManager Plus and AD360.
Pros and cons
Pros:
- Extensive reporting features for audits and compliance
- Various MFA options
- Self-service password reset
Cons:
- Free version has limited features
- Can be expensive for smaller organizations
LastPass functions as a comprehensive tool designed to both manage passwords securely and offer multi-factor authentication (MFA). It has cleverly combined these two essential features, making it an ideal choice for those who prioritize both password management and improved authentication.
Why I Picked LastPass: During my selection process, LastPass distinctly stood out because of its dual capability: managing passwords while also offering MFA. Comparing it with other tools, its comprehensive approach to security is what I found to be unique. My judgment is that for individuals or businesses that see the value in uniting password management with MFA, LastPass is a fitting choice.
Standout features & integrations:
LastPass provides a secure vault for storing passwords, notes, and other credentials, all of which are encrypted locally on the user's device. Additionally, its MFA functionality is robust, integrating biometric and contextual factors for improved security. Integration-wise, LastPass can be coupled with numerous web browsers, and platforms, and has extensions that ensure its functionality is easily accessible across devices.
Pros and cons
Pros:
- Wide range of browser and platform integrations
- Local encryption ensures user data remains private
- Combines password management and MFA in one platform
Cons:
- Some advanced features are only available in higher-priced tiers
- The user interface might be challenging for non-tech-savvy individuals
- Annual billing may not appeal to all users
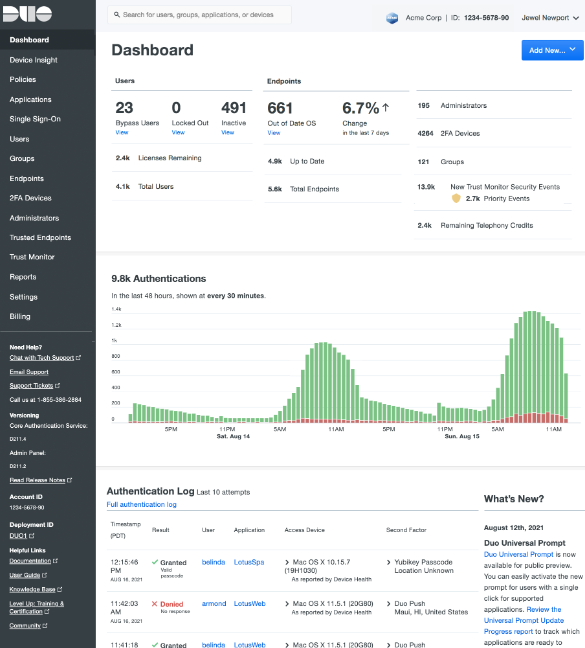
Duo Security, a part of Cisco, is recognized for its multi-factor authentication services and its commitment to safeguarding all user devices. Duo ensures that every device accessing sensitive data meets security standards.
Why I Picked Duo Security: I chose Duo Security after determining and comparing its capabilities with numerous other tools on the market. In my judgment, for organizations that value a holistic approach to securing user access and device compliance, Duo is unparalleled in its commitment to comprehensive endpoint security.
Standout features & integrations:
Duo's adaptative authentication allows policies to be set based on the user and device risk, ensuring dynamic and risk-aware access controls. Additionally, Duo's endpoint health inspection ensures that only compliant devices access applications. For integrations, Duo supports a vast number of platforms, from VPNs to web applications, and is consistently updated to integrate with emerging technology solutions.
Pros and cons
Pros:
- User-friendly interface and easy deployment
- Broad array of integrations, accommodating a wide range of platforms
- Holistic approach to authentication and endpoint security
Cons:
- Some users might find the policy setup process complex
- Integration with non-Cisco products can sometimes require additional configuration
- Might have features unnecessary for very small organizations
Uniqkey is a robust authentication solution designed to offer users the convenience and security of passwordless authentication. Uniqkey stands as a formidable option to bridge this transition, particularly for those who prioritize passwordless solutions.
Why I Picked Uniqkey: In the process of determining the best tools for this list, Uniqkey grabbed my attention because of its dedication to a passwordless environment. Its focus on such a specific and critical area of cybersecurity made it different from many others I compared. I judged it as the best tool for those who are looking to achieve passwordless authentication, given its specialized approach and effectiveness in this domain.
Standout features & integrations:
Uniqkey's primary strength is its adaptive authentication which analyzes risk factors in real-time to determine the necessary level of verification. Moreover, it offers biometric verification options and a secure password vault for users who might still have some passwords to manage. For integrations, Uniqkey is compatible with a range of enterprise systems, ensuring businesses can incorporate it without causing disruptions to existing workflows.
