Best Vulnerability Management Tools Shortlist
Here’s my shortlist of the best vulnerability management tools:
Our one-on-one guidance will help you find the perfect fit.
Keeping up with security threats isn’t easy when vulnerabilities constantly emerge, and patching them manually is time-consuming. If your team struggles with prioritizing threats, managing false positives, or maintaining compliance, vulnerability management tools can simplify the process.
I've tested and evaluated these tools with a focus on threat detection, automation, and risk prioritization. From my experience working with security teams, I know how critical it is to balance thorough coverage with minimal disruption. This guide will give you a clear, unbiased look at the top solutions to help you reduce risk, automate patching, and stay compliant—without adding unnecessary complexity.
Why Trust Our Software Reviews
We’ve been testing and reviewing SaaS development software since 2023. As tech experts ourselves, we know how critical and difficult it is to make the right decision when selecting software. We invest in deep research to help our audience make better software purchasing decisions.
We’ve tested more than 2,000 tools for different SaaS development use cases and written over 1,000 comprehensive software reviews. Learn how we stay transparent & check out our software review methodology.
Best Vulnerability Management Tools Summary
This comparison chart summarizes pricing details for my top Vulnerability Management Tools selections to help you find the best one for your budget and business needs.
| Tool | Best For | Trial Info | Price | ||
|---|---|---|---|---|---|
| 1 | Best for third-party vendor risk assessments | Free demo available | Pricing upon request | Website | |
| 2 | Best for continuous vulnerability monitoring | 14-day free trial + demo available | From $99/month | Website | |
| 3 | Best for comprehensive code-to-cloud security | Free plan available + free demo | From $350/month | Website | |
| 4 | Best for zero-configuration security insights | Free plan + demo available | Pricing upon request | Website | |
| 5 | Best for multi-framework compliance management | 30-day free trial | From $99/month | Website | |
| 6 | Best for extensive device and protocol coverage | Not available | Pricing upon request | Website | |
| 7 | Best for integration with Microsoft ecosystem | Not available | From $10/user/month (billed annually) | Website | |
| 8 | Best for attack surface management | Free demo available | Pricing upon request | Website | |
| 9 | Best for managed detection and response services | Not available | Pricing upon request | Website | |
| 10 | Best for multi-cloud environment security | Not available | Pricing upon request | Website |
-

Docker
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.6 -

Pulumi
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.8 -

GitHub Actions
Visit Website
Best Vulnerability Management Tool Reviews
Below are my detailed summaries of the best Vulnerability Management Tools that made it onto my shortlist. My reviews offer a detailed look at the key features, pros & cons, integrations, and ideal use cases of each tool to help you find the best one for you.
Prevalent is a third-party risk management platform that helps organizations assess and monitor the risks associated with their vendors and suppliers. By automating the collection and analysis of vendor data, Prevalent enables you to focus on reducing risk and ensuring compliance throughout your vendor ecosystem.
Why I Picked Prevalent: As a vulnerability management tool, Prevalent offers cyber intelligence to help you identify and address potential security issues within your vendor network. It monitors over 550,000 companies for cyber incidents by tracking more than 1,500 criminal forums, numerous dark web pages, and various threat feeds. This extensive monitoring allows you to stay informed about vulnerabilities and take proactive measures to protect your organization.
Standout features & integrations:
Features include automated onboarding and offboarding processes, simplifying the management of vendor relationships. The platform also includes a vendor dashboard that centralizes security, performance, and compliance reporting, making it easier for your team to monitor and address risks. Furthermore, Prevalent provides built-in remediation guidance.
Integrations include Active Directory, BitSight, ServiceNow, SecZetta, and Source Defense.
Pros and cons
Pros:
- Strong security protocols to protect data
- Users can tailor reports according to specific needs
- Extensive functionalities for managing vendor risk
Cons:
- Challenges in migrating data can complicate the initial setup
- The platform is complex and comes with a learning curve
Intruder is a cloud-based vulnerability management tool that helps you identify and address security weaknesses in your digital infrastructure.
Why I Picked Intruder: Intruder's continuous vulnerability management ensures your systems are regularly scanned for new threats. This feature automatically initiates scans when changes are detected, helping you stay ahead of potential security risks. Additionally, Intruder's attack surface management discovers unknown assets like subdomains and untracked APIs, providing a comprehensive view of your organization's exposure. It also offers exposure management, which combines multiple scanning engines to identify over a thousand attack surface issues that other scanners might miss.
