10 Best Container Security Solutions Shortlist
Here's my pick of the 10 best software from the 23 tools reviewed.
Our one-on-one guidance will help you find the perfect fit.
Navigating the complex world of container security, I've delved deep into runtime security, scanning container images, and ensuring robust access control. With the rise of on-premises and public cloud workloads, it's crucial to have airtight cybersecurity that defends against malware, pinpoints known vulnerabilities, and offers swift remediation.
From managing metadata to reducing your application's attack surface, I've found that the right tool diminishes security issues, equips security teams to tackle vulnerabilities, and ensures that false positives don't detract from real threats. Think of it as your safety net, securing both your cloud workload and application security, making it an essential asset for any security-focused enterprise.
What Are Container Security Solutions?
Container security solutions focus on safeguarding containerized applications throughout their lifecycle, from development to deployment. These solutions provide protection against vulnerabilities, misconfigurations, and threats that might compromise the integrity or confidentiality of container deployments. Developers, IT professionals, and organizations that deploy containerized applications use these tools to ensure the security of their software within containers.
The primary aim is to protect application infrastructure from potential threats while maintaining the benefits of scalability and portability that containers offer. These solutions are more than just a firewall; they scan repositories, assess dependencies, and safeguard your operating system, ensuring that your running containers and virtual machines remain uncompromised.
Best Container Security Solutions Summary
| Tool | Best For | Trial Info | Price | ||
|---|---|---|---|---|---|
| 1 | Best for auto-fixing container vulnerabilities | Free plan available + free demo | From $350/month | Website | |
| 2 | Best for application-centric container security | 15-day free trial + demo available | From $0.0001 | Website | |
| 3 | Best for comprehensive cloud-native security | Not available | Pricing upon request. | Website | |
| 4 | Best for full-stack container risk assessment | Free demo | Pricing upon request. | Website | |
| 5 | Best for container visibility and forensics | Not available | Pricing upon request. | Website | |
| 6 | Best for eBPF-powered networking and security | Not available | Pricing upon request. | Website | |
| 7 | Best for container vulnerability management | Free plan available | From $25/product/month | Website | |
| 8 | Best for vulnerability and compliance scanning | Not available | Pricing upon request. | Website | |
| 9 | Best for full lifecycle container protection | Not available | Pricing upon request. | Website | |
| 10 | Best for side-scanning container technology | 30-day free trial | Pricing upon request. | Website |
-

Docker
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.6 -

Pulumi
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.8 -

GitHub Actions
Visit Website
Best Container Security Solutions Reviews
Aikido Security is a comprehensive application security platform that covers the entire spectrum from code to cloud, featuring tools for vulnerability management, secrets detection, and compliance monitoring.
Why I Picked Aikido Security: The platform's container image scanning capability identifies vulnerabilities, outdated packages, and license risks. It scans for open-source vulnerabilities and intelligently prioritizes findings based on the sensitivity of the data managed by the container. This prioritization allows you to focus on the most critical threats first, ensuring that resources are allocated efficiently to mitigate risks.
The platform also employs instant deduplication to consolidate reported vulnerabilities and utilizes auto-ignore rules for fast triaging, allowing you to customize severity scores based on specific contexts.
Standout Features & Integrations:
Other standout features include its secrets detection capability, which is crucial for safeguarding sensitive information by identifying exposed API keys and passwords, therefore preventing unauthorized access. It also offers cloud posture management (CSPM), dynamic application security testing (DAST), open-source dependency scanning, static code analysis, surface monitoring, and firewall capabilities.
Integrations include Amazon Web Services (AWS), Google Cloud, Microsoft Azure Cloud, Drata, Vanta, AWS Elastic Container Registry, Docker Hub, Jira, Asana, and GitHub.
Pros and cons
Pros:
- Code-to-cloud security
- Has a comprehensive dashboard and customizable reports
- Scalable for growing teams
Cons:
- Ignores vulnerabilities if no fix is available
- No endpoint security or intrusion detection capabilities
New Product Updates from Aikido Security
Aikido Security's New Integration and Monitoring Updates
Aikido Security's latest update includes attack surface monitoring, enhanced Microsoft Teams integration, and IaC support. For more details, visit Aikido Security's official site.
Dynatrace offers robust monitoring solutions that deliver insights into every aspect of the application lifecycle. Given the rise in containerized application deployments, Dynatrace's focus on application-centric security becomes ever more crucial, ensuring that applications within containers remain free of vulnerabilities and threats.
Why I Picked Dynatrace: After comparing several tools, Dynatrace emerged as a top contender due to its unique application-centric approach to container security. While many tools provide container security, Dynatrace pivots this notion by ensuring the applications within these containers are secure.
This differentiation was significant in my judgment, and it's the reason why I determined Dynatrace to be the 'best for application-centric container security.'
