12 Best Vulnerability Scanning Tools Shortlist
After carefully testing dozens of the top vulnerability scanning tools, I’ve found the following 12 best at solving cybersecurity challenges.
- Nessus - Best for comprehensive vulnerability scanning
- OpenVAS - Best for open-source vulnerability management
- Wireshark - Best for network protocol analysis
- QualysGuard - Best for cloud-based security and compliance
- Nexpose - Best for integrating with incident response
- Nikto - Best for identifying web server vulnerabilities
- Acunetix - Best for web application security testing
- Nmap - Best for network discovery and mapping
- Tripwire - Best for integrity monitoring and compliance
- Burp Suite - Best for web security analysis and auditing
- ZAP (Zed Attack Proxy) - Best for automated security testing
- GFI LanGuard - Best for network security management and patching
In the ever-evolving landscape of cybersecurity, hackers are relentlessly searching for types of vulnerability, exploiting misconfigurations, and finding ways to penetrate IT infrastructure. Vulnerability scanning tools are a tenable management solution that provides both automated vulnerability assessment and authenticated security scans, targeting everything from endpoint devices to web application vulnerability areas.
They efficiently minimize the attack surface by identifying weaknesses within your system, drawing from an extensive vulnerability database. Whether utilizing an open-source vulnerability scanner or a more robust security scanner, these tools are essential in safeguarding your digital assets. The benefits are clear: they empower organizations to pinpoint vulnerabilities before they can be exploited. The main pain points they address are the potential gaps in security, providing proactive protection, and peace of mind. If you’re serious about securing your digital landscape, exploring these tools is a must.
What is a Vulnerability Scanning Tool?
Vulnerability scanning tools are specialized software applications designed to identify computer system, network, or software application weaknesses. These tools are commonly utilized by cybersecurity professionals, IT administrators, and developers to detect and evaluate security holes that could be exploited by malicious actors.
By scanning for known vulnerabilities, the tools enable organizations to understand their risk exposure and implement necessary security measures. This proactive approach to security helps safeguard sensitive data and maintain compliance with regulatory standards, thus forming a critical aspect of modern cybersecurity practices.
Overview of the 12 Best Vulnerability Scanning Tools
1. Nessus - Best for comprehensive vulnerability scanning
Nessus is a highly recognized tool in the cybersecurity world, designed to provide comprehensive vulnerability scanning across networks, systems, and applications. Its robust capabilities in scanning for vulnerabilities and weaknesses make it a leading choice among professionals who need a complete security overview. This aligns perfectly with its reputation as the best for comprehensive vulnerability scanning.
Why I Picked Nessus:
I chose Nessus after closely evaluating its extensive set of features and its ability to perform accurate scans across various platforms. Its adaptability to different environments and commitment to detailed reporting make it stand out among its peers. Nessus proves itself as the best for comprehensive vulnerability scanning, providing in-depth insights into potential risks and assisting in effective remediation strategies.
Standout Features & Integrations:
Nessus offers an impressive range of features, including customizable templates for specific compliance standards, live results, and advanced visualizations for quick risk assessment. Its ability to integrate with a multitude of platforms adds to its broad utility. Integrations include prominent security solutions and incident response platforms, allowing for a more streamlined workflow and facilitating collaboration within security teams.
Pricing:
From $2,790 per scanner per year (billed annually)
Pros:
- Broad range of scanning capabilities
- Integrates with many third-party systems
- Customizable reporting and templates
Cons:
- Can be complex for beginners
- Annual billing may not suit all budgets
- Limited community support for the commercial version
2. OpenVAS - Best for open-source vulnerability management

OpenVAS stands out as an open-source tool designed for vulnerability scanning and management. Its commitment to providing a flexible and transparent security solution is what truly makes it an excellent choice for those who value open-source methodologies. It's no wonder OpenVAS is recognized as the best for open-source vulnerability management, aligning with the principles of community-driven security enhancements.
