10 Best User Provisioning Software Shortlist
Here's my pick of the 10 best software from the 27 tools reviewed.
Our one-on-one guidance will help you find the perfect fit.
Navigating the intricate maze of permissions, managing user access, and ensuring the proper set-up of user accounts can be a formidable challenge. User provisioning software is the compass that guides you through, simplifying the task of granting, adjusting, and revoking access within your IT infrastructure. Automating these processes not only saves you valuable time but also amplifies security by ensuring that only the right individuals have access to your sensitive resources. If you've ever felt overwhelmed by the endless juggle of access controls and user account management, these tools are your lifeline.
What is a User Provisioning Software?
User provisioning software is a specialized tool designed to manage creating, modifying, and deleting user accounts within an organization's systems and networks. Typically used by IT administrators and security professionals, it ensures that employees and users have the appropriate permissions and access rights to resources, streamlining the onboarding process, role-based access control, and offboarding. By doing so, organizations can maintain security, compliance, and operational efficiency in their digital environments.
Best User Provisioning Software Summary
| Tool | Best For | Trial Info | Price | ||
|---|---|---|---|---|---|
| 1 | Best for global user provisioning for physical assets | Free trial + demo available | From $29/month | Website | |
| 2 | Best for streamlined Active Directory management | 30-day free trial | From $7/user/month (min 5 seats) | Website | |
| 3 | Best for directory-as-a-service capabilities | Free plan available (up to 10 devices) + Free demo available | From $2/device/month | Website | |
| 4 | Best for Apple device identity management | Not available | Pricing upon request. | Website | |
| 5 | Best for adaptive workforce authentication | Not available | From $5/user/month (billed annually) | Website | |
| 6 | Best for open-source identity and access management | Not available | From $20/user/month (billed annually) | Website | |
| 7 | Best for energy-efficient IT solutions | Not available | Pricing upon request. | Website | |
| 8 | Best for risk-based authentication | Not available | Pricing upon request | Website | |
| 9 | Best for SaaS operations management | Not available | Pricing upon request | Website | |
| 10 | Best for secure enterprise identity verification | Not available | From $6/user/month (billed annually) | Website |
-

Docker
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.6 -

Pulumi
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.8 -

GitHub Actions
Visit Website
Best User Provisioning Software Reviews
Deel is a global leader in payroll, HR, and IT management, offering a wide range of solutions that empower businesses to manage distributed teams in over 130 countries. With a strong focus on supporting global operations, Deel provides tools for handling everything from equipment delivery to workforce management, ensuring compliance.
Why I Picked Deel: Deel IT automates key workflows, such as onboarding and offboarding, enabling businesses to set up new hires with pre-configured devices, complete with all necessary apps and security settings. The platform’s global reach ensures that the provisioning of physical assets is not limited by geographic barriers—equipment and user accounts can be activated quickly, no matter where your employee is located.
Standout features & integrations:
Other standout features include its 24/7 global support and real-time visibility into all IT assets, enabling businesses to track, update, and manage devices across different regions efficiently. The platform also supports device recovery and reuse, ensuring optimal use of physical resources. Deel integrates with systems like Apple Business Manager, Windows Autopilot, Okta, BambooHR, Rippling, and Workday.
Pros and cons
Pros:
- Can combine HR and IT asset management in one
- Helps automate asset workflows
- Supports equipment deployment in over 130 countries
Cons:
- Doesn't offer features beyond device management, like network and server management
- May not be ideal for teams with very complex IT asset needs
New Product Updates from Deel

Deel Launches Anytime Pay Beta for Daily Earnings Access
Deel introduced an Anytime Pay beta, allowing EOR workers with Deel Cards to withdraw earned pay daily. Automatic tax and ledger updates are included, with PEO and Global Payroll support coming soon. More details at Deel Blog.
