Endpoints are devices–smartphones, laptops, and desktop computers–that connect to a network. Endpoints may be vulnerable to cyber threats and can provide a direct pathway for attackers to access sensitive information or disrupt network operations.
Endpoint security (EPS) involves safeguarding the entry points of user devices against exploitation by malicious entities and campaigns. It’s an extremely important investment, given that data breaches cost companies an average of $9.44 million in 2023.
What is Endpoint Security?
Endpoint security encompasses a range of technologies and practices that aim to secure the endpoints of a network. The capabilities to mitigate risks associated with endpoint devices broadly include antivirus software, firewalls, data encryption, intrusion detection and prevention systems (IDPS), and regular patch management.
Endpoints are often the weakest link in a network's security. Therefore, protecting them involves deploying security measures across multiple layers, such as the network, host, and application layer.
For example, organizations can prevent unauthorized access from external and internal sources by using a combination of network firewalls, host-based firewalls, and application-level firewalls. This ensures the integrity and availability of the endpoints and the data they handle.
Endpoint security solutions help improve the overall security posture of an organization — especially when you consider remote work; employees are connecting from all over on a range of devices.
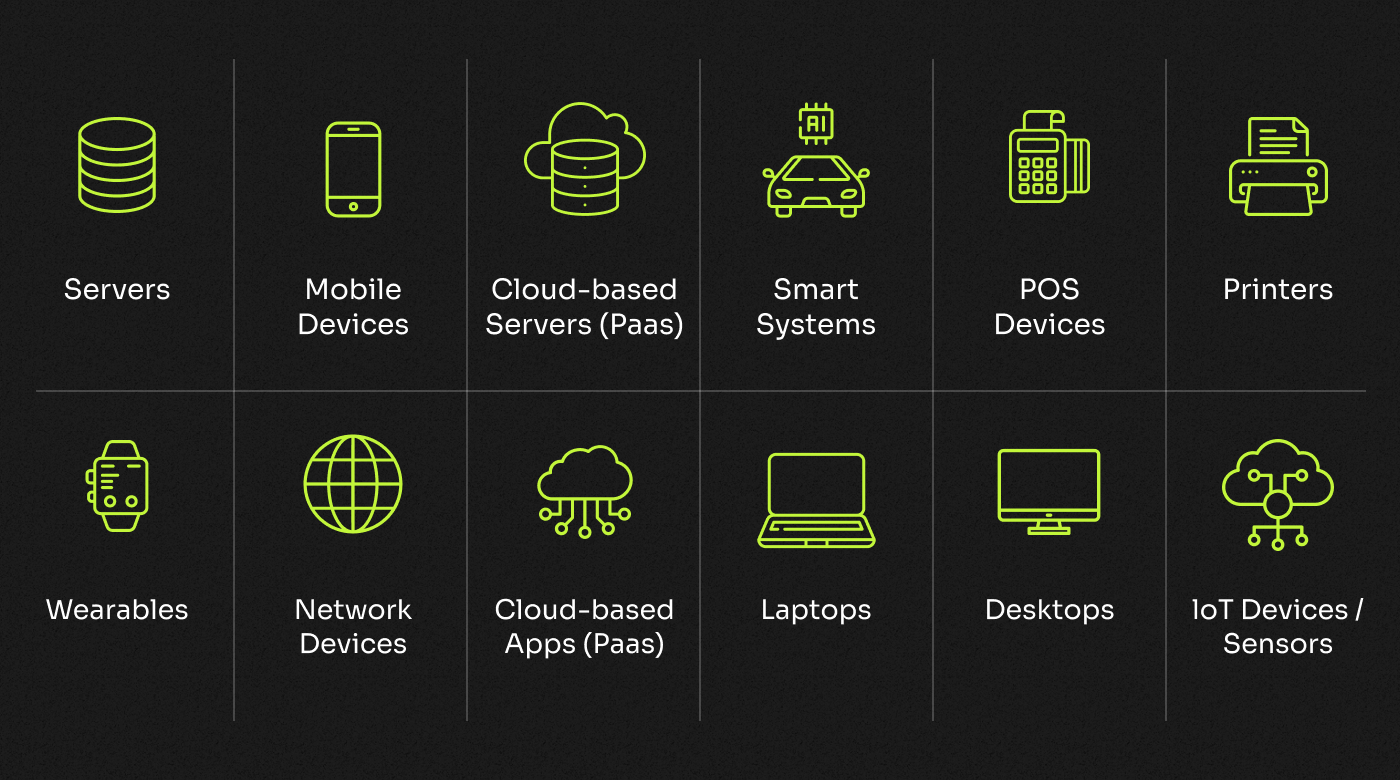
What are Endpoints?