Why I Picked OpenVAS:
I chose OpenVAS for its distinctive open-source framework and commitment to transparent security processes. It differentiates itself by actively engaging a community of developers and security experts to refine and expand its functionalities continually. OpenVAS rightfully earns its title as the best for open-source vulnerability management by allowing full customization and adaptation to specific security requirements without the constraints of commercial licensing.
Standout Features & Integrations:
OpenVAS features a comprehensive and regularly updated database of Network Vulnerability Tests (NVTs), along with highly customizable scanning profiles. Its modular architecture allows users to add or modify functionalities according to their needs. OpenVAS can integrate with other open-source tools and provides APIs for developers to create custom connections with proprietary systems.
Pricing:
Free (open-source)
Pros:
- Community-driven development
- Highly customizable and adaptable
- Extensive library of Network Vulnerability Tests
Cons:
- Might require technical expertise for customization
- Community support might vary in quality
- Integration with proprietary systems might need manual configuration
3. Wireshark - Best for network protocol analysis
Wireshark is a prominent tool used for monitoring and analyzing network traffic. Its ability to dissect network protocols and present data in an understandable format makes it an essential tool for network engineers and cybersecurity professionals. Being best for network protocol analysis, Wireshark offers deep insights into network behavior and potential vulnerabilities.
Why I Picked Wireshark:
I chose Wireshark for its powerful capabilities in decoding numerous network protocols and its well-earned reputation as a go-to tool for network diagnostics. Its distinctive feature set, including live data capture and offline analysis, sets it apart from other tools in the market. I found Wireshark to be best for network protocol analysis due to its comprehensive set of features that facilitate thorough examination and troubleshooting of network-related issues.
Standout Features & Integrations:
Wireshark offers in-depth network protocol analysis with features like customizable display filters, color coding for quick identification, and graphical statistics visualization. These features are coupled with the ability to export data to various formats and to interface with third-party tools. Integration possibilities include compatibility with network analyzers and various scripting languages, enhancing its utility across different use cases.
Pricing:
Free (open-source)
Pros:
- Extensive support for multiple network protocols
- Active community providing regular updates
- Flexible data export and integration options
Cons:
- Steeper learning curve for beginners
- Resource-intensive, may require robust hardware
- Limited customer support due to its open-source nature
4. QualysGuard - Best for cloud-based security and compliance
QualysGuard offers a cloud-based security platform that helps businesses monitor, detect, and remediate vulnerabilities across their digital landscape. Its specialization in cloud-based security and compliance solutions has made it an attractive option for organizations looking to manage complex cybersecurity challenges in the cloud era.
Why I Picked QualysGuard:
I picked QualysGuard due to its strong commitment to delivering an all-in-one cloud-based security solution. The scalability and flexibility of its platform have made it an essential tool for managing security compliance across various industries. Its alignment with cloud infrastructure and the ability to integrate with several cloud providers makes QualysGuard the best for cloud-based security and compliance. The platform's real-time data analysis and robust reporting tools further justify my decision.
Standout Features & Integrations:
QualysGuard brings advanced features like continuous monitoring, threat protection, and policy compliance to the table. Its web app scanning and secure configuration assessment provide a holistic view of an organization's security posture. Integration with popular cloud providers, SIEM systems, and ticketing tools enables a coordinated approach to threat management and response.
Pricing:
Pricing upon request
Pros:
- Comprehensive cloud-based security solutions
- Integration with various cloud and on-premise systems
- Real-time monitoring and flexible reporting options
Cons:
- Complex interface may require training
- Customization may require professional services
- Lack of transparent pricing information online
5. Nexpose - Best for integrating with incident response

Nexpose, developed by Rapid7, is a vulnerability management tool designed to identify and assess risks within an IT environment. By focusing on integration with incident response tools and processes, it enables businesses to swiftly identify, prioritize, and respond to threats. This strong emphasis on integration and timely response explains why it is best to integrate with incident response.
