Best Encryption Software Shortlist
Here’s my shortlist of the best encryption software:
Our one-on-one guidance will help you find the perfect fit.
If you're evaluating encryption software, you might already know what's at stake: ensuring confidential information stays private and protecting your organization from costly breaches and compliance failures. But deciding which encryption solution to choose can feel confusing, particularly when each provider claims superior security, ease-of-use, or compliance-readiness.
Encryption software helps you secure sensitive data, control who accesses your information, and comply effortlessly with regulatory standards. The right solution doesn't just encrypt—it integrates smoothly into your workflow, reduces security management headaches, and helps you and your team confidently handle sensitive information day-to-day.
With over a decade advising tech teams and personally reviewing a wide selection of encryption solutions, I’ve learned how to identify tools that deliver tangible value. In this article, I share my insights to help you choose software confidently. You'll find practical, unbiased evaluations of features, pros, cons, and pricing—so your decision is informed, clear, and aligned with your real-world needs.
Why Trust Our Software Reviews
We’ve been testing and reviewing SaaS development software since 2023. As tech experts ourselves, we know how critical and difficult it is to make the right decision when selecting software. We invest in deep research to help our audience make better software purchasing decisions.
We’ve tested more than 2,000 tools for different SaaS development use cases and written over 1,000 comprehensive software reviews. Learn how we stay transparent & check out our software review methodology.
Best Encryption Software Summary
This comparison chart summarizes pricing details for my top encryption software selections to help you find the best one for your budget and business needs.
| Tool | Best For | Trial Info | Price | ||
|---|---|---|---|---|---|
| 1 | Best for team password management | 14-day free trial | From $2.99/user/month (billed annually) | Website | |
| 2 | Best for secure file storage | 30-day free trial | From $3.33/user/month (billed annually) | Website | |
| 3 | Best for business endpoint security | 30-day free trial + free demo available | From $338.50/year | Website | |