Standout Features & Integrations:
One of Dynatrace's standout features is its full-stack monitoring, which covers applications, containers, infrastructure, and cloud. The AI-powered, automatic, and dynamic baselining helps in proactive anomaly detection. Furthermore, Dynatrace offers real-user monitoring to track and improve user experiences.
When it comes to integrations, Dynatrace offers compatibility with numerous platforms, from cloud providers to CI/CD tools. Its integrations with AWS, Azure, Kubernetes, and Jenkins, among others, enable monitoring and security across various deployment scenarios.
Pros and cons
Pros:
- Broad integration range supports various deployment infrastructures
- AI-powered anomaly detection streamlines threat identification
- Comprehensive full-stack monitoring from infrastructure to applications
Cons:
- While integrations are vast, there might be gaps in some niche technologies or platforms
- Customization may require advanced expertise
- The depth of features might be overwhelming for some users
Prisma Cloud by Palo Alto Networks offers a holistic approach to securing cloud-native applications and infrastructure. It provides an extensive suite of security capabilities that encompass various stages of the application lifecycle, from development to runtime. The tool's comprehensive nature makes it particularly apt for businesses keen on end-to-end cloud security.
Why I Picked Prisma Cloud: After assessing a variety of tools, I determined that Prisma Cloud uniquely addressed a range of cloud-native security challenges. Many solutions in the market focus on individual aspects, but Prisma Cloud stood out because of its ability to provide a comprehensive set of security features.
In my judgment, it is indeed the top choice for those seeking thorough cloud-native security, which is why I believe it's 'Best for comprehensive cloud-native security.'
Standout Features & Integrations:
Among its wide array of features, Prisma Cloud offers robust threat intelligence, compliance assurance, and vulnerability management. Furthermore, its dynamic policy engine enables users to create custom security protocols, tailoring protection to specific organizational needs.
In terms of integrations, Prisma Cloud offers support for a broad range of platforms and services, including AWS, Azure, GCP, Kubernetes, and more. These integrations ensure that businesses can deploy and manage Prisma Cloud across diverse cloud environments with ease.
Pros and cons
Pros:
- Wide-ranging platform and service integrations
- Ability to tailor security protocols with a dynamic policy engine
- Provides an end-to-end cloud-native security solution
Cons:
- Overlapping features might not be utilized by all businesses, leading to potential over-purchasing
- Given its comprehensive nature, there might be a steeper learning curve for some users
- Lack of transparent pricing might be a deterrent for some
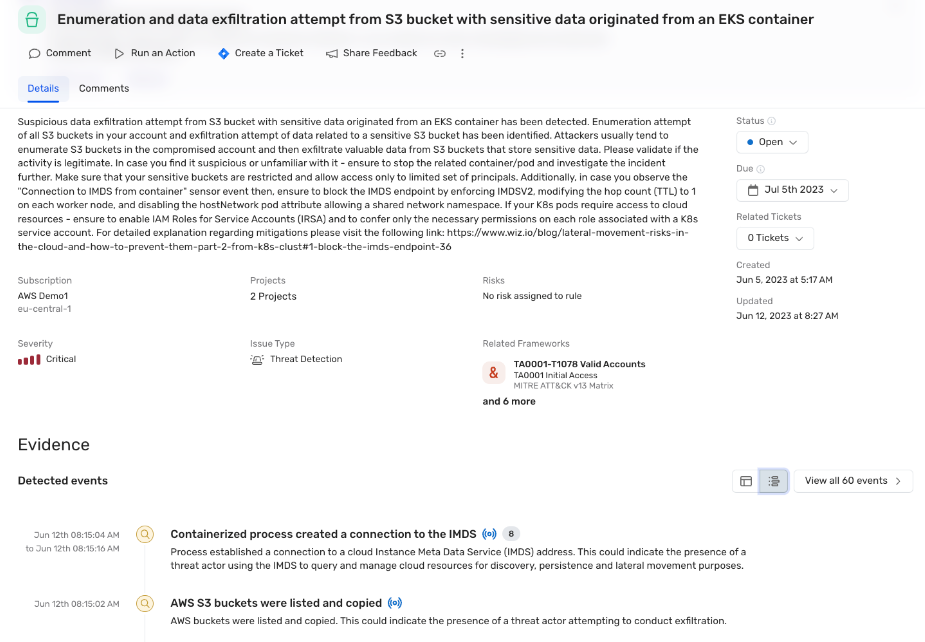
Wiz is a security solution that offers a comprehensive assessment of container risks across an entire tech stack. Through its advanced analysis, it provides organizations with a deeper understanding of their container vulnerabilities and potential threats, justifying its recognition as the 'best for full-stack container risk assessment.'
