10 Best Network Security Software Shortlist
Here's my pick of the 10 best software from the 22 tools reviewed.
Our one-on-one guidance will help you find the perfect fit.
Securing your network is one of the toughest challenges organizations face. Cyberattacks are becoming more sophisticated, whether it’s malware, phishing, or targeted breaches, and even a single vulnerability can lead to devastating consequences. If you’ve dealt with struggles like protecting sensitive data, managing sprawling IT systems, or staying ahead of new threats, you know how critical it is to have reliable network security software in place.
The right network security tools do more than just block unauthorized access—they actively monitor vulnerabilities, prevent breaches, and give you confidence that your systems are protected. Over the years, I’ve worked with a wide range of security solutions across different industries, helping teams move from reactive problem-solving to proactive defense. In this guide, I’ve evaluated the best network security software, breaking down their features and strengths to help you choose the one that best fits your unique environment.
What's Network Security Software?
Network security software is designed to strengthen your IT infrastructure and keep sensitive data safe. This is done with tools like antivirus software, intrusion detection and prevention systems (IDS/IPS), encryption, and security protocols. Network security software can protect from external threats like phishing and malware, as well as threats occurring within a network, such as unauthorized resource access.
By implementing network security software, service providers, institutions, and organizations can mitigate cyber risks and achieve real-time threat detection to maintain network infrastructure’s reliability.
Best Network Security Software Summary
| Tool | Best For | Trial Info | Price | ||
|---|---|---|---|---|---|
| 1 | Best for zero trust access | Free demo available | From $8/user/month (5 users minimum) | Website | |
| 2 | Best for real-time network alerts | Free trial + demo available | Pricing upon request | Website | |
| 3 | Best for secure network access | 30-day free trial | From $10/user/month | Website | |
| 4 | Best for cloud-based security monitoring and threat detection | 30-day free trial | From $39/user/month | Website | |
| 5 | Best for cloud-based threat detection | 14-day free trial | From $23.99 for 1st year (1 device) | Website | |
| 6 | Best comprehensive security services | 30-day free trial | From $15/user/month | Website | |
| 7 | Best for individual users and home environments | 30-day free trial | From $4.17/user/month | Website | |
| 8 | Best for total device security | 14-day free trial | From $4.17/user/month | Website | |
| 9 | Best for robust data protection and backup solutions | 30-day free trial | From $42/user/year (billed annually) | Website | |
| 10 | Best for advanced security analytics | 14-day free trial | From $16/user/month (billed annually) | Website |
-

Docker
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.6 -

Pulumi
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.8 -

GitHub Actions
Visit Website
Best Network Security Software Reviews
I’ll explain each tool’s features, integrations, and pricing below, so you can choose the solution that matches your network security needs.
NordLayer is a cloud-based network security platform tailored for businesses, providing secure access to corporate resources and safeguarding sensitive data.
Why I picked NordLayer: I like its implementation of Zero Trust Network Access (ZTNA). This approach ensures that only authorized users can access specific resources, minimizing the risk of unauthorized entry. Another feature that stands out is NordLayer's threat protection measures. It includes tools like DNS filtering and web protection to prevent access to malicious websites, safeguarding your team from potential online threats.
NordLayer Standout Features and Integrations:
Standout features include multi-factor authentication, which adds an extra layer of security by requiring users to provide multiple forms of verification before accessing company resources. Additionally, NordLayer offers a cloud firewall that monitors and controls incoming and outgoing network traffic based on predetermined security rules, providing a barrier against potential threats. The platform also supports site-to-site connections, allowing secure communication between different office locations or networks.
Integrations include Entra ID, Okta, OneLogin, JumpCloud, Google Workspace, Google Cloud, IBM Cloud, and AWS.
Pros and cons
Pros:
- Provides robust VPN support
- Security measures like AES-256 encryption and multi-factor authentication
- Utilizes a zero-trust framework
Cons:
- Server setup can be complex
- Number of available server locations could be expanded
Site24x7 is a cloud-based network monitoring tool designed to help you track the health and performance of your network infrastructure. It offers visibility into various network components, including devices, interfaces, and traffic patterns.
