Best Penetration Testing Tools Shortlist
Here’s my shortlist of the best penetration testing tools:
Our one-on-one guidance will help you find the perfect fit.
Finding the right penetration testing tool isn’t just about features—it’s about confidence. Confidence that you’re not missing critical vulnerabilities. That your security efforts scale with your growing infrastructure. And that the tool your team uses won’t slow down your development cycle or flood you with noise.
The problem? Many tools promise comprehensive coverage but either overwhelm with complexity or underdeliver in real-world testing environments. Choosing one often means sifting through marketing hype without a clear picture of how it’ll perform in your specific stack.
I’ve spent the last several years working closely with engineering and security teams in SaaS environments—vetting, deploying, and troubleshooting pen testing tools across both cloud-native and hybrid systems. This guide distills those hands-on experiences into practical recommendations tailored for teams who need results, not just reports.
Why Trust Our Software Reviews
We’ve been testing and reviewing SaaS development software since 2023. As tech experts ourselves, we know how critical and difficult it is to make the right decision when selecting software. We invest in deep research to help our audience make better software purchasing decisions.
We’ve tested more than 2,000 tools for different SaaS development use cases and written over 1,000 comprehensive software reviews. Learn how we stay transparent & check out our software review methodology.
Best Penetration Testing Tools Summary
This comparison chart summarizes pricing details for my top penetration testing tools selections to help you find the best one for your budget and business needs.
| Tool | Best For | Trial Info | Price | ||
|---|---|---|---|---|---|
| 1 | Best for automated scanning | 14-day free trial + demo available | From $99/month | Website | |
| 2 | Best for continuous testing | Free demo available | From $69/month | Website | |
| 3 | Best for comprehensive code-to-cloud security | Free plan available + free demo | From $350/month | Website | |
| 4 | Best for developers | Free plan + demo available | Pricing upon request | Website | |
| 5 | Best for web vulnerabilities | Free demo available | Pricing upon request | Website | |
| 6 | Best for web application protection | 14-day free trial + free demo | From $99/month | Website | |
| 7 | Best for open-source tools | Not available | Free to use | Website | |
| 8 | Best for cloud-based pentesting | Not available | Pricing upon request | Website | |
| 9 | Best for enterprise use | Free demo available | Pricing upon request | Website | |
| 10 | Best for multi-vector testing | Free trial available + free demo | From $9,450/user/year | Website |
-

Docker
