Best Cloud Security Tools Shortlist
I’ve evaluated the best cloud security tools based on their suitability in securing workloads and data for cloud adopters:
Our one-on-one guidance will help you find the perfect fit.
Finding the right cloud security tools can significantly streamline threat detection and boost compliance, whether protecting sensitive data, securing multi-cloud environments, or automating incident response.
However, the sheer number of available cloud security tools and the challenge of integrating them into existing workflows can make selecting the best option overwhelming.
In this article, I leverage my years of experience in cloud security and testing dozens of solutions to break down what these tools offer, who they’re best suited for, and how they can help you strengthen your cloud defenses with efficiency and confidence.
Why Trust Our Cloud Security Tools Reviews
We’ve been testing and reviewing cloud security tools since 2023. As IT specialists ourselves, we know how critical and difficult it is to make the right decision when selecting new solutions.
We invest in deep research to help our audience make better software purchasing decisions. We’ve tested more than 2,000 tools for different IT use cases and written over 1,000 comprehensive software reviews. Learn how we stay transparent & our hybrid cloud solution review methodology.
Best Cloud Security Tools Summary
| Tool | Best For | Trial Info | Price | ||
|---|---|---|---|---|---|
| 1 | Best for managing cloud-based devices and applications | Free trial available | From $8/user/month (billed annually) | Website | |
| 2 | Best for SaaS access security | 30-day free trial | From $3/user/month (billed annually) | Website | |
| 3 | Best for unified SIEM with DLP and CASB | Free demo available | Pricing upon request | Website | |
| 4 | Best range of scanning services | 14-day free trial + demo available | From $99/month | Website | |
| 5 | Best for comprehensive cloud posture management | Free plan available + free demo | From $350/month | Website | |
| 6 | Best for insight-driven defense | Free trial available | From $10/user/month (billed annually) | Website | |
| 7 | Best for proactive threat detection | 30-day free trial + free demo available | From $338.50/year | Website | |
| 8 | Best for end-to-end identity security | Free demo available | Pricing upon request | Website | |
| 9 | Best for vulnerability management in hybrid environments | Free trial available | Pricing upon request | Website | |
| 10 | Best for access management | Free demo available | Pricing upon request | Website |
-

Docker
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.6 -

Pulumi
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.8 -

GitHub Actions
Visit Website
Best Cloud Security Tools Reviews
My evaluations of the best cloud security tools will cover the core features, pricing, integration options, and much more. Let’s get started.
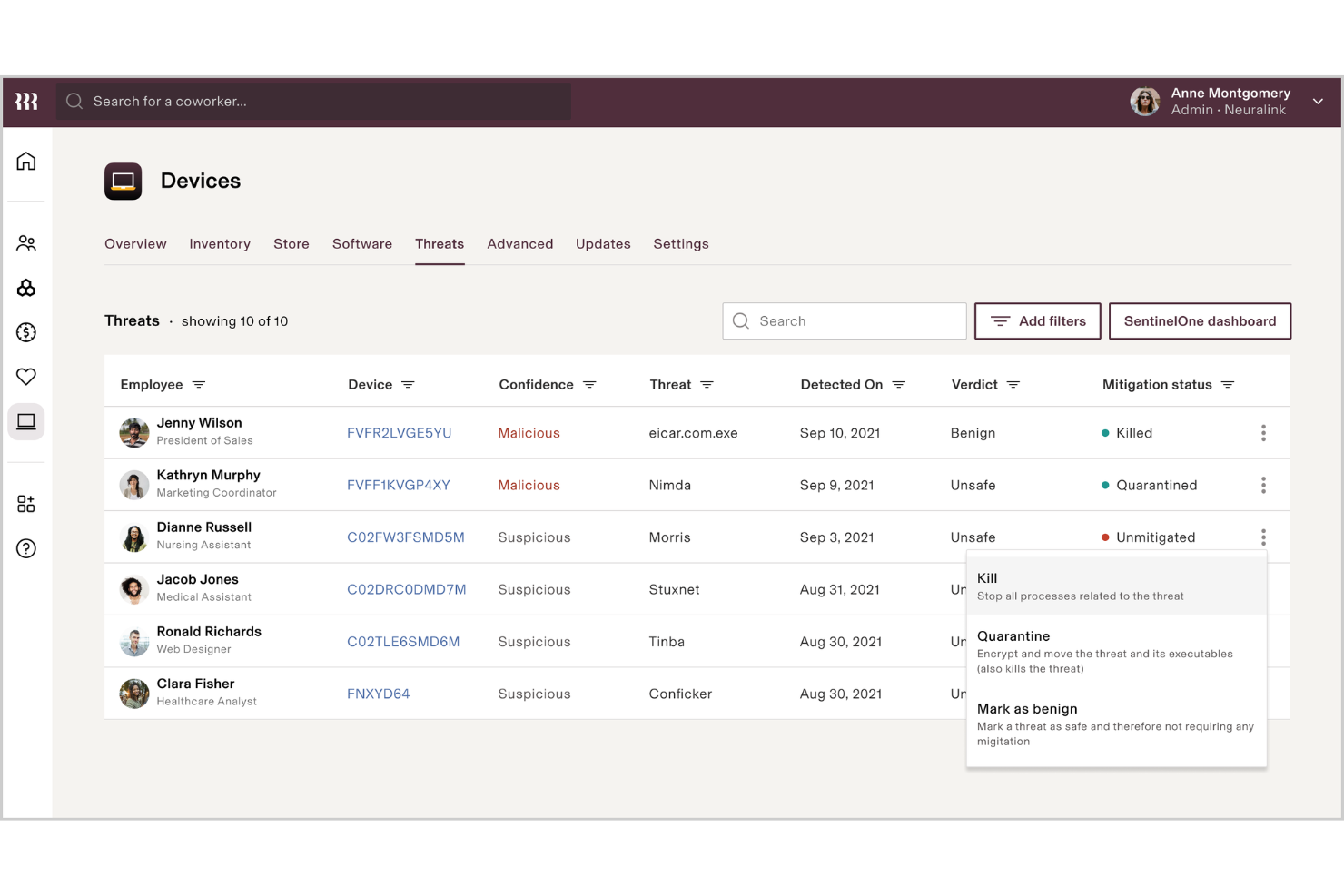
Rippling IT is an all-in-one platform designed to manage your company's IT infrastructure in the cloud. It lets you oversee your team’s devices, applications, and user access from a single location, automating much of the process.