Pros and cons
Pros:
- Secure vault for residual passwords
- Adaptive authentication based on real-time risks
- Dedicated to a passwordless environment
Cons:
- Relatively new in the market, which might concern some users seeking established brands
- Limited to certain platforms and devices
- Might have a learning curve for those new to passwordless systems
The Salesforce Platform provides an extensive suite of tools and services designed to enable businesses to build and scale applications quickly. It is tailored especially for companies and teams that are already immersed in the Salesforce ecosystem.
Why I Picked Salesforce Platform: Selecting tools for this list, I was drawn to the Salesforce Platform because of its deep integration capabilities and the comprehensive solutions it offers. This platform provides the most aligned and synergistic approach. That's why I believe it's best for those already in the Salesforce environment.
Standout features & integrations:
The Salesforce Platform is notable for its low-code development capabilities, allowing businesses to create applications swiftly. It also boasts AI-powered analytics and a robust security model to protect sensitive data. When it comes to integrations, the platform naturally works well with other Salesforce offerings like Sales Cloud, Service Cloud, and Marketing Cloud, ensuring a cohesive experience for users.
Pros and cons
Pros:
- Strong security features
- Low-code development accelerates application creation
- Deep integration with other Salesforce products
Cons:
- Requires investment in learning and training for optimal use
- Pricing can become high as more features are added
- Might be overwhelming for those new to Salesforce
Auth0 is a leading identity management platform designed to simplify authentication and authorization for businesses of all sizes. Tailored especially for enterprises, it ensures that as businesses grow, their security measures scale with them, making it a top pick for scalable enterprise authentication.
Why I Picked Auth0: When I was selecting an authentication tool, Auth0 consistently emerged at the forefront of the options. Its reputation for robustness and adaptability in the identity management space set it apart from its peers. In comparing it to other tools, its scalability especially for larger corporations cemented its position as the best for scalable enterprise authentication in my opinion.
Standout features & integrations:
Among its myriad of features, Auth0's Single Sign-On, Adaptive Multifactor Authentication, and user-friendly administration dashboard are particularly noteworthy. When considering integrations, Auth0 shines with its compatibility across a range of platforms such as AWS, Slack, Salesforce, and Zendesk, ensuring businesses have a cohesive and integrated workflow.
Pros and cons
Pros:
- Comprehensive security tools
- Wide range of third-party integrations
- Adaptable for various business sizes
Cons:
- Starting price might be steep for some budgets
- Some customizations can demand technical know-how
- Potential complexity for smaller businesses
Google Authenticator is a tool dedicated to ensuring users' accounts are protected through two-factor authentication. As a product within Google's ecosystem, it offers a streamlined experience, especially for users already familiar with Google services, enhancing security without complicating the user journey.
Why I Picked Google Authenticator: While selecting tools for this list, Google Authenticator was a clear inclusion, mainly due to its integration with Google's extensive suite. I have determined that its synchronicity with Google services makes it a top pick for users already nested within the Google ecosystem. I hold the opinion that for those heavily invested in Google's suite, Authenticator offers unmatched convenience.
Standout features & integrations:
Google Authenticator provides time-based one-time passwords, ensuring an added layer of security. The ability to scan QR codes for faster setup of accounts is a feature that simplifies the user experience. Additionally, it integrates with most major web services and platforms, not limited to just Google's suite, expanding its utility.
Pros and cons
Pros:
- Supports a broad range of web services beyond Google
- QR code scanning feature simplifies setup
- Direct integration with Google services
Cons:
- Lacks cloud-based backup for account recovery
- Loss of device can lead to setup complications
- Requires manual setup for non-Google services
Microsoft Authenticator streamlines the multi-factor authentication process for those immersed in the Microsoft ecosystem. By integrating deeply with Microsoft services, it provides a smooth and efficient authentication experience, making it an ideal choice for users heavily reliant on Microsoft products.
Why I Picked Microsoft Authenticator: When selecting tools for this list, Microsoft Authenticator stood out due to its natural integration with the vast array of Microsoft services. From my perspective, the tool's compatibility and synchronicity within the Microsoft environment differentiate it from many other authenticators. Based on these observations, I judged it as the best fit for users who are deeply enmeshed in the Microsoft ecosystem.