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.6 -

Pulumi
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.8 -

GitHub Actions
Visit Website
Best Penetration Testing Tool Reviews
Below are my detailed summaries of the best penetration testing tools that made it onto my shortlist. My reviews offer a detailed look at the key features, pros & cons, integrations, and ideal use cases of each tool to help you find the best one for you.
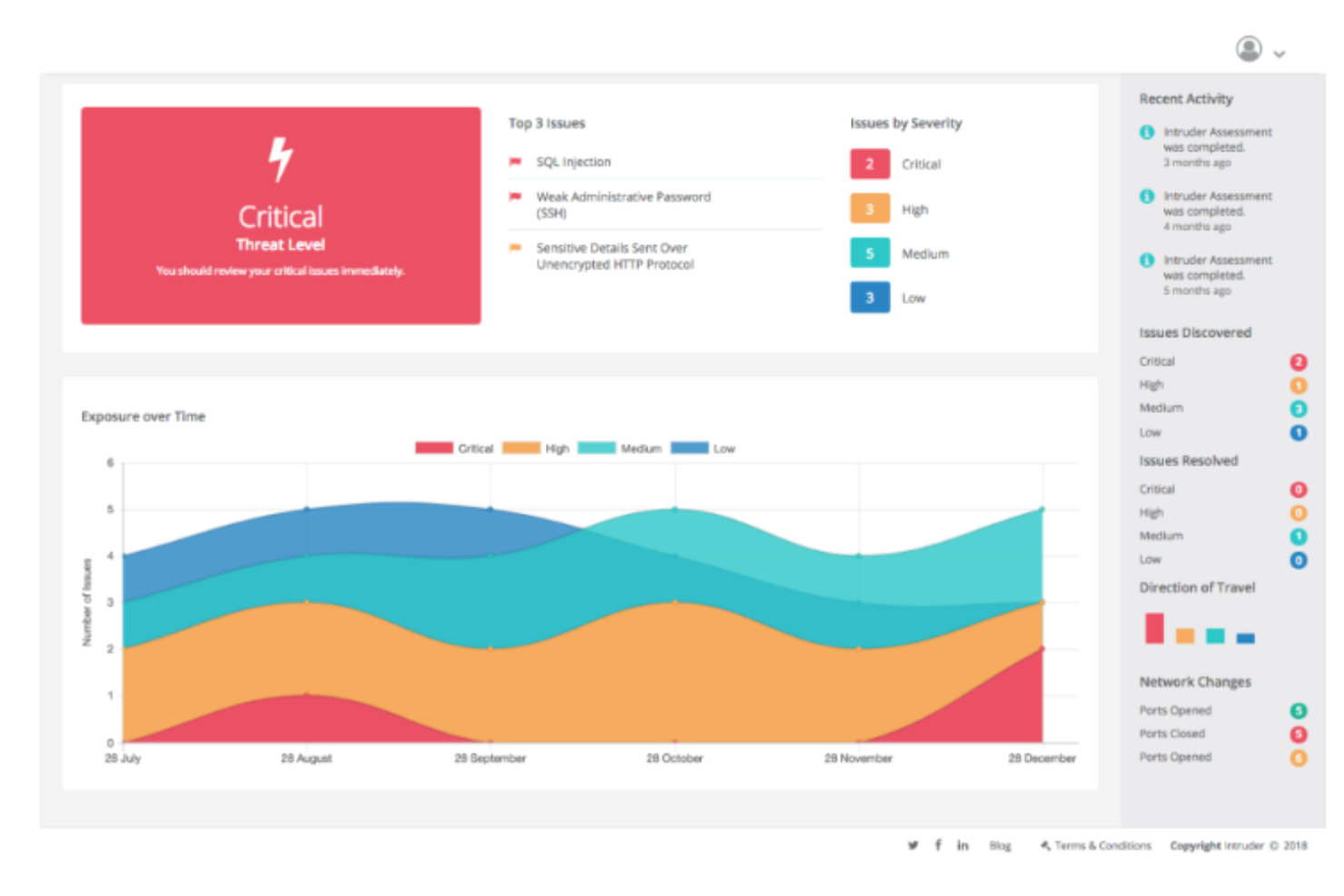
Intruder is an automated vulnerability scanner designed for IT and security teams to identify cybersecurity weaknesses. It offers year-round protection and performs continuous vulnerability management, making it ideal for preventing data breaches.
Why I picked Intruder: Intruder excels at automated scanning, providing proactive change detection and detailed vulnerability reports. It uses advanced scanning technology similar to that used by major banks. The platform's noise reduction algorithm helps prioritize actionable insights. Intruder's user-friendly reports make it accessible for both technical and non-technical users.
Standout features & integrations:
Features include advanced scanning technology that identifies both known and emerging threats, a noise reduction algorithm that helps prioritize critical issues, and user-friendly reports that simplify understanding of security risks. The platform also offers expert analysis to catch vulnerabilities that automated scans might miss.
Integrations include Slack, Jira, AWS, Azure, Google Cloud, Microsoft Teams, Trello, GitHub, GitLab, and Bitbucket.
Pros and cons
Pros:
- Proactive change detection
- Detailed vulnerability reports
- Easy to set up
Cons:
- May require technical knowledge
- Limited customization options
Astra Pentest is a penetration testing tool designed for businesses seeking continuous security assessments. Its main users include IT security teams and developers focused on identifying and managing vulnerabilities.
Why I picked Astra Pentest: It provides continuous testing capabilities that set it apart from other tools. The platform offers automated vulnerability scanning and manual penetration testing, covering over 8,000 security tests. The centralized dashboard simplifies the process of tracking and remediating vulnerabilities. This makes it particularly suitable for teams needing constant security evaluation.
Standout features & integrations:
Features include automated vulnerability scanning that covers a wide range of threats, manual pentesting options for more detailed analysis, and a user-friendly dashboard that centralizes all findings for easy access. The tool's ability to conduct over 8,000 security tests ensures comprehensive coverage.
Integrations include Jira, Slack, GitHub, GitLab, Bitbucket, Asana, Trello, Azure DevOps, Zapier, and Microsoft Teams.