Why I picked Site24x7: I picked Site24x7 because it includes several features that directly support network security efforts. Its network configuration management lets you detect unauthorized device changes and stay compliant with security policies, helping prevent misconfigurations that could be exploited. The traffic analysis tools, which support NetFlow, sFlow, and J-Flow, give you visibility into bandwidth usage and potential malicious activity by highlighting traffic anomalies.
Site24x7 Standout Features and Integrations:
Standout features include real-time alerts that ensure you’re immediately notified of changes or threats across your infrastructure. The tool also offers automated compliance audits, continuously checking your network devices against industry standards and internal policies to ensure adherence.
Integrations include AWS, Microsoft Azure, Google Cloud Platform, VMware, Amazon EventBridge, Zoho Analytics, Moogsoft, Jira, ConnectWise, PagerDuty, Microsoft Teams, and Slack.
Pros and cons
Pros:
- Automated compliance audits
- Real-time alerts for immediate issue detection
- Comprehensive network monitoring capabilities
Cons:
- Excessive alerts can be overwhelming for users
- Lacks more robust security features, like threat detection
New Product Updates from Site24x7
Amazon CloudWatch Logs Integration
Site24x7 integrates with Amazon CloudWatch Logs, offering centralized log analytics, real-time alerts, and metric correlation. Monitor log groups and gain region-level insights within Site24x7. More details at Site24x7 What's New.
Perimeter 81 is a network security software focusing on secure remote access and cloud security. It provides a secure VPN, multi-factor authentication, and network segmentation to protect remote workers and cloud resources.
Why I picked Perimeter 81: I picked Perimeter 81 for its zero-trust network architecture and granular access controls, which provides me with secure connectivity for the distributed workforce. The user-centric design and seamless integration with existing infrastructure have simplified the remote access process, allowing employees to work from anywhere securely.
Perimeter 81 Standout Features and Integrations:
Standout Features that I thought were useful include secure network access and a user-centric design prioritizing ease of use and accessibility. It has a Software-Defined Perimeter (SDP) and Zero Trust Network Access (ZTNA) architecture, which drastically reduces the risk of unauthorized access and strengthens overall network security while allowing approved users to connect securely. Perimeter 81 also offers device management, traffic inspection, and secure web gateways.
Integrations include native integration with popular identity providers (e.g., Active Directory, Azure AD, Okta) and cloud providers (e.g., AWS, Azure)
Pros and cons
Pros:
- Offers granular access control and auditing capabilities
- Centralized management and policy enforcement
- Provides secure access to on-premises and cloud resources from anywhere
Cons:
- Integration with some legacy systems may require additional configuration
- Limited customization options for VPN protocols and settings
SolarWinds is a cloud-based security monitoring and detection platform that combines log management, threat intelligence, and SIEM capabilities. Its real-time threat detection, automated response, and centralized dashboard provide organizations with enhanced visibility and rapid incident response to combat advanced cyber threats effectively.
Why I picked SolarWinds: The automated incident response feature is the main reason I chose SolarWinds as the best cloud-based solution for security monitoring. This feature has saved me countless hours by swiftly mitigating security incidents with little or no manual intervention, allowing me to focus on more strategic security tasks.
SolarWinds Standout Features and Integrations:
Standout Features include a centralized and automated incident management system, which has streamlined my response processes. SolarWinds provides reports to help me see potential threats, system events, security incidents, and compliance adherence.
Integrations come pre-built with incident response tools like Splunk, LogRhythm, and IBM QRadar. SolarWinds integrates natively with other SolarWinds products, such as Network Performance Monitor (NPM) and Server & Application Monitor (SAM).
Pros and cons
Pros:
- Scalability and flexibility
- Advanced reporting
- Robust log management
Cons:
- Complex licensing structure
- Difficult to learn
Webroot is a lightweight security software that provides cloud-based antivirus and anti-malware protection. It offers real-time scanning, web protection, firewall monitoring, and threat intelligence, and its cloud-based approach guarantees efficient scanning while minimizing system resource usage.
Why I picked Webroot: the aspect of Webroot I love most is its lightweight cloud-based architecture, making it easy and speedy to use. I like that it offers behavior-based malware detection in the background and rollback capabilities for restoring infected files.
Webroot Standout Features and Integrations:
Standout Features include cloud-based endpoint protection that applies behavior-based malware detection and offers minimal system impact. Its intelligent scanning technology enables quick scans without compromising the thoroughness of the process. You can also select a plan with additional features such as DNS security, email protection, and password management.