| 4 | Best for cloud storage encryption | Free plan available | From $3/user/month (billed annually) | Website | |
| 5 | Best for personal file encryption | Free plan available | From $2.99/month (billed annually) | Website | |
| 6 | Best for secure file encryption | 30-day free trial | From $39.70/license | Website | |
| 7 | Best for folder and drive locking | Free plan available | From $39.95/license | Website | |
| 8 | Best for open-source file compression | Not available | Free to use | Website | |
| 9 | Best for Windows file encryption | Free trial available | From $49.95/license | Website | |
| 10 | Best for creating hidden volumes | 30-day free trial | From $35/month (billed annually) | Website |
-

Docker
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.6 -

Pulumi
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.8 -

GitHub Actions
Visit Website
Best Encryption Software Reviews
Below are my detailed summaries of the best encryption software that made it onto my shortlist. My reviews offer a detailed look at the key features, pros & cons, integrations, and ideal use cases of each tool to help you find the best one for you.
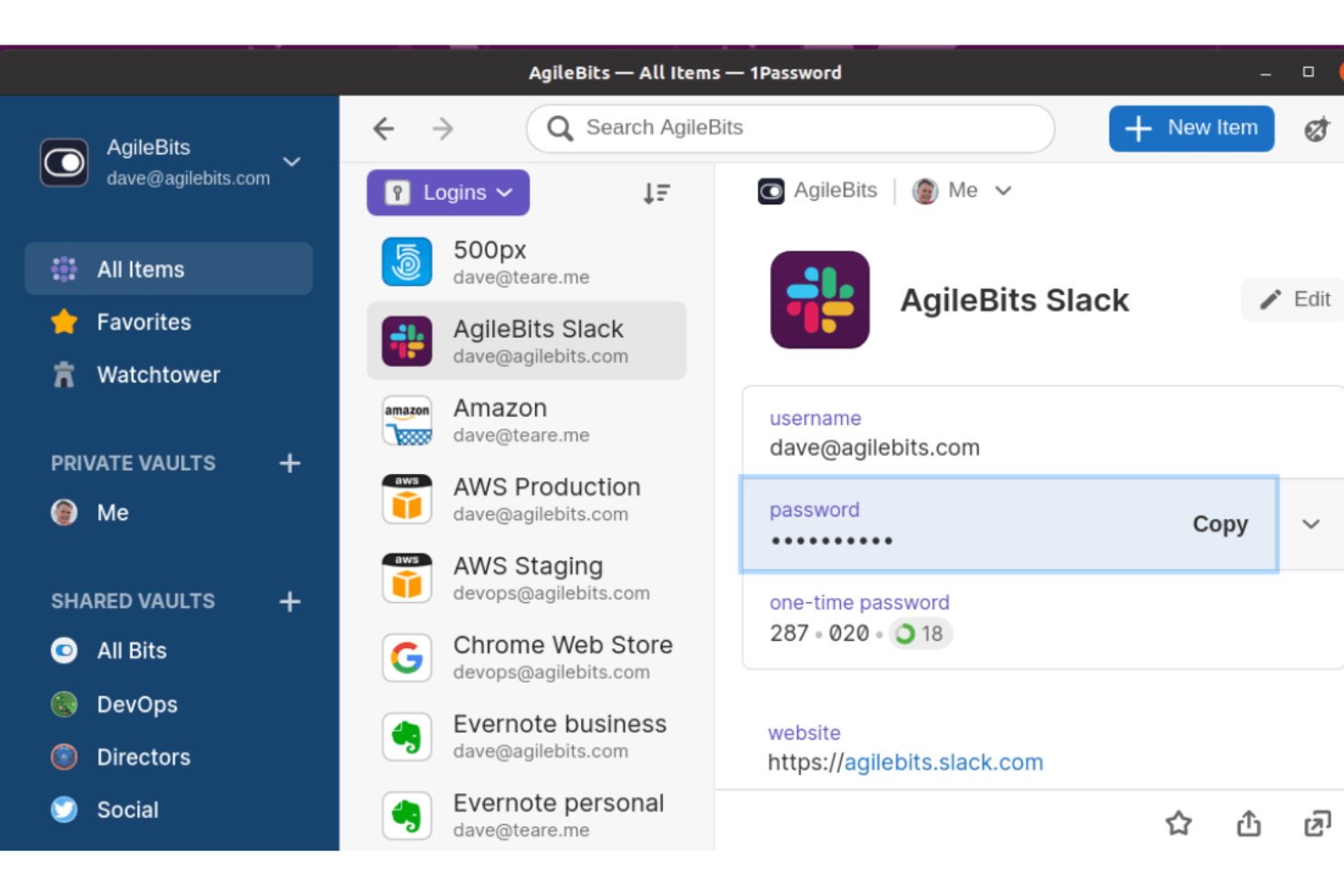
1Password is a password manager and encryption software mainly used by businesses to secure access to applications and devices. It supports various industries by focusing on secure access management, making it a key player in protecting sensitive information.
Why I picked 1Password: It stands out with its Extended Access Management (XAM), which secures all applications from any device, enhancing security in hybrid work environments. This feature extends single sign-on capabilities, mitigating vulnerabilities. Trusted by over 165,000 organizations, including IBM and Salesforce, 1Password offers reliable support and a high return on investment. Its role as the exclusive Cybersecurity Partner of Oracle Red Bull Racing highlights its commitment to data security.
Standout features & integrations:
Features include a secure password vault for storing sensitive information, two-factor authentication for added security, and password sharing for team collaboration. Admins can manage permissions and access, ensuring that only authorized users have access to critical data.
Integrations include Slack, Jira, GitHub, AWS, Dropbox, Google Workspace, Microsoft 365, Okta, Azure AD, and Zoom.