Pros and cons
Pros:
- Continuous scanning capability
- Comprehensive test coverage
- Easy setup and use
Cons:
- Dashboard can be overwhelming at first
- Limited customization options
Aikido Security is a security platform tailored for small businesses needing to secure code, cloud, and runtime environments. It serves IT security teams by providing a centralized system that integrates static and dynamic security testing.
Why I picked Aikido Security: It offers a comprehensive security approach, making it ideal for small businesses that need an all-in-one solution. Aikido provides static application security testing and cloud posture management, ensuring robust protection. The platform's AI capabilities, like AI autofix, simplify vulnerability management. Its compliance automation tools assist with meeting industry standards.
Standout features & integrations:
Features include code security features like static application security testing and infrastructure-as-code scanning. Cloud security is enhanced with container image and virtual machine scanning. Runtime protection is available through in-app firewalls and automated threat blocking.
Integrations include GitHub, GitLab, Bitbucket, Azure DevOps, AWS, Google Cloud, Azure, Jenkins, Jira, and Slack.
Pros and cons
Pros:
- SOC 2 and ISO compliant
- Reduces false positives
- All-in-one security solution
Cons:
- May require technical knowledge
- Limited customization
New Product Updates from Aikido Security
Aikido Security's Azure Support and Multi-Cloud Search
Aikido Security's update introduced Azure support and multi-cloud search capabilities to its CSPM offering, enhanced by Zen LLM tracking for NodeJS and Python, alongside improved file-type scanning support. For more details, visit the Aikido Changelog.
New Relic is a software analytics and monitoring tool primarily used by developers to track application performance and infrastructure health. It provides insights into application behavior, helping teams optimize performance and troubleshoot issues.
Why I picked New Relic: Its detailed monitoring capabilities make it particularly useful for developers. New Relic offers real-time analytics that help you understand application performance. The tool's customizable dashboards allow you to focus on metrics that matter most to your team. Its alerting system ensures you’re notified of critical issues, enabling prompt responses.
Standout features & integrations:
Features include real-time performance monitoring that provides instant insights into application behavior. Customizable dashboards let you focus on specific metrics that are crucial for your operations. The alerting system automatically notifies you of any critical performance issues.
Integrations include AWS, Azure, Google Cloud, Kubernetes, Docker, Slack, PagerDuty, Jira, Trello, and GitHub.
Pros and cons
Pros:
- Detailed performance insights
- Customizable dashboards
- Real-time data analysis
Cons:
- Can be resource-intensive
- Requires technical expertise
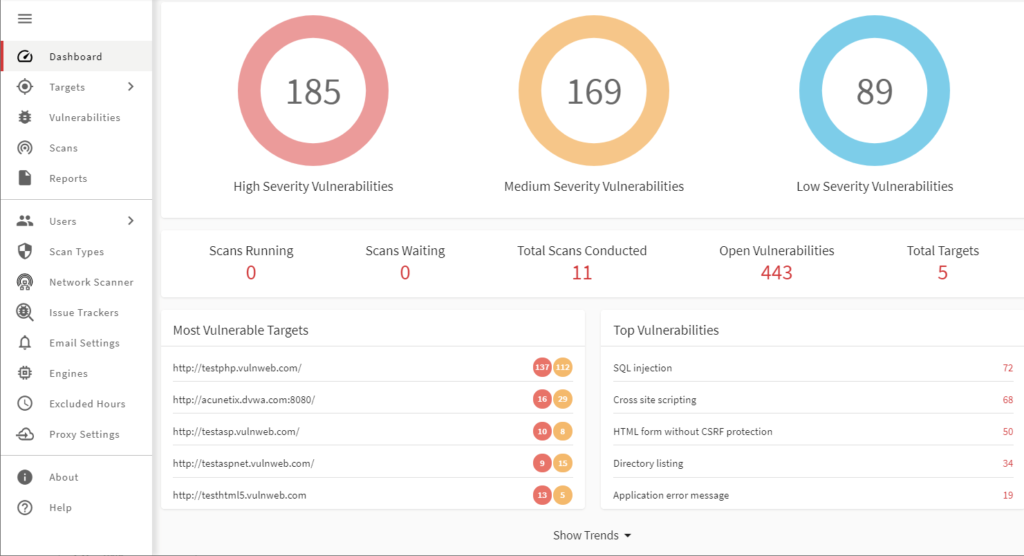
Acunetix is a web application security scanner primarily used by security professionals to identify vulnerabilities in web applications. It automates the process of finding security flaws, which helps teams improve their web security posture.