Why I picked Rippling IT: Rippling IT works well as a cloud security tool because it centralizes identity and access management (IAM) for cloud-based assets. You can control which employees have access to what applications and data through role-based access control, and these permissions automatically update when employees change roles. Multi-factor authentication (MFA) is built-in, adding another layer of security for cloud apps. This feature ensures that access to sensitive cloud data and apps is only granted to authorized users, minimizing the risk of breaches.
Rippling IT Standout Features and Integrations:
Features include centralized identity and access management (IAM), allowing control over employee access to cloud-based applications and data. Its role-based access control ensures permissions are dynamically updated as employees change roles, reducing administrative overhead and enhancing security. Additionally, built-in multi-factor authentication (MFA) adds an extra layer of protection, ensuring that only authorized users can access sensitive resources.
Integrations include Slack, Google Workspace, Office 365, AWS, Zoom, Dropbox, and Salesforce.
Pros and cons
Pros:
- Remote wipe protects data on lost or stolen devices
- Multi-factor authentication improves cloud app security
- Simplifies managing cloud-based devices and access
Cons:
- Limited to devices and apps rather than more comprehensive cloud assets
- Complex setup for more granular security policies
New Product Updates from Rippling IT
Assign Identity Providers by Team with Rippling IT
Rippling IT now allows assigning specific identity providers like Okta and Entra ID to different teams, with Rippling’s SSO as a backup for instant rollbacks. More details at Rippling Blog.
Zygon is an identity governance tool designed to meet modern IT and security demands. It offers features like identity lifecycle management and access reviews to ensure your team's security needs are met.
Why I picked Zygon: I picked Zygon because of its strong identity and access management features. It gives you a real-time inventory of users and their access to cloud applications, making it easier to identify risks like unmanaged accounts, redundant access, and external collaborators. It also lets you detect unauthorized SaaS usage, which helps cut down on shadow IT—a common blind spot in cloud environments that can lead to data breaches. Zygon also lets you automate identity workflows and access reviews, reducing manual overhead while keeping your environment secure and audit-ready.
Zygon Standout Features and Integrations:
Features include a unified identity inventory that merges data from identity providers and SaaS apps to give you a single view of all access. Zygon also includes customizable campaign management tools for certifying user access across departments or during offboarding. Its policy alerting system continuously monitors access activity and notifies you when it detects mismatches between actual access and expected configurations.
Integrations include n8n, Make, MS Teams, Google Workspace, Entra ID, Slack, Microsoft 365, and Okta.
Pros and cons
Pros:
- Offers flexible, policy-based alerting
- Provides real-time visibility into identity access
- Detects unmanaged and unauthorized SaaS usage
Cons:
- Limited support for infrastructure-level cloud configs
- Doesn’t offer traditional threat detection or scanning
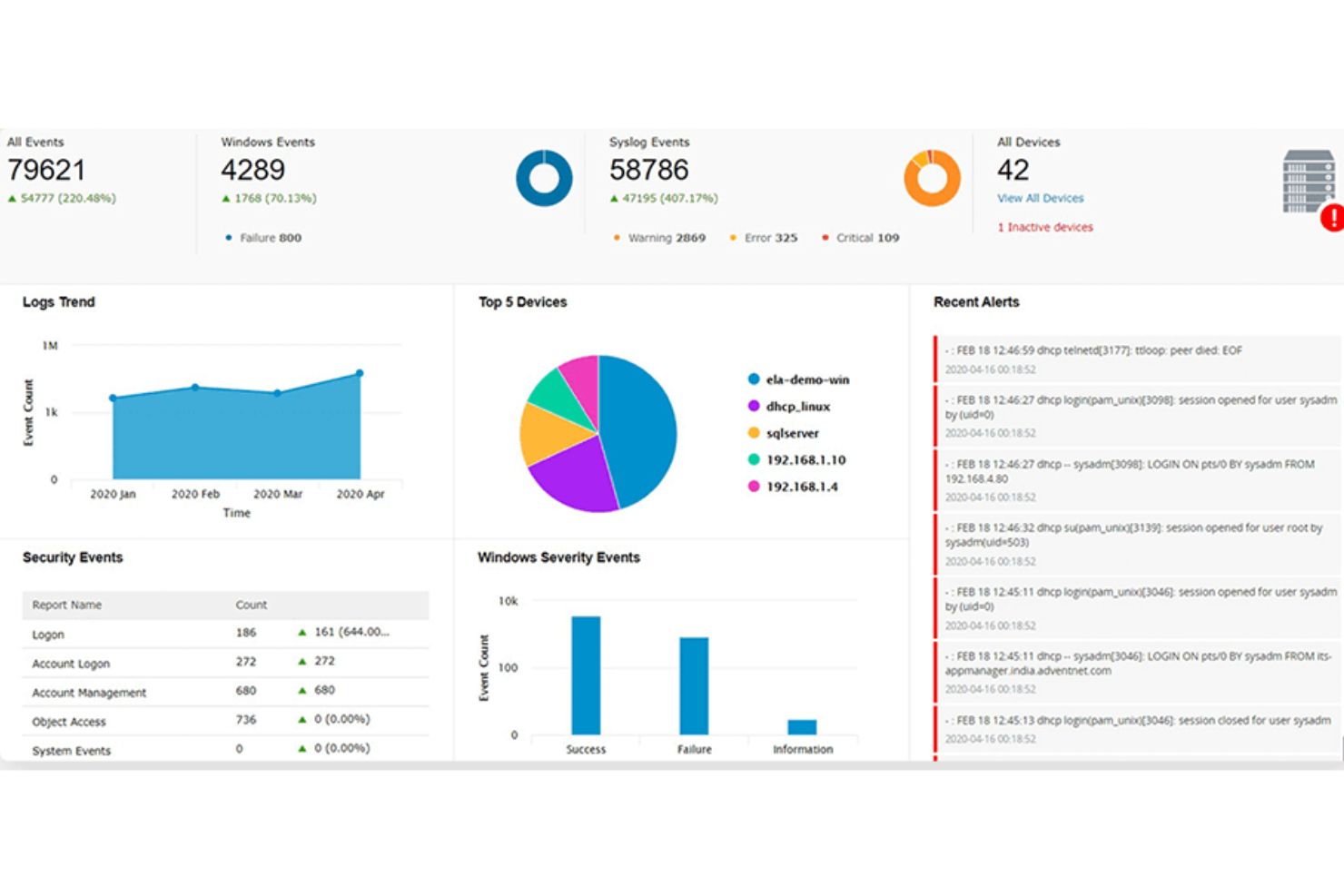
ManageEngine Log360 is a comprehensive security information and event management (SIEM) solution that provides log management, threat detection, compliance reporting, and real-time security alerts. It aims to enhance visibility into an organization's network, improve security measures, and provide a user-friendly experience.