Standout features & integrations:
Features include prioritization that leverages the latest threat intelligence, such as CISA's Known Exploited Vulnerabilities list and machine learning-driven exploitation predictions. It also offers private bug bounty access, allowing your team to collaborate with elite hackers to uncover vulnerabilities that automated scanners might overlook.
Integrations include AWS, Azure, Google Cloud, Drata, Jira, Azure DevOps, GitHub, GitLab, ServiceNow, Cloudflare, Microsoft Sentinel, and Okta.
Pros and cons
Pros:
- Compliance reporting capabilities
- Automated scanning and monitoring
- Comprehensive vulnerability detection
Cons:
- Attack surface feature limited to premium plan
- Occasional false positives
Aikido Security is an all-in-one platform that helps you identify and fix vulnerabilities in your code and cloud environments. It offers a range of tools to detect security risks, from static code analysis to cloud posture management.
Why I Picked Aikido Security: Aikido's static code analysis (SAST) scans your source code to spot vulnerabilities like SQL injection and cross-site scripting before they become issues. This proactive approach lets your team address potential threats early, enhancing your application's security. Additionally, Aikido's secret detection feature checks your code for exposed API keys, passwords, and other sensitive information, preventing accidental leaks that could be exploited.
Standout features & integrations:
Features include its cloud posture management (CSPM) capabilities that detect risks in your cloud infrastructure across major providers, helping you maintain a secure cloud environment. Aikido also offers infrastructure as code (IaC) scanning, open-source dependency scanning, container image scanning, surface monitoring, and malware detection in dependencies.
Integrations include Amazon Web Services (AWS), Google Cloud, Microsoft Azure Cloud, Drata, Vanta, AWS Elastic Container Registry, Docker Hub, Jira, Asana, and GitHub.
Pros and cons
Pros:
- Scalable for growing teams
- Offers actionable insights
- Has a comprehensive dashboard and customizable reports
Cons:
- Only available in English
- Ignores vulnerabilities if no fix is available
New Product Updates from Aikido Security
Aikido Security's July 2025 Update: NodeJS Safe-chain, Tuxcare Libraries, and IDE Enhancements
Aikido Security's update on July 22, 2025, introduced NodeJS Safe-chain, hardened libraries through Tuxcare, and IDE enhancements, including AutoFix in Visual Studio. More details can be found at Aikido Security Changelog.
New Relic is an all-in-one observability platform designed to help you monitor, debug, and improve your entire software stack. It offers a range of tools to ensure your applications run smoothly and securely.
Why I Picked New Relic: I chose New Relic for its ability to provide continuous runtime software composition analysis (SCA) and vulnerability assessment without requiring additional configuration. This means you can instantly detect common vulnerabilities and exposures (CVEs) across your application's dependencies, helping you identify potential security risks early in the development process.
Standout features & integrations:
Features include enhanced prioritization analytics that help you prioritize which risks need immediate attention by incorporating data like the Exploit Prediction Scoring System (EPSS). It is also an open ecosystem that enables easy integration with your existing security assessment tools.
Integrations include AWS, Google Cloud Platform, Microsoft Azure, Slack, Atlassian Jira, AWS EventBridge, Email Notifications, Mobile Push Notifications, Opsgenie, PagerDuty, ServiceNow, and Prometheus.