Why I Picked Nexpose:
I chose Nexpose after a thorough comparison with other tools in the market due to its exceptional ability to align vulnerability management with incident response. The comprehensive integration with incident response platforms stood out to me, making it unique in its capability to act swiftly on detected vulnerabilities. The real-time analytics, coupled with actionable insights, confirm why Nexpose is best for integrating with incident response and adapting to changing threat landscapes.
Standout Features & Integrations:
Nexpose comes with features like Real Risk™ scores, automated actions, and Live Dashboards that help in efficient risk prioritization and mitigation. Its integration capabilities with incident response tools, SIEM systems, and ticketing platforms set it apart, allowing for a flow of information between vulnerability detection and incident management.
Pricing:
Pricing upon request
Pros:
- Strong integration with incident response tools
- Real-time analytics and actionable insights
- Automated actions for timely response
Cons:
- Interface may be challenging for beginners
- Custom reporting may require technical expertise
- Lack of transparent pricing information online
6. Nikto - Best for identifying web server vulnerabilities
Nikto is an open-source web server scanner that is highly efficient in probing and identifying vulnerabilities and potential security risks. Its specialized focus on web server vulnerabilities, including over 6700 potentially dangerous files/programs, reflects why it is best to identify weaknesses in this area.
Why I Picked Nikto:
I chose Nikto due to its prominence in identifying web server vulnerabilities, and having a remarkable database of tests specifically targeting this domain. Judging by its extensive testing capabilities, frequent updates, and thorough probing methods, it stands out as a crucial tool for web security. The specialization in uncovering web server vulnerabilities makes it the best choice for those looking to strengthen their web security, justifying why it is best for this particular use case.
Standout Features & Integrations:
Nikto offers features like SSL support, full HTTP proxy support, and checks for outdated server components. It also provides extensive logging and reporting options. While Nikto primarily operates as a standalone tool, its command-line nature allows for integration with other security tools and systems through scripts and common data formats.
Pricing:
Since Nikto is an open-source tool, it is available for free.
Pros:
- Extensive database of tests focused on web server vulnerabilities
- Regular updates with new vulnerability checks
- Open-source and free to use
Cons:
- Command-line interface may be challenging for some users
- Lack of a graphical user interface (GUI)
- May generate false positives, requiring manual verification
7. Acunetix - Best for web application security testing
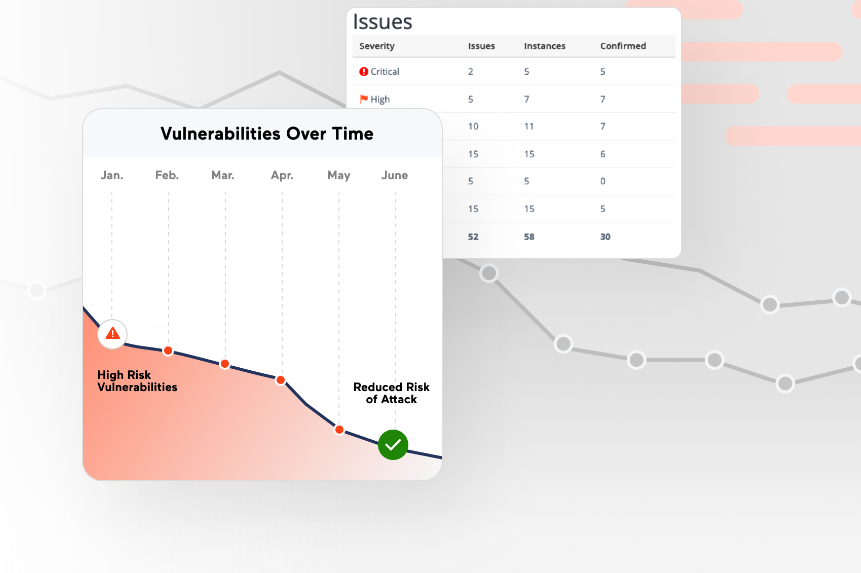
Acunetix is a web application security testing tool designed to identify vulnerabilities within web applications, websites, and web services. By focusing on the intricate aspects of web application security, Acunetix has established itself as a leading tool in this field, making it best for the detailed analysis and protection of web platforms.
