10 Best Digital Forensics Software
Here's my pick of the 10 best software from the 24 tools reviewed.
Our one-on-one guidance will help you find the perfect fit.
Navigating the intricate world of computer forensics, I've come to realize the invaluable role digital forensics software plays. By sifting through digital evidence, it becomes a formidable shield against malware, ensuring the integrity of operating systems and bolstering our overall cybersecurity posture. Imagine a tool that extracts and analyzes digital data, presenting a clearer picture amidst the chaos.
This software not only safeguards your digital assets but alleviates the daunting challenges of uncovering malicious activities and securing sensitive data. It's essential gear for anyone venturing into the vast realm of digital investigations.
What Is Digital Forensics Software?
Digital forensics software is a specialized suite of tools designed to extract, analyze, and preserve digital evidence from various electronic devices and platforms. Used predominantly by law enforcement, cybersecurity professionals, and corporate investigators, this software aids in investigating incidents ranging from data breaches to cybercrimes, ensuring a meticulous and systematic approach to uncovering and presenting digital artifacts in scenarios where the integrity and authenticity of information are paramount.
Best Digital Forensics Software Summary
| Tool | Best For | Trial Info | Price | ||
|---|---|---|---|---|---|
| 1 | Best for mobile and cloud evidence recovery | Not available | Pricing upon request | Website | |
| 2 | Best for comprehensive digital investigations | Not available | Pricing upon request | Website | |
| 3 | Best for domain and DNS-based research | Not available | Pricing upon request | Website | |
| 4 | Best for security event and log management | Free demo available | Pricing upon request | Website | |
| 5 | Best for rapid incident response | Not available | Pricing upon request | Website | |
| 6 | Best for extracting digital artifacts | Not available | Pricing upon request | Website | |
| 7 | Best for on-site mobile data extraction | Not available | Pricing upon request | Website | |
| 8 | Best for unified digital forensics operations | Not available | Pricing upon request | Website | |
| 9 | Best for email analysis and recovery | Not available | Pricing upon request | Website | |
| 10 | Best for real-time network activity insights | Not available | Pricing upon request | Website |
-

Docker
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.6 -

Pulumi
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.8 -

GitHub Actions
Visit Website
Best Digital Forensics Software Reviews
Magnet AXIOM is a comprehensive tool designed to aid computer forensic examiners in retrieving evidence from a variety of digital platforms, particularly mobile phones and cloud environments. Given its specialization in these areas, it truly shines when tasked with mobile and cloud evidence recovery.
Why I Picked Magnet AXIOM:
In my quest to find the most efficient software tools, I compared numerous options. Magnet AXIOM stood out distinctly, not just due to its acclaimed reputation, but also because of its pinpointed functionality that caters to both mobile and cloud platforms. This tool, in my judgment, rightfully earns its title for being the best in mobile and cloud evidence recovery.
Standout Features and Integrations:
Magnet AXIOM excels in providing detailed timeline analysis, allowing examiners to trace back activities on a device or account comprehensively. Additionally, its adeptness in retrieving internet history, even from mobile phones, proves invaluable.
Integrations with major cloud service providers and popular mobile phone operating systems further enhance its utility.
Pros and cons
Pros:
- Noteworthy integrations with cloud platforms and mobile OS.
- Proficient in retrieving internet history from various devices, especially mobile phones.
- Detailed timeline analysis ensures comprehensive insight.
Cons:
- Reliance on continuous updates to support the latest mobile OS versions.
- Some advanced features could be overwhelming.
- Might have a steeper learning curve for beginners.
OpenText EnCase Forensic is a renowned tool that empowers professionals to undertake extensive digital investigations, delving into hard drives, smartphones, and a plethora of other devices. Recognized for its ability to conduct holistic investigations, it stands out as the top choice for comprehensive digital exploration tasks.
Why I Picked OpenText EnCase Forensic:
In my journey of selecting and comparing forensic tools, EnCase Forensic caught my attention due to its expansive capabilities. I determined that when it comes to thorough investigations across diverse digital platforms, this tool has an edge. Its breadth of features and device compatibility firmly positions it as 'best for comprehensive digital investigations.'
Standout Features and Integrations:
EnCase Forensic boasts a suite of features that allow professionals to probe deep into both open-source and proprietary systems. This robust analysis tool is also adept at handling data from smartphones and various mobile devices, ensuring a wide range of electronic evidence can be accessed and assessed.