Pros and cons
Pros:
- Wide range of integrations with cloud platforms and development tools
- Offers real-time tracking and detailed error logging
- Provides comprehensive monitoring and alerting capabilities
Cons:
- Dashboards may require customization for specific use cases
- Learning curve for new users
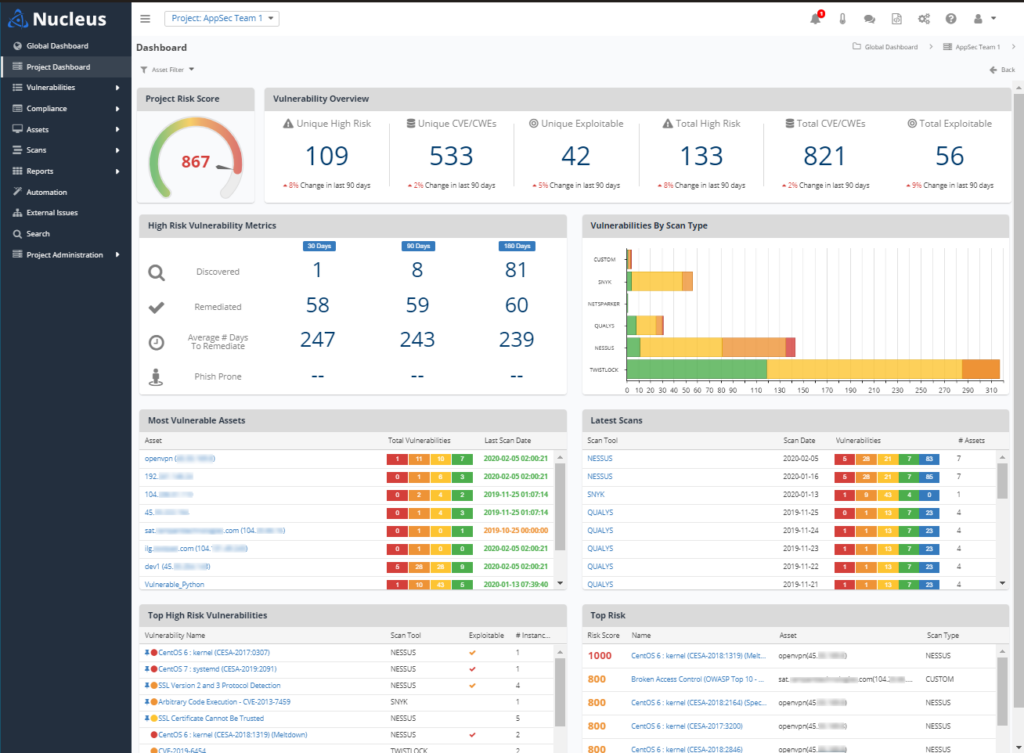
Nucleus is a robust vulnerability management solution built to handle complex security environments. Its key strength lies in facilitating multi-framework compliance management, making it a unique player in vulnerability management.
Why I Picked Nucleus: Nucleus stands out for its ability to manage multi-framework compliance and consolidate data from various security tools. I chose Nucleus as the best for multi-framework compliance management since it's uniquely tailored to handle different security frameworks simultaneously, a feature that most other tools lack.
Standout features & integrations:
Some key features of Nucleus include risk-based vulnerability management and streamlined reporting. It also provides threat intelligence feeds to stay updated with emerging new vulnerabilities.
For integrations, Nucleus supports a wide range of security tools, including vulnerability scanners like Nessus, Burp Suite, and OWASP ZAP, allowing it to serve as a central hub for security data.
Pros and cons
Pros:
- Supports wide range of security tools
- Offers risk-based vulnerability management
- Facilitates multi-framework compliance management
Cons:
- Advanced features may require dedicated staff to manage effectively
- The user interface might be complex for beginners
- Pricing information not readily available
Cisco Vulnerability Management is a robust security solution that offers an expansive range of device and protocol coverage. The tool scans your network to identify and manage vulnerabilities, making it an excellent choice for those seeking to secure diverse device environments and protocols.
Why I Picked Cisco Vulnerability Management: I chose Cisco Vulnerability Management primarily because of its wide device and protocol coverage, which is critical for businesses operating in a mixed environment. I determined this tool to be unique in its capability to cover many devices and protocols, making it best for organizations that utilize the diverse technological infrastructure.
Standout features & integrations:
Key features of Cisco Vulnerability Management include robust scanning capabilities, extensive device and protocol support, and advanced reporting.
Its integrations are also impressive, with connectivity to other Cisco security products and third-party security systems, broadening its utility and effectiveness within your security ecosystem.
Pros and cons
Pros:
- Integration with Cisco and third-party security systems
- Advanced reporting capabilities
- Extensive device and protocol coverage
Cons:
- Limited customization features for reporting and dashboards
- May have a steep learning curve for new users
- Pricing details are not readily available
Best for integration with Microsoft ecosystem
Microsoft Defender Vulnerability Management is a comprehensive security tool designed to identify, assess, and mitigate vulnerabilities. It fits into the Microsoft ecosystem, providing an integrated solution for businesses heavily invested in Microsoft products.