Why I Picked Acunetix:
I chose Acunetix for its specialized focus on web application security, which I determined to be essential in today's complex online environment. By comparing its scanning capabilities and efficiency, I found it to stand out in detecting vulnerabilities such as SQL Injection and Cross-Site Scripting (XSS). The tool’s dedication to providing comprehensive testing for web applications explains why it’s best suited for web application security.
Standout Features & Integrations:
Acunetix boasts features like DeepScan Technology, allowing it to analyze JavaScript and HTML5, and full support for HTML5, JavaScript, and Single Page Applications (SPAs). It has a robust vulnerability management platform that integrates well with popular issue trackers like Jira, GitLab, and Microsoft TFS, along with Continuous Integration (CI) tools such as Jenkins.
Pricing:
From $45/user/month (billed annually)
Pros:
- Comprehensive web vulnerability scanning capabilities
- Integrates easily with popular development and management tools
- Offers a prioritized list of issues to streamline the remediation process
Cons:
- Pricing may be on the higher side for smaller organizations
- Some users may find the interface overwhelming initially
- Limited customization options for certain tests and reports
8. Nmap - Best for network discovery and mapping
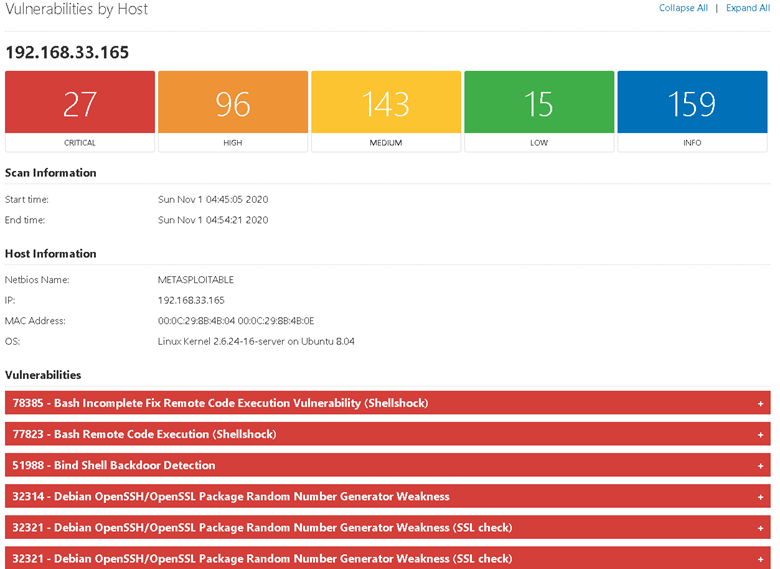
Nmap is an open-source tool used for network discovery and mapping, providing detailed information about network inventories, host availability, and open ports. Given its robust and versatile set of features for uncovering the network landscape, it is best for conducting comprehensive scans that are integral to understanding network structures and potential vulnerabilities.
Why I Picked Nmap:
I picked Nmap after judging and comparing it with other network mapping tools, and it stood out for its flexibility, accuracy, and the strong community support that continually refines it. Its adaptability across various platforms and integration with scripts makes it unique and powerful. Nmap's ability to provide a clear view of network topology and its status confirms why it's best for network discovery and mapping.
Standout Features & Integrations:
Nmap includes features like OS detection, version detection, and flexible scripting through its Nmap Scripting Engine (NSE). It's not only robust in scanning but also integrates with various security and management tools like Nessus, SolarWinds, and OpenVAS. These integrations add to its efficiency and make it a multifunctional network analysis tool.