Why I picked Acunetix: It specializes in detecting web vulnerabilities, making it a top choice for web security. Acunetix features sophisticated scanning technology that identifies SQL injection, XSS, and other threats. Its ability to scan complex web applications ensures comprehensive security. The platform's detailed reports guide your team on how to remediate vulnerabilities effectively.
Standout features & integrations:
Features include advanced scanning capabilities that identify a wide range of web vulnerabilities. The platform supports both authenticated and unauthenticated scans, providing flexibility for different security needs. Acunetix also offers detailed reporting that helps your team understand and address security issues.
Integrations include Jira, Jenkins, GitHub, GitLab, Bitbucket, Microsoft TFS, Azure DevOps, Slack, Bamboo, and ServiceNow.
Pros and cons
Pros:
- Supports complex web applications
- Detailed and actionable reports
- Detects a wide range of vulnerabilities
Cons:
- Can be resource-intensive
- Limited support for non-web applications
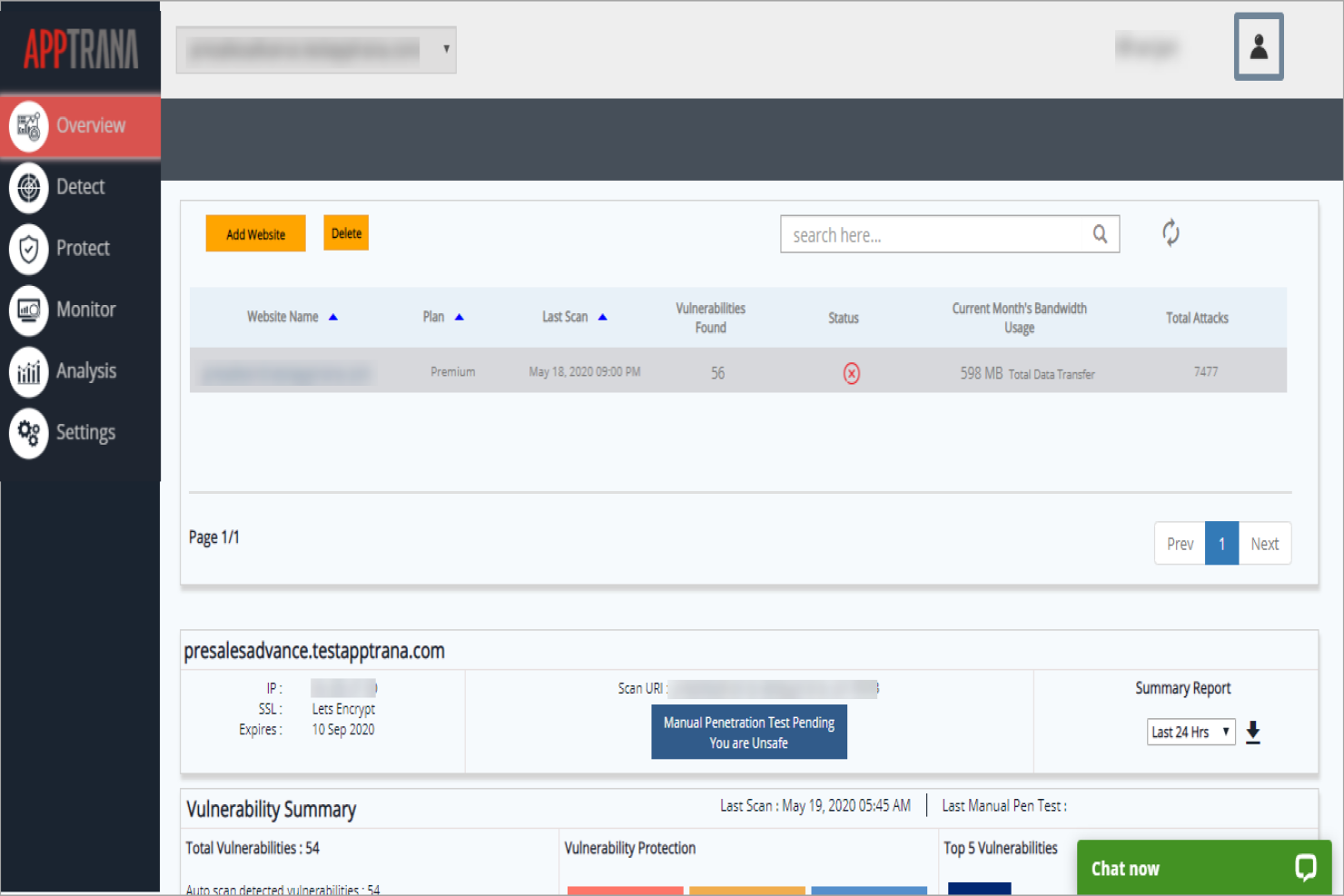
AppTrana is a web application firewall and security solution primarily used by businesses to protect their web applications from threats. It offers continuous monitoring and protection, making it vital for maintaining web security.