Why I Picked Microsoft Defender Vulnerability Management: I selected Microsoft Defender Vulnerability Management because it integrates with the Microsoft ecosystem. Given its native integration with products like Windows, Office 365, and Azure, it provides a unified security solution that stands apart from many competitors. It also supports macOS, Linux, Android and iOS, and some network devices. Therefore, this tool is best for businesses that have a strong reliance on Microsoft products.
Standout features & integrations:
Microsoft Defender Vulnerability Management offers advanced threat analytics, vulnerability assessment, and threat & vulnerability management.
Its most notable aspect is its integration with the Microsoft ecosystem, including Microsoft 365 Defender, Microsoft Defender for Endpoint, and Azure Security Center, contributing to a more consolidated and effective security posture.
Pros and cons
Pros:
- Effective vulnerability assessment and management
- Advanced threat analytics feature
- Integration with Microsoft ecosystem
Cons:
- Limited customization options for reports and dashboards
- Pricing can be high for smaller organizations
- Less effective for non-Microsoft systems
CyCognito is a cloud-based vulnerability management platform designed to uncover and prioritize security gaps across your external infrastructure. Its standout capability is discovering unknown or unmanaged assets without requiring pre-configured inputs, which gives security teams visibility into blind spots often missed by traditional scanners.
Why I Picked CyCognito: I chose CyCognito because it addresses a fundamental issue in vulnerability management—lack of visibility. While many tools rely on a known asset inventory, CyCognito starts with external reconnaissance, helping you find what’s exposed before attackers do. I also appreciate its ability to contextualize discovered risks, ranking them based on exploitability and potential business impact. For CTOs managing complex or hybrid environments, this external-first model adds significant value.
Standout Features & Integrations:
Features include external risk discovery powered by machine learning, exploit intelligence that maps vulnerabilities to real-world attack paths, and automated prioritization to help teams focus on high-impact fixes. Its remediation acceleration tools integrate with common ticketing and SOAR platforms to streamline handoff and validation.
Integrations include ServiceNow, Splunk, Jira, Microsoft Sentinel, Slack, Axonius, Wiz, IBM QRadar, Cortex XSOAR, JupiterOne, Armis, Microsoft Teams, Tenable, and AWS S3.
Pros and cons
Pros:
- Strong exploit intelligence and prioritization
- Detailed reports and continuous testing
- Intuitive interface with great visibility
Cons:
- Reporting lacks customization for some roles
- Limited control over testing configurations
Arctic Wolf is a risk-based vulnerability management service that helps prevent cyberattacks before they occur. Its services include monitoring, threat detection, and response, making it an excellent fit for businesses seeking comprehensive managed security services.
Why I Picked Arctic Wolf: I chose Arctic Wolf for this list because it specializes in Managed Detection and Response. This focus on MDR services sets it apart from generalist tools, making it an excellent choice for businesses that need specialized attention to security threats. The platform’s risk-scoring mechanism helps users determine the most mission-critical vulnerabilities. I believe Arctic Wolf is best for managed detection and response services.
Standout features & integrations:
Arctic Wolf's services include around-the-clock risk monitoring, threat hunting, and risk management. Moreover, it offers a cloud-native security platform,
Arctic Wolf Platform, which integrates well with existing IT infrastructure, making it easier for businesses to improve their security stance.