Pricing:
Nmap is open-source and available for free.
Pros:
- Comprehensive scanning capabilities with various supported techniques
- Open-source, which promotes community-driven enhancements
- Cross-platform support including Windows, Linux, and macOS
Cons:
- Can have a steep learning curve for beginners
- Lack of a graphical user interface in the standard version
- Potential legal and ethical considerations when used improperly in unauthorized environments
9. Tripwire - Best for integrity monitoring and compliance
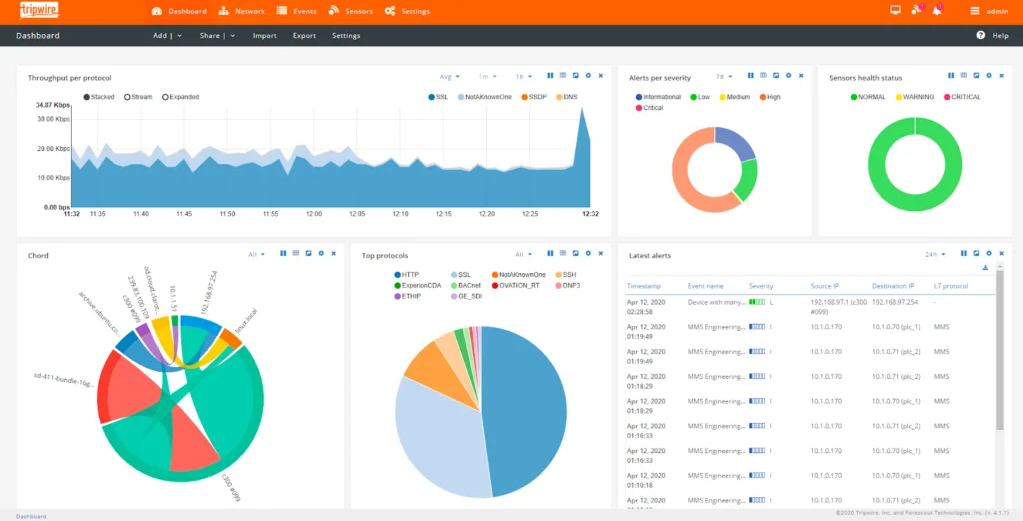
Tripwire is a well-known cybersecurity solution specifically designed for integrity monitoring and compliance management. By actively detecting changes in system files and configurations, it helps in ensuring that the security posture is maintained in alignment with various regulatory standards, making it best for organizations focused on integrity and compliance.
Why I Picked Tripwire:
I chose Tripwire after careful comparison and analysis of various monitoring solutions. What makes it different is its specialized focus on file integrity, change detection, and comprehensive compliance features. These attributes are vital for organizations that must adhere to strict regulations, demonstrating why Tripwire is best for integrity monitoring and compliance.
Standout Features & Integrations:
Tripwire's standout features include real-time change detection, deep system inspection, and a broad array of compliance templates covering major standards such as HIPAA, PCI DSS, and SOX. It integrates easily with other security and IT management platforms like Splunk, ServiceNow, and McAfee, enhancing the tool's ability to provide a holistic security view.
Pricing:
Pricing for Tripwire starts from $30/user/month (billed annually), with the exact cost depending on the specific needs and configuration of the organization.