Endpoint devices can be, but are not limited to, any of the following:
- Computers (desktops and laptops)
- Mobile devices (smartphones and tablets)
- Servers
- Virtual machines
- Network routers
- Printers, fax machines, and scanners
- IoT devices
How Do Endpoint Security Platforms Work?
Each tool differs, but it typically includes a suite of features used to implement security measures across multiple individual devices. These tools continuously monitor, analyze, and log the behavior of endpoints, looking for signs of suspicious activities in real time.
A primary layer of security is provided by scanning incoming files for malware with antivirus software and setting up firewalls to block unwanted connections. To detect threats, these tools use various methods, such as signature-based scanning, heuristic analysis, and machine learning algorithms. If a potentially harmful file is detected, the endpoint protection system can quarantine it before it is allowed to enter the network.
Endpoint protection systems use a management console to provide a centralized view of all devices, their security statuses, and any detected threats. This interface allows administrators to monitor and control the endpoint protection across the client's systems.
Administrators can configure policies, set security rules, and deploy updates or patches to the client's systems through the console. The console is typically connected to the systems through a secure communication channel, such as a VPN or encrypted connection, to ensure the confidentiality and integrity of the data exchanged between the console and the endpoints.
Additionally, endpoint protection often includes patch management controls to apply regular updates and address newly discovered vulnerabilities.
Endpoint protection platforms can be deployed in three models: on-premise, hybrid, and cloud.
On-Premises
On-premises endpoint protection involves deploying the security infrastructure within the client's own data center. This offers complete control and allows organizations to oversee their security environment directly. It may be suitable for organizations with strict compliance requirements or sensitive data that must be kept in-house, such as financial institutions.
Cloud
Cloud-based endpoint protection relies on security services hosted in the cloud. This model offers ease of deployment, scalability, and access to security features from anywhere. It may be ideal for organizations with limited IT resources or those that prioritize agility and remote management.
Hybrid
A hybrid model combines both on-premises and cloud-based components. It offers the security and granular control of managing some aspects of security on-premises while leveraging the scalability and convenience of cloud-based services for others. It may be a good choice for organizations that want to balance customization and scalability.
For example, a healthcare organization may choose a hybrid model to give them the best tools for meeting compliance requirements for protecting patient data while benefiting from cloud-based scalability and ease of delivery.
Case Study: How Allied Beverage Group Stopped a Ransomware Attack
To better understand how endpoint security functions in real-world scenarios, let's examine a case where a beverage company employed it to protect against cyber threats.
Allied Beverage Group is a prominent beverage distributor in the United States. When they first set up their IT infrastructure, they knew how important it was to spot hidden threats across control points, but their resources limited the extent of their security team.
They employed a popular endpoint solution from Cisco with cloud-native delivery, comprehensive visibility for threat management, and managed threat-hunting services. Using this platform, they soon spotted the start of an infiltration attack in which an unauthorized user attempted to escalate their user privileges to reach more sensitive parts of the network. Thanks to early detection, Allied could quickly remediate the issue before actual harm was done.
When the COVID pandemic hit, they were able to seamlessly transition 80% of their workforce to remote work despite having not been previously remote, thanks to already having security in place on their endpoint devices. Allied representatives say it would have been difficult to properly safeguard their devices in these circumstances without a comprehensive endpoint security solution.
The Value of Endpoint Security
In an increasingly interconnected world, endpoint security solutions are critical to protecting sensitive data and preventing cyber threats. Organizations face an ever-evolving landscape of potential security risks, including malware, spyware, ransomware, phishing, and social engineering attacks, as well as advanced cyber threats such as man-in-the-middle schemes, distributed denial of service attacks, and advanced persistent threats created by hackers with undetected access.
With 450,000 new malware programs detected daily, IT professionals say it’s a top security threat. Plus, in the second quarter of 2021, there were 188.9 million ransomware attacks.