Key integrations of EnCase Forensic include popular operating systems and a variety of file systems, fostering its ability to gather comprehensive digital evidence.
Pros and cons
Pros:
- Extensive integrations with popular operating systems.
- Can navigate both open-source and proprietary platforms.
- Broad device compatibility, including hard drives and mobile devices.
Cons:
- Could be considered pricey compared to more niche forensic tools.
- Initial setup may require expert knowledge.
- Might be overwhelming for beginners given its range of features.
DomainTools is a comprehensive platform dedicated to providing insights and research on domain names and DNS records. Tailored for those who require deep dives into domain-related metadata, it's the go-to for individuals and organizations focused on domain and DNS-based research.
Why I Picked DomainTools:
During my evaluation of various platforms, choosing DomainTools became evident. This decision was rooted in its singular focus on domain and DNS data. Its unparalleled ability to extract metadata and present it in an accessible manner was unmatched, emphasizing why I deemed it 'best for domain and DNS-based research.'
Standout Features and Integrations:
DomainTools is renowned for its exhaustive domain metadata extraction. It serves as a robust network forensic tool, allowing users to pinpoint vulnerabilities, and offering an edge in cybersecurity research. The tool has proven its mettle in integrating with a multitude of platforms, including Android systems, ensuring broader applicability.
Pros and cons
Pros:
- Wide integration, including with Android platforms.
- Strong network forensic features to detect vulnerabilities.
- Deep domain metadata extraction capabilities.
Cons:
- Real-time updates or alerts might not be instantaneous.
- The user interface may seem complex for beginners.
- Might require some time to familiarize yourself with its plethora of features.
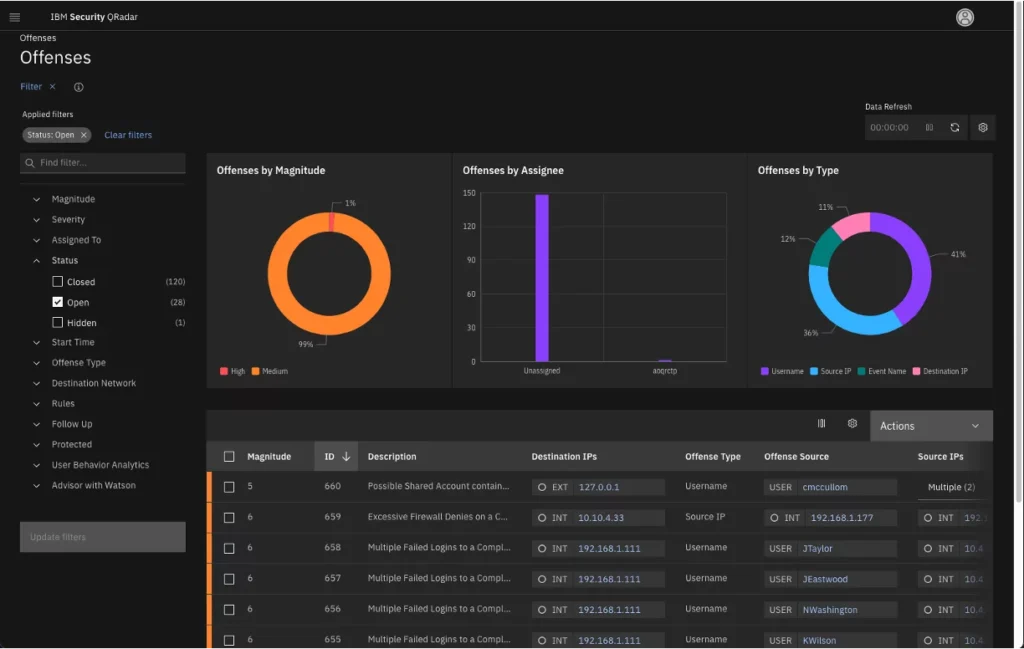
IBM Security QRadar SIEM is a robust platform designed to manage and analyze security events and logs from various sources. Its capabilities to effectively organize and interpret vast amounts of security data make it a premier choice for log management.
Why I Picked IBM Security QRadar SIEM:
In my journey of selecting tools for inclusion, QRadar consistently emerged at the forefront. Its features, compared to other offerings, showed clear advantages in the realm of security event and log management. I chose this tool, based on its comprehensive features and the opinion of industry experts, as the best for security events and log management.