Integrations include built-in integrations with best-in-class vendors in remote monitoring and management, like Datto, Atera, BreightGuage, and ConnectWise.
Pros and cons
Pros:
- Integration with remote monitoring and management (RMM) tools for centralized administration
- A wide variety of features and plans for both individual and business needs
- Real-time updates and threat intelligence
Cons:
- The user interface could benefit from a more modern and intuitive design
- Limited customization options
McAfee+ offers a robust suite of security tools, including antivirus, firewall, identity theft protection, and secure VPN. Its AI-powered threat intelligence, with real-time scanning and automatic updates, provides proactive protection against malware, ransomware, and other cyber threats.
Why I picked McAfee+: As someone who values comprehensive security, McAfee+ has been my go-to solution for protecting my personal and business data. Its antivirus, firewall, and identity theft protection feature have a repetition for effectiveness, giving me peace of mind that my digital assets are properly safeguarded.
McAfee+ Standout Features and Integrations:
Standout Features include real-time scanning and threat intelligence features to detect and remove malware, as well as a firewall to prevent unauthorized network access. The identity theft protection component safeguards personal information, including credit card details and Social Security numbers, providing an extra layer of security.
Integrations include native integrations with McAfee MVISION Cloud and McAfee ePO and pre-built integrations with third-party tools like North Star, Trellix, D3 Security, Aruba Networks, and tray.io.
Pros and cons
Pros:
- Strong customer support
- Provides multi-device protection across different platforms
- User-friendly interface
Cons:
- The initial installation process can be lengthy and resource-intensive
- High system resource usage
ESET Internet Security provides comprehensive solutions with features like advanced threat detection, firewall, anti-phishing, and secure browsing. Its lightweight and efficient design makes it a reliable choice for protecting against cyber threats.
Why I picked ESET Internet Security: I consider this tool the best for individual users and home environments because it offers comprehensive protection, including firewall, email scanning, and web browsing for up to 10 of your devices. ESET also has a long-standing reputation in the cybersecurity industry, known for its consistent and reliable security solutions across multiple platforms and devices.
ESET Internet Security Standout Features and Integrations:
Features I appreciated most in ESET Internet Security include a Device Control System that lets you choose the devices that can connect to your PC. I also liked how the Network Inspector let me track my network by receiving notifications when new unregistered devices connect. ESET also offers advanced threat detection, firewall protection, ransomware shield, anti-phishing, anti-spam, and secure payment protection to provide a safe browsing environment for online shopping and banking.
Integrations include Splunk, ServiceNow, Cisco Umbrella, IBM QRadar, McAfee ePO, and SolarWinds MSP RMM. It also integrates natively with other ESET technologies, including Secure VPN, Anti-Theft, SysInspector, Secure Authentication, and Cloud Administrator.
Pros and cons
Pros:
- Minimal impact on system performance
- Excellent mobile security app for Android
- Offers anti-theft features for stolen devices
Cons:
- Multi-device protection is expensive
- No iOS support
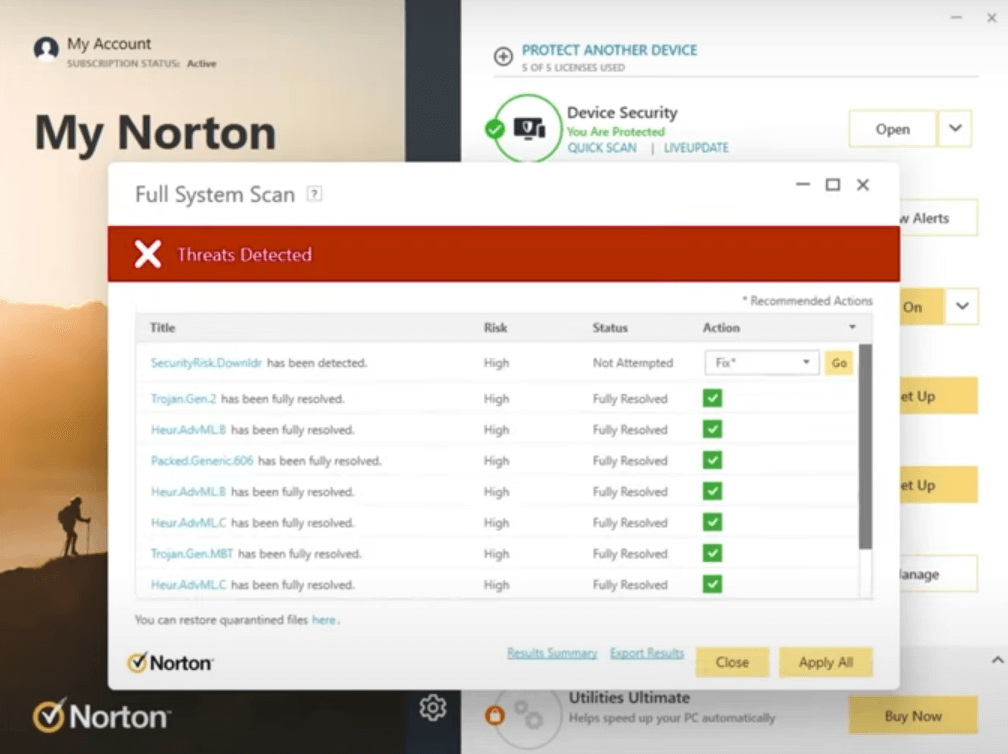