Pros and cons
Pros:
- High return on investment
- Trusted by major companies
- Extended access management
Cons:
- Complex setup for beginners
- Limited free plan options
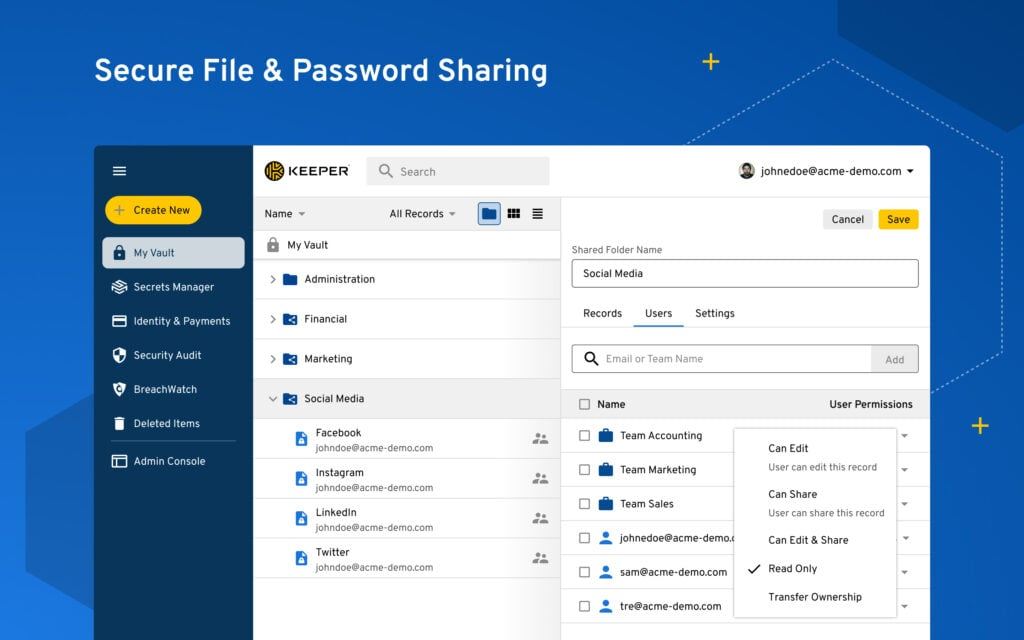
Keeper Security is a password manager and encryption software designed for businesses and individuals to securely store and manage passwords and sensitive files. Its primary users include IT teams and organizations focused on enhancing their data protection and access management.
Why I picked Keeper Security: It excels in secure file storage, providing a digital vault that encrypts files and passwords, ensuring only authorized access. You can easily organize and share files within your team while maintaining strict security protocols. It offers advanced reporting and auditing capabilities, allowing you to monitor access and changes in real-time. Keeper Security also includes a zero-knowledge architecture, meaning only you have access to your encrypted data, enhancing overall security.
Standout features & integrations:
Features include a user-friendly interface for easy password management, secure autofill for faster login processes, and a built-in password generator to enhance password strength. You can also benefit from emergency access, allowing trusted users to access your vault in critical situations.
Integrations include Microsoft 365, Google Workspace, Active Directory, Azure AD, Okta, Duo Security, Slack, Jira, Salesforce, and AWS.
Pros and cons
Pros:
- Real-time monitoring
- Advanced reporting features
- Zero-knowledge architecture
Cons:
- Some features need separate purchase
- Requires regular updates
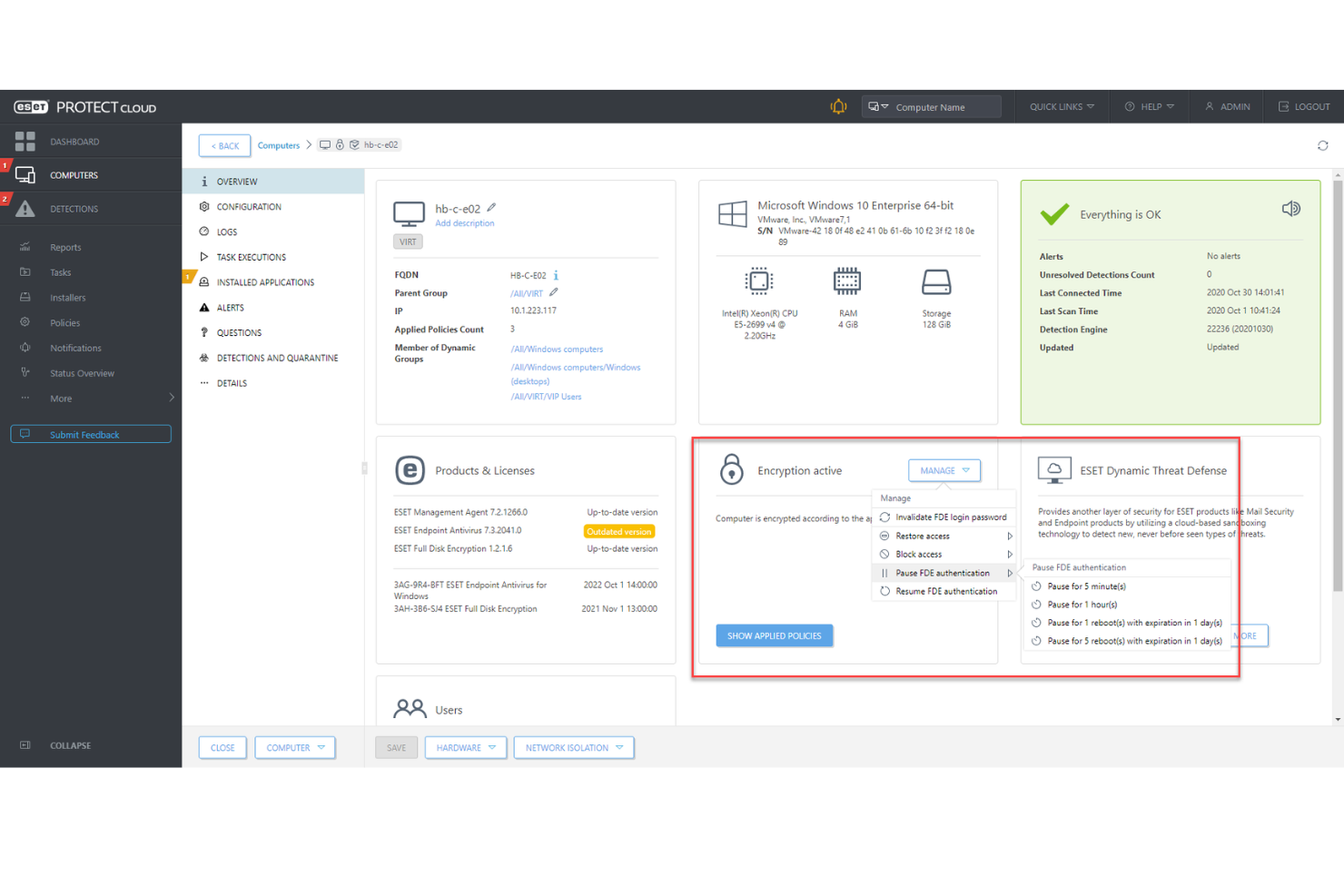