Pros and cons
Pros:
- Cloud-native platform integrates well with existing IT infrastructure
- Offers 24/7 monitoring and threat hunting
- Specializes in Managed Detection and Response
Cons:
- Less suitable for businesses looking for a simple, standalone tool
- Could be overkill for smaller organizations
- Pricing information is not transparent
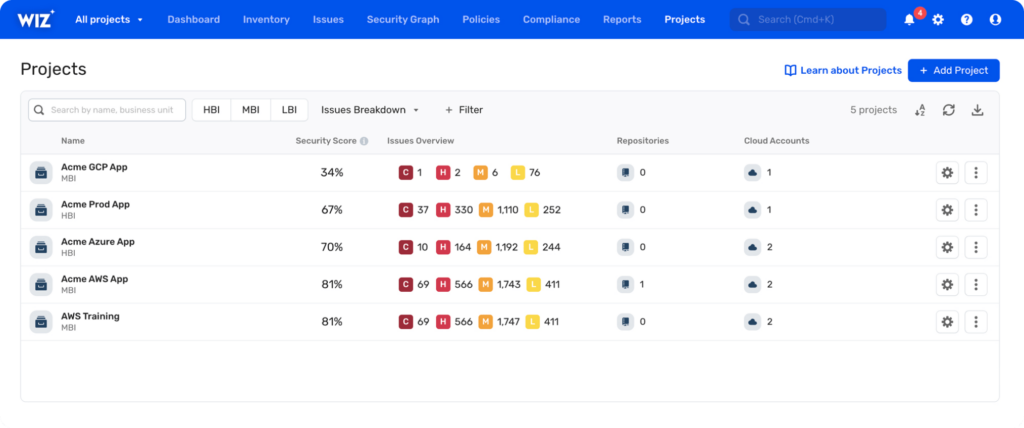
Wiz is a vulnerability management tool that provides security visibility across all multi-cloud environments. Its ability to analyze workloads, network data, and configurations makes it ideal for organizations operating in multi-cloud ecosystems.
Why I Picked Wiz Vulnerability Management: I chose Wiz for its holistic approach to multi-cloud security. It differentiates itself with its ability to provide visibility across all public clouds (AWS, GCP, Azure, and Oracle Cloud), even if multiple vendors manage them. Considering the increasing adoption of multi-cloud strategies, I determined that Wiz is the best option for multi-cloud environment security.
Standout features & integrations:
Wiz's notable features include comprehensive vulnerability scanning tools, advanced risk prioritization, and Cloud Security Posture Management (CSPM).
Furthermore, it offers robust integrations with popular DevOps tools such as Jira, Slack, and Microsoft Teams to streamline the vulnerability management workflow.
Pros and cons
Pros:
- Integrations with popular DevOps tools
- Advanced risk prioritization feature helps in effective vulnerability management
- Offers comprehensive visibility across multi-cloud environments
Cons:
- Dependence on integrations for workflow management may not suit all teams
- May have features that are too advanced or unnecessary for small businesses
- Lack of transparent pricing could be a deterrent for some potential users
Other Vulnerability Management Tools
Here are some additional vulnerability management tools options that didn’t make it onto my shortlist, but are still worth checking out:
- Tenable Vulnerability Management
For active directory and infrastructure security
- CYRISMA
For intuitive user interface and automated patching
- IBM Security QRadar EDR
For comprehensive threat intelligence
- Frontline Vulnerability Manager
For cloud and network security integration
- InsightVM (Nexpose)
For real-time end-to-end visibility
- Qualys VMDR
For comprehensive IT asset management
- Adlumin
For financial sector-focused security
- Astra Pentest
For comprehensive vulnerability scanning
- Resolver
Good for integrating risk management across business operations
- ManageEngine Vulnerability Manager Plus
Good for unified vulnerability management and patching
- SanerNow
Good for combined vulnerability management and patch remediation
- HostedScan
Good for providing quick and easy external vulnerability scans
- Continuity Software
Good for business continuity planning and incident management
- Brinqa
Good for risk-based vulnerability management
- Aqua Security
Good for cloud-native application protection
- VulScan
Good for comprehensive internal and external vulnerability scanning
- ServiceNow Security Operations
Good for security incident response and vulnerability response workflows
Vulnerability Management Tool Selection Criteria
When selecting the best Vulnerability Management Tools to include in this list, I considered common buyer needs and pain points like integration with existing IT infrastructure and real-time threat detection. I also used the following framework to keep my evaluation structured and fair:
Core Functionality (25% of total score)
To be considered for inclusion in this list, each solution had to fulfill these common use cases:
- Identify vulnerabilities
- Prioritize threats
- Provide remediation guidance
- Offer compliance reporting
- Conduct continuous monitoring
Additional Standout Features (25% of total score)
To help further narrow down the competition, I also looked for unique features, such as:
- Cloud-native security
- Automated patch management
- Threat intelligence integration
- Real-time analytics
- Customizable dashboards
Usability (10% of total score)
To get a sense of the usability of each system, I considered the following:
- Intuitive interface design
- Easy navigation
- Minimal learning curve
- Customizable user settings
- Efficient workflow integration
Onboarding (10% of total score)
To evaluate the onboarding experience for each platform, I considered the following:
- Availability of training videos
- Interactive product tours
- Access to templates
- Webinars and workshops
- Responsive chatbots
Customer Support (10% of total score)
To assess each software provider’s customer support services, I considered the following:
- 24/7 support availability
- Multiple support channels
- Knowledgeable support staff
- Comprehensive documentation
- Fast response times
Value For Money (10% of total score)