Best for streamlined Active Directory management
ManageEngine ADManager Plus provides an extensive platform designed to manage and maintain Active Directory domains efficiently. Focusing on making Active Directory operations more intuitive, it ties directly into our rationale for being the best tool for streamlined Active Directory management.
Why I Picked ManageEngine ADManager Plus: I chose ManageEngine ADManager Plus after comparing various tools for Active Directory management. Its focus on providing a streamlined user experience and rich features made it stand out. When judging its ability to simplify complex AD tasks, it became evident that it truly was the best for those looking for a tool that offers a straightforward approach to Active Directory management.
Standout features & integrations:
ManageEngine ADManager Plus boasts an array of features catering to novice and expert administrators. Its bulk user management capabilities, combined with the detailed reports, make day-to-day operations efficient. Furthermore, it has vital integrations with various apps and on-premises systems, allowing for a more unified IT management experience.
Pros and cons
Pros:
- Provides a self-service portal for end-users
- Integrated reporting system
- Comprehensive Active Directory management capabilities
Cons:
- Lacks some advanced automation features
- User interface could be more modern
- Steeper learning curve for beginners
JumpCloud provides a centralized platform to manage user identities across various IT resources. Businesses can achieve unified identity management through their directory-as-a-service capabilities, thus fulfilling complex access requests in today's heterogeneous IT environments.
Why I Picked JumpCloud: In the vast landscape of IT tools, selecting the right one often boils down to specific needs and standout features. When determining the best fit for directory services, JumpCloud immediately surfaced as a top contender due to its robust capabilities in handling user identities. I chose this tool because it effectively blends automated user processes with intricate directory functionalities, marking it as the best for directory-as-a-service capabilities.
Standout features & integrations:
JumpCloud excels in managing and automating user identities, ensuring that access requests are processed efficiently. The platform's comprehensive API further augments its directory functionalities, facilitating intricate integrations and custom workflows. As for integrations, JumpCloud has built partnerships with various IT platforms, allowing businesses to maintain cohesion in identity management across diverse ecosystems.
Pros and cons
Pros:
- Efficient handling of access requests
- Advanced API for custom integrations and workflows
- Comprehensive management of user identities
Cons:
- Integrations, while vast, may not cover niche industry tools
- Some advanced features could require technical expertise
- Might be overwhelming for smaller organizations
Jamf Connect simplifies identity management on Apple devices, providing swift and secure access to resources. It's designed for the Apple ecosystem, prioritizing security and simplicity, and ideal for businesses using Macs, iPhones, or iPads.
Why I Picked Jamf Connect: In the arena of identity management tools, a deep dive into specifics led me to recognize the unique value of Jamf Connect. I chose this tool after comparing its features with others, and judging its capacity to integrate Apple identity management into business processes. With its focus and specialization, Jamf Connect stood out as the best for Apple device identity management.
Standout features & integrations:
Key features of Jamf Connect include on-demand identity verification and synchronization with Apple’s native user experience. This ensures that users maintain consistent credentials across services. In terms of integrations, Jamf Connect can effectively exchange data with various directory services, making it easier for organizations to harmonize their Apple device management with existing infrastructure.
Pros and cons
Pros:
- On-demand identity verification adds an extra layer of security
- Effective integration with major directory services
- Designed specifically for Apple device management
Cons:
- Requires familiarity with the Apple ecosystem for optimal configuration
- Might be over-specialized for organizations with minimal Apple device usage
- Limited to Apple devices, making it less versatile for mixed-device environments
Okta Workforce Identity is a renowned tool in the cybersecurity realm that focuses on providing robust identity solutions for the modern workforce. Its main thrust is adaptive authentication, tailoring access requirements based on varying user contexts and scenarios, which is essential for today's diverse and dynamic work environment.
Why I Picked Okta Workforce Identity: I have found that Okta Workforce Identity is a top choice for adaptive authentication. This tool stands out due to its ability to adjust access protocols based on user behavior and context. After comparing various options, I am confident that Okta Workforce Identity is the ideal solution for adaptive workforce authentication. It is particularly useful for businesses with constantly changing dynamics and security requirements.