Standout features & integrations:
One of Microsoft Authenticator's prime features is its passwordless login capability, which enhances security while simplifying the user experience. The tool also boasts biometric verification, allowing users to authenticate using their fingerprint or face recognition. Regarding integrations, it flawlessly meshes with Microsoft services such as Office 365, Outlook, and OneDrive, providing a unified and secure experience across all platforms.
Pros and cons
Pros:
- Biometric verification options
- Passwordless login feature
- Deep integration with Microsoft services
Cons:
- Limited customization options compared to other tools on the market
- Requires regular updates for optimal functionality
- Might be less appealing to non-Microsoft users
IBM Security Verify offers an identity and access management solution that is designed to provide a secure user experience across various platforms and applications. This tool stands out especially for businesses operating in hybrid cloud environments, given its robust integration capabilities and security features tailored for such scenarios.
Why I Picked IBM Security Verify: In the process of selecting tools, IBM Security Verify caught my eye because of its distinct focus on hybrid cloud situations. Judging from its features and the feedback from users, it became evident that its strengths lie in addressing the unique challenges posed by hybrid cloud setups. This makes me believe it's ideally suited for businesses navigating such complex environments.
Standout features & integrations:
IBM Security Verify boasts a comprehensive suite of features, including adaptive access policies, AI-driven insights, and a user behavior analytics engine. It's also equipped with single sign-on (SSO) and multi-factor authentication (MFA) to bolster security. As for integrations, the tool supports a wide array of applications, databases, and platforms, making it adaptable to diverse IT ecosystems.
Pros and cons
Pros:
- Broad spectrum of integrations
- Comprehensive security measures, including SSO and MFA
- Tailored features for hybrid cloud environments
Cons:
- Some businesses might find it feature-dense for simpler use cases
- Initial setup can be complex for some users
- Pricing transparency could be improved
WatchGuard AuthPoint operates as a multi-factor authentication solution designed specifically with mobile users in mind. AuthPoint provides an added layer of security, aligning perfectly with its mission to prioritize mobile-based security.
Why I Picked WatchGuard AuthPoint: In the vast sea of authentication tools, WatchGuard AuthPoint caught my attention due to its dedicated focus on mobile device security. My opinion is rooted that as mobile devices become integral to daily routines, a tool like AuthPoint, which specifically addresses mobile-based threats, becomes essential.
Standout features & integrations:
At its core, WatchGuard AuthPoint offers time-based one-time passwords (TOTPs), push-based authentication, and QR code-based authentication, all optimized for mobile experiences. In terms of integrations, AuthPoint supports a range of applications, from VPNs to cloud services, and can be integrated with the WatchGuard ecosystem of security products.
Pros and cons
Pros:
- Part of the trusted WatchGuard ecosystem
- Supports a broad array of integrations including VPNs and cloud services
- Mobile-centric authentication methods
Cons:
- Some features might be overkill for smaller businesses or individual users
- Limited customization options compared to some competitors
- Might be less appealing to businesses not using other WatchGuard products
Other Noteworthy Multi Factor Authentication Software
Below is a list of additional multi factor authentication software that I shortlisted but did not make it to the top 12. Definitely worth checking them out.
- CyberArk Identity
Good for privileged access management integration
- GateKeeper Proximity Authentication
Good for hands-free, proximity-based access
- SecureID
Good for risk-based dynamic access decisions
- PortalGuard
Good for flexible security solution integrations
- Silverfort
Good for adaptive authentication across environments
- Yubico
Good for hardware-based authentication keys
- Google Security Key Enforcement
Good for hardware-improved phishing protection
- PingID
Good for mobile biometric verification
- Prove
Good for phone-centric identity verification
- Azure Multi-Factor Authentication
Good for Azure users needing native MFA
Selection For Choosing Multi Factor Authentication Software
I evaluated more than 15 tools, aiming to distill the essence of what truly matters when choosing an MFA solution. My decisions have been clear into the following criteria, which I hope will help guide you in your own selection process.
Core Functionality
- Robust Authentication: The software should, at its heart, provide layered and secure verification processes.
- Dynamic Adjustments: It should have the capability to adjust authentication processes based on the perceived risk of a login attempt.
- Wide Coverage: The tool should cover multiple access points, ensuring that every possible entry is secured.
Key Features
- Adaptive Authentication: A system that intelligently adjusts the authentication method based on user behavior and other contextual factors.
- Biometric Verification: Incorporating unique human characteristics, such as fingerprints or facial recognition, for additional security.