ESET PROTECT Complete is an endpoint security software designed for businesses to safeguard their network and devices. It primarily serves IT departments looking to manage and secure endpoints across their organization efficiently.
Why I picked ESET PROTECT Complete: It focuses on business endpoint security, providing comprehensive protection against malware and other threats. You can benefit from its advanced threat detection features, ensuring your network stays secure. It offers centralized management, allowing you to monitor and control all endpoints from a single console. Additionally, its cloud sandboxing feature provides an extra layer of security by analyzing suspicious files in a secure environment.
Standout features & integrations:
Features include real-time file and email scanning to detect potential threats before they cause harm. The software also provides detailed logging and reporting, giving you insights into security events and trends. Its device control feature helps you manage and restrict the use of external devices, reducing the risk of data breaches.
Integrations include Microsoft Azure, VMware, Amazon AWS, Google Cloud, Microsoft Outlook, Microsoft Exchange, IBM Domino, Citrix, Splunk, and ServiceNow.
Pros and cons
Pros:
- Cloud sandboxing feature
- Centralized management console
- Advanced threat detection
Cons:
- Complex for new administrators
- Can be resource-intensive
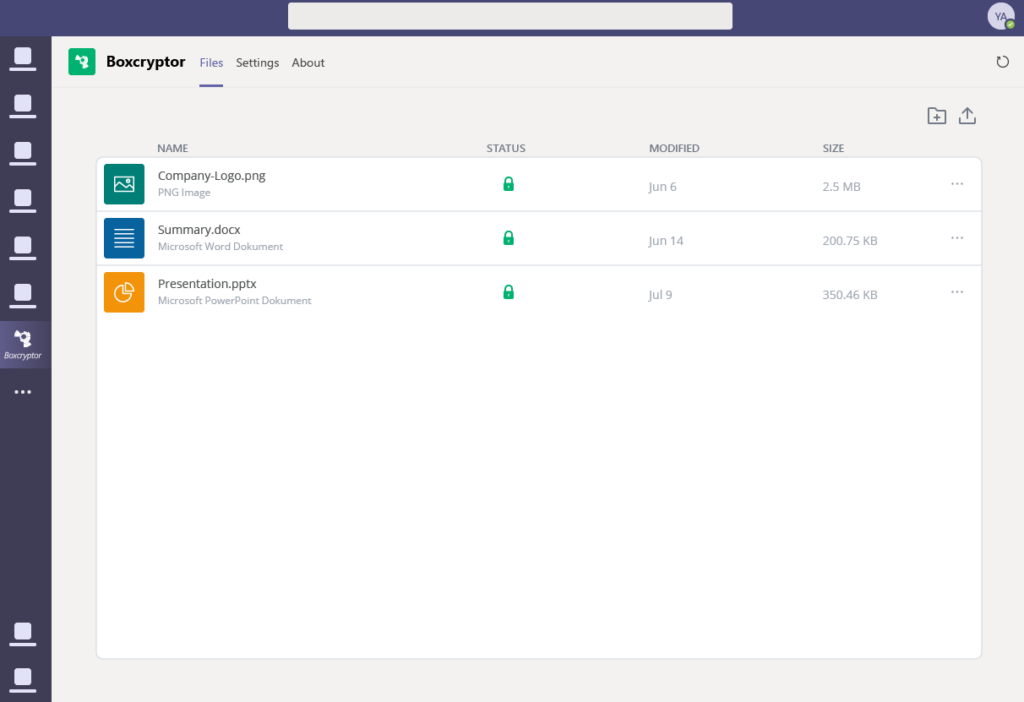
Boxcryptor is an encryption software designed for individuals and businesses to protect files stored in cloud services. It primarily serves users who need to secure their data across multiple cloud platforms, focusing on encryption and secure file sharing.