Why I picked AppTrana: It excels in providing web application protection with features like continuous threat monitoring. AppTrana includes automated vulnerability scanning and managed security services. Its round-the-clock monitoring helps ensure your web applications remain secure. The tool's ability to adapt to new threats keeps your security measures current.
Standout features & integrations:
Features include automated vulnerability scanning that identifies and mitigates potential threats. The platform provides managed security services for continuous protection and threat monitoring. AppTrana also adapts to new security threats, ensuring your web applications stay secure.
Integrations include AWS, Azure, Google Cloud, Cloudflare, Slack, Jira, GitHub, GitLab, Bitbucket, and Microsoft Teams.
Pros and cons
Pros:
- Adapts to new threats
- Managed security services
- Continuous threat monitoring
Cons:
- Limited customization options
- May require technical expertise
Kali Linux is an open-source penetration testing platform widely used by cybersecurity professionals and ethical hackers. It provides a suite of tools to conduct comprehensive security assessments and identify vulnerabilities.
Why I picked Kali Linux: Its open-source nature offers flexibility and customization for security experts. Kali Linux includes a wide array of pre-installed security tools for various testing needs. The platform is adaptable, allowing users to tailor it to specific security requirements. Its community-driven development ensures regular updates and improvements.
Standout features & integrations:
Features include a vast library of pre-installed security tools that cater to different testing scenarios. Kali Linux is highly customizable, enabling users to configure the platform to their specific needs. Its regular updates ensure the latest security tools are available to users.
Integrations include Metasploit, Wireshark, Aircrack-ng, Hydra, Nmap, Burp Suite, John the Ripper, Netcat, SQLmap, and Maltego.
Pros and cons
Pros:
- Regular updates from the community
- Highly customizable environment
- Extensive tool library
Cons:
- Limited support for beginners
- Initial setup complexity
BreachLock is a penetration testing tool that offers on-demand, continuous and scalable security testing. The tool can be used both for modern cloud and DevOps businesses. BreachLock allows for detection of vulnerabilities, and provides your contextualized reports of the findings, allowing you to act quickly to secure your systems.
BreachLock provides an abundance of features, such as the ability to schedule monthly or quarterly manual penetrations tests. The tests are conducted manually to experience the process of hackers, allowing you to determine the robustness of your security network. BreachLock also issues consistent alerts for new vulnerabilities, allowing you to stay updated.
BreachLock provides integrations with platforms such as Slack, Jira and Trello.
BreachLock offers customized pricing upon request.
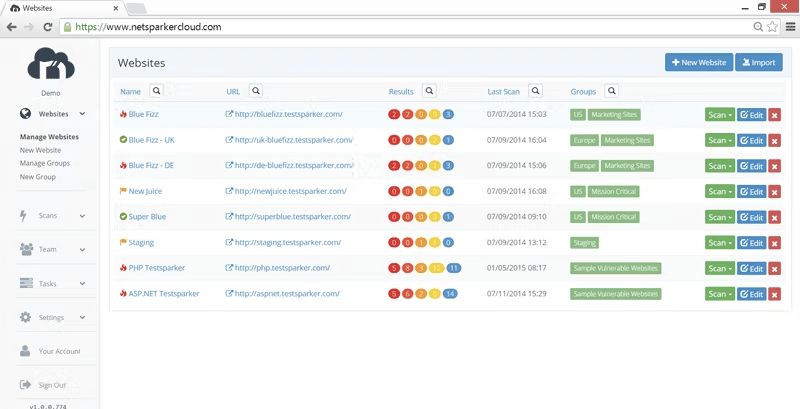
Invicti is a web application security scanner tailored for enterprises to identify and manage vulnerabilities. It provides automated scanning and comprehensive reporting, helping security teams protect their web applications.