Standout Features and Integrations:
IBM Security QRadar SIEM excels in correlating disparate sets of data, identifying potential security threats before they escalate. Its advanced analytics capabilities allow for a deeper dive into security events, pinpointing anomalies with precision. On the integration front, QRadar incorporates a wide range of third-party security tools, bolstering its analytical prowess.
Pros and cons
Pros:
- A broad range of integrations with third-party security tools.
- Advanced analytics capabilities for pinpointing threats.
- Comprehensive correlation of security data from various sources.
Cons:
- Requires periodic tuning to remain optimally effective.
- The sheer amount of data may require significant storage solutions.
- Can be complex to set up initially.
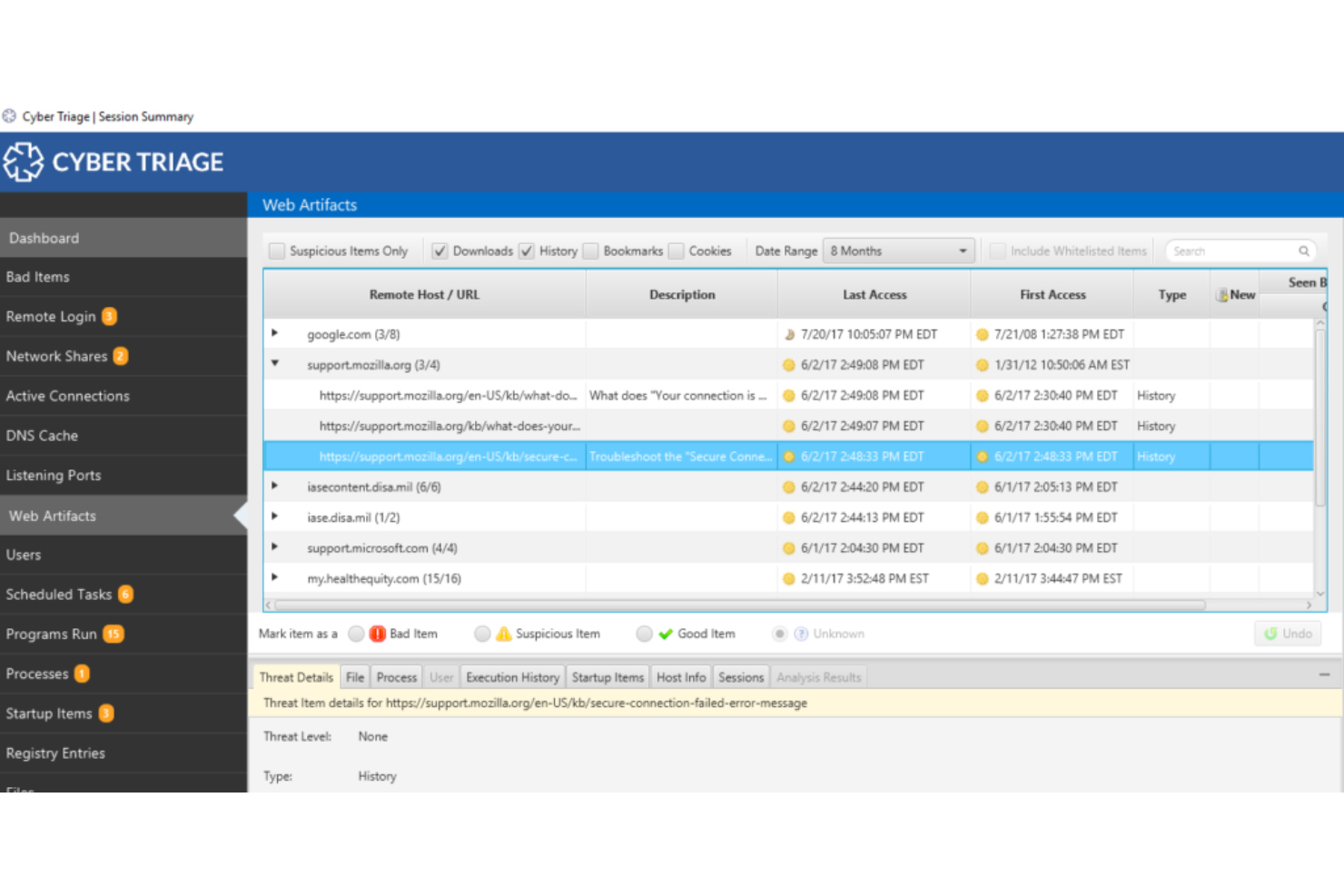
Cyber Triage focuses on providing efficient tools for incident response by diving deep into memory analysis and integrating threat intelligence. Catering specifically to incidents where time is of the essence, this tool lives up to its reputation as the optimal solution for rapid response.