To evaluate the value for money of each platform, I considered the following:
- Competitive pricing
- Feature set versus cost
- Flexible pricing plans
- Discounts for annual subscriptions
- Transparent pricing structure
Customer Reviews (10% of total score)
To get a sense of overall customer satisfaction, I considered the following when reading customer reviews:
- Overall satisfaction ratings
- Feedback on feature effectiveness
- Comments on ease of use
- Opinions on customer support
- Value-for-money perceptions
How to Choose a Vulnerability Management Tool
It’s easy to get bogged down in long feature lists and complex pricing structures. To help you stay focused as you work through your unique software selection process, here’s a checklist of factors to keep in mind:
| Factor | What to Consider |
| Scalability | Ensure the tool can grow with your business. Consider if it can handle increased data loads and more users without compromising performance. |
| Integrations | Check if the tool integrates with your existing software, such as SIEM systems, ticketing tools, and cloud services, to streamline workflows. |
| Customizability | Look for customization options that let you tailor dashboards, reports, and alerts to fit your team’s specific needs and preferences. |
| Ease of Use | Choose a tool with an intuitive interface and minimal learning curve to ensure quick adoption by your team. |
| Budget | Evaluate the cost against the features offered. Consider flexible pricing plans that fit your financial constraints and provide value for money. |
| Security Safeguards | Assess the tool's ability to protect sensitive data and comply with industry regulations, ensuring robust security measures are in place. |
| Vendor Support | Consider the vendor's reputation for customer support, including availability, response time, and the resources they provide for troubleshooting. |
| Reporting Features | Look for comprehensive reporting capabilities that provide insights into vulnerabilities and compliance, helping you make informed security decisions. |
Trends in Vulnerability Management Tool
In my research, I sourced countless product updates, press releases, and release logs from different Vulnerability Management Tools vendors. Here are some of the emerging trends I’m keeping an eye on:
- AI-Powered Threat Detection: Vendors are using artificial intelligence to enhance threat detection capabilities. AI can identify patterns and anomalies faster than traditional methods, helping teams respond to threats more quickly. Some tools are incorporating machine learning to predict potential vulnerabilities.
- Cloud-Native Security: As more businesses move to the cloud, tools are evolving to provide better cloud-native security features. This trend is crucial for companies relying heavily on cloud infrastructure, offering deeper insights into cloud-specific vulnerabilities.
- Zero Trust Security Models: More tools are adopting zero trust models, which require verification for every user and device. This approach enhances security by assuming threats could be internal or external. Vendors like Cisco are integrating zero trust principles into their platforms.
- Enhanced Reporting Capabilities: Detailed and customizable reporting is becoming more important. Users need insights into vulnerabilities and compliance status. Tools are offering more advanced reporting features to meet these demands, allowing for better risk management.
- User Behavior Analytics: Some vendors are incorporating user behavior analytics to monitor and identify unusual activities. This trend helps detect insider threats and compromised accounts, adding another layer of security for businesses.
What Are Vulnerability Management Tools?
Vulnerability Management Tools are software solutions designed to identify, assess, and manage security vulnerabilities in IT systems. These tools are generally used by IT security professionals and network administrators to protect their organizations from potential threats and ensure compliance with security standards. Features like AI-powered threat detection, cloud-native security, and enhanced reporting capabilities help with identifying vulnerabilities, managing risks, and maintaining a secure environment. Overall, these tools help businesses stay ahead of potential security threats and protect sensitive data.
Features of Vulnerability Management Tools
When selecting Vulnerability Management Tools, keep an eye out for the following key features:
- AI-powered threat detection: Uses artificial intelligence to quickly identify patterns and anomalies, helping teams respond to threats faster.
- Cloud-native security: Provides specialized security features for cloud environments, offering insights into cloud-specific vulnerabilities.
- Zero trust security models: Requires verification for every user and device, enhancing security by assuming all access could be a threat.