Why I picked Invicti: Its enterprise-level capabilities make it ideal for large organizations. Invicti offers automated vulnerability scanning with proof-based scanning to eliminate false positives. The tool's scalability supports extensive web application portfolios. With detailed reporting, your team can easily prioritize and address security issues.
Standout features & integrations:
Features include proof-based scanning that validates vulnerabilities to reduce false positives. The tool provides detailed reporting that helps prioritize security measures effectively. Invicti's scalability is designed to handle large numbers of web applications, making it suitable for enterprise use.
Integrations include Jira, Jenkins, GitHub, GitLab, Azure DevOps, Slack, ServiceNow, Bamboo, Bitbucket, and Microsoft Teams.
Pros and cons
Pros:
- Detailed and actionable reports
- Scalable for large enterprises
- Proof-based scanning reduces false positives
Cons:
- Learning curve for new users
- Resource-intensive for smaller teams
Core Impact is a penetration testing tool designed to help security teams identify and exploit vulnerabilities across various systems. It enables users to assess the security of their network infrastructure, endpoints, web applications, and more. By simulating real-world attacks, Core Impact assists organizations in uncovering and addressing potential security weaknesses.
Why I picked Core Impact: It offers multi-vector testing capabilities, allowing you to evaluate security across networks, client systems, web applications, and even mobile devices. Its Rapid Penetration Tests (RPTs) provide guided automation, simplifying complex testing processes and enabling your team to focus on critical tasks. The tool includes a library of certified exploits, ensuring tests are both current and reliable. Additionally, Core Impact's self-destructing agents minimize residual impact on your systems after testing.
Standout features & integrations:
Features include the ability to conduct ransomware simulations, helping your team assess and improve responses to such threats. Core Impact also offers teaming capabilities, allowing multiple testers to collaborate within the same session and share data securely.
Integrations include compatibility with vulnerability scanners such as Fortra VM, beSECURE, Acunetix Web Security Scanner, Retina Network Security Scanner, GFI LANguard, HP WebInspect, IBM AppScan, PortSwigger Burp Suite, McAfee Vulnerability Manager, Tripwire IP360, Rapid7 Nexpose, Qualys QualysGuard, SAINTscanner, and Tenable Nessus. Additionally, Core Impact integrates with tools like Cobalt Strike and PlexTrac.
Pros and cons
Pros:
- Includes a library of certified exploits
- Offers guided automation with Rapid Penetration Tests
- Allows for multi-vector testing
Cons:
- Some advanced features might necessitate additional training
- Integration with certain tools may require configuration
Other Penetration Testing Tools
Here are some additional penetration testing tools options that didn’t make it onto my shortlist, but are still worth checking out:
- Aircrack-ng
For Wi-Fi security
- Burp Suite
For manual testing
- W3af
For web application auditing
- CyCognito
For large-scale penetration testing
- Metasploit
For penetration testing frameworks
- Nessus
For vulnerability assessment
- UnderDefense
For managed security services
- Canvas
For exploit development
- BeEF (Browser Exploitation Framework)
Penetration testing tool
- NMap
Open source utility
- John the Ripper
Free password cracking tool
- Wireshark
Open-source network protocol analyzer
- Indusface WAS Free Website Security Check
For vulnerability protection
- Cain & Abel
For password recovery
- Zed Attack Proxy (ZAP)
For beginners
- SQLMap
Open source penetration testing tool
Penetration Testing Tool Selection Criteria
When selecting the best penetration testing tools to include in this list, I considered common buyer needs and pain points like identifying security vulnerabilities and ensuring compliance with security standards. I also used the following framework to keep my evaluation structured and fair:
Core Functionality (25% of total score)
To be considered for inclusion in this list, each solution had to fulfill these common use cases:
- Identify security vulnerabilities
- Conduct automated scans
- Provide detailed reporting
- Support manual testing
- Integrate with existing security tools
Additional Standout Features (25% of total score)
To help further narrow down the competition, I also looked for unique features, such as:
- Real-time threat detection
- Customizable scanning profiles
- AI-driven vulnerability analysis
- Multi-vector attack simulation
- Compliance management tools
Usability (10% of total score)
To get a sense of the usability of each system, I considered the following:
- Intuitive user interface
- Easy navigation
- Quick access to key features
- Minimal technical expertise required
- Clear and concise documentation
Onboarding (10% of total score)
To evaluate the onboarding experience for each platform, I considered the following:
- Availability of training videos
- Interactive product tours
- Comprehensive user guides
- Access to webinars