Why I picked ManageEngine Log360: I picked ManageEngine Log360 because of its ability to provide comprehensive security coverage for cloud environments. Its integration of SIEM capabilities with cloud access security broker (CASB) and data loss prevention (DLP) features ensures robust threat detection and response. Additionally, the software’s machine learning-based anomaly detection, coupled with real-time analytics, offers dynamic and proactive cloud security, making it an ideal choice for protecting cloud assets and data.
ManageEngine Log360 Standout Features and Integrations:
Features include unified log management and SIEM capabilities, enabling real-time threat detection and compliance reporting from a single console. Its integration with popular IT and security tools enhances visibility across hybrid IT environments, simplifying compliance with regulations like GDPR and HIPAA. Additionally, Log360’s automated log correlation and anomaly detection provide actionable insights to swiftly identify and mitigate potential security risks.
Integrations include Microsoft Active Directory, Office 365, Google Workspace, AWS, Azure, Salesforce, Box, ServiceNow, Jira, Slack, IBM QRadar, Splunk, SolarWinds, Palo Alto Networks, Fortinet, Cisco, and Sophos.
Pros and cons
Pros:
- Compliance with legal regulations
- Incident management console
- Holistic security visibility across on-premises, cloud, and hybrid networks
Cons:
- Logs can be hard to read and understand
- Complex to set up and configure
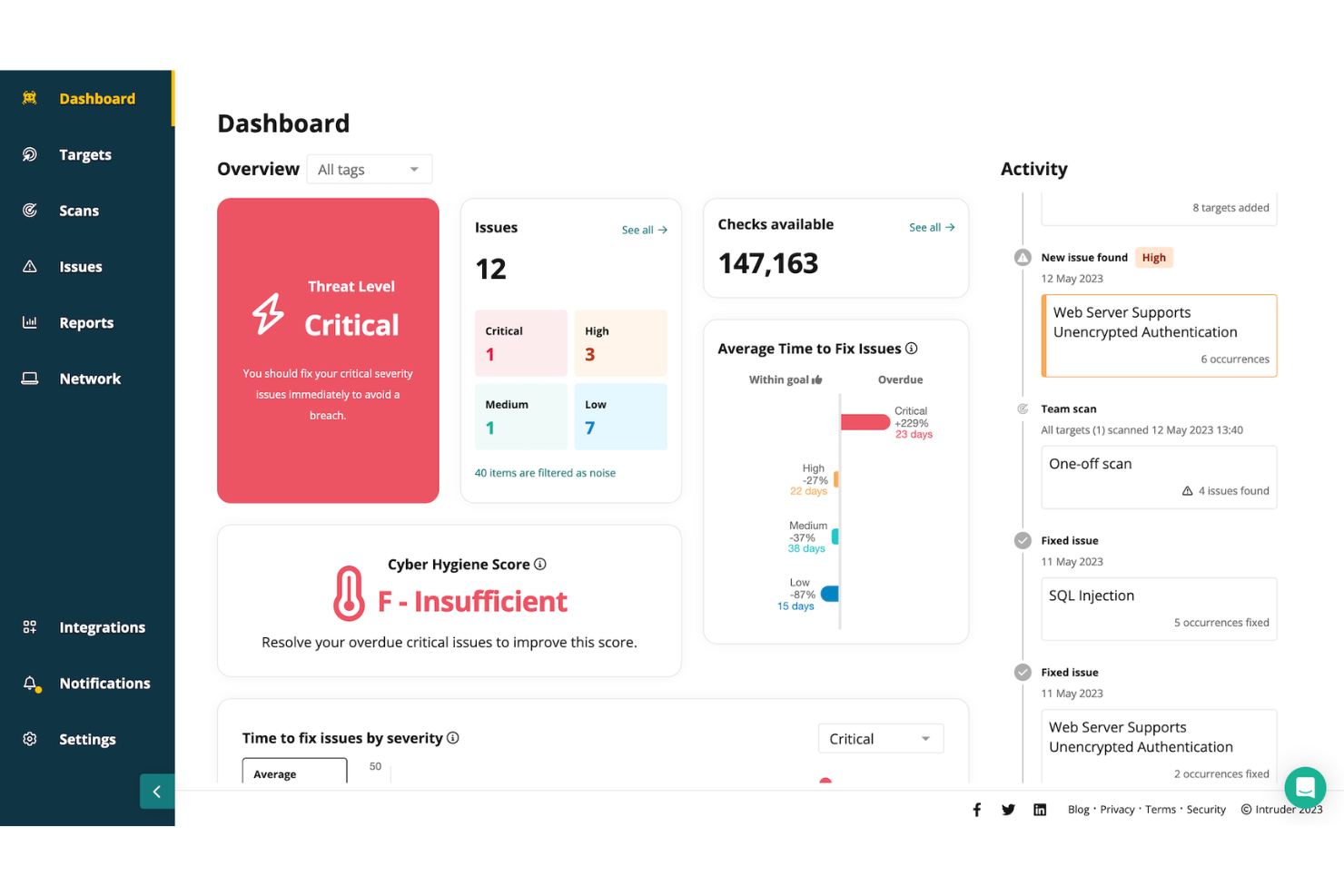
Intruder is a cloud security tool designed to help organizations manage vulnerabilities and protect their digital assets. It focuses on continuous vulnerability management and attack surface management, offering a comprehensive approach to identifying and addressing security weaknesses.
Why I picked Intruder: I picked Intruder because of its ability to perform various scanning services, including external, internal, cloud, web application, and API vulnerability scanning. These features allow you to monitor your organization's security posture in real-time, ensuring that critical vulnerabilities are prioritized and addressed promptly. Additionally, Intruder's platform offers exposure management by utilizing multiple scanning engines, which helps identify issues that might be overlooked by other tools.
Intruder Standout Features and Integrations:
Features include the ability to prioritize vulnerabilities based on their potential impact, helping you focus on the most pressing issues. Intruder also provides clear remediation guidance, making it easier for your team to address identified problems. Additionally, the platform offers comprehensive reporting capabilities, allowing you to track your security posture over time and demonstrate compliance with industry standards.
Integrations include AWS, GitLab, GitHub, Jira, Azure, Teams, Slack, Azure DevOps, Cloudflare, Google Cloud, Microsoft Sentinel, and Okta.