Standout features & integrations:
Okta Workforce Identity is more than just an authentication tool. It offers advanced compliance reporting features, helping businesses meet their compliance requirements without hassles. Furthermore, Okta integrates with a multitude of enterprise applications, enhancing its adaptability and ensuring consistent identity practices across various platforms.
Pros and cons
Pros:
- Extensive integrations with a myriad of enterprise tools, making it versatile in diverse IT environments.
- In-depth compliance reporting assists businesses in meeting stringent compliance requirements.
- Comprehensive adaptive authentication caters to varying workforce needs.
Cons:
- As a comprehensive tool, setup and initial configuration might be extensive
- Certain advanced features might require a steeper learning curve
- Might be perceived as overkill for very small businesses
WSO2 Identity Server offers a comprehensive solution for identity management, ensuring real-time and secure access to applications and services. As an open-source platform, it caters to organizations prioritizing flexibility, customization, and transparency in their identity and access management strategies.
Why I Picked WSO2 Identity Server: After evaluating various tools, I found that the open-source WSO2 Identity Server was the best option for identity and access management. Its transparency and flexibility make it the top choice.
Standout features & integrations:
WSO2 Identity Server prides itself on an efficient provisioning process, ensuring timely and accurate user data management. The platform supports Single Sign-On (SSO) and Multi-Factor Authentication (MFA) mechanisms, reinforcing its commitment to secure access. In integrations, WSO2 connects with a range of enterprise tools, ensuring consistent identity management across diverse business systems.
Pros and cons
Pros:
- Wide-ranging integrations support uniform identity practices across tools.
- Efficient provisioning process enhances the user data management experience.
- Open-source nature ensures transparency and customization options.
Cons:
- Potential for complexities when integrating with proprietary systems
- Requires dedicated resources for optimal customization and deployment
- Might pose a steeper learning curve for those unfamiliar with open-source platforms
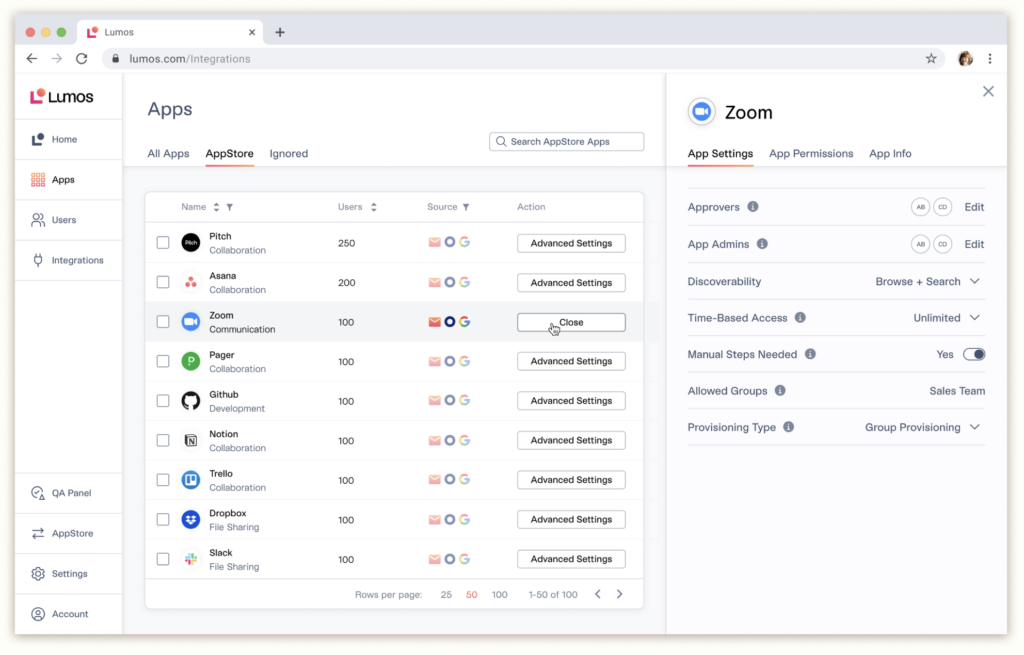
Lumos is an avant-garde IT platform centered around delivering energy-efficient solutions. Its eco-friendly approach not only aids businesses in being environmentally responsible but also connects directly to its prowess in energy-efficient IT solutions.
