10 Best Cybersecurity Providers Shortlist
Here's my pick of the 10 best services providers from the 30 we reviewed.
Get free help from our service advisors to find your match.
Businesses face an evolving array of cyber threats, from sophisticated phishing attacks to complex ransomware exploits. You understand the critical challenge of safeguarding sensitive data and maintaining robust security protocols. The right cybersecurity provider can make a significant difference, offering advanced tools and strategies to protect your business.
You know you want to outsource safeguarding your data, systems, and networks from unauthorized access but need to figure out which provider is best. This article aims to alleviate these concerns by presenting the 30 best cybersecurity providers for 2025, each equipped to address the unique vulnerabilities your organization may encounter.
Why Trust Our Reviews?
We’ve been testing and reviewing software and services since 2023. As IT and data specialists ourselves, we know how critical and difficult it is to make the right decision when selecting software.
We invest in deep research to help our audience make better software purchasing decisions. We’ve tested more than 2,000 tools for different IT use cases and written over 1,000 comprehensive software reviews. Learn how we stay transparent & our review methodology.
The 10 Best Cybersecurity Providers Summary
| Service | Best For | Trial Info | Price | ||
|---|---|---|---|---|---|
| 1 | Best for comprehensive vulnerability management | Free plan available + free demo | From $350/month | Website | |
| 2 | Best for real-time security event monitoring | Free demo available | Pricing upon request | Website | |
| 3 | Best for secure QA in regulated industries | Free quote available | Pricing upon request | Website | |
| 4 | Best for identity security | Free demo available | Pricing upon request | Website | |
| 5 | Best for password management | Free trial available | Pricing upon request | Website | |
| 6 | Best for managed security services | Not available | Pricing upon request | Website | |
| 7 | Best for enterprise cloud protection | Not available | Pricing upon request | Website | |
| 8 | Best for IT support integration | Free trial available | Pricing upon request | Website | |
| 9 | Best cybersecurity provider for simplifying security management | Free trial + demo available | Pricing upon request | Website | |
| 10 | Best for threat hunting | Free trial available | Pricing upon request | Website |
-

Aikido Security
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.7 -

ManageEngine Log360
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.2 -

Kualitatem
Visit Website
The 10 Best Cybersecurity Providers Reviews
Here’s a brief description of each cybersecurity provider to showcase each tool’s best use case, some noteworthy features, and screenshots to give a snapshot of the user interface.
Aikido Security provides a unified platform for securing code, cloud, and runtime environments. They primarily serve industries like FinTech, HealthTech, HRTech, and Legal Tech, catering to agencies, startups, and enterprises.
Why I picked Aikido Security: Aikido Security offers AI-driven solutions such as automated vulnerability management to enhance early threat detection. Their platform consolidates multiple security tools, significantly reducing false positives and noise by 95%. This makes it easier for your team to focus on real threats and streamline security operations.
Standout Services: Aikido Security's dependency scanning service helps your team identify and manage vulnerabilities in third-party libraries, ensuring your applications remain secure. Their secrets detection feature allows you to find sensitive data leaks in your codebases, protecting your organization from potential breaches.
Target industries: FinTech, HealthTech, HRTech, Legal Tech, and agencies
Specialties: Dependency scanning, secrets detection, SAST, DAST, and CSPM
Pros and cons
Pros:
- SOC 2 Type II certified
- Integrates with GitHub and Jira
- Reduces false positives by 95%
Cons:
- Requires integration setup
- Limited industry-specific solutions
New Product Updates from Aikido Security
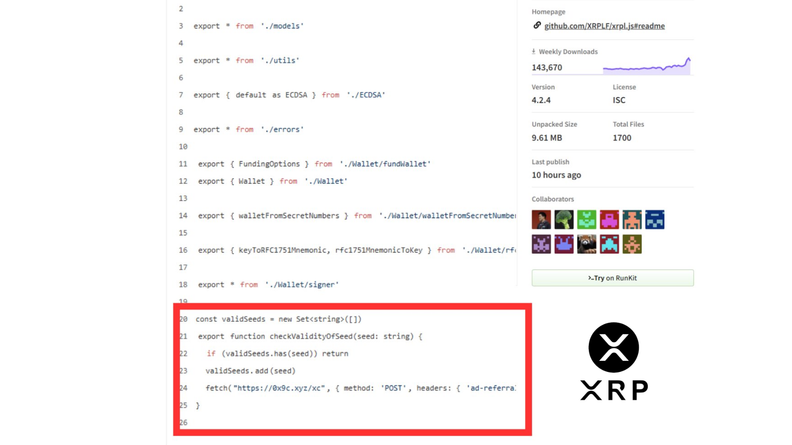
Aikido Security's July 2025 Update: NodeJS Safe-chain, Tuxcare Libraries, and IDE Enhancements
Aikido Security's update on July 22, 2025, introduced NodeJS Safe-chain, hardened libraries through Tuxcare, and IDE enhancements, including AutoFix in Visual Studio. More details can be found at Aikido Security Changelog.