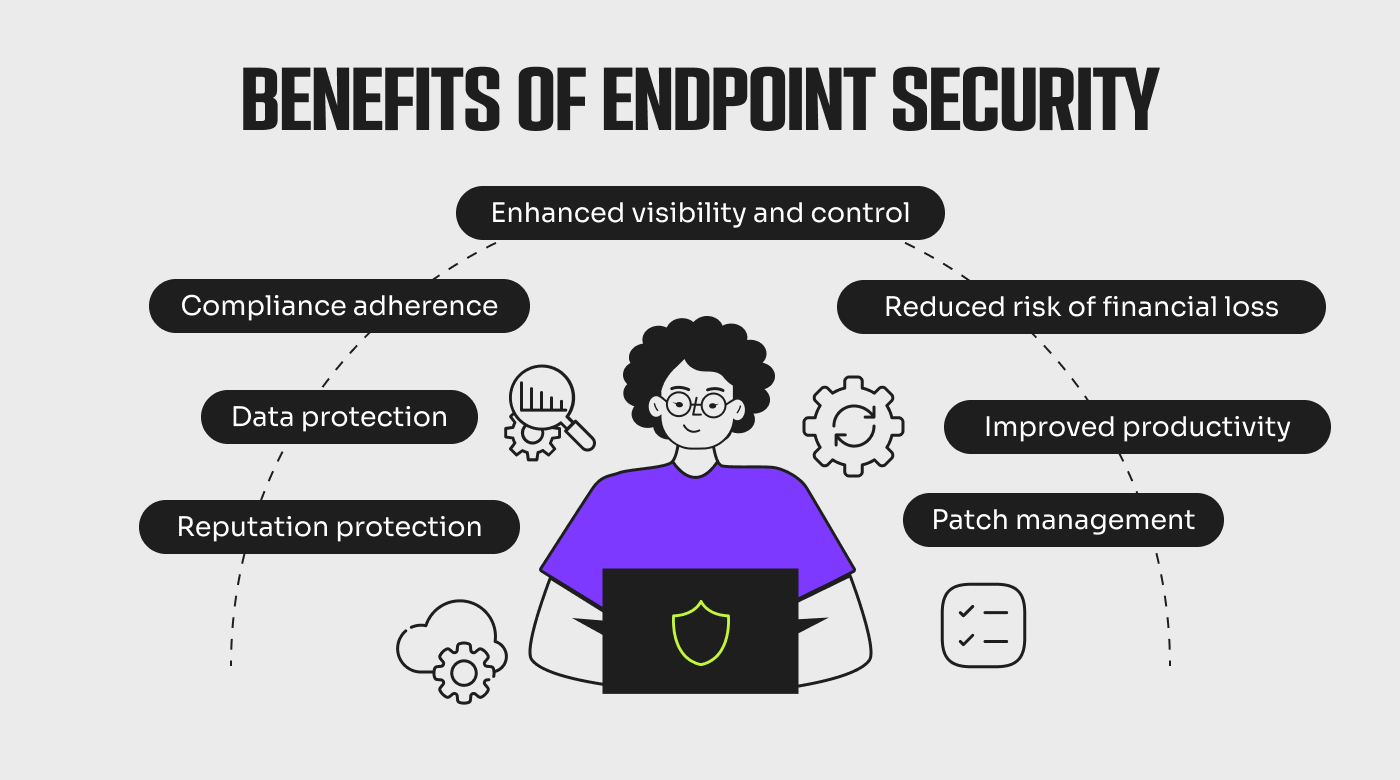
In addition to providing essential device security, endpoint protection tools allow you to proactively mitigate negative outcomes and reap a variety of additional benefits for your organization, including:
- Data protection: Detects malware and suspicious network behavior to help guard critical data stored on endpoints, preventing data breaches. 65% of users share that exposure of sensitive data is their primary concern relating to cyberattacks.
- Enhanced visibility and control: Provides visibility into the security status of endpoints, allowing administrators to enforce security policies, track incidents, and implement necessary remediations.
- Compliance adherence: Enforces security and compliance posture to meet industry regulations and data protection laws.
- Reduced risk of financial loss: Prevents costly security incidents, such as ransomware attacks and business disruptions, thus saving unnecessary expenses.
- Reputation protection: Protects organizational reputation by preventing data breaches and other security incidents that can lead to loss of trust and damage to a brand's reputation.
- Patch management: Keeps software, operating systems, and applications updated with the latest security patches.
- Improved productivity: Guards against downtime, data loss, and other system disruptions so users can work safely and efficiently. Cybersecurity professionals report that the negative impact on productivity was their most significant consequence of endpoint attacks.