Why I Picked Lumos: While evaluating numerous platforms, Lumos distinctly caught my eye due to its rare blend of IT capabilities, emphasizing energy efficiency. Lumos's commitment to combining lifecycle management with energy savings was unparalleled in determining and judging the tools. This, along with its facility to effortlessly handle new user integrations, made me confident in my opinion that Lumos truly stands out as the best for energy-conscious IT solutions.
Standout features & integrations:
Lumos offers a comprehensive lifecycle management feature, ensuring that every aspect of your IT resources is optimized for performance and energy consumption. Furthermore, its efficient single sign-on (SSO) capability streamlines access for new users, making onboarding swift and secure. For integrations, Lumos connects with many leading IT applications, ensuring a flow of information and a unified user experience.
Pros and cons
Pros:
- Efficient single sign-on for new users
- Comprehensive lifecycle management capabilities
- Emphasis on energy-efficient IT solutions
Cons:
- Custom integrations might need additional setup
- Not as widely recognized as some competitors
- Might require a learning curve for some users
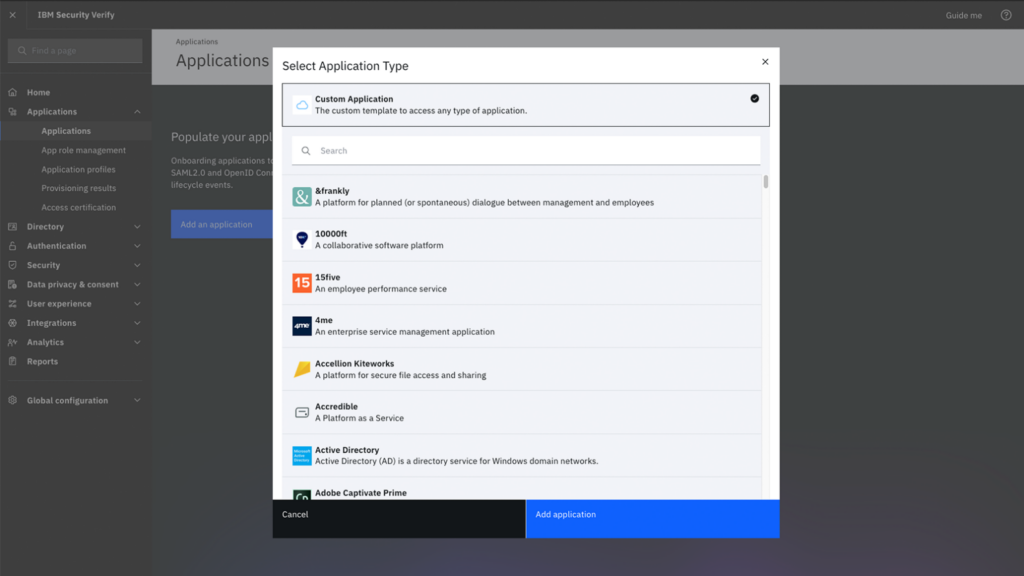
IBM Security Verify is a comprehensive access management solution emphasizing risk-based authentication, ensuring users are granted access based on contextual risks. This approach balances security and user convenience, aligning perfectly with the rising demands of modern digital businesses.