Pros and cons
Pros:
- Prioritization of issues helps focus on critical threats
- Offers detailed reports
- The platform proactively scans for newly disclosed vulnerabilities
Cons:
- Attack surface monitoring limited to Premium plan
- Some may find the customization options for scans limited
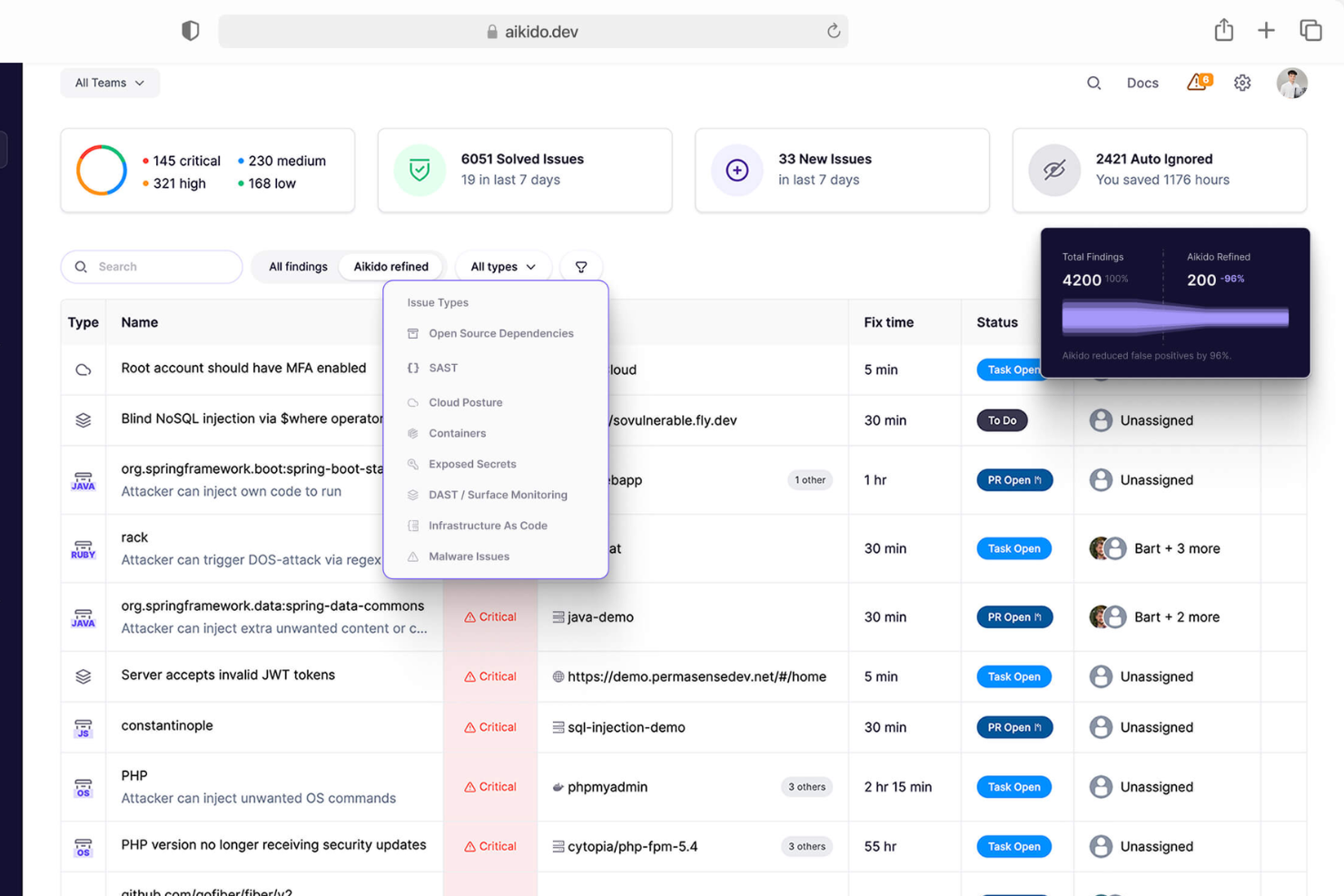
Aikido Security is a comprehensive DevSecOps platform designed to provide full security coverage from code to cloud. It integrates multiple security scanning capabilities, including SAST, DAST, SCA, CSPM, IaC, and container scanning, to identify and manage high-risk vulnerabilities in source code, containers, and cloud environments.
Why I picked Aikido Security: I like its cloud posture management (CSPM), which detects cloud infrastructure risks across major cloud providers. This feature ensures that your cloud environment is continuously monitored for vulnerabilities, misconfigurations, and compliance issues, providing a robust defense against potential security breaches. Additionally, Aikido Security offers Infrastructure as Code (IaC) scanning, which scrutinizes Terraform, CloudFormation, and Kubernetes configurations for security risks.
Aikido Security Standout Features and Integrations:
Features include an innovative approach to detecting attack paths by visualizing potential security vulnerabilities in your cloud infrastructure, enabling preemptive remediation. Its risk prioritization offers actionable insights based on real-time context and potential impact to help teams focus on the most critical threats. Aikido Security integrates with CI/CD pipelines and popular DevOps tools, making it easy to incorporate security checks into development workflows without disrupting productivity.
Integrations include Amazon Web Services (AWS), Google Cloud, Microsoft Azure Cloud, Drata, Vanta, AWS Elastic Container Registry, Docker Hub, Jira, Asana, and GitHub.
Pros and cons
Pros:
- Provides actionable insights and recommendations
- Helps in compliance tracking and reporting
- User-friendly interface
Cons:
- Does not have endpoint security or intrusion detection capabilities
- Ignores vulnerabilities if no fix is available
New Product Updates from Aikido Security
Aikido Security's New Security Features and Enhancements
Aikido Security's update includes secure-by-default hardened container images, autogenerated OpenAPI specs, inline SCA vulnerability detection, and additional Advanced Cloud Rules for improved security. More details at Aikido Changelog.