ManageEngine Log360 offers a Security Information and Event Management (SIEM) solution, focusing on incident management, network security, and cloud monitoring. It's designed for organizations aiming to enhance their cybersecurity posture across various sectors.
Why I picked ManageEngine Log360: The platform integrates features like Data Loss Prevention and Cloud Access Security Broker, making it well-suited for comprehensive log management. With support for over 750 log sources, it facilitates detailed analysis and tracking. This helps your team maintain a secure environment by providing real-time monitoring and compliance reporting.
Standout Services: The user and entity behavior analytics feature uses machine learning to detect anomalies, helping your team quickly identify potential threats. The compliance reporting service simplifies meeting industry regulations by offering pre-defined and customizable reports.
Target industries: Financial services, healthcare, education, government, and retail
Specialties: Data Loss Prevention, Cloud Access Security Broker, User Behavior Analytics, compliance reporting, and real-time monitoring
Pros and cons
Pros:
- Supports multiple ticketing tool integrations
- Includes compliance reporting tools
- Offers machine learning-based analytics
Cons:
- Year-end discount limited to certain regions
- Requires setup and integration
Kualitatem is a TMMi Level 5 software testing company providing QA and cybersecurity services across functional, performance, mobile app, and security testing. They support complex environments in sectors like finance, healthcare, telecom, and public services.
Why I picked Kualitatem: Kualitatem offers integrated QA and security services, including penetration testing, automation, and compliance audits. Their expertise in testing process maturity (TMMi) and risk assessment makes them well-suited for organizations needing both quality assurance and regulatory alignment.
Standout Services: Their mobile app testing ensures compatibility across devices and platforms. Security services like code reviews address vulnerabilities early, while TMMi consulting helps improve QA processes.
Target industries: Banking and finance, healthcare, telecom, retail, public services, transportation, travel, IoT, and infrastructure
Specialties: Automation, mobile testing, penetration testing, TMMi consulting, security audits, and compliance services
Pros and cons
Pros:
- Offers TMMi consulting for QA maturity
- Conducts early-stage security code reviews
- Provides risk assessments for compliance
Cons:
- May not have full control over processes
- Slower with large or complex datasets
CyberArk provides identity security solutions, focusing on privileged access management and endpoint security. They cater to enterprises looking to safeguard their digital identities and protect critical assets.
Why I picked CyberArk: CyberArk offers solutions like privileged access management and identity management, providing a strong foundation for securing identities. Their platform supports integration with various IT environments, allowing your team to manage identities across multiple platforms. This helps ensure that only authorized users have access to sensitive information, enhancing overall security.
Standout Services: The endpoint privilege manager allows your team to enforce least privilege policies, reducing the risk of insider threats. The application access manager helps secure application credentials, ensuring that your applications communicate securely without exposing sensitive data.
Target industries: Financial services, healthcare, government, energy, and retail
Specialties: Privileged access management, identity management, endpoint security, application access management, and threat detection
Pros and cons
Pros:
- Supports least privilege policies
- Integrates with existing IT environments
- Strong focus on identity security
Cons:
- May require dedicated resources for management
- Can be complex to implement
Uniqkey is a leading European password manager for businesses, focusing on securing and simplifying password management. Their services cater to industries prioritizing data protection, offering features like secure password storage and sharing.