Why I picked Boxcryptor: It specializes in cloud storage encryption, providing end-to-end encryption for over 30 cloud services. You can encrypt files locally before uploading them to the cloud, ensuring data privacy. Boxcryptor supports collaboration by allowing you to securely share encrypted files with team members. Its zero-knowledge standard ensures that only you have access to your encryption keys, maintaining full control over your data.
Standout features & integrations:
Features include support for two-factor authentication to add an extra layer of security. The software allows for encrypted file sharing, enabling you to collaborate without compromising data integrity. Additionally, Boxcryptor offers cross-platform support, letting you access your encrypted files on various devices.
Integrations include Dropbox, Google Drive, Microsoft OneDrive, Box, SharePoint, Amazon S3, WebDAV, iCloud, Egnyte, and SugarSync.
Pros and cons
Pros:
- Supports multiple cloud services
- Local file encryption
- End-to-end encryption
Cons:
- May need additional setup
- Requires cloud service compatibility
NordLocker is a file encryption tool designed for individuals and small teams to secure their personal and business files. It focuses on encrypting data stored locally or in the cloud, providing a secure environment for sensitive information.
Why I picked NordLocker: It excels in personal file encryption, offering a user-friendly experience with its drag-and-drop interface. You can encrypt files on your computer and in the cloud, ensuring privacy across platforms. NordLocker uses end-to-end encryption, giving you confidence that your data remains private. With its zero-knowledge policy, only you have access to your encryption keys, maintaining complete control over your information.
Standout features & integrations:
Features include an intuitive drag-and-drop interface that simplifies the encryption process. The software offers automatic backup to the cloud, ensuring your files are always protected. NordLocker also provides cross-platform support, allowing you to access encrypted files on different devices.
Integrations include Dropbox, Google Drive, OneDrive, iCloud, and NordVPN.
Pros and cons
Pros:
- End-to-end encryption
- Easy drag-and-drop interface
- Automatic cloud backup
Cons:
- Can be costly for small teams
- Limited advanced features
CryptoForge is an encryption software designed for individuals and small businesses to secure sensitive files and information. It provides users with tools to encrypt, decrypt, and securely manage data, ensuring privacy and protection against unauthorized access.
Why I picked CryptoForge: It specializes in secure file encryption, offering a simple yet effective solution for protecting data. You can encrypt files with strong algorithms, ensuring your information remains confidential. The tool supports multiple encryption standards, providing flexibility in how you secure your files. Its lightweight design makes it easy to integrate into your daily workflow without consuming significant system resources.
Standout features & integrations:
Features include support for multiple encryption algorithms, allowing you to choose the level of security that suits your needs. The software provides a command-line interface for advanced users who prefer scripting. Additionally, CryptoForge offers a file shredder to permanently delete sensitive files, ensuring they cannot be recovered.
Integrations include Windows Explorer, making it easy to encrypt and decrypt files directly from your file manager.
Pros and cons
Pros:
- Command-line interface available
- Supports multiple encryption algorithms
- Lightweight and efficient design
Cons:
- Limited customer support options
- No cloud storage integration
Folder Lock is a security software designed to protect files, folders, and drives for individuals and small businesses. It provides users with tools to encrypt and secure sensitive data, ensuring privacy and protection against unauthorized access.