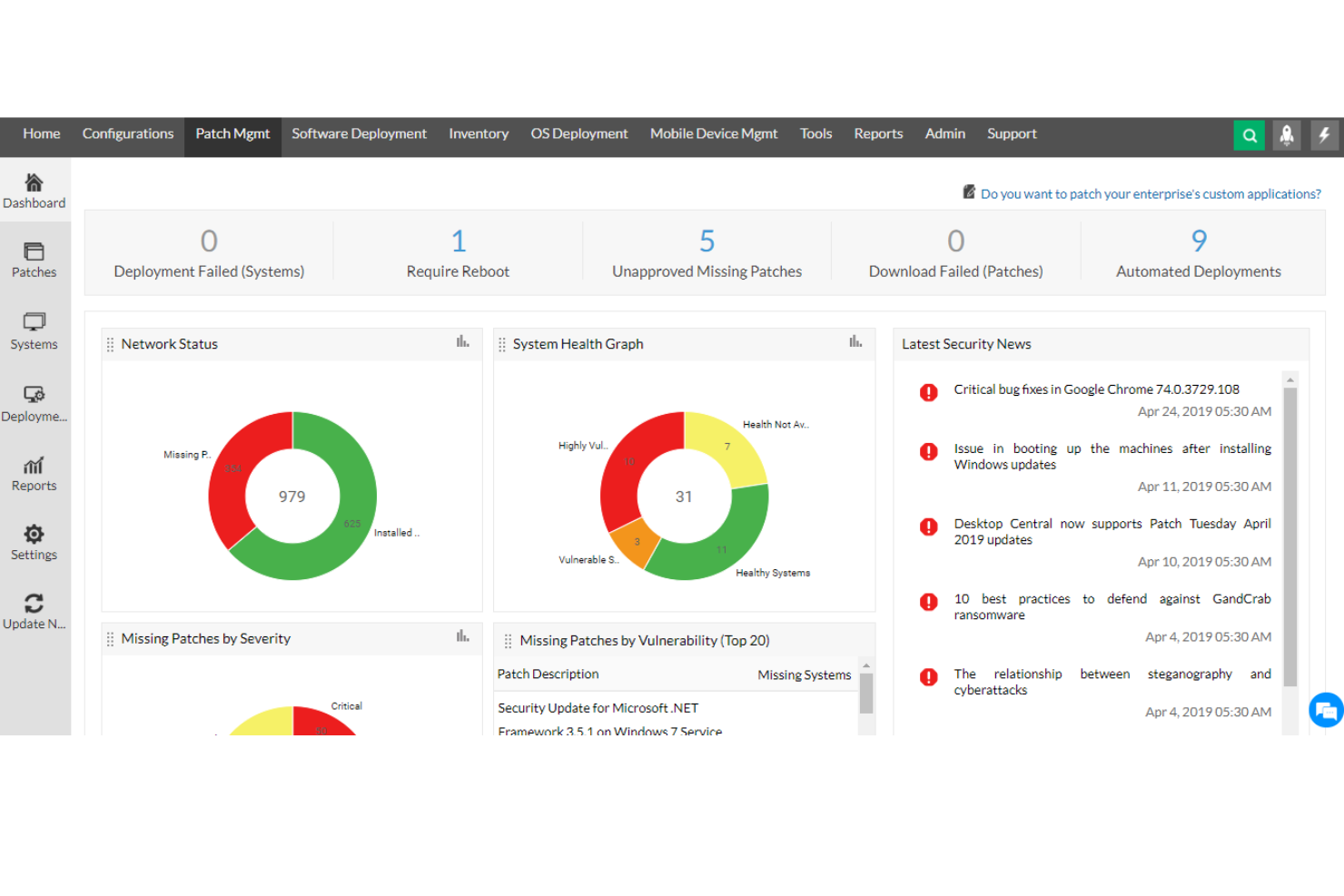
ManageEngine Desktop Central is a comprehensive tool that offers unified endpoint management and cloud security for all devices within an organization, ideal for IT professionals, managed service providers (MSPs), and enterprises of various sizes. Its goal is to assist in managing servers, laptops, desktops, smartphones, and tablets from a centralized location.
Why I picked ManageEngine Desktop Central: The software provides insight-driven defense through its extensive data collection and analytics features, which help IT administrators with actionable intelligence to proactively tackle security threats. A key feature that supports this approach is its real-time system monitoring and alerts. ManageEngine Desktop Central also offers end-to-end visibility and control and data hardening.
ManageEngine Desktop Central Standout Features and Integrations:
Features include endpoint management across devices and operating systems, ensuring seamless administration of desktops, servers, and mobile devices. Its integration with tools like ServiceDesk Plus enables efficient IT operations by connecting ticketing and device management workflows. Additionally, the software provides advanced automation for patch management and configuration enforcement, enhancing security and reducing manual effort.
Integrations include ServiceNow, Jira, Zoho Desk, Zendesk, Jira Service Desk, Microsoft SCCM, IBM BigFix, Slack, Microsoft Teams, Trello, Zapier, ManageEngine ServiceDesk Plus, Microsoft Intune, and more.
Pros and cons
Pros:
- Active directory management
- Patch management for software updates
- Remote desktop management capabilities
Cons:
- Users can feel overwhelmed with a lot of configurable features
- Some advanced features require additional research
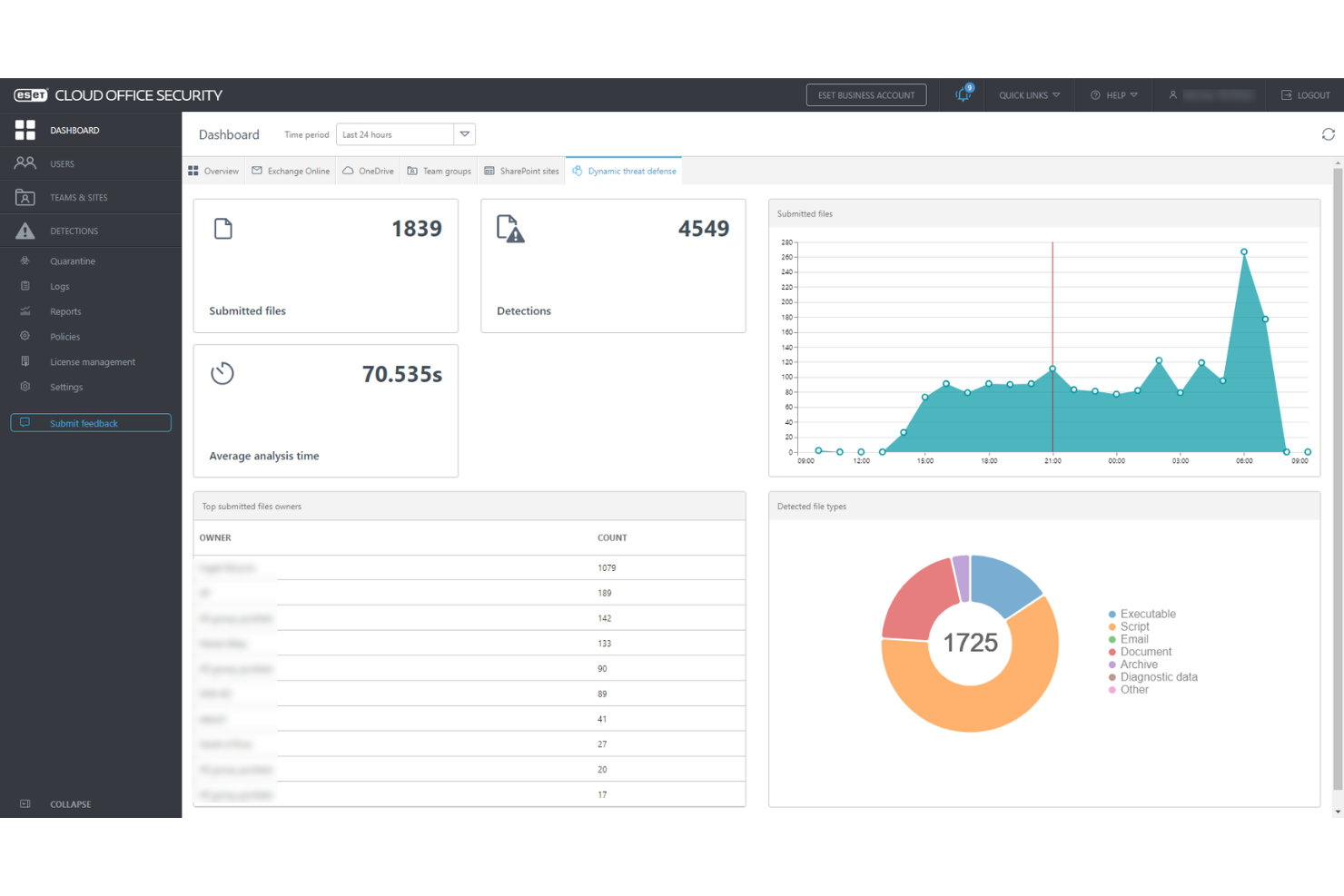
ESET PROTECT Complete is a comprehensive cloud-based security solution designed to provide multilayered protection for business endpoints, including computers, laptops, and mobile devices. The solution features cloud sandboxing technology to counteract zero-day threats and includes full disk encryption to enhance data protection.