Factors to Consider
To make the most of your endpoint security platform, you should understand the best practices in the field and carefully evaluate which tools to purchase. Before I jump into my top recommended endpoint security solutions, let’s see what factors you should look for:
- Threat detection capabilities: Ensure the solution provides real-time detection and prevention mechanisms to safeguard against cyber threats.
- Ease of use and management: Look for a solution that is user-friendly and offers centralized management capabilities, allowing you to easily deploy, monitor, and update security measures across all endpoints.
- Integration: Consider the solution's ability to integrate with your existing security infrastructure and other tools to provide a cohesive security ecosystem.
- Performance impact: Evaluate the impact of the solution on the performance of your endpoints. Ensure that the solution doesn’t significantly hinder your users' productivity.
- Compatibility: Ensure the solution is compatible with your organization's operating systems and devices. It should protect endpoints on different platforms, such as Windows, macOS, and mobile devices.
Tools you can use

You know endpoint security is necessary to protect your business, but there are so many options to choose from that it’s hard to know which is best. To help you pick the right fit for your needs, I’ve tested several solutions and can recommend my top 5 selections based on what each one does best.
1. Kaspersky - Best for Advanced Power Users
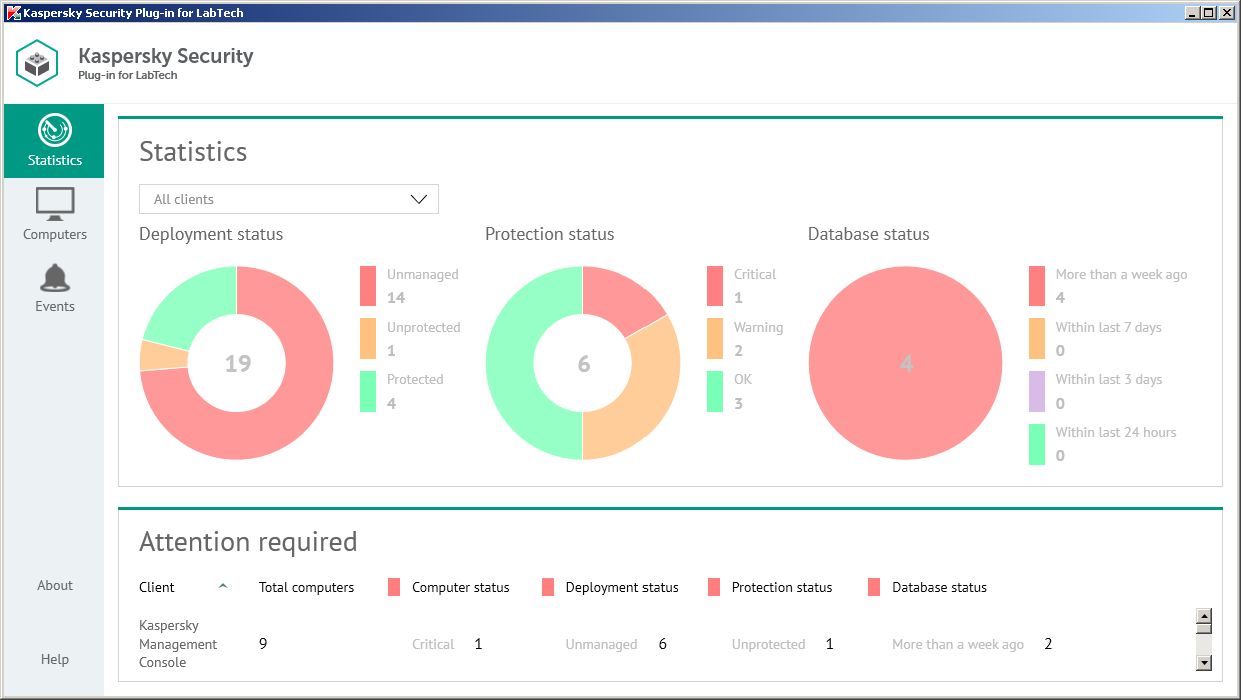
Kaspersky offers a centralized management console that allows administrators to easily deploy, monitor, and manage security policies across multiple devices.