Why I Picked Cyber Triage:
In determining the tools for this list, I diligently compared various options and assessed their capabilities. I chose Cyber Triage because its emphasis on speed and thoroughness is evident.
After judging its functionalities and hearing opinions from peers, it's clear that Cyber Triage stands out, especially when rapid incident response is paramount.
Standout Features and Integrations:
One of Cyber Triage's most valuable features is its robust memory analysis, which allows users to delve into the intricacies of an incident swiftly. The tool also offers mobile forensics capabilities, expanding its reach beyond traditional systems. Its integration with Microsoft and open-source tools enhances its versatility, making it a favored choice among professionals.
Pros and cons
Pros:
- Strong integration with Microsoft and various open-source tools.
- The mobile forensics feature provides broader applicability.
- In-depth memory analysis facilitates a deeper understanding of incidents.
Cons:
- Reliance on third-party integrations for some functionalities.
- Not all features might be intuitive for novice users.
- May require specialized training for full utility.
In the complex landscape of digital forensics, Belkasoft Evidence Center emerges as a robust tool designed primarily to remove a wealth of digital artifacts. Its specialized functionalities make it an impeccable choice for professionals aiming to dive deep into forensic data.
Why I Picked Belkasoft Evidence Center:
In my journey of sifting through various tools, selecting Belkasoft was a clear decision based on its unique capabilities. My determination hinged on its unparalleled prowess in extracting nuanced digital artifacts from computer systems. Its emphasis on meticulous artifact extraction convinced me that it’s the 'best for extracting digital artifacts.'
Standout Features and Integrations:
Belkasoft shines with its advanced forensic data extraction capabilities. It excels in memory forensics, allowing examiners to retrieve crucial data that many other tools might overlook. In addition, it offers forensic imaging, a vital feature for preserving evidence in its original state. Its platform integrates efficiently with several prominent computer systems, ensuring a wide range of compatibility.
Pros and cons
Pros:
- Efficient forensic imaging feature for evidence preservation.
- Advanced memory forensics capabilities.
- Comprehensive focus on digital artifact extraction.
Cons:
- Potential hidden costs for additional modules or advanced training.
- The breadth of features might seem daunting initially.
- A learning curve may be present for newcomers.
Cellebrite functions as a powerful computer-aided investigative environment, designed explicitly to facilitate the extraction of mobile data swiftly and effectively. Its prowess in on-site mobile data retrieval makes it invaluable for scenarios demanding immediate extraction.
Why I Picked Cellebrite:
When selecting a tool for my list, especially for mobile data extraction, Cellebrite's reputation was undeniable. Comparing its features and real-world application, I determined that it has a distinct edge in on-site operations. I hold the opinion that Cellebrite is, undeniably, the best for on-site mobile data extraction based on its precision and speed.
Standout Features and Integrations:
Cellebrite boasts a range of features tailored for immediate on-site extraction, ensuring that investigators have timely access to crucial data. Its compatibility with a wide variety of mobile devices ensures that extraction is possible regardless of the device brand or operating system.
In terms of integrations, Cellebrite works effectively with other investigative platforms, amplifying the depth and breadth of any investigation.
Pros and cons
Pros:
- Effective integrations with other investigative platforms.
- High compatibility with a vast range of mobile devices.
- Robust computer-aided investigative environment.
Cons:
- Initial setup and calibration can be time-consuming.
- Hardware components might need frequent updates for newer devices.
- Requires specialized training for optimal usage.
Detego Global is at the forefront of streamlining digital forensics, offering tools and functionalities that unify operations from endpoint to endpoint. Its unified approach makes it particularly suited for those looking to consolidate their digital forensics procedures, maximizing efficiency and clarity.