Why I picked Folder Lock: It excels in folder and drives locking, offering a range of security options like file encryption and password protection. You can lock files and folders to keep them hidden from unauthorized users. The tool also allows you to encrypt entire drives, ensuring comprehensive data security. Its stealth mode feature further enhances privacy by allowing you to hide the software itself from prying eyes.
Standout features & integrations:
Features include a secure backup option that lets you store encrypted files in the cloud. The software offers shredding capabilities to permanently delete sensitive files. Additionally, Folder Lock provides a wallet feature for storing personal information securely.
Integrations include Windows Explorer, allowing for easy file and folder management.
Pros and cons
Pros:
- Secure backup options
- Stealth mode feature
- Comprehensive drive encryption
Cons:
- Basic user interface
- Limited to Windows platform
7-Zip is a file compression and encryption tool widely used by individuals and businesses for managing file archives. It serves users looking for an efficient way to compress files and encrypt data, making it a valuable tool for storage and security.
Why I picked 7-Zip: It offers open-source file compression, providing a high compression ratio with its native 7z format. You can compress files to save space and encrypt them using strong AES-256 encryption for added security. Its open-source nature allows for community-driven improvements, ensuring it remains reliable. The tool supports multiple file formats, giving you flexibility in handling various types of data.
Standout features & integrations:
Features include a high compression ratio in 7z format, which helps reduce file sizes significantly. The software supports strong AES-256 encryption, ensuring your data stays secure. It also offers a file manager for easy navigation and management of compressed files.
Integrations include Windows Shell, allowing easy access through right-click menus.
Pros and cons
Pros:
- Open-source community-driven updates
- High compression ratio
- Supports multiple file formats
Cons:
- Requires manual updates
- Basic user interface
Kruptos 2 Professional is an encryption tool designed for Windows users to secure their files and folders. It primarily serves individuals and small businesses looking to protect sensitive data on their Windows devices.
Why I picked Kruptos 2 Professional: It is tailored for Windows file encryption, providing strong AES-256 encryption to secure your data. You can encrypt files and folders with ease, ensuring that unauthorized users cannot access your information. The tool also offers a password manager, helping you keep track of your encryption keys securely. Its simple interface makes it accessible to users with varying levels of technical expertise.
Standout features & integrations:
Features include the ability to create self-extracting encrypted files, allowing you to share secure data without requiring recipients to have the software installed. The software provides a file shredder to permanently delete sensitive files, ensuring they cannot be recovered. Kruptos 2 Professional also offers a secure notes feature, enabling you to encrypt and store important information safely.
Integrations include Windows Explorer, allowing easy access through right-click menus.
Pros and cons
Pros:
- Includes file shredder
- Strong AES-256 encryption
- Simple interface for all users
Cons:
- No cloud storage integration
- Limited to Windows devices
Rohos Disk Encryption is a tool designed to create encrypted virtual drives on your computer, primarily used by individuals and small businesses. It focuses on protecting sensitive data by creating hidden and encrypted volumes, ensuring privacy and security.
Why I picked Rohos Disk Encryption: It specializes in creating hidden volumes, allowing you to conceal sensitive data within your system. You can easily set up hidden partitions that remain invisible until you unlock them, providing an extra layer of privacy. Rohos also supports automatic encryption, ensuring your data is always protected without manual intervention. Its ability to encrypt USB drives extends its security features beyond just your computer.
Standout features & integrations:
Features include support for two-factor authentication, adding an additional security layer. The software offers portable encryption, allowing you to secure data on USB drives. Rohos Disk Encryption also provides a password manager, helping you keep track of your encryption keys securely.
Integrations include Windows Explorer, Microsoft Office, and USB devices.