Pros:
- Specialized in providing robust file integrity monitoring and compliance management
- Offers a wide variety of pre-configured compliance templates
- Integrates with major security and IT management platforms
Cons:
- Might be complex and time-consuming to set up
- Pricing can be on the higher side for small businesses
- The user interface may not be as intuitive as some other tools
10. Burp Suite - Best for web security analysis and auditing
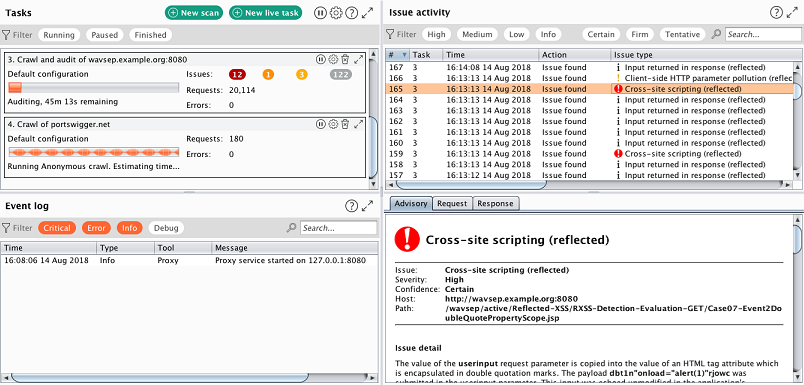
Burp Suite is a well-recognized toolkit used by security professionals for testing and analyzing the security of web applications. With features ranging from scanning to vulnerability exploitation, it's uniquely suited for comprehensive web security analysis, making it the best for auditing web applications for potential vulnerabilities and flaws.
Why I Picked Burp Suite:
I chose Burp Suite because of its long-standing reputation and proven effectiveness in the field of web security analysis. It stands out due to its detailed and customizable scanning capabilities and robust range of features that cover the full spectrum of web vulnerability testing. This multifaceted approach is why I consider Burp Suite best for web security analysis and auditing, allowing professionals to examine web applications thoroughly.
Standout Features & Integrations:
Burp Suite offers a wide array of tools, including an Intercepting Proxy, Scanner, Intruder, Repeater, and more. These features enable users to observe, analyze, and manipulate web traffic efficiently. Burp Suite also integrates with popular issue-tracking systems like JIRA and various CI/CD pipelines, which allows collaboration and issue management within a team.
Pricing:
Pricing for Burp Suite starts from $39/user/month (billed annually), and this includes the full range of web vulnerability scanning features.
Pros:
- Comprehensive set of tools for in-depth web security analysis
- Regular updates with the latest vulnerability checks
- Integration with popular issue tracking and CI/CD systems
Cons:
- May have a steep learning curve for beginners
- Some users might find the interface to be less user-friendly
- Can be considered expensive for small organizations or individual practitioners
11. ZAP (Zed Attack Proxy) - Best for automated security testing
ZAP is an open-source security testing tool actively maintained by OWASP. It is designed to automatically find security vulnerabilities in web applications while developers are in the process of developing and testing them. Because of its comprehensive and easy-to-use automated security testing features, it stands as one of the best tools for this purpose, suitable for both professionals and those new to security testing.
Why I Picked ZAP (Zed Attack Proxy):
I selected ZAP for this list, judging its strong capabilities in providing automated scans alongside manual testing features. What makes it different is its extensive community support and the fact that it caters to both seasoned security professionals and those new to the field. This flexibility and adaptability to different user needs make it the best tool for automated security testing, fulfilling a range of requirements.
Standout Features & Integrations:
ZAP offers a robust set of features, including automated scanners, spiders, and various types of fuzzers. It also provides a convenient REST API, enabling automation and integration with other tools in the development pipeline. The active community around ZAP contributes to plugins and scripts, which integrate with other popular development and security tools, making it adaptable to different workflows and environments.
Pricing:
ZAP is an open-source tool, and therefore, it's available free of charge.
Pros:
- Comprehensive automated and manual testing capabilities
- Open-source and backed by a large community
- Extensible through plugins and scripts
Cons:
- May require some time to configure properly
- The large number of features might be overwhelming for beginners
- Limited official support, relies on community for assistance and updates
12. GFI LanGuard - Best for network security management and patching

GFI LanGuard is a network security management tool that offers a comprehensive scanning, patching, and compliance solution. It functions as a virtual security consultant, identifying vulnerabilities and providing automated patch management. Given its ability to oversee the entire network, GFI LanGuard stands out as the best for network security management and patching, fulfilling essential requirements for keeping systems up-to-date and secure.