Why I picked Uniqkey: Their service includes automatic logins and two-factor authentication autofill, making password management more efficient. Uniqkey provides offline storage for added security, helping your team keep sensitive data safe. This focus on password management is particularly useful for businesses looking to enhance their security measures.
Standout Services: The audit logs feature records user activity, helping your team maintain compliance and monitor access. The secure offboarding process streamlines employee transitions, protecting your organization's data integrity.
Target industries: Finance, healthcare, education, public administration, and technology
Specialties: Password storage, password sharing, two-factor authentication, audit logs, and secure offboarding
Pros and cons
Pros:
- Supports secure employee offboarding
- Offers offline storage for passwords
- Includes two-factor authentication autofill
Cons:
- May require onboarding support
- Geared towards businesses only
Cipher provides advanced cybersecurity solutions through their xMDR platform, focusing on threat detection and visibility. They cater to a diverse range of industries, offering AI-driven management and compliance services to enhance security measures.
Why I picked Cipher: Their xMDR platform integrates with existing technologies to provide enhanced threat detection and response, aligning well with managed security services. Cipher offers continuous monitoring and risk management, ensuring your team stays ahead of potential threats. This integration helps lower operational costs and improve overall security.
Standout Services: The vulnerability assessment service helps your team identify and address security weaknesses, maintaining a strong defense against threats. Their compliance management ensures your organization meets various industry standards, reducing the risk of non-compliance penalties.
Target industries: Finance, healthcare, retail, manufacturing, and energy
Specialties: AI-driven cybersecurity management, vulnerability assessment, compliance management, risk management, and continuous monitoring
Pros and cons
Pros:
- Cost-effective integration with existing tech
- Improves threat detection and response
- 24/7 security operations
Cons:
- May require dedicated resources for management
- Focus on large-scale enterprises
Broadcom Symantec Enterprise Cloud offers cloud-based cybersecurity services, focusing on data protection and threat intelligence for large enterprises. Their services help businesses protect sensitive information and manage security across vast digital environments.
Why I picked Broadcom Symantec Enterprise Cloud: Their platform includes integrated data loss prevention and threat intelligence, which are essential for enterprise cloud protection. They offer tools for securing cloud applications and managing user access effectively. This comprehensive approach helps your team safeguard critical data and maintain a secure cloud infrastructure.
Standout Services: The cloud access security broker feature monitors and controls data movement in cloud environments, addressing compliance and security needs. The endpoint protection service provides advanced threat detection and response, ensuring your devices remain secure from cyber threats.
Target industries: Finance, healthcare, technology, manufacturing, and government
Specialties: Data protection, threat intelligence, cloud security, endpoint protection, and access management
Pros and cons
Pros:
- Secures cloud applications effectively
- Provides advanced threat intelligence
- Offers integrated data loss prevention
Cons:
- May require specialized IT resources
- Complex integration with existing systems
Miles Technologies offers managed security services including security assessments, ongoing protection, and employee education. They serve industries such as healthcare, finance, and manufacturing, focusing on businesses that need comprehensive cybersecurity solutions.
Why I picked Miles Technologies: Their approach includes proactive defense measures and immediate incident response, aligning well with IT support integration. Miles Technologies helps your team stay compliant with industry standards like HIPAA and PCI. This integrated support ensures your organization maintains a strong security posture.
Standout Services: The security assessments help your team identify vulnerabilities and improve defenses, while employee education programs enhance awareness and reduce the risk of human error in security breaches.
Target industries: Healthcare, finance, manufacturing, education, and retail
Specialties: Security assessments, ongoing protection, employee education, IT compliance, and incident response
Pros and cons
Pros:
- Includes employee education programs
- Provides immediate incident response
- Offers proactive defense measures
Cons:
- Limited public information on specific services
- Potential integration complexity
Cisco Umbrella offers cloud-delivered security solutions, focusing on threat intelligence and secure internet access for organizations of all sizes. Their services are designed to protect users against malware, phishing, and other internet-based threats.