I chose Kaspersky because of its robust features that advanced and power users can take advantage of, including:
- Sophisticated threat detection goes above and beyond the essential antivirus. It can detect and stop admin account takeover and use rollbacks to correct any changes the attacker makes
- Automatic vulnerability and patch management
- Multiple platform protection – Windows, Linux, macOS, mobile devices, and servers
- Root cause analysis can visualize the attack spread, including how it was created on the endpoint and file information like its origin, metadata, and digital signature
2. Bitdefender - Best for Enterprises

Bitdefender’s endpoint security platform utilizes advanced algorithms and machine learning to detect and block sophisticated cyber threats. The solution continuously monitors files and processes in real-time, preventing malware infections.
What I like about Bitdefender is that it has a wide range of features that enterprises can benefit from, including:
- Behavioral analysis that lets you establish a baseline of expected behavior so that any anomalies can be identified and flagged as potential security risks
- Web protection that secures web browsing activities on endpoints
- Built-in firewall
- Application and device control
- Patch management
3. CrowdStrike Falcon Insight XDR - Best for Full Attack Visibility
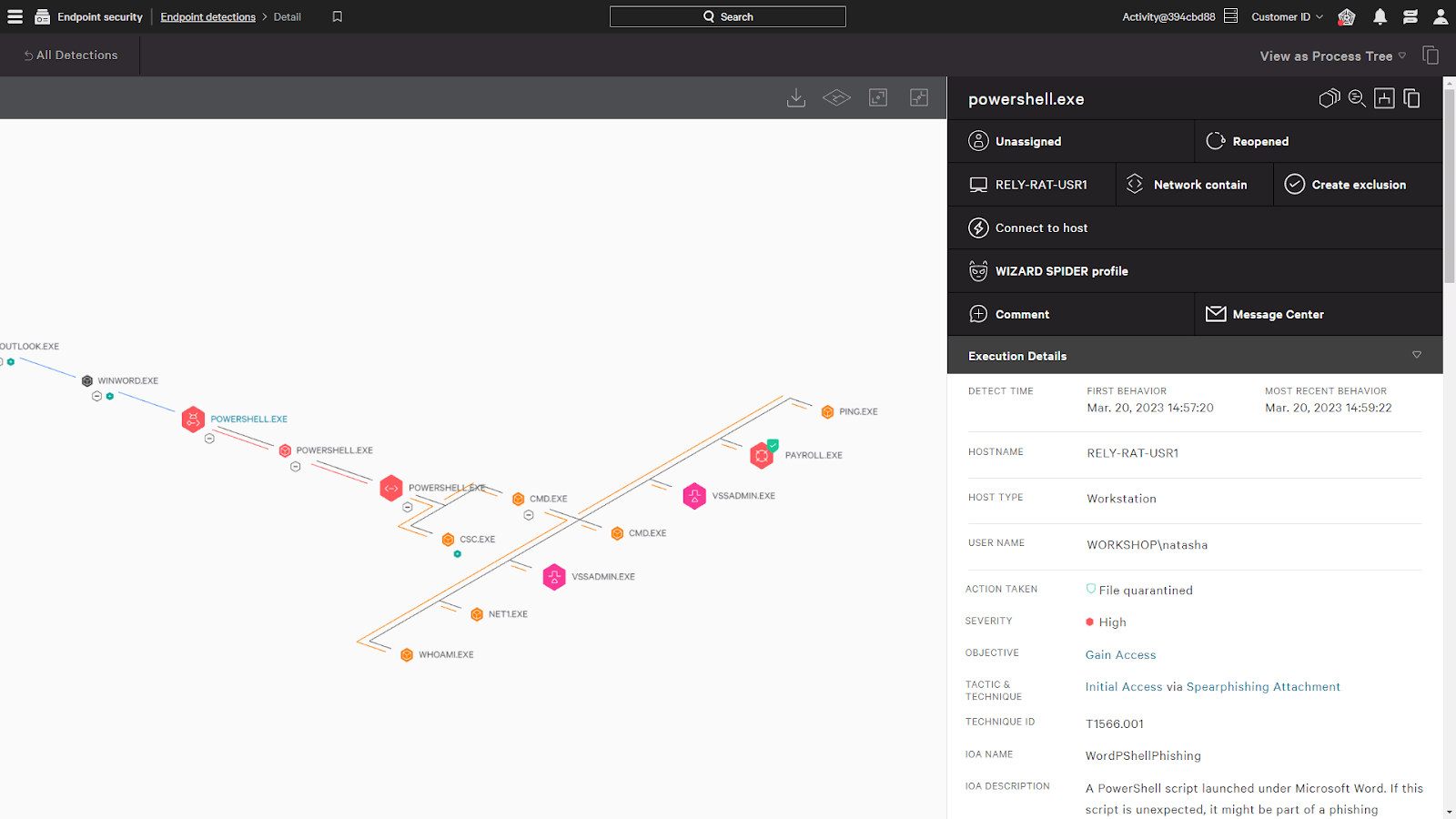
Crowdstrike Falcon Insight XDR provides comprehensive visibility into the status of your endpoints and offers alert prioritization to combat threats on time.