Norton 360 Deluxe is a comprehensive network security software suite offered by Norton LifeLock that protects against malware, ransomware, phishing attacks, and online threats.
Why I picked Norton Security: I picked Norton 360 Deluxe because it offers a full-featured suite of security tools, including antivirus protection, firewall, secure VPN, password manager, parental controls, and cloud backup. I found the password manager simplified my digital life by securely managing credentials across multiple devices. The cloud backup feature also impressed me with its ease of use, ensuring my files are always backed up and recoverable.
Norton 360 Deluxe Standout Features and Integrations:
Standout Features include its antivirus component, which protects against malware, while the VPN encrypts internet traffic, ensuring secure browsing. The password manager securely stores my login credentials, and the cloud backup feature provides automated backup and recovery of essential files, protecting data from loss or damage.
Integrations include native integration with other Norton tools like Norton Lifelock and Norton Antivirus Plus. It also offers pre-built integrations with tools like KamuSEO, RapidSSL, and AIOSEO.
Pros and cons
Pros:
- Provides secure online backup and cloud storage options
- Comprehensive suite of security features, including firewall, VPN, and password manager
- Robust malware and ransomware protection with a high detection rate
Cons:
- Subscription costs can be relatively higher compared to some other security solutions
- System resource usage can be noticeable
Commvault is a network security software solution focusing on data protection, with features for backup and recovery, data deduplication, encryption, and disaster recovery. Commvault centralizes data management for multiple devices and platforms to ensure data security and availability.
Why I picked Commvault: The main reason I chose Commvault is the assurance it offers to restore critical data and minimize downtime in case of a system failure. I also found that the multi-cloud support and data deduplication features provided cost-effective and efficient data management, allowing organizations to focus on their core business operations.
Commvault Standout Features and Integrations:
Standout Features that caught my eye include comprehensive backup and recovery capabilities, which are especially good for data resilience in hybrid and multi-cloud environments–including coverage for virtual machines and containers. I also liked the disaster recovery, data archiving, and secure file-sharing features.
Integrations include pre-built integrations with Google Cloud, Amazon Web Services, Microsoft Azure, Splunk, Webroot, and VMware.
Pros and cons
Pros:
- Centralized management and monitoring of data across multiple locations
- Cloud integration with significant providers
- Comprehensive data protection and backup capabilities
Cons:
- Support response times may vary
- Higher costs compared to some other data backup and recovery solutions
Elastic offers a range of solutions for security analytics, log management, and SIEM, leveraging its Elasticsearch, Logstash, and Kibana (ELK) stack. The platform's ability to adapt to meet any organization's security needs makes it an ideal solution for detecting and responding to security incidents.
Why I picked Elastic: Elastic's security analytics and SIEM solutions have been instrumental in detecting and responding to security incidents in my organization. The scalability and flexibility of the platform have allowed me to handle large volumes of log data and perform real-time analysis, enabling proactive threat mitigation.