Why I Picked IBM Security Verify: In choosing and comparing various tools, IBM Security Verify particularly caught my attention due to its unique approach to authentication. The tool's emphasis on a risk-based method, which is different from traditional authentication strategies, piqued my interest. Hence, I am of the opinion that for organizations looking to pivot towards a more contextual and dynamic authentication system, IBM Security Verify is best for risk-based authentication.
Standout features & integrations:
IBM Security Verify is an account provisioning tool and a complete identity solution. Its risk-based authentication mechanism evaluates numerous parameters before granting access, adding an extra layer of security. Integration-wise, IBM Security Verify is compatible with various enterprise applications and systems, ensuring consistent identity practices regardless of the underlying platform.
Pros and cons
Pros:
- Wide compatibility with numerous enterprise applications and systems.
- Comprehensive user provisioning tool ensuring efficient account management.
- Advanced risk-based authentication for improved security.
Cons:
- As with many IBM solutions, it may come with a steeper learning curve for some users
- Integration with certain legacy systems might require additional effort
- Might be perceived as complex for smaller organizations
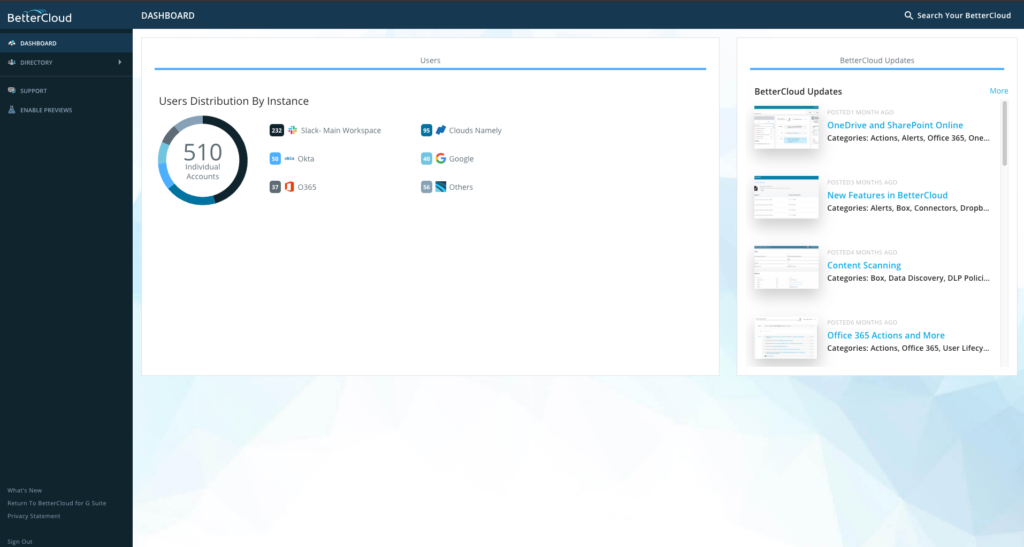
BetterCloud is a cloud-based platform tailor-made for IT professionals, offering extensive SaaS management tools to ensure efficient and secure operations. Its excellence in overseeing multiple SaaS environments ties in directly with our earlier declaration of its prowess in SaaS operations management.
Why I Picked BetterCloud: When selecting tools for the list, BetterCloud caught my attention because of its unique approach to managing diverse SaaS ecosystems. In comparing various platforms, it became evident that BetterCloud had a distinct edge, especially in centralizing the management of SaaS applications. Given its adeptness in offering granular controls over various SaaS apps, it is best for those keen on robust SaaS operations management.
Standout features & integrations:
BetterCloud flourishes with features such as advanced audit trails, multi-factor authentication, and automated deprovisioning to secure and optimize SaaS applications. Furthermore, it provides crucial integrations with prominent SaaS applications like Slack, Google Workspace, and Dropbox, making the management process coherent and integrated.