Why I Picked GFI LanGuard:
I chose GFI LanGuard for this list after carefully comparing various tools and judging its powerful capabilities in handling network security management, particularly in the patching aspect. Its ability to integrate with over 60 security and vulnerability scanners makes it stand out in the crowd. I determined that it's best for network security management and patching because of its robust features, adaptability to various network sizes, and efficient vulnerability remediation capabilities.
Standout Features & Integrations:
GFI LanGuard offers a central dashboard for vulnerability assessment, patch management, and network auditing. Its scanning engine can detect missing patches and service packs and deploy them across different operating systems and applications. It also integrates with leading solutions like Windows, Mac, Linux, and third-party applications, making it a well-rounded tool that can work across various environments.
Pricing:
The pricing for GFI LanGuard starts from $32/user/month (min 10 seats).
Pros:
- Comprehensive network scanning and patch management
- Supports a wide range of OS and third-party applications
- Easy-to-use central dashboard for network monitoring
Cons:
- Might be expensive for small businesses
- Initial setup and configuration can be complex
- Some users may find the interface outdated or less intuitive than competing tools
Other Noteworthy Vulnerability Scanning Tools
Below is a list of additional vulnerability scanning tools that I shortlisted but did not make it to the top 12. Definitely worth checking them out.
- Intruder - Good for continuous security monitoring
- Checkmarx - Good for source code scanning and vulnerability detection
- Core Impact - Good for penetration testing and threat validation
- AppScan - Good for application security and risk management
- ManageEngine Vulnerability Manager Plus - Good for vulnerability detection and patch automation
- Secunia PSI - Good for personal software inspection and security
- ImmuniWeb - Good for AI-powered web security testing
- Outpost24 - Good for full-stack vulnerability risk management
- Apptega - Good for cybersecurity and compliance management
- Astra - Good for web application firewall and malware removal
- AVG AntiVirus - Good for malware protection and secure browsing
- Bitdefender - Good for multi-layered ransomware protection
- SolarWinds Security Event Manager - Good for real-time threat detection and response
Selection Criteria for Choosing Vulnerability Scanning Tools
Choosing the right security software can be an arduous task, with an array of options, features, and functionalities available. Having personally evaluated dozens of security tools, I was specifically looking for core functionalities, key features, and usability that align with the unique needs of different organizations and individuals. My rigorous testing has led me to some favorites, focusing on the following criteria:
Core Functionality
- Threat Detection: Identify and analyze potential threats in real-time
- Vulnerability Scanning: Regularly scan for weaknesses in the system
- Patch Management: Automate the process of updating or patching software
- Compliance Monitoring: Ensure adherence to security standards and regulations
Key Features
- Multi-Layered Security: Provides different layers of protection like firewall, antivirus, anti-malware
- Real-Time Alerts and Monitoring: Immediate notifications of suspicious activities
- Integration with Existing Systems: Compatibility with current infrastructure for operation
- Data Protection and Encryption: Secure sensitive information through robust encryption methods
- Customizable Reporting: Tailored reports to analyze security status and compliance
Usability
- Intuitive Interface: A clear and understandable dashboard that allows quick navigation
- Easy Onboarding and Setup: Minimal setup time with guided walkthroughs for new users
- Responsive Customer Support: Access to help and support when needed, including knowledge bases or learning libraries
- Role-Based Access Control: Easy configuration of access rights according to the user's role, ensuring the right people have the right access
- Scalability: The ability to grow and adapt to the changing needs of the organization
Most Common Questions Regarding Vulnerability Scanning Tools (FAQs)
What are the benefits of using vulnerability scanning tools?
Vulnerability scanning tools offer several essential benefits to organizations and individuals:
- Identify Weaknesses: They detect vulnerabilities in your systems, applications, or networks before attackers can exploit them.