Pros and cons
Pros:
- USB drive encryption
- Hidden volume creation
- Automatic encryption features
Cons:
- Some features need separate purchase
- Limited cross-platform support
Other Encryption Software
Here are some additional encryption software options that didn’t make it onto my shortlist, but are still worth checking out:
- Sophos SafeGuard Encryption
For enterprise data protection
- GnuPG (GNU Privacy Guard)
For email encryption
- CloudFlare
For web application security
- WebTitan
For content filtering
- Privacy Drive
For virtual disk encryption
- Advanced Encryption Package
For Windows file encryption
- ZixMail
For secure email communication
Encryption Software Selection Criteria
When selecting the best encryption software to include in this list, I considered common buyer needs and pain points like data security and ease of use. I also used the following framework to keep my evaluation structured and fair:
Core Functionality (25% of total score)
To be considered for inclusion in this list, each solution had to fulfill these common use cases:
- Encrypting files and folders
- Securing email communications
- Providing password protection
- Supporting multiple encryption algorithms
- Ensuring data integrity and confidentiality
Additional Standout Features (25% of total score)
To help further narrow down the competition, I also looked for unique features, such as:
- Integration with cloud storage services
- Support for end-to-end encryption
- Availability of portable encryption tools
- Advanced key management options
- Customizable encryption settings
Usability (10% of total score)
To get a sense of the usability of each system, I considered the following:
- Intuitive user interface
- Easy navigation and accessibility
- Minimal learning curve
- Clear instructions and prompts
- Responsive design across devices
Onboarding (10% of total score)
To evaluate the onboarding experience for each platform, I considered the following:
- Availability of training videos and tutorials
- Interactive product tours
- Access to comprehensive documentation
- Support for data migration
- Onboarding webinars and workshops
Customer Support (10% of total score)
To assess each software provider’s customer support services, I considered the following:
- 24/7 support availability
- Multiple support channels (email, phone, chat)
- Access to a knowledge base
- Responsiveness to inquiries
- Availability of support in multiple languages
Value For Money (10% of total score)
To evaluate the value for money of each platform, I considered the following:
- Competitive pricing compared to peers
- Availability of free trials or demos
- Scalability of pricing plans
- Inclusion of essential features in base plans
- Discounts for long-term commitments
Customer Reviews (10% of total score)
To get a sense of overall customer satisfaction, I considered the following when reading customer reviews:
- Overall satisfaction ratings
- Positive feedback on core functionality
- Critiques on usability and interface
- Comments on customer support experiences
- Recommendations from industry peers
How to Choose Encryption Software
It’s easy to get bogged down in long feature lists and complex pricing structures. To help you stay focused as you work through your unique software selection process, here’s a checklist of factors to keep in mind:
| Factor | What to Consider |
| Scalability | Ensure the software can grow with your needs. Consider user limits and data capacity for future expansion. |
| Integrations | Look for compatibility with your existing tools like cloud storage, email clients, and office software. |
| Customizability | Check if you can tailor encryption settings to fit your specific security policies and protocols. |
| Ease of Use | Evaluate the user interface and learning curve. A straightforward design can save time and reduce errors. |
| Budget | Align pricing with your financial plan. Consider long-term costs like updates and additional features. |
| Security Safeguards | Verify encryption strength and compliance with data protection regulations. Prioritize robust security protocols. |
| Support | Assess the availability of customer support. Opt for providers that offer 24/7 assistance and multiple contact channels. |
| User Feedback | Research reviews and testimonials to gauge real-world performance and user satisfaction. |
Trends in Encryption Software
In my research, I sourced countless product updates, press releases, and release logs from different encryption software vendors and email security software providers. Here are some of the emerging trends I’m keeping an eye on:
- Quantum-Resistant Encryption: As quantum computing advances, encryption software vendors are developing algorithms that can resist quantum attacks. This trend is crucial for future-proofing data security. Some vendors are already testing these algorithms to ensure their software remains secure.
- Zero-Knowledge Encryption: More tools are offering zero-knowledge encryption, where only users have access to their data. This trend ensures maximum privacy and security, as even the service provider can't access the encrypted information. It's becoming a key selling point for privacy-focused users.
- User-Centric Design: Encryption tools are evolving to offer more intuitive interfaces that simplify complex security tasks. This trend makes encryption accessible to non-technical users, encouraging broader adoption. Vendors are focusing on reducing the learning curve without compromising security.
- Cross-Platform Compatibility: There's a growing demand for encryption solutions that work across different operating systems and devices. This trend ensures that users can maintain security no matter where they access their data. Vendors are enhancing compatibility to meet this need.
- Integration with Blockchain: Some vendors are exploring blockchain technology to enhance data integrity and security. This trend leverages blockchain's decentralized nature to ensure that encrypted data remains tamper-proof, adding a layer of trust for users concerned about data breaches.
What Is Encryption Software?
Encryption software is a type of tool that secures data by converting it into unreadable code, accessible only to those with the correct decryption key. IT professionals, security experts, and businesses use these tools to protect sensitive information and ensure privacy.