Why I Picked Detego Global:
During my evaluation of numerous forensics tools, Detego Global resonated with me for its comprehensive, integrated approach. When determining the most effective tool for a holistic forensics workflow, Detego stood apart.
I judged its all-encompassing suite as the 'best for unified digital forensics operations' due to its ability to connect various aspects of the digital investigation process.
Standout Features and Integrations:
Detego Global boasts a wide range of features tailored for forensic professionals, from handling volatility in digital evidence to efficient endpoint analysis. The platform integrates with both Mac and Windows operating systems, ensuring a smooth investigative experience. Additionally, its app-focused features offer insights into application-based evidence, broadening its utility.
Pros and cons
Pros:
- Specialized features for app-based evidence extraction.
- Strong integration with major operating systems like Mac and Windows.
- Comprehensive endpoint analysis capabilities.
Cons:
- Potential for additional costs for advanced integrations or features.
- The vast suite of tools could be overwhelming initially.
- Might require some training for novice users.
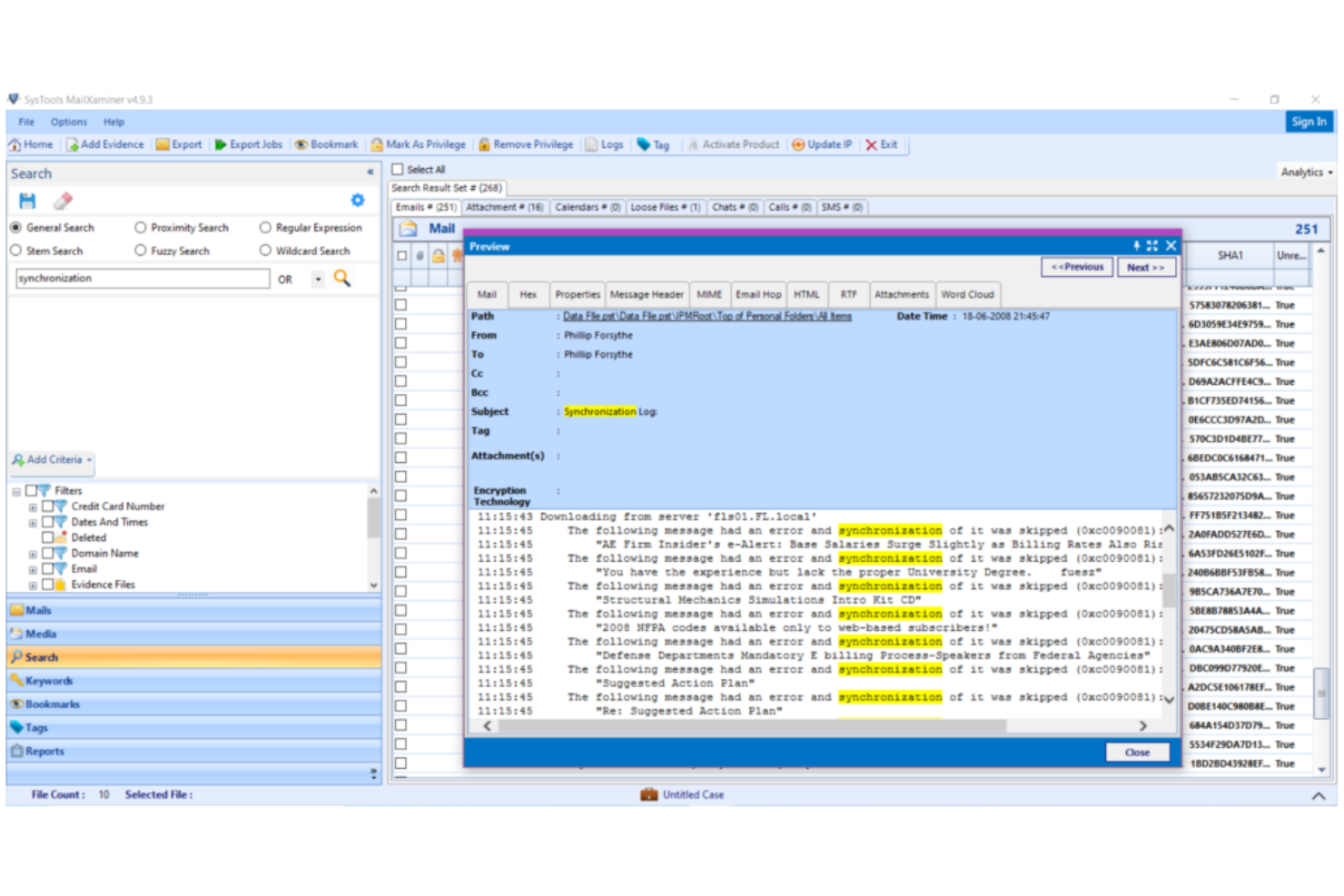
MailXaminer is a dedicated tool designed to unlock the complexities of email data for forensic investigators. Tailored to specialize in the extraction, research, and recovery of email content, it's no wonder I've tagged it as the best in its niche for email-centric tasks.