Why I picked ESET PROTECT Complete: As a cloud security tool, ESET PROTECT offers robust protection specifically designed to address the unique security challenges of cloud computing. Additionally, the platform's cloud-based console enables administrators to manage security across distributed cloud environments seamlessly, enhancing visibility and control over all resources.
ESET PROTECT Complete Standout Features and Integrations:
Features include a unified security management platform with advanced threat detection and response capabilities, enabling IT teams to monitor endpoints, servers, and networks in real time. ESET’s multi-layered security approach includes endpoint protection, data encryption, and cloud sandboxing, ensuring comprehensive defense against known and zero-day threats. Its integration with cloud-native tools and streamlined deployment makes it particularly user-friendly for organizations seeking efficient, scalable cybersecurity solutions.
Integrations include ConnectWise Automate, Microsoft Windows Defender Antivirus, Microsoft Azure, Datto RMM, NinjaOne, Kaseya VSA, and ATERA.
Pros and cons
Pros:
- Comprehensive reporting tools for in-depth security insights
- Advanced threat detection and response capabilities
- Lightweight system footprint ensures minimal impact on performance
Cons:
- Requires technical knowledge for advanced feature utilization
- Pricing can be high for smaller organizations
CyberArk provides comprehensive and expandable identity security solutions by enabling zero trust and enforcing the least privilege. Access management is a vital aspect of security posture, and CyberArk secures identities throughout the entire Identity Lifecycle, helping you protect what matters most from malicious attacks and unauthorized access.
Why I picked CyberArk: I picked CyberArk because it has intelligent privilege control that protects data in on-premises, cloud, and hybrid settings. Its real value comes from its security-focused identity access management, which reduces cyber risk and provides cloud users with simple and secure access to resources.
CyberArk Standout Features and Integrations:
Features include its advanced Privileged Access Manager, which secures credentials and monitors privileged sessions in real-time, offering protection against insider threats and cyberattacks. Its automation capabilities streamline credential management across hybrid and multi-cloud environments, ensuring scalability for large and evolving IT infrastructures. Additionally, CyberArk’s behavioral analytics provide proactive threat detection, automatically flagging and halting suspicious activities to mitigate risks before they escalate.
Integrations are pre-built for Ansible, Jenkins, Git, AWS, Google Cloud Platform, Okta, Microsoft Azure AD, and Ping.
Pros and cons
Pros:
- Extensive functionality with a wide range of optional integrations
- Streamlined processing of authorization requests
- Single admin portal with unified audits
Cons:
- High learning curve before you get comfortable with the system
- Upgrades aren't easy
Qualys is a cloud-based security solution that offers a unified risk-based view, compliance solutions, and critical security intelligence for hybrid environments. I have included it because of the platform's comprehensive vulnerability management capabilities.
Why I picked Qualys: I chose Qualys for its excellent visibility, continuous monitoring, and high accuracy, which helps reduce false positives in cloud security analysis. In my opinion, the tool's true value lies in its ability to detect vulnerabilities from across diverse cloud assets and present them in a single, unified dashboard. Their Vulnerability Management, Detection, and Response (VMDR) solution provides improved risk management and robust patching capabilities.
Qualys Standout Features and Integrations:
Features include a highly configurable platform that allows businesses to tailor their modules for specific governance, risk, and compliance needs. Its Audit Manager automates audit trails, tracks real-time performance, and generates detailed compliance reports to simplify regulatory adherence. The Document Manager ensures smooth collaboration with version control, making managing and maintaining critical documents across teams in regulated environments easier.
Integrations are available natively with AWS, Microsoft Azure, GCP, and other managed service providers like ServiceNow and JIRA. You can also add your integrations into your applications using the open XML APIs.
Pros and cons
Pros:
- Easy to deploy with flexible scanning methods and automated workflows
- Great visibility across cloud infrastructure with continuous monitoring of cloud assets
- Useful and speedy vulnerability assessment
Cons:
- Doesn't have a vulnerability triaging feature, resulting in false positives
- Scanners lack customization
Cakewalk is an access management tool designed to help your team control and monitor software usage within your organization. It offers features that allow you to oversee employee access to various applications, ensuring that only authorized personnel can use specific tools.
Why I picked Cakewalk: I chose Cakewalk because it provides comprehensive visibility into all applications your employees use. By identifying every app accessed within your organization, Cakewalk enables you to detect unauthorized or potentially risky software, reducing the chances of security breaches. This level of insight is crucial for maintaining a secure cloud environment. Another reason for selecting Cakewalk is its automated access review process. This feature allows you to regularly assess and confirm that each employee has appropriate access rights, adhering to the principle of least privilege.