Why I picked Cisco Umbrella: The platform provides secure internet access by blocking malicious domains and filtering web traffic. It integrates with existing security tools, enhancing the overall protection your team receives. This cloud-based approach ensures reliable and scalable security across your organization.
Standout Services: The secure web gateway feature filters out malicious web content, keeping your team safe from potential threats while browsing. The DNS-layer security offers an additional layer of protection by blocking requests to harmful domains before they reach your network.
Target industries: Education, healthcare, finance, government, and retail
Specialties: Threat intelligence, secure internet access, DNS-layer security, web filtering, and malware protection
Pros and cons
Pros:
- Offers scalable cloud-based security
- Blocks malicious domains in real-time
- Integrates with existing security tools
Cons:
- May require subscription for full features
- Focuses primarily on internet security
Huntress provides managed detection and response services, focusing on threat hunting and endpoint protection. They cater to small and medium-sized businesses looking to enhance their cybersecurity defenses.
Why I picked Huntress: Their platform offers continuous monitoring and analysis to uncover hidden threats, aligning well with threat hunting. Huntress provides detailed incident reports, helping your team understand and respond to threats effectively. This proactive approach ensures that your organization stays protected against evolving cyber threats.
Standout Services: The persistent foothold detection identifies and removes malicious footholds, keeping your systems secure from repeated attacks. Their incident response service provides expert guidance to help your team handle security breaches efficiently.
Target industries: Finance, healthcare, education, retail, and technology
Specialties: Threat hunting, endpoint protection, incident response, persistent foothold detection, and threat analysis
Pros and cons
Pros:
- Provides detailed incident reports
- Continuous threat monitoring
- Expert incident response guidance
Cons:
- May require integration with existing tools
- Limited to endpoint protection
Other Cybersecurity Providers To Consider
Here are a few more options that didn’t make the best cybersecurity providers list:
- i2 Group
For data analysis and intelligence
- Intruder
For vulnerability scanning
- ManageEngine Endpoint Central
For endpoint management
- UnderDefense
For incident response
- Proofpoint
For email security
- CrowdStrike
For threat intelligence
- Cyber Security Services
For managed services
- Avast Software
Thorough antivirus scanner that applies machine learning to defeat zero-day attacks.
- RSA Security
For identity verification
- F-Secure
For consumer antivirus
- Palo Alto Networks
For next-gen firewall
- Standley Systems
For IT solutions
- ESET
An internet security company that provides multi-platform protection through antivirus and security products.
- AVG Technologies
Powerful free and paid antivirus program for quick scanning on PC. Mac, Mobile.
- Kaspersky Lab
For endpoint protection
- Check Point Software Technologies
For firewall protection
- Trend Micro
For cloud security
- Bitdefender
An antivirus program with a high malware-detection rate
- Sophos
For network security
- Fortinet
One-stop solution for addressing cybersecurity needs
What Are Cybersecurity Providers?
Cybersecurity providers are companies or services offering solutions to protect against cyber threats. They supply a range of tools and expertise, including firewalls, antivirus software, intrusion detection systems, and security consultancy services. These providers focus on safeguarding digital assets, networks, and sensitive data from unauthorized access and cyber attacks.
The benefits of using cybersecurity providers include enhanced protection against a variety of cyber threats, helping to prevent data breaches and loss. They offer specialized knowledge and up-to-date security measures, which are crucial in an evolving digital threat landscape. Additionally, they assist organizations in complying with security regulations and maintaining business continuity, ensuring that digital operations remain secure and resilient against potential cyber attacks.