Why I Picked MailXaminer:
In the realm of digital forensics, email often holds a trove of crucial evidence. MailXaminer stands out in its commitment to dive deep into this specific area, ensuring detailed email analysis and recovery.
When comparing its capabilities with other tools, it was clear to me that for email-based forensic investigations, MailXaminer has an edge.
Standout Features and Integrations:
Equipped with a suite of powerful features, MailXaminer can navigate various email formats, providing investigators with comprehensive insights. Its advanced search capabilities paired with decryption support are game-changers for examiners.
Moreover, its smooth integration with the Windows operating system ensures a consistent and user-friendly experience.
Pros and cons
Pros:
- Supports a wide variety of email formats.
- Offers extensive decryption techniques.
- Exclusively designed for email-centric forensic investigations.
Cons:
- Might lack integrations available in more comprehensive forensics solutions.
- Might present a learning curve for those unfamiliar with forensic tools.
- Specific to email data, not suitable for broader digital investigations.
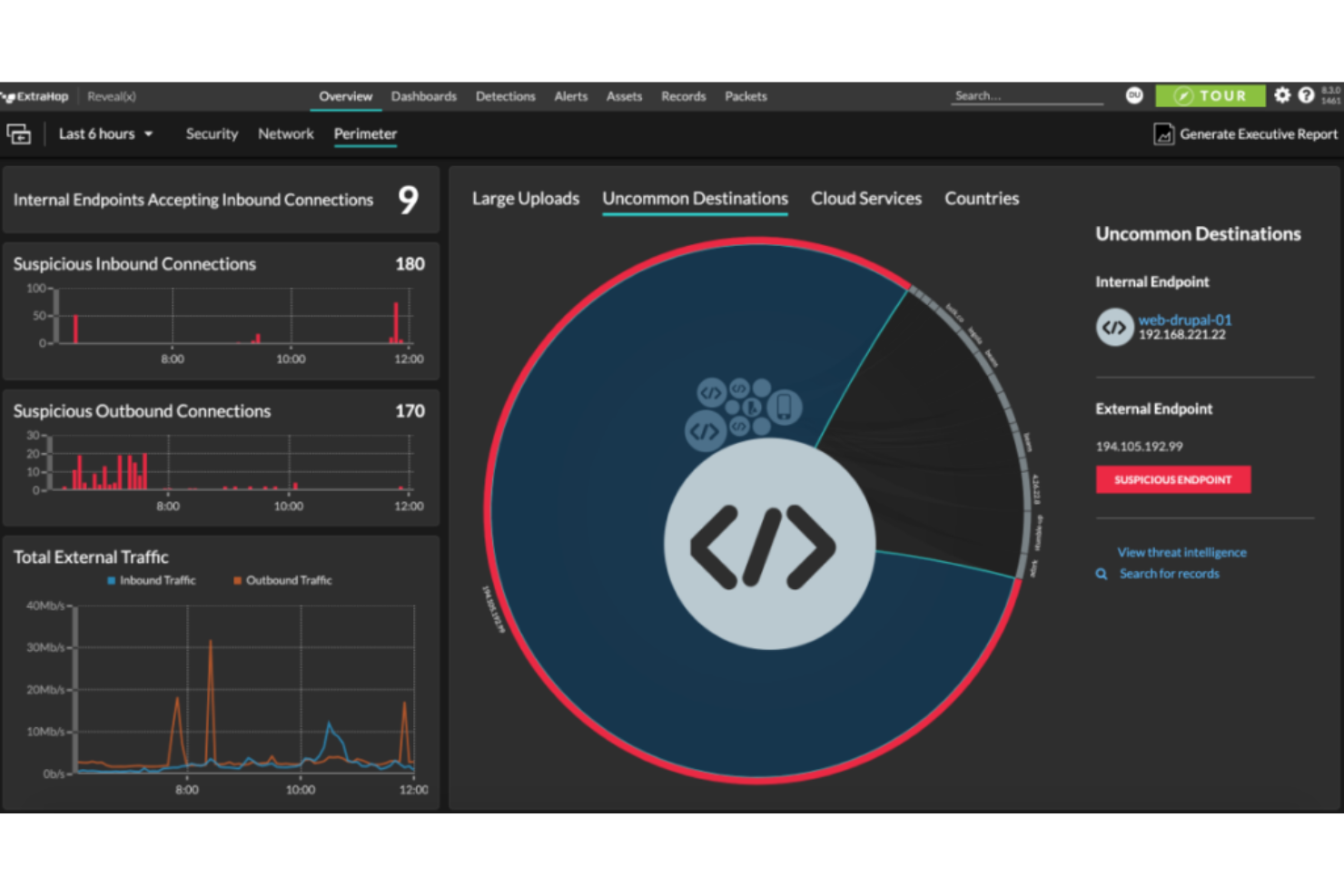
ExtraHop is a distinguished tool offering in-depth monitoring and insights into real-time network activities. With its advanced graphical interface, it simplifies the complex task of tracking network anomalies, proving it is exceptionally suited for providing real-time network activity insights.
Why I Picked ExtraHop:
When selecting tools, I always keep the user's needs at the forefront. I chose ExtraHop because of its distinctive capacity to provide real-time insights via a user-friendly graphical interface. Among the plethora of tools I compared, ExtraHop resonated with me due to its unique focus on live network analysis, and in my judgment, it is undeniably 'best for real-time network activity insights.'
Standout Features and Integrations:
ExtraHop boasts a state-of-the-art graphical interface that makes malware analysis feasible and intuitive. The platform is optimized for various systems, including macOS, making it accessible to diverse user bases.