- Compliance Management: Helps in maintaining compliance with various security standards and regulations.
- Automated Scanning: Regular automated scans save time and ensure consistent monitoring.
- Prioritization of Threats: Helps prioritize vulnerabilities based on their risk, allowing for efficient remediation.
- Comprehensive Reporting: Generates detailed reports to provide insights into the security status and necessary actions.
How much do vulnerability scanning tools typically cost?
The pricing for vulnerability scanning tools can vary widely based on features, the size of the organization, and specific requirements. Most tools offer different pricing models, such as:
- Per User Pricing: Charging based on the number of users
- Subscription-Based: Monthly or annual subscriptions with different tiers
- Enterprise Pricing: Customized pricing for larger organizations
The typical range of pricing can be from $10/user/month to several thousand dollars for enterprise-level solutions. Some tools offer free trials or even free versions with limited functionality.
What is the cheapest and most expensive software for vulnerability scanning?
The cheapest options often include free versions or lower-tier plans of tools like Nexpose Community Edition, which offers basic functionality for small environments. On the other hand, enterprise-level solutions like IBM's AppScan can be among the most expensive, tailored to large organizations with complex needs.
Are there any free vulnerability scanning tools available?
Yes, there are several free vulnerability scanning tools that provide basic scanning functionalities. Tools like OpenVAS and Nexpose Community Edition are popular free options. While they may lack some advanced features found in paid versions, they can be a great starting point for smaller organizations or individual use.
How do vulnerability scanning tools integrate with other systems?
Vulnerability scanning tools often integrate with various other security and IT management systems. This enables a flow of information and coordinated response to threats. Common integrations include SIEM systems, patch management tools, firewalls, and ticketing systems.
Can vulnerability scanning tools help with regulatory compliance?
Absolutely! Many vulnerability scanning tools offer features specifically designed to assist with regulatory compliance, such as PCI DSS, HIPAA, or GDPR. They can automate the process of checking compliance and generate necessary reports to demonstrate adherence to regulatory standards.
Are vulnerability scanning tools suitable for small businesses?
Yes, vulnerability scanning tools are not exclusive to large enterprises. Many tools offer flexible pricing and feature sets that cater to the needs of small and medium-sized businesses. They can provide essential protection and insights without requiring extensive resources.
How often should I use a vulnerability scanning tool?
The frequency of scans depends on various factors, like the nature of your business, the regulatory environment, and the overall risk profile. Regular scans, such as weekly or monthly, are common, but critical systems might require more frequent scans. Most tools allow you to set a schedule that fits your organization's needs.
Other Cybersecurity Software Reviews
Summary
Vulnerability scanning tools are essential for maintaining the security and integrity of your systems, applications, and networks. They offer a wide range of functionalities, from identifying and prioritizing threats to assisting with regulatory compliance. Selecting the right tool for your needs requires carefully assessing core functionalities, key features, usability, and pricing models.
Key Takeaways:
- Assess Your Needs Carefully: Understand the specific requirements of your organization, such as size, industry, compliance needs, and existing security infrastructure. This will help you choose a tool with the right functionalities and integrations.
- Consider Pricing Models and Options: Vulnerability scanning tools offer various pricing models, including per-user, subscription-based, and enterprise pricing. Assess the available options against your budget, and consider free or lower-tier plans if suitable.
- Focus on Usability and Support: Look for tools that offer an intuitive interface and strong customer support. Ease of onboarding, role-based access, and availability of training or learning resources can significantly impact the effectiveness of the tool in your environment.
What do you think?
The world of vulnerability scanning tools is vast and constantly evolving, and while I've done my best to compile a thorough list, there might be some tools that I've missed. If you know of a tool that should have made this list or have personal experience with something not mentioned, please share your insights.
Your contributions will help others make informed decisions and ensure this guide remains comprehensive and up-to-date. Feel free to leave a comment or reach out directly with your suggestions.