- Hardware Tokens: Some solutions offer physical devices that generate codes, adding an extra layer of security.
- Geo-fencing: Determining access based on the geographic location of the user.
- Time-limited Access: Granting access only for specific time durations, after which re-authentication is required.
- Risk Analysis: Ability to gauge the risk of an access request and respond accordingly.
Usability
- Intuitive Dashboard: For MFA solutions, a centralized dashboard that gives an overview of authentication requests and potential security threats is vital.
- Quick Integration: Easy integration capabilities with existing systems, ensuring minimal disruption to current operations.
- Efficient Onboarding: The solution should come with an interactive tutorial or guide, especially for administrators who need to understand the nuances of setting up and managing the tool.
- Responsive Support: Given the critical nature of security, the software provider should offer prompt customer support, addressing concerns and issues in real time.
- Customizable User Experience: Depending on the business environment, the software should allow tailoring of user experiences, such as setting up role-based access or adjusting the frequency of authentication prompts.
Most Common Questions Regarding Multi Factor Authentication Software (FAQ's)
What are the benefits of using multi-factor authentication software?
Multi factor authentication software provides several advantages:
- Improved Security: By requiring multiple forms of verification, MFA reduces the risk of unauthorized access.
- Reduced Reliance on Passwords: With MFA, even if a password is compromised, the account remains secure because of the additional layers of authentication.
- Flexibility: Many MFA tools offer various authentication methods, allowing users to choose the most convenient one for them.
- Protection Against Phishing: Even if a user unknowingly reveals their credentials, attackers can’t access the account without additional verification.
- Compliance: Certain regulations and standards require MFA, so implementing it helps organizations stay compliant.
How much do these tools typically cost?
The pricing of multi-factor authentication software can vary widely based on the features offered, the number of users, and the deployment method (cloud-based vs on-premises).
What are the common pricing models for these tools?
Most MFA tools adopt one of the following pricing models:
- Per User: Pricing is determined by the number of users who will utilize the software.
- Feature-Based: Different pricing tiers offer varying features, with advanced features costing more.
- Flat Rate: Some providers charge a flat monthly or annual fee, irrespective of the number of users.
What's the typical range of pricing for these tools?
Generally, for cloud-based solutions, prices can range from $3/user/month to over $20/user/month. On-premises solutions might have higher upfront costs but may be more economical in the long run for large enterprises.
Which software is known to be the most affordable?
While exact prices can change, OneLogin and Azure Multi-Factor Authentication have historically been among the more affordable options on the market.
Which software tends to be the most expensive?
Premium solutions like CyberArk Identity and Thales SafeNet Trusted Access often come at a higher price point due to their advanced features and enterprise-level capabilities.
Are there any free multi-factor authentication options available?
Yes, several MFA tools offer free versions, though with limited features. Google’s Security Key Enforcement and Azure Multi-Factor Authentication, for instance, provide basic MFA functionalities at no cost.
Why is there such a vast difference in pricing among these tools?
The difference in pricing can be attributed to various factors, including the depth of features, the intended audience (small business vs. large enterprise), deployment method, and the brand’s reputation and customer support quality.
Other Multi Factor Authentication Software-Related Reviews
- Password Manager Software
- Network Security Software
- Encryption Software
- Network Access Control Software
- PKI Software
Summary
Selecting the best multi factor authentication software is a crucial decision for ensuring robust security. With a multitude of options available, the choice hinges on understanding the specific needs of your organization and matching them with the tool's capabilities. The benefits of using MFA software are clear, from security to compliance. Pricing models vary, with some tools offering per-user rates, while others might charge based on features or offer a flat rate.
Key Takeaways:
- Prioritize Your Needs: Before diving into options, outline what you specifically require from an MFA tool. Consider factors like core functionalities, key features, and usability aspects tailored to your organization.
- Understand the Costs: Pricing can be complex. While some tools may seem affordable at a glance, consider the total cost of ownership, including any potential additional fees or long-term contracts.
- Seek Flexibility and Scalability: As your organization grows, so will your security needs. Opt for an MFA solution that not only meets your current requirements but can also scale and adapt to future challenges.
What do you think?
I’ve evaluated the top multi factor authentication software options available today. However, the tech landscape is ever-evolving, and there might be emerging tools or hidden gems I haven't covered yet. If you've come across a tool that you believe should be on this list or have firsthand experience with one that's made a difference for you, please share it with me. Your input can help make this guide even more comprehensive and beneficial for everyone. Let's collaborate and secure the digital landscapes together.