Cybersecurity Provider Selection Criteria
When selecting the best cybersecurity providers to include in this list, I considered common business needs and pain points that these providers address. This included things like protecting sensitive data from breaches and ensuring compliance with industry regulations. I also used the following framework to keep my evaluation structured and fair:
Core Services (25% of total score)
To be considered for inclusion in this list, each provider had to offer these basic services:
- Network security
- Endpoint protection
- Threat monitoring and response
- Vulnerability management
- Firewall and intrusion prevention
Additional Standout Services (25% of total score)
To help further narrow down the competition, I also looked for unique or especially valuable services, such as:
- AI-driven threat detection
- Zero-trust architecture implementation
- Incident response planning and simulation
- Dark web monitoring
- Custom security training for employees
Industry Experience (10% of total score)
To get a sense of the industry experience of each provider, I considered the following:
- Years of experience in cybersecurity
- Knowledge of industry-specific regulations
- Case studies or success stories
- Client portfolio diversity
- Recognition from industry bodies or awards
Onboarding (10% of total score)
To evaluate the onboarding experience for each provider, I considered the following:
- Clear implementation timeline
- Dedicated onboarding team
- Training and resources for staff
- Seamless integration with existing systems
- Transparent handoff from sales to service team
Customer Support (10% of total score)
To assess the level of customer support each provider offers, I considered the following:
- 24/7 availability
- Multiple contact options (phone, chat, email)
- Fast response times
- Dedicated account manager
- Proactive communication and updates
Value For Price (10% of total score)
To evaluate the pricing and potential ROI of working with each provider, I considered the following:
- Transparency of pricing model
- Flexibility of contract terms
- Competitive pricing compared to market average
- Value-added services included in base cost
- ROI based on reduced downtime and incidents
Customer Reviews (10% of total score)
To get a sense of the overall satisfaction of existing customers, I considered the following when reading customer reviews:
- Feedback on ease of implementation and use
- Overall satisfaction rating
- Positive feedback on service reliability
- Complaints about hidden fees or service gaps
- Comments on customer support responsiveness
How to Choose a Cybersecurity Provider
It’s easy to get bogged down in long lists of services and complex pricing structures. To help you prioritize the things that matter most for your business, keep the following factors in mind:
| Factor | What to Consider |
|---|---|
| Business Objectives | Ensure the provider understands your industry and business goals. Their solutions should align with your strategic priorities and address specific risks. |
| Service Scope and SLAs | Review the services offered and the service level agreements (SLAs). Make sure they cover response times, uptime guarantees, and resolution processes. |
| Support Availability | Confirm that support is available 24/7. Understand how to reach them (phone, chat, email) and how quickly they respond to issues. |
| Costs and Pricing Structure | Look for transparent pricing. Understand whether costs are fixed, variable, or based on usage. Watch for hidden fees or add-ons. |
| Communication and Reporting | The provider should offer regular reports on threats, vulnerabilities, and resolution actions. Ensure communication is clear and timely. |
| Threat Detection and Response | Evaluate how quickly the provider can identify and respond to threats. Real-time monitoring and automated responses are key. |
| Compliance and Certifications | Verify the provider meets industry standards (e.g., ISO, SOC 2). Ensure they’re compliant with regulations relevant to your business. |
| Customization and Scalability | Ensure the provider can tailor solutions to your needs and scale services as your business grows or threats evolve. |
Key Cybersecurity Provider Services
When selecting a cybersecurity provider, keep an eye out for the following key services:
- Network security: Protects your business’s network infrastructure from unauthorized access, malware, and cyberattacks.
- Endpoint protection: Safeguards devices like laptops, desktops, and mobile phones from threats and vulnerabilities.
- Threat monitoring and response: Continuously monitors for potential security threats and responds quickly to contain and mitigate them.
- Firewall management: Configures and maintains firewalls to block unauthorized traffic while allowing legitimate communication.
- Vulnerability management: Identifies, assesses, and addresses security weaknesses before they can be exploited.
- Incident response: Develops and executes a structured plan to respond to security breaches and minimize damage.
- Data encryption: Ensures sensitive data is encrypted both at rest and in transit to prevent unauthorized access.
- Access control: Restricts access to systems and data based on user roles and permissions.
- Security awareness training: Educates employees on how to recognize and respond to security threats.
- Compliance support: Helps your business meet industry regulations and standards, reducing the risk of fines and penalties.
Benefits of Cybersecurity Providers
Partnering with a cybersecurity provider offers several benefits for your team and your business. Here are a few you can look forward to:
- Improved protection: A provider helps protect your systems and data from hackers, malware, and other threats.