Cakewalk Standout Features and Integrations:
Features include customizable approval workflows that let you tailor access requests and approvals to fit your organization's policies, role-based access management to assign permissions based on job functions, and automated offboarding processes that ensure all access rights are promptly revoked when an employee leaves the company.
Integrations include ADP, Workday, Sage, HiBob, UKG, BambooHR, Zoho, Remote, and Personio.
Pros and cons
Pros:
- Provides real-time alerts for unauthorized access attempts
- Provides detailed visibility into all employee-used applications
- Automates access reviews
Cons:
- Limited integration options with certain niche applications
- May require time to fully implement and customize workflows
Other Cloud Security Tools
Some other great choices that didn’t quite make my top 10 list include
- OPSWAT Security Score
For quick security checks
- Barracuda CloudGen Firewall
Firewall for cloud and hybrid networks
- Forcepoint ONE
For enterprises with a hybrid workforce
- Splunk
Unified security and observability platform
- Pentera
For automated security validation
- Rubrik
For enterprise data backup and recovery
- Zscaler
Zero trust solution
- Trend Micro
For extended detection and response (XDR)
- CrowdStrike Falcon
For endpoint protection
- Orca Security
Agentless cloud security solution
- Wiz
For medium to large enterprises
- Astra Pentest
For continuous scanning with expert support
- Stream Security
For real-time cloud exposure detection
- UnderDefense
For 24/7 threat detection & response
- CloudFlare
For secure network-as-a-service
- Perimeter 81
VPN solution for network infrastructures
- Cyscale
For identity and access management
- Fugue
Developer-first solution
- Silver Sky
For managed detection and response
- ZeroSpam
For email and spam protection
Related Software and Tool Reviews
If you still haven't found what you're looking for here, check out these other types of tools that we've tested and evaluated.
- Network Monitoring Software
- Server Monitoring Software
- SD-Wan Solutions
- Infrastructure Monitoring Tools
- Packet Sniffer
- Application Monitoring Tools
Selection Criteria for Cloud Security Tools
I try to keep various needs, use cases, and concerns in mind when I conduct my research into specific software categories. To make sure I compiled a list of cloud security tools that would meet various needs and contexts, I used the following evaluation criteria:
Core Cloud Security Tools Functionality: 25% of total weighting score
To be considered for inclusion on my list of the best cloud security tools, the solution had to fulfill common use cases. These include:
- Continuous monitoring and threat detection
- Automated vulnerability assessment and remediation
- Identity and access management controls
- Data protection through encryption
- Compliance and security posture management
Additional Standout Features: 25% of total weighting score
- Unique integration capabilities with existing security infrastructures
- Advanced analytics and machine learning for predictive threat modeling
- Customizable security policies and the flexibility to adapt to specific organizational needs
- Enhanced visibility and control over cloud environments
- Exceptional scalability to accommodate growing security needs
Usability: 10% of total weighting score
- Intuitive interface design that simplifies complex security operations
- Streamlined navigation pathways to access key features quickly
- Clear and concise dashboard visualizations of security posture and alerts
Onboarding: 10% of total weighting score
- Comprehensive training materials, including videos and tutorials
- Interactive product tours and on-demand webinars for a hands-on learning experience
- Efficient setup processes, with templates and guided workflows to accelerate deployment
Customer Support: 10% of total weighting score
- Responsive and knowledgeable support team available through multiple channels
- Proactive engagement through regular security updates and best practices sharing
- Community forums for peer support and advice
Value For Money: 10% of total weighting score
- Competitive pricing models that offer clear cost-benefit advantages
- Transparent billing practices with flexibility to scale based on usage
- Free trials or demos to evaluate core functionalities before purchase
Customer Reviews: 10% of total weighting score
- Strong testimonials regarding the effectiveness of threat detection and response capabilities
- High satisfaction rates with customer support responsiveness and helpfulness
Through this comprehensive criteria framework, I've meticulously evaluated cloud security tools to ensure they meet the broad spectrum of needs and challenges faced by organizations securing their cloud environments.
How To Choose a Cloud Security Tool
As you're shortlisting, trialing, and selecting cloud cybersecurity tools, consider the following:
- What problem are you trying to solve - Start by identifying the cloud security feature gap you're trying to fill to clarify the features and functionality the tool needs to provide.
- Who will need to use it - To evaluate cost and requirements, consider who'll be using the platform and how many licenses you'll need. You'll need to evaluate if it'll just be the IT team, or the whole organization that will require access. When that's clear, it's worth considering if you're prioritizing ease of use for all, or speed for your technical power users.
- What other tools it needs to work with - Clarify what tools you're replacing, what tools are staying, and the tools you'll need to integrate with. This could include your existing cloud infrastructure, various data sources, and your overall tech stack. You might also need to decide if the tools will need to integrate together, or alternatively, if you can replace multiple tools with one consolidated cloud security tool.
- What outcomes are important - Consider the result that the tool needs to deliver to be considered a success. Think about what capability you want to gain, or what you want to improve, and how you will be measuring success. You could compare cloud security tool offerings until you’re blue in the face, but if you aren’t thinking about the outcomes you want to drive, you could be wasting a lot of valuable time.
- How it would work within your organization - Consider the solutions alongside your workflows and delivery methodology. Evaluate what's working well, and the areas that are causing issues that need to be addressed. Remember every business is different — don’t assume that because a tool is popular that it'll work in your organization.
Trends in Cloud Security Tools For 2025
By analyzing the latest product updates, press releases, and release logs from leading and rapidly evolving cloud cybersecurity tools, we gain valuable insights into how the industry is responding to the escalating complexity of cyber threats to cloud infrastructure.
These insights not only reveal the direction in which cloud security technologies are heading, but also highlight which features are gaining prominence, evolving rapidly, and becoming essential for organizations. Here's my overview of the common cloud security trends shaping the direction of these tools in 2024:
Evolving Trends in Cloud Security Tools
- Enhanced Focus on Identity and Access Management (IAM): IAM features are rapidly evolving to include more sophisticated user verification methods, such as biometric authentication and behavior analysis. This trend underlines the growing recognition of identity-based vulnerabilities and the need for stringent access controls.
Novel and Unusual Functionalities
- Zero Trust Architecture Implementation: Some cloud security tools are pioneering the integration of Zero Trust principles directly into their platforms, offering novel approaches to network security that assume no entity within or outside the network is trustworthy without verification. This represents a significant shift from traditional perimeter-based security models.
- Blockchain for Data Integrity: An unusual yet emerging functionality involves leveraging blockchain technology to enhance data integrity and security within cloud environments. This novel application of blockchain is gaining traction as a means to secure transactions and data exchanges across distributed networks.