- Enhanced reporting capabilities: Offers customizable and detailed reports that provide insights into vulnerabilities and compliance status.
- User behavior analytics: Monitors and identifies unusual user activities to detect insider threats and compromised accounts.
- Risk prioritization: Helps teams focus on the most critical vulnerabilities by assessing and ranking potential threats.
- Automated patch management: Streamlines the process of applying security patches, reducing manual workload and minimizing vulnerabilities.
- Continuous monitoring: Provides ongoing assessment of the network to detect new vulnerabilities as they arise.
- Compliance reporting: Ensures that security measures meet industry standards and regulations, simplifying the compliance process.
- Customizable dashboards: Allows users to tailor their view of data and metrics to fit specific needs and preferences.
Benefits of Vulnerability Management Tools
Implementing Vulnerability Management Tools provides several benefits for your team and your business. Here are a few you can look forward to:
- Improved security posture: By identifying and managing vulnerabilities, these tools help protect your systems from potential threats and reduce security risks.
- Efficient risk management: Risk prioritization features allow your team to focus on the most critical vulnerabilities, ensuring resources are used effectively.
- Enhanced compliance: Compliance reporting helps you meet industry standards and regulations, simplifying audits and reducing compliance-related stress.
- Time savings: Automated patch management and continuous monitoring reduce manual tasks, freeing up your team to focus on other important activities.
- Informed decision-making: Detailed reporting and analytics provide insights that support better security decisions and strategies.
- Increased visibility: Features like cloud-native security and user behavior analytics give you a clearer view of your network and potential threats.
- Proactive threat detection: AI-powered threat detection enables faster identification and response to vulnerabilities, keeping your systems secure.
Costs and Pricing of Vulnerability Management Tools
Selecting Vulnerability Management Tools requires an understanding of the various pricing models and plans available. Costs vary based on features, team size, add-ons, and more. The table below summarizes common plans, their average prices, and typical features included in Vulnerability Management Tools solutions:
Plan Comparison Table for Vulnerability Management Tools
| Plan Type | Average Price | Common Features |
| Free Plan | $0 | Basic vulnerability scanning, limited reporting, and community support. |
| Personal Plan | $5-$25/user/month | Standard scanning capabilities, risk prioritization, and basic compliance checks. |
| Business Plan | $30-$60/user/month | Advanced analytics, automated patch management, and customizable dashboards. |
| Enterprise Plan | $70-$150/user/month | Comprehensive reporting, AI-powered threat detection, and dedicated support. |
Vulnerability Management Tools (FAQs)
Here are some answers to common questions about Vulnerability Management Tools:
How do vulnerability management tools work?
Vulnerability management tools assess your network using IP scanners, network and port scanners, and more. They prioritize issues to ensure the most critical weaknesses are fixed first and suggest practical remediation steps. This process helps secure your systems by addressing vulnerabilities promptly.
What is common with most vulnerability assessment tools?
A key feature of vulnerability assessment tools is their ability to scan your systems. They run automated scans across your network, analyzing every device, application, and system for potential vulnerabilities. This automation ensures comprehensive coverage and efficient vulnerability detection.
What are the typical pricing models for vulnerability management tools?
A key feature of vulnerability assessment tools is their ability to scan your systems. They run automated scans across your network, analyzing every device, application, and system for potential vulnerabilities. This automation ensures comprehensive coverage and efficient vulnerability detection.
What is the disadvantage of an automated vulnerability tool scan?
Automated vulnerability tool scans have some drawbacks. They might not detect newly discovered vulnerabilities or complex ones that are hard to automate. This limitation means you might need manual checks to ensure comprehensive security coverage.
How often should vulnerability scans be performed?
The frequency of vulnerability scans depends on your organization’s needs and risk tolerance. Generally, it’s best to perform scans regularly, such as weekly or monthly, to ensure continuous protection against emerging threats. Regular scans help maintain a strong security posture.
Can vulnerability management tools integrate with existing security systems?
Yes, many vulnerability management tools can integrate with existing security systems. This integration allows for seamless data sharing and improved threat management. By working with your current infrastructure, these tools enhance your overall security strategy.
What's Next?
Boost your SaaS growth and leadership skills. Subscribe to our newsletter for the latest insights from CTOs and aspiring tech leaders. We'll help you scale smarter and lead stronger with guides, resources, and strategies from top experts!