What I appreciate about Crowdstrike is that its setup takes minutes, and you don’t need to reboot your systems. It offers automated updates, sandbox submissions, and in-depth actor profiles to give you more information on attacks.
I believe one of its most substantial offerings is endpoint telemetry collection and analysis. It collects and analyzes data from endpoints, such as computers, servers, and mobile devices, to identify potential indicators of compromise or suspicious activities.
4. Sophos Intercept X - Best for Malware Detection

Sophos Intercept X uses deep learning algorithms to prevent known and unknown malware. In my analysis, I noticed that it provides all the standard features of an endpoint protection platform, like real-time threat intelligence, exploit protection, and root cause analysis.
What stands out for me, however, is its offering called CryptoGuard. It protects against ransomware by detecting and stopping unauthorized encryption attempts in real time.
Another strong point is that it can filter web traffic to block access to malicious or inappropriate websites, preventing users from unknowingly downloading malware.
5. VMware Carbon Black Endpoint - Best for a Range of Integrations
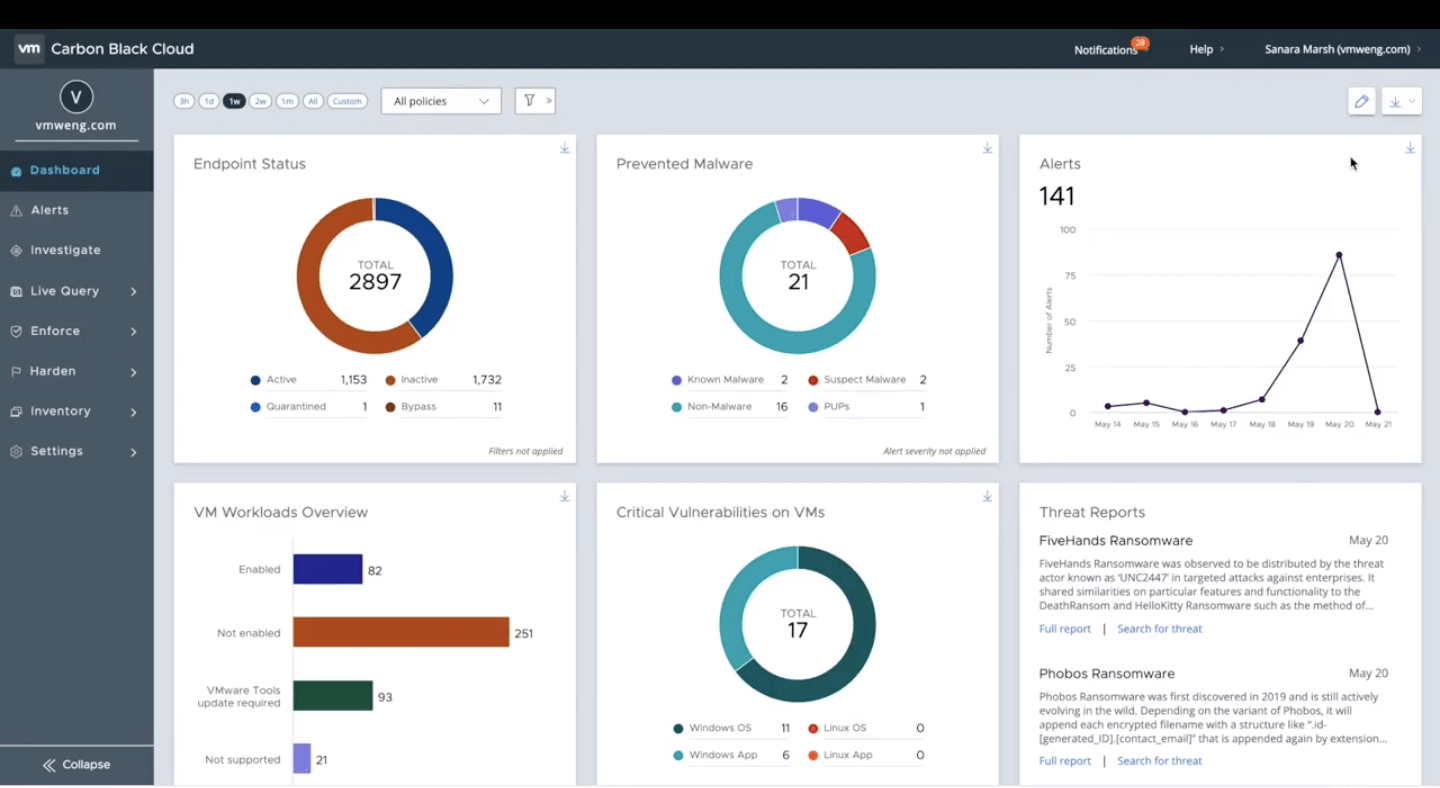
VMware Carbon Black Endpoint analyzes endpoint behavior and uses machine learning algorithms to find and flag suspicious activities, providing enhanced threat detection capabilities.