Additionally, its integration capabilities are noteworthy, especially its collaborations with IoT platforms and its utility for law enforcement agencies.
Pros and cons
Pros:
- Robust integrations with IoT platforms and utility for law enforcement agencies.
- Broad compatibility including support for macOS.
- The intuitive graphical interface simplifies malware analysis.
Cons:
- Some custom integrations might necessitate additional configurations.
- Advanced features require a steeper learning curve.
- The initial setup might be intricate for some users.
Other Digital Forensics Software
Below is a list of additional digital forensics software that I shortlisted, but did not make it to the top 10. They are definitely worth checking out.
- Imperva Attack Analytics
For identifying large-scale attack campaigns
- FTK Forensic Toolkit
For advanced data recovery
- Autopsy Digital Forensics
Good for detailed digital investigations
- Wireshark
Good for network protocol analysis
- OSForensics
Good for rapid digital forensic discovery
- Aware
Good for forensic research and compliance
- CYREBRO
Good for cybersecurity and forensic analysis
- Parrot Security
Good for ethical hacking and pen testing
- Sleuth Kit
Good for open-source forensic investigations
- Binalyze AIR
Good for automated incident response
- Oxygen Forensic Detective
Good for mobile data extractions
- PALADIN
Good for OS-based forensic acquisition
- Paraben E3 Universal
Good for comprehensive digital evidence examination
- Sandblast Threat Extraction
Good for advanced threat defense
Selection Criteria For Choosing Digital Forensics Software
When diving into the world of forensic and cybersecurity software, choosing the right tool can be daunting. The market is flooded with a plethora of options, each claiming superiority. Having tested and evaluated dozens of these tools, I focused my attention on a specific set of functionalities and features essential for professionals in the field. Below are the criteria I deem paramount when selecting the best-fit software for this niche.