Elastic Standout Features and Integrations:
Standout Features include advanced capabilities for security analytics, log management, and SIEM. It allows me to collect, analyze, and visualize security-related log data from multiple sources in a unified location. The platform's scalability provides efficient handling of large volumes of data, while its flexible architecture allows for customization and integration with existing security tools and workflows.
Integrations include native integration with Elastic Agent and pre-built connectors for third-party tools like Google Cloud, AWS, Microsoft Azure, Red Hat OpenShift, IBM Cloud, Oracle, Splunk, Webroot, and VMware.
Pros and cons
Pros:
- Large and active community
- Powerful search and visualization capabilities
- Scalable and flexible platform
Cons:
- Resource-intensive deployment, particularly for larger-scale implementations
- Setting up and configuring the Elastic stack may require technical expertise
Other Network Security Software Options
Still didn’t find the perfect network security tool for you? Here are a few more that didn’t make my top list but are worth checking out for other uses:
- Avira Prime
For privacy-focused individuals and organizations
- Astra Pentest
For comprehensive vulnerability scanning
- ManageEngine Log360
For centralized log management
- Acunetix
For tailored network security solutions
- CrowdStrike
For AI-driven endpoint protection
- CloudFlare
For web app security and performance optimization
- NordVPN
VPN for personal use
- SonicWall Capture ATP
For advanced threat protection
- Palo Alto Network
For security orchestration, automation, and response (SOAR)
- pfSense
Open-source solution for robust network security
- WatchGuard Network Security
For network visibility and unified threat management (UTM)
- Snort
For real-time network intrusion detection and prevention
Selection Criteria For Best Network Security Software
Here are the evaluation criteria I used to develop my list of the best network security software for this article:
Core Functionality
I prioritized tools with a wide range of security measures to create a multi-layered defense. Aside from protecting your network from unauthorized access and external threats, the best security platforms should enable you to:
- Encrypt sensitive data transmitted throughout the network
- Conduct vulnerability assessments to identify and address security weaknesses
- Monitor network traffic and implement strong firewall protection to control it
- Manage user access and permissions within the network securely
Key Features
To deliver this core functionality, the following features or elements are essential in an effective network security platform:
- Real-time monitoring and reporting: An effective network security platform should provide real-time monitoring capabilities, allowing for continuous monitoring of network traffic, system logs, and security events. It should offer comprehensive reporting functionality, providing insights into security incidents, anomalies, and compliance status.
- Vulnerability scanning: This feature includes vulnerability scanning capabilities to identify potential weaknesses in the network infrastructure. It enables proactive identification and remediation of vulnerabilities, reducing the risk of exploitation by malicious actors.
- Identity and access management: The software should support secure authentication methods, role-based access controls, and multi-factor authentication, ensuring that only authorized users can access sensitive data and systems.
- Centralized management: A network security software should provide a centralized console or dashboard that allows administrators to monitor, configure, and manage security controls across the network infrastructure from a single interface.
- Integration capabilities: The software should support integration with threat intelligence feeds, SIEM (Security Information and Event Management) solutions, incident response platforms, and other security infrastructure components. This enables enhanced threat detection, automated response actions, and seamless collaboration between different security tools.
Usability
I chose software with easy-to-use and intuitive dashboards that show the network’s security status, key metrics, and real-time alerts in a centralized system. I also looked for tools that had a history of positive reviews and a strong user base.
Integrations
I chose software that worked well with other security solutions, like SIEM platforms and vulnerability scanners, to simplify security management. You can review the critical integrations of each software on my list in the overview to choose a solution that best aligns with your existing tools.
People Also Ask
Here are some FAQs about network security software you can explore to make a more practical decision that addresses your security needs:
How does network security software work?
What is the difference between network security software and incident response software?
What are the fundamental principles of network security?
Choosing The Right Network Security Software
The 12 best network security software options showcase a wide variety of capabilities designed to safeguard networks, detect intrusions, and prevent data breaches. For example, if you’re interested in just the essential coverage for your home or small business, a straightforward antivirus package from ESET or McAfee could do the trick. More complex security tasks might require additional tools, such as Elastic for data analytics, Commvault for data protection, or others from my list.
In any case, I hope my overview makes it easy for you to select the right network security software for your individual or organizational needs, budget considerations, and network security requirements.
For more articles and insights from leading security industry experts, subscribe to The CTO Club newsletter.