Pros and cons
Pros:
- Efficient deprovisioning of user accounts
- Incorporates multi-factor authentication for added security
- Comprehensive cloud-based SaaS management tools
Cons:
- Pricing structure could be more transparent
- Might be overkill for small businesses
- Can be complex for beginners
Microsoft Entra ID is a tool designed to provide businesses with a robust mechanism for identity verification. As enterprises grow and navigate through complex hybrid environments, a secure and reliable identity verification becomes indispensable. Microsoft Entra ID squarely focuses on this, ensuring that enterprise identities are verified with utmost security.
Why I Picked Microsoft Entra ID: I picked Microsoft Entra ID as my top choice for identity verification tools. It's great for the enterprise sector, especially those in hybrid environments. After comparing it to other options, I found that it excels at providing secure identity verification. This makes it easy for the IT department to handle and authenticate users with confidence.
Standout features & integrations:
Microsoft Entra ID boasts of features that are tailored for today's complex business infrastructures. It's highly adaptive to hybrid environments, ensuring absolute identity verifications across both on-premise and cloud platforms. Furthermore, its deep integration with Microsoft 365 means that businesses can maintain a consistent identity verification method across the suite of Microsoft applications.
Pros and cons
Pros:
- Deep integration with Microsoft 365 ensures a streamlined experience for the IT department.
- Extensive function in hybrid environments, balancing both on-premise and cloud.
- Tailored for enterprises, addressing specific challenges they face in identity verification.
Cons:
- The complexity may require dedicated IT personnel for setup and maintenance
- Businesses not invested in the Microsoft ecosystem might find some features redundant
- May be perceived as intricate for small businesses without hybrid infrastructures
Other Noteworthy User Provisioning Software
- OneLogin
Good for unified access management across devices
- SailPoint
Good for comprehensive identity governance
- Coreview
Good for Microsoft 365 management and insights
- External User Manager for Microsoft Teams
Good for managing Teams external users
- Teleport
Good for secure infrastructure access
- Cerby
Good for shadow IT discovery and control
- Auth0
Good for customizable identity authentication
- Avigilon ACM
Good for on-premise access control
- Fastpath
Good for compliance and audit readiness
- PingFederate
Good for scalable enterprise federation and single sign-on
Selection Criteria for Choosing User Provisioning Software
When choosing identity and access management (IAM) software, there's a lot to consider. Over the years, I've evaluated dozens of IAM tools. For this specific review, I was particularly interested in the comprehensive coverage of core functionalities, user experience, and essential features that stand out in practical applications. Let me dive deeper into my criteria:
Core Functionality
- User Authentication: The ability for users to prove their identities securely.
- Authorization Management: Ensuring users access only what they are permitted to.
- Group or Role Management: Creating and managing groups or roles for assigning specific access rights.
- Audit Trails: Tracking user activity to maintain records and trace potential security breaches.
- Single Sign-On (SSO): Permitting a single set of credentials to access multiple applications.
Key Features
- Multi-Factor Authentication (MFA): Enhances security by requiring multiple methods of verification.
- Directory Services Integration: Connection with organizational directories, such as Active Directory or LDAP.
- Self-Service Capabilities: Enables users to reset passwords, request permissions, or update their profiles without admin intervention.
- Adaptive Authentication: Adjusts authentication methods based on user behavior and other context factors.
- Session Management: Controls user sessions after authentication, ensuring timeouts for idle sessions and secure session terminations.
- Compliance Reports: Provides ready-to-use reports for common regulatory and industry standards.
Usability
- Intuitive Dashboard: A centralized control panel where administrators can view system health, alerts, and manage configurations.
- Drag-and-Drop Workflow Builder: Allows for creating and modifying user lifecycle processes without coding.
- Easy Role Configuration: A design interface where access roles can be defined and modified without diving into complex settings.
- Accessible Learning Resources: Given the complexity of IAM tools, there should be a well-structured learning library, training programs, or video tutorials to assist in onboarding.
- Efficient Support Channels: Quick response customer support, preferably with 24/7 availability and a comprehensive knowledge base for users to refer to.