What I like about Carbon Black is that it provides 140+ integration options so that you can integrate it with your current workflows. Integrations are natively built for Splunk, ServiceNow, Netskope, LogRhythm, Exabeam, and Sumo Logic.
Limitations of Endpoint Security
Suppose you’ve chosen the right tool for your organization. Great! But your journey isn’t over yet. In my cybersecurity career, I’ve seen that there can still be some roadblocks with implementation and ongoing management.
Here are a few obstacles to be prepared for.
Complex Environments
When protecting their endpoints, organizations may have a diverse range of operating systems, platforms, and devices in their network. This can include different versions of Windows, macOS, and Linux or mobile devices like iOS and Android.
Each platform may require specific security measures and configurations to ensure protection against threats. For instance, when deploying a web application on a cloud platform like AWS, you might need to set up security groups and network access control lists (ACLs) and configure web application firewalls (WAFs) to protect against potential attacks. On the other hand, when deploying a mobile app on iOS, you may need to consider securing user data with encryption and adhering to Apple's guidelines on data privacy and security.
You may also have a complex network with numerous access points, routers, and switches, which increase the attack surface. This diversity makes it challenging to implement a uniform security solution that covers all endpoints effectively.
Further, organizations may have a large and diverse workforce, including remote employees, contractors, and partners. Managing and securing endpoints for this dynamic workforce can be challenging.
False Positives and Negatives
False positives occur when a security solution mistakenly identifies a harmless activity or file as malicious. This can lead to unnecessary alerts or actions, such as blocking legitimate user activities or quarantining harmless files. False positives can affect productivity and create frustration for users and administrators.
On the other hand, false negatives occur when a security solution fails to detect a genuine threat. This can happen for several reasons, such as outdated threat intelligence, new and unknown attack techniques, or sophisticated evasion tactics employed by cybercriminals. False negatives can leave endpoints vulnerable to attacks and result in security breaches.
User Awareness and Education
User awareness and education are essential components of a comprehensive endpoint security strategy. While endpoint security solutions can protect against known threats, user actions and behaviors can still introduce vulnerabilities.
For example, a user may receive an email that appears to be from a legitimate company or organization, asking them to click on a link or provide sensitive information. If the user is unaware of the signs of a phishing attempt, they may unknowingly fall for it and cause a security breach.
By educating users about common types of social engineering attacks and best practices for identifying and responding to them, organizations can empower their employees to be more cautious and vigilant.
Evolving Threats
The biggest challenge cybersecurity professionals encounter with their current endpoint protection solution is insufficient protection against the newest attacks.
As a result, endpoint security solutions must continuously adapt and evolve to effectively detect and mitigate these emerging threats. This requires regular updates to threat intelligence feeds, which provide information about the latest malware signatures and attack patterns.
Furthermore, as new vulnerabilities are discovered in operating systems and software, endpoint security solutions need to be able to quickly apply patches or updates to address these vulnerabilities. This requires regular monitoring and communication with software vendors.
Bring Your Own Device (BYOD)
BYOD can present challenges in adopting endpoint security tools, mainly due to the sprawling complexity introduced by the increasing use of mobile and IoT devices. For example, there are already 14.3 billion active IoT endpoints globally.