- Responsive onboarding support
Customer Support (10% of total score)
To assess each software provider’s customer support services, I considered the following:
- 24/7 availability
- Multiple support channels
- Quick response times
- Knowledgeable support staff
- Access to a community forum
Value For Money (10% of total score)
To evaluate the value for money of each platform, I considered the following:
- Competitive pricing
- Range of pricing plans
- Features offered at each price point
- Cost-effectiveness for small teams
- Discounts for annual subscriptions
Customer Reviews (10% of total score)
To get a sense of overall customer satisfaction, I considered the following when reading customer reviews:
- Overall satisfaction ratings
- Commonly reported issues
- Feedback on feature effectiveness
- User recommendations
- Sentiment towards customer support
How to Choose a Penetration Testing Tool
It’s easy to get bogged down in long feature lists and complex pricing structures. To help you stay focused as you work through your unique software selection process, here’s a checklist of factors to keep in mind:
| Factor | What to Consider |
| Scalability | Ensure the tool can grow with your needs. Consider if it can handle an increasing number of tests and larger data volumes as your organization expands. |
| Integrations | Check if the tool integrates with your existing security software and workflows. Look for compatibility with tools like Jira, GitHub, and Slack. |
| Customizability | Look for features that allow you to tailor the tool to your specific security needs. Customizable scanning profiles and reporting options are essential. |
| Ease of Use | Evaluate if the tool is user-friendly and intuitive. Your team should be able to navigate and utilize it without extensive training or technical support. |
| Budget | Consider the total cost, including setup and potential additional fees. Ensure the tool fits your budget while meeting your essential requirements. |
| Security Safeguards | Verify the tool’s security measures to protect sensitive data. Look for encryption, secure data storage, and compliance with industry standards. |
| Support | Assess the availability and quality of customer support. 24/7 support and multiple contact options can be crucial during critical security incidents. |
| Reputation | Research reviews and testimonials from other users. A tool with a strong reputation in the cybersecurity community can provide added assurance of reliability. |
Trends in Penetration Testing Tools
In my research, I sourced countless product updates, press releases, and release logs from different penetration testing tools vendors. Here are some of the emerging trends I’m keeping an eye on:
- AI-Driven Testing: Many tools are now incorporating AI to enhance threat detection and vulnerability analysis. AI can quickly identify patterns and predict potential security breaches, making it a valuable addition for users looking to stay ahead of threats.
- Cloud-Native Security: As businesses move to the cloud, penetration testing tools are adapting to focus on cloud environments. This shift ensures that cloud infrastructures are as secure as traditional networks, with vendors like BreachLock leading the way.
- Continuous Testing: There's a growing demand for tools that provide ongoing security assessments rather than one-off tests. Continuous testing helps businesses maintain security over time, ensuring vulnerabilities are caught and addressed promptly.
- IoT Security Testing: With the rise of IoT devices, there's a need for penetration testing tools that can assess the security of these interconnected devices. Tools that support IoT testing help businesses secure their expanding network of devices.
- User-Centric Dashboards: Vendors are enhancing user interfaces to provide more intuitive and informative dashboards. These dashboards offer real-time insights and actionable data, making it easier for teams to assess and respond to security threats effectively.
What Are Penetration Testing Tools?
Penetration testing tools are software solutions designed to identify and assess security vulnerabilities in networks and applications. These tools are generally used by cybersecurity professionals, ethical hackers, and IT security teams to ensure systems are secure from potential threats.
Automated scanning, vulnerability analysis, and detailed reporting help with identifying weak points, ongoing security assessments, and providing actionable insights. Overall, these tools offer businesses the ability to proactively protect their digital assets and maintain a strong security posture.
Features of Penetration Testing Tools
When selecting penetration testing tools, keep an eye out for the following key features:
- Automated scanning: Quickly identifies vulnerabilities across networks and applications, saving time and resources for security teams.
- Vulnerability analysis: Provides detailed insights into potential security threats, helping teams prioritize and address issues effectively.
- Customizable testing profiles: Allows users to tailor scans to specific needs, ensuring thorough and relevant security assessments.