Core Functionality
- Data extraction: Ability to pull information from a wide range of devices and platforms
- Analysis capability: Decoding, interpreting, and presenting data in a comprehensible manner
- Reporting: Generating detailed and accurate forensic reports for legal or investigative purposes
- Real-time monitoring: Continuous surveillance for instant threat detection and response
Key Features
- Multi-device compatibility: Ensures the tool works across different devices, including mobile phones, computers, and cloud storage
- Encryption handling: The ability to decrypt or bypass encrypted data, especially critical for accessing protected information
- Timeline analysis: Visualization of events in chronological order for a better understanding of incidents
- Artifact recovery: Extracting hidden or deleted data fragments that can be crucial evidence
- Advanced search capabilities: Swiftly locating specific data points amidst vast volumes of information
- Integration with other forensic tools: Augments the software's functionality and broadens its utility
Usability
- Intuitive dashboard: A well-organized central hub that presents crucial data and actions without overwhelming the user
- Workflow efficiency: Tools should support a logical flow of tasks, minimizing redundant steps in the forensic process
- Customizable interface: Adaptable to individual user preferences or specific case requirements
- Comprehensive documentation: A robust knowledge base or learning library for users to refer to, ensuring they can fully utilize the tool's capabilities
- Prompt customer support: Responsive and knowledgeable support teams ready to assist with complex issues or queries
- Role-based access: Clear and easy-to-configure user roles ensuring that sensitive data is only accessible to authorized personnel
Most Common Questions Regarding Digital Forensics Software (FAQs)
What are the benefits of using digital forensics software?
Digital forensics software offers several advantages:
- Detailed data analysis: These tools can sift through vast amounts of data, identifying, extracting, and presenting crucial evidence.
- Enhanced investigation capabilities: Users can uncover hidden or deleted data, like exif metadata from images, which can be pivotal in cybercrime investigations.
- Time efficiency: Automated processes and advanced search functions speed up investigations.
- Comprehensive reporting: Detailed reports generated can be used for legal proceedings or to inform cybersecurity strategies.
- Integration and compatibility: Many tools, such as The Sleuth Kit, can integrate with other software or operate on various platforms, like Linux or Ubuntu, increasing their utility.
How much do digital forensics tools typically cost?
The pricing of digital forensics software varies widely based on its capabilities, brand, and target audience. Some tools are designed for individual enthusiasts, while others cater to large organizations or law enforcement agencies.
What are the common pricing models for these tools?
There are several pricing models in the digital forensics software market:
- One-time purchase: Pay a lump sum upfront for lifetime access.
- Subscription-based: Monthly or annual payments.
- Freemium: Basic features are free, with advanced functionalities available for a fee.
- Open-source: Free to use and modify, like CAINE, which runs on Linux.
What is the typical price range for these tools?
Pricing can range from free for open-source tools or freemium models, to several thousand dollars for advanced enterprise-level solutions. The cost typically reflects the tool’s capabilities, user interface, support, and updates.
Which are some of the cheapest and most expensive software in this category?
The cheapest options usually include open-source tools like The Sleuth Kit or CAINE, both based on Linux. On the other hand, enterprise-level solutions with extensive functionalities and continuous updates can be among the priciest, often requiring customized quotes based on the needs of the organization.
Are there any free tool options available?
Yes, there are several free tools available. Open-source tools such as CAINE, which is a Linux-based solution, or SIFT, built on Ubuntu, are freely available. Additionally, software like The Sleuth Kit offers a robust set of features without any associated cost.
Other Cybersecurity Management Software Reviews
Summary
Navigating the world of digital forensics software can be a complex task, given the numerous choices and varied functionalities each tool offers. This guide aims to streamline that process by highlighting top-notch tools and laying out the crucial criteria you should consider when making your selection. Ensuring your chosen software aligns with your specific needs and has the requisite features, will ensure the tool not only aids in investigations but optimizes the process.
Key Takeaways
- The core functionality is crucial: The primary functions of your digital forensics software should cater to your investigative needs, whether that's mobile data extraction, timeline analysis, or internet history probing.
- User experience matters: A tool with a host of features is of little use if it isn't user-friendly. Look for intuitive designs, easy onboarding processes, and responsive customer support to make your forensic analysis smoother and more efficient.
- Cost and value proposition: While pricing is an essential factor, focusing solely on the cheapest tool might not offer the best value. Ensure that the software you select provides the functionalities you need at a price point that offers genuine value for money. Consider free tools like CAINE and The Sleuth Kit, especially if they align well with your requirements.
What Do You Think?
While I've done my best to curate a comprehensive list of digital forensics software, the tech landscape is vast and ever-evolving. If you've come across a tool that you believe deserves a spot on my list or have had exceptional experiences with one not mentioned, I'd love to hear from you.
Your insights not only enrich my guide but also help my community make more informed decisions. So, please, share your recommendations, and let's keep this conversation going!