Features like strong encryption algorithms, cross-platform compatibility, and zero-knowledge encryption help with maintaining data security, user privacy, and accessibility. Overall, these tools provide essential protection against unauthorized access and data breaches.
Features of Encryption Software
When selecting encryption software, keep an eye out for the following key features:
- Strong encryption algorithms: Protects data by converting it into secure code, ensuring only authorized access.
- Zero-knowledge encryption: Ensures that only you can access your data, maintaining maximum privacy.
- Cross-platform compatibility: Allows you to use the software across different devices and operating systems, enhancing accessibility.
- File and folder encryption: Secures individual files and folders, preventing unauthorized access to sensitive information.
- Full disk encryption: Protects entire drives, ensuring all stored data remains secure.
- User-friendly interface: Simplifies complex security tasks, making it accessible to users of all technical levels.
- Encryption key management: Provides tools to create, store, and manage encryption keys securely, essential for maintaining data integrity.
- Cloud integration: Allows secure encryption of cloud-stored data, protecting information in online environments.
- Data shredding: Permanently deletes sensitive files, ensuring they cannot be recovered or accessed.
- Customizable encryption settings: Lets you tailor security protocols to fit your specific needs, enhancing data protection.
Benefits of Encryption Software
Implementing encryption software provides several benefits for your team and your business. Here are a few you can look forward to:
- Data protection: Keeps sensitive information secure from unauthorized access by using strong encryption algorithms.
- Regulatory compliance: Helps meet industry regulations and standards by ensuring data privacy and security.
- Peace of mind: Provides confidence that your data is safe, reducing concerns about potential breaches.
- Enhanced privacy: Zero-knowledge encryption ensures that only you can access your data, maintaining confidentiality.
- Flexibility: Cross-platform compatibility allows you to protect data on various devices and operating systems.
- Cost efficiency: Prevents costly data breaches by securing information, potentially saving on damage control expenses.
- Increased trust: Builds trust with clients and partners by demonstrating a commitment to data security and privacy.
Costs and Pricing of Encryption Software
Selecting encryption software requires an understanding of the various pricing models and plans available. Costs vary based on features, team size, add-ons, and more. The table below summarizes common plans, their average prices, and typical features included in encryption software solutions:
Plan Comparison Table for Encryption Software
| Plan Type | Average Price | Common Features |
| Free Plan | $0 | Basic encryption, limited storage, and community support. |
| Personal Plan | $5-$25/user/month | File and folder encryption, multi-device support, and basic key management. |
| Business Plan | $25-$50/user/month | Full disk encryption, advanced key management, and centralized admin control. |
| Enterprise Plan | $50-$100/user/month | Customizable encryption policies, compliance tools, and dedicated support. |
Encryption Software: FAQs
Here are some answers to common questions about encryption software:
What is the hardest encryption to break?
AES 256-bit encryption is considered the strongest and most secure encryption standard available today. It’s widely used in various applications, including banking and military communications. When choosing encryption software, ensure it supports AES 256-bit to protect your data effectively.
What are the three different encryption methods?
The three most common encryption methods are symmetric encryption, asymmetric encryption, and hashing. Symmetric encryption uses the same key for encryption and decryption, while asymmetric uses a pair of keys. Hashing converts data into a fixed-size string, often used for data verification.
Can encryption software impact system performance?
Yes, encryption software can affect system performance, especially during data encryption and decryption processes. However, most modern tools are optimized to minimize this impact. It’s crucial to choose software that balances security with performance to avoid slowing down your operations.
How do I choose the right encryption software for my needs?
To choose the right encryption software, consider factors like scalability, integration capabilities, and ease of use. Assess your specific security requirements and budget. Look for software that offers strong encryption standards and features that align with your business needs.
Is it necessary to encrypt all data?
Not all data requires encryption, but sensitive information like financial records, personal details, and proprietary business data should be encrypted. Prioritize encrypting data that, if compromised, could lead to significant harm or compliance issues.
What should I do if I forget my encryption key?
If you forget your encryption key, you may lose access to your encrypted data. Some software offers key recovery options or backup solutions. Always securely store your keys and consider using password manager software to keep track of them.
What's Next?
Boost your SaaS growth and leadership skills.
Subscribe to our newsletter for the latest insights from CTOs and aspiring tech leaders.
We'll help you scale smarter and lead stronger with guides, resources, and strategies from top experts!