Most Important and In Demand Features
- Comprehensive Cloud Security Posture Management (CSPM): The demand for CSPM features that provide visibility across cloud environments, assess security postures, and automate remediation of misconfigurations is at an all-time high. This reflects the critical need for continuous monitoring and management of cloud security postures to prevent data breaches.
Features Becoming Less Important
- Static Rule-Based Security Controls: There's a noticeable decline in the demand for static, rule-based security controls in favor of more dynamic, context-aware policies. This shift acknowledges the limitations of traditional security measures in keeping pace with the adaptive strategies employed by cyber attackers.
- Perimeter-Based Security Models: With the adoption of cloud and hybrid environments, perimeter-based security models are becoming less relevant. The focus is moving towards securing data and applications irrespective of their location, rather than relying on traditional network boundaries.
For IT professionals navigating this landscape, understanding these trends is crucial for selecting tools that not only address current security needs but are also poised to evolve with the digital ecosystem.
What Are Cloud Security Tools?
Cloud security tools are software or services that protect cloud services from cyber-attacks using tools such as vulnerability scanning, firewalls, encryption, and threat detection and remediation.
You can deploy cloud cybersecurity tools across a variety of cloud-based network configurations, such as hybrid, private, and multi-cloud networks. Without them, your data and cloud assets are more vulnerable to unauthorized access, data breaches.
Features of Cloud Security Tools
Let's explore the most important features I look for in cloud security tools throughout my research:
- Real-time Threat Detection: This feature enables immediate identification of potential threats. It's vital because it allows for the quick containment and mitigation of threats such as data breaches before they escalate, safeguarding cloud assets from immediate harm.
- Automated Vulnerability Scanning: Automated scans for vulnerabilities ensure continuous monitoring and assessment of the cloud environment. This feature is crucial for identifying and rectifying security weaknesses promptly, preventing attackers from exploiting them.
- Data Encryption: Encryption of data, both at rest and in transit, provides a strong layer of protection. It ensures that, even if data is intercepted or accessed by unauthorized individuals, it remains unreadable and secure.
- Identity and Access Management (IAM): IAM controls who can access what in the cloud environment. This feature is essential for ensuring that only authorized users have access to sensitive data and systems, significantly reducing the risk of insider threats or accidental data exposure.
- Firewall Protection: Firewalls act as a barrier between your cloud network and the outside world. They are key to regulating incoming and outgoing network traffic based on security rules, thereby preventing unauthorized access to cloud resources.
- Intrusion Detection and Prevention Systems (IDPS): IDPS monitor network and system activities for malicious actions or policy violations. This feature is indispensable for not only detecting but also preventing potential security breaches from occurring.
- Cloud Security Posture Management (CSPM): CSPM automatically detects and remediates security risks in cloud configurations. It's critical for maintaining a strong security posture and compliance with industry standards, reducing the risk of configuration errors leading to breaches.
- Secure Configuration Management: This feature ensures that cloud systems are configured according to best security practices. Proper configuration management is key to eliminating unnecessary vulnerabilities and maintaining the integrity of cloud environments.
- Endpoint Security: Protecting the devices that access the cloud (endpoints) is as important as securing the cloud itself. This feature prevents breaches originating from compromised devices, ensuring that endpoints do not become the weak link in cloud security.
- Compliance Monitoring: Continuous monitoring for compliance with legal and industry standards ensures that cloud environments adhere to necessary regulations. This feature helps avoid legal penalties and reputational damage that can arise from non-compliance.
Protecting cloud assets from cyber attacks requires a multifaceted approach, and each of the features above plays a critical role in creating a secure cloud environment. Compare these features with the priorities of your business to narrow your focus in your solution search.
Benefits of Cloud Security Tools
Here are five primary benefits that underscore the importance of integrating cloud security tools within your organizational strategy:
- Enhanced Threat Detection and Response: Cloud security tools provide advanced capabilities to detect and respond to threats in real-time. By leveraging these tools, organizations can identify potential security breaches early and mitigate them swiftly, thereby minimizing the risk of data loss or damage.
- Streamlined Compliance Management: These tools automate the process of adhering to regulatory and compliance standards. For businesses operating in regulated industries, cloud security tools simplify the complex and time-consuming task of ensuring compliance, reducing the risk of penalties and reputational damage.
- Scalable Security Solutions: Cloud security tools offer scalable solutions that grow with your business. This flexibility allows organizations to adjust their security measures as their cloud usage expands, ensuring continuous protection without the need for constant manual intervention or upgrades.
- Cost-Effective Security Management: By consolidating various security functions into a single platform, cloud security tools reduce the need for multiple disparate systems. This consolidation leads to lower operational costs, as it minimizes the need for extensive hardware and reduces the manpower required for security management.
- Improved Data Protection and Privacy: These tools employ encryption and other security measures to protect sensitive information stored in the cloud. For organizations handling confidential or personal data, cloud security tools are essential in preventing unauthorized access and ensuring data privacy.
Cloud security tools represent a critical investment for organizations looking to navigate the complexities of cloud computing securely and efficiently. As the digital landscape continues to evolve, these tools will play an increasingly vital role in enabling organizations to protect their assets and maintain trust with their customers.
Costs & Pricing For Cloud Security Tools
Understanding the typical pricing plans for cloud security tools and what they offer can help you make an informed decision that aligns with your organization's security requirements and financial constraints.
Plan Comparison Table For Cloud Security Tools
Here's an overview of typical pricing models and costs for these types of solutions:
| Plan Type | Average Price | Common Features |
|---|---|---|
| Free | $0 | Basic threat detection, Limited scans, Community support, Access to forums |
| Basic | $20 - $100/month | Enhanced threat detection, Automated scans, Email support, Basic compliance tools |
| Professional | $100 - $500/month | Real-time threat detection, Advanced compliance management, Phone support, Integration capabilities |
| Enterprise | $500 - $2000+/month | Customizable features, Dedicated support, Full compliance suite, Advanced analytics and reporting |
When selecting a plan, consider both the level of security your organization requires and the budget you have available. The right plan should not only provide comprehensive protection but also offer scalability as your organization grows and its needs change.
Cloud Security Tools Frequently Asked Questions
Here are some of the most common questions when choosing a cloud security tool.
What are some typical cloud security risks?
Why is cloud security important?
How many layers are in cloud security?
When should you think about using cloud security tools?
Want More?
With my list of the best cloud security tools, you're equipped to make an informed decision about which is right for your business. There are endless cloud resources to learn more.
Subscribe to The CTO Club newsletter to stay updated on the latest cloud insights to help you build SaaS teams and systems that scale.