These criteria served as the backbone for my assessments, ensuring I prioritized tools that offered not just a wide array of features, but also practicality and ease-of-use for both end-users and administrators.
Most Common Questions Regarding User Provisioning Software (FAQ's)
What benefits can I expect from using user provisioning software?
User provisioning software streamlines and automates user access to systems, ensuring security and efficiency. Some of the benefits include:
- Automated User Lifecycle Management: It simplifies processes from onboarding to offboarding.
- Enhanced Security: Ensuring that only authorized users get access to specific resources, it minimizes the risk of unauthorized access.
- Compliance Maintenance: With audit trails and reports, you can always ensure adherence to regulatory requirements.
- Reduced Administrative Overhead: Automation means fewer manual tasks, saving resources and time.
- Integrations with Existing Infrastructure: Many tools integrate with platforms like SharePoint, Office 365, and others, providing a cohesive environment.
How much do these tools typically cost?
Pricing for user provisioning software varies widely depending on the features, the number of users, and other factors. While some tools offer free versions with basic functionalities, premium features often come at a cost.
What are the common pricing models for these tools?
There are several pricing models, including:
- Per User: Pricing based on the number of users in the system.
- Per Feature: A tiered approach where pricing is based on the features you choose to include.
- Flat Rate: A fixed price regardless of the number of users or features.
- Freemium: Basic features are free, but advanced features are expensive.
What's the typical pricing range for these tools?
Prices can range from $5/user/month for basic tools to $50/user/month or more for enterprise-level solutions with advanced features.
Which software are considered the cheapest and most expensive?
While prices can change based on new releases and offers, as of my last update, SolarWinds Access Rights Manager is on the more affordable end of the spectrum. On the other hand, comprehensive solutions tailored for large enterprises, often come at a premium price.
Are there any free user provisioning software options?
Yes, several tools offer free versions. However, these free options might have limitations regarding features, number of users, or integrations. It’s crucial to determine whether the free version meets your needs or if a paid option is more appropriate.
How do these tools integrate with platforms like SharePoint or Office 365?
Most top-tier user provisioning software offers integrations with popular platforms like SharePoint and Office 365. This allows for synchronized user management, where changes made in one platform reflect in others. Such integrations enable consistent access rights management across your organization’s tools and platforms.
Are there tools designed explicitly for certain platforms like Office 365?
Yes, some tools specialize in specific platforms. For instance, there are user provisioning tools tailored for Office 365 that handle everything from user onboarding to managing permissions within the forum. They leverage the unique features of Office 365 to offer impeccable user management.
Other User Provisioning Software-Related Reviews
Summary
Choosing the ideal user provisioning software is paramount to ensuring efficient user management, maintaining data security, and optimizing organizational workflows. By exploring various software in the market, the guide illuminates the significant facets to consider during the selection process.
Key Takeaways:
- Core Functionality: It's essential to pick software that aligns with the organization's needs, whether single sign-on, role-based access control, or lifecycle management. Ensure that the tool addresses your present demands and is adaptable to future growth.
- Features and Usability: Distinctive features like automation, integration capabilities with platforms like SharePoint or Office 365, and customization options set the best tools apart. Furthermore, a software's user interface should be intuitive, making it easier for both IT departments and end-users to navigate without extensive training.
- Pricing and Scalability: While cost is a crucial factor, it's also vital to consider the software's scalability. A tool might be affordable now, but if it cannot sit may become a limitation if it cannot scale with your organization's growth the total cost, including potential future expansions, against the software's capabilities and integrations, like SolarWinds Access Rights Manager.
What do you think?
We've endeavored to cover the most effective user provisioning software available, but the tech landscape is vast and ever-evolving. If there's a tool you swear by that didn't make our list, we'd love to hear from you. Your insights and recommendations are invaluable in keeping our guide comprehensive and up-to-date. Drop your suggestions in the comments or reach out, and let's enrich this resource together.