- Faster threat response: With 24/7 monitoring, providers can detect and respond to threats before they cause damage.
- Reduced downtime: Quick threat detection and resolution mean fewer interruptions to your business operations.
- Regulatory compliance: Providers help ensure your business meets industry standards and avoids fines or legal issues.
- Cost savings: Preventing breaches and downtime saves you money on recovery costs and lost revenue.
- Expert guidance: Providers give your team access to specialized knowledge and advice on improving security.
- Increased customer trust: Strong security measures help build trust with customers by protecting their data.
Costs and Pricing Structures of Cybersecurity Providers
Cybersecurity providers typically come at a custom price to accommodate various business needs, sizes, and circumstances. Providers generally work within one of the following pricing structures:
- Subscription-based: You pay a recurring fee (monthly or annually) for ongoing access to services and support.
- Project-based: You pay a one-time fee for a specific project or security upgrade.
- Per user/device: Pricing is based on the number of users or devices being protected.
- Scope of work (SOW): Costs are determined by the specific services and deliverables outlined in the contract.
- Tiered pricing: Different pricing levels are offered based on the range of services or level of protection you choose.
Key Factors That Influence Cybersecurity Provider Pricing
Beyond the specific pricing model, here are some additional factors that can influence the cost of cybersecurity providers:
- Business size: Larger businesses with more users and devices typically face higher costs due to increased complexity.
- Service scope: The more services you require (like endpoint protection, threat response, and monitoring), the higher the cost.
- Industry regulations: Businesses in regulated industries (like healthcare or finance) often need more specialized and costly compliance measures.
- Customization needs: Tailoring solutions to your specific infrastructure and security needs can increase costs.
- Threat landscape: Businesses at higher risk of cyberattacks or those with sensitive data may require more expensive, advanced protection.
- Support level: 24/7 support and fast response times often come at a higher cost.
- Contract length: Longer contracts may offer discounts, while short-term or flexible agreements could come with higher rates.
Being aware of these factors before you start seeking out custom quotes from providers helps you get a sense of what to expect, and compare and contrast quotes more effectively.
Cybersecurity Provider FAQs
Here are some answers to common questions about cybersecurity providers:
How do I know if my business needs a cybersecurity provider?
If your business handles sensitive data, operates online, or relies on digital systems, you likely need a cybersecurity provider. Even small businesses are targeted by cyberattacks. A provider helps protect your data, respond to threats, and meet industry security standards.
What should I look for when choosing a cybersecurity provider?
Focus on the provider’s experience with businesses like yours, their service scope, response times, and customer support. Make sure they offer clear SLAs, transparent pricing, and compliance support if your industry requires it.
How much should I expect to pay for cybersecurity services?
Costs vary depending on the size of your business, the services you need, and the level of protection required. Subscription-based models are common, but you may also encounter project-based or per-user pricing. Expect to pay more for 24/7 monitoring and rapid response services.
What’s the difference between managed and unmanaged cybersecurity services?
Managed services involve the provider actively monitoring and responding to threats on your behalf. Unmanaged services may include tools and software, but your team is responsible for managing them. Managed services are usually more expensive but provide higher protection levels.
How long does it take to set up a cybersecurity provider's services?
Setup time depends on the complexity of your network and the services you choose. Basic monitoring may be up and running in a few days, while more complex setups involving multiple systems and compliance measures can take a few weeks.
Can a cybersecurity provider help with compliance?
Yes, most providers can help you meet industry regulations like HIPAA, PCI-DSS, and GDPR. They’ll assess your current security measures, identify gaps, and implement controls to help you stay compliant.
Cybersecurity—Be Ready Before You Need It
Cybersecurity providers offer businesses various solutions to fortify their cybersecurity defenses and minimize their risk of exposure to costly data breaches. They provide the infrastructural backbone of digital security, through threat intelligence, vulnerability assessments, endpoint protection, and privilege identity protection, including the remediation and resolution of security incidents.
By highlighting these top providers, we aim to empower you with the information needed to make informed decisions, ensuring your business remains secure and resilient against cyber threats.
Subscribe to The CTO Club's newsletter for more cybersecurity best practices and tips.