Further, organizations may not have the same level of administrative control and visibility over BYOD devices and IoT devices. This can make it more difficult to enforce security policies and ensure that endpoint security tools are properly installed and configured on employee-owned devices.
BYOD can blur the line between personal and professional use of devices. Employees may have personal apps, email accounts, and files on their devices, which can increase the risk of data leakage.
If an employee's personal device is infected with malware or compromised by a cybercriminal, this can threaten the organization's data and systems. Endpoint security tools need to be able to detect and respond to such threats on employee-owned devices, which can be a complex task.
Best Practices to Adopt
While endpoint security measures aren't entirely foolproof, there are some best practices your organization can adopt to minimize risks and maximize security.
Regular Patching and Updates
By keeping operating systems, applications, and software up to date, organizations can effectively protect against known vulnerabilities.
To do so, you can use automated tools to streamline the patching process and ensure timely updates across all endpoints. You can establish a regular patch deployment schedule to ensure consistent updates without disrupting business operations.
If you have a centralized patch management system in place, it can help you generate reports to track patching progress and identify any gaps. Before deploying patches, you can conduct thorough testing to minimize potential system disruptions or compatibility issues.
Access Controls
Access controls are security measures that regulate and manage access to a system or resource. They determine what actions a user can perform on the system or resource and ensure that only authorized individuals can interact with a system.
Under access controls, you can:
- Implement robust authentication mechanisms such as multi-factor authentication (MFA) to ensure only authorized individuals can access endpoints
- Implement strong password policies, including regular password changes and the use of complex passwords
- Whitelist applications through which you can control which applications can run on the endpoints
- Use role-based access control (RBAC) to assign appropriate privileges based on user roles and responsibilities
- Use least privilege principles to restrict access to only necessary resources
- Employ encryption to protect sensitive data on endpoints, like full-disk and file-level encryption
- Use secure connection protocols like Secure Sockets Layer (SSL) or a Virtual Private Network (VPN) to authenticate users and verify their identities before granting access to an endpoint
- Regularly monitor and analyze access logs for suspicious activities
Network Segmentation
Network segmentation is a method to divide a computer network into smaller subnetworks called segments. For example, organizations can create separate segments for different user groups or departments, such as finance, HR, and IT.
By segregating different parts of a network, organizations can limit access to sensitive data and resources, making it more difficult for attackers to move laterally within the network.
One common approach to network segmentation is using virtual LANs (VLANs). VLANs allow for logical separation of devices within a physical network, reducing the surface area that an attacker can exploit.
Employee Training and Awareness
Raising awareness about the latest threats helps to instill a culture of security within the organization and reduce the risk of human error and social engineering attacks. Some activities that you can undertake here are:
- Share information about common attack vectors and social engineering techniques
- Conduct simulated phishing exercises to assess employee awareness and response
- Offer incentives or rewards for employees who demonstrate good security practices
- Offer specialized training for employees in high-risk roles
- Collaborate with IT and security teams to ensure training aligns with organizational security policies and procedures
- Train employees on incident response planning—define roles and responsibilities, establish communication protocols, and outline the steps to be taken during and after an incident
- Regularly update training materials and resources to stay current with evolving security risks
Continuous Monitoring and Threat Intelligence
By combining continuous monitoring with threat intelligence, organizations can proactively identify vulnerabilities, detect anomalous behavior, and mitigate threats before they cause significant damage. This approach ensures that endpoint security practices are always up-to-date and aligned with the latest threats, offering a higher level of protection against cyberattacks.
Organizations can implement an endpoint security platform with threat management and monitoring features. They offer centralized management, allowing organizations to streamline security operations and maintain visibility over all endpoints.
Prioritize Endpoint Security
As businesses face evolving cyber threats, prioritizing endpoint security remains crucial for maintaining a solid defense against potential attacks. The landscape of cybersecurity threats poses new challenges to organizations daily. To deepen your understanding of how to counter these threats, exploring a range of insightful cybersecurity books can provide foundational knowledge and advanced strategies.
Staying ahead of these threats requires not only up-to-date knowledge but also a community of informed leaders sharing insights and strategies. There are many noteworthy cybersecurity resources available for you to learn more.
For CTOs and tech leaders at the forefront of cybersecurity innovation and defense, join our newsletter for expert advice and cutting-edge solutions in endpoint security.