- Real-time threat detection: Alerts teams to immediate threats, enabling timely responses to potential breaches.
- Cloud-native security: Offers protection and testing capabilities specifically designed for cloud environments, keeping pace with modern infrastructure trends.
- IoT device testing: Assesses the security of interconnected devices, ensuring the entire network, including IoT, is secure.
- Detailed reporting: Generates comprehensive reports that offer actionable insights, aiding in the remediation of vulnerabilities.
- User-friendly dashboards: Provide intuitive interfaces for easy navigation and quick access to critical security data.
- Compliance management: Helps organizations meet industry standards and regulations through built-in compliance checks.
Benefits of Penetration Testing Tools
Implementing penetration testing tools provides several benefits for your team and your business. Here are a few you can look forward to:
- Improved security posture: By identifying and addressing vulnerabilities, these tools help strengthen your organization's defenses against cyber threats.
- Proactive threat management: Real-time threat detection and continuous testing allow your team to address issues before they escalate into major security breaches.
- Resource efficiency: Automated scanning saves time and effort, enabling your team to focus on more strategic security initiatives.
- Compliance assurance: Built-in compliance management features help ensure your organization meets industry standards and regulatory requirements.
- Enhanced decision-making: Detailed reporting provides actionable insights, aiding your team in making informed security decisions.
- Adaptability to modern infrastructure: Features like cloud-native security and IoT device testing ensure your security measures are aligned with current technology trends.
- User-friendly experience: Intuitive dashboards and customizable testing profiles make these tools accessible and easy to use for your team.
Costs and Pricing of Penetration Testing Tools
Selecting penetration testing tools requires an understanding of the various pricing models and plans available. Costs vary based on features, team size, add-ons, and more. The table below summarizes common plans, their average prices, and typical features included in penetration testing tools solutions:
Plan Comparison Table for Penetration Testing Tools
| Plan Type | Average Price | Common Features |
| Free Plan | $0 | Basic vulnerability scanning, limited reporting, and community support. |
| Personal Plan | $10-$30/user/month | Automated scanning, basic reporting, and email support. |
| Business Plan | $50-$100/user/month | Advanced scanning capabilities, detailed reporting, integration support, and priority email support. |
| Enterprise Plan | $150-$300/user/month | Comprehensive security assessments, customizable testing profiles, dedicated account management, and 24/7 support. |
Penetration Testing Tool FAQs
Here are some answers to common questions about penetration testing tools:
Which tool is commonly used for penetration testing?
Penetration testing often involves a variety of tools, each suited to different tasks. Popular options include Metasploit for exploiting vulnerabilities, Nmap for network scanning, and Wireshark for packet analysis. Your choice of tools will depend on your specific needs and the scope of your testing activities.
Do penetration testing tools fall under the category of vulnerability analysis?
Yes, penetration testing tools are a part of vulnerability analysis. While vulnerability scanners identify potential weak points, penetration testing tools go a step further by attempting to exploit these vulnerabilities. This helps determine the potential impact and risk associated with each vulnerability.
What are the top 5 penetration testing techniques?
Common penetration testing techniques include blind testing, where testers have no prior knowledge of the system, and targeted testing, which involves collaboration with IT staff. Other methods are external testing to assess internet-facing assets, internal testing for internal network vulnerabilities, and double-blind testing for real-world attack simulation
How often do you need to do penetration testing?
It’s recommended to conduct penetration testing at least once a year. Regular testing helps ensure that your security measures are up-to-date and can effectively combat emerging threats. Depending on your industry and risk level, more frequent testing may be necessary to maintain security.
What is the difference between automated and manual penetration testing?
Automated testing uses tools to quickly scan for known vulnerabilities, providing broad coverage with minimal human intervention. Manual testing, on the other hand, involves human testers who use their expertise to identify complex vulnerabilities that automated tools might miss. A combination of both can provide comprehensive security assessments.
How do penetration testing tools integrate with existing security systems?
Penetration testing tools often offer integration capabilities with other security systems like SIEMs, vulnerability management tools, and ticketing systems. This allows for streamlined workflows, where identified vulnerabilities can be easily tracked and managed within your existing security infrastructure.
What's Next?
Boost your SaaS growth and leadership skills.
Subscribe to our newsletter for the latest insights from CTOs and aspiring tech leaders.
We'll help you scale smarter and lead stronger with guides, resources, and strategies from top experts!.