Why I Picked Wiz: When selecting tools for the list, Wiz stood out due to its robust approach to full-stack container security. What sets it apart is its ability to analyze vulnerabilities in depth across all layers of a tech stack, from the application to the infrastructure. After comparing and judging various tools, I determined that Wiz indeed stands out as the 'best for full-stack container risk assessment.'
Standout Features & Integrations:
Wiz is known for its in-depth risk assessment that spans the entirety of an organization's tech stack, ensuring no stone is left unturned. The tool offers actionable insights that are prioritized based on risk severity, ensuring teams can address the most pressing vulnerabilities first.
Integration-wise, Wiz supports a broad range of cloud platforms, including AWS, Azure, GCP, and more. It also pairs with various CI/CD tools, ensuring security checks can be an integral part of the development process.
Pros and cons
Pros:
- Extensive integration support with major cloud platforms and CI/CD tools
- Prioritized risk findings ensure that teams tackle the most critical threats first
- Comprehensive full-stack analysis covers all aspects of container vulnerabilities
Cons:
- As it's specialized in full-stack risk assessment, it might be overkill for teams looking for more basic security checks
- Requires a more strategic setup and understanding of the tech stack to fully utilize its potential
- The breadth of the tool might be overwhelming for smaller teams or simpler setups
Sysdig specializes in offering a granular level of visibility into containerized environments. Its tools not only monitor but also dive deep into containers to offer forensic insights, making it an invaluable asset when the need arises to investigate incidents or ensure compliance.
Why I Picked Sysdig: When assessing the various tools on the market, Sysdig grabbed my attention with its unparalleled forensic capabilities. Many tools offer visibility, but few provide the depth and breadth of information that Sysdig does.
I judged it as the prime candidate for those prioritizing a meticulous examination of their container environments, precisely because of its superior visibility and post-incident investigation strengths.
Standout Features & Integrations:
Sysdig's standout features include detailed container monitoring, real-time security data, and comprehensive forensic capabilities, allowing users to delve deep into container activities past and present. Moreover, its adaptive alerts can notify users of any unusual patterns or potential threats within their environment.
Integration-wise, Sysdig easily interacts with popular platforms such as Kubernetes, AWS, and Docker. Its adaptability ensures that users can draw insights from a variety of sources, reinforcing their security and operational postures.
Pros and cons
Pros:
- Robust integration options with key platforms
- Offers adaptive alerts for proactive threat management
- Unrivaled forensic and deep dive capabilities
Cons:
- Some users may experience a learning curve with advanced features
- Might be overwhelming for beginners due to its depth
- Lack of transparent pricing can deter potential users
Cilium is a container networking and security project that brings the power of eBPF (Extended Berkeley Packet Filter) to the world of microservices. It provides API-aware network security, load balancing, and visibility for applications running in container orchestration platforms like Kubernetes.
Why I Picked Cilium: I chose Cilium because it takes a unique approach to container networking and security. By leveraging eBPF, Cilium provides granular network visibility, security, and load balancing without modifying application code or container runtimes. This approach stood out to me as it allows organizations to deploy scalable and secure microservices with ease. Cilium is best for eBPF-powered networking and security as it uses this technology to deliver an easy, API-aware network security solution that is both robust and highly customizable.
Standout Features & Integrations:
Cilium provides a wide range of features that enhance container networking and security. Some of its most notable features include API-aware network security, transparent encryption, load balancing, and monitoring capabilities. Additionally, Cilium supports multiple container orchestration platforms, making it a versatile choice for organizations with diverse deployment needs.
Integration is a strong suit of Cilium, as it supports popular container orchestration platforms like Kubernetes and Docker. It also integrates with major cloud providers such as AWS, Azure, and Google Cloud Platform, making it easier for organizations to deploy and manage containerized applications across different environments.
Pros and cons
Pros:
- Integrates with major cloud providers for easier deployment
- Support for multiple container orchestration platforms
- API-aware network security for improved container protection
Cons:
- May require additional configuration to achieve optimal performance
- Steeper learning curve for those unfamiliar with eBPF
- Pricing information not readily available
Snyk stands as a formidable security tool that empowers developers to find and fix vulnerabilities in containers, applications, and open-source libraries. Its expertise in scanning and rectifying container-based vulnerabilities makes it deserving of the title 'Best for container vulnerability management.'
Why I Picked Snyk: In the process of determining the most suitable tools for this list, Snyk was hard to overlook due to its in-depth vulnerability scanning capabilities tailored for containers. The clarity and specificity of its container-focused vulnerability alerts made it stand apart from others.
Given the rising prominence of containerized applications, I believe Snyk rightly fits the bill as 'best for container vulnerability management.'
Standout Features & Integrations:
Snyk not only identifies vulnerabilities but also automates the fixing process, enabling faster resolution. It provides detailed insights into the vulnerability's origin, helping developers trace the issue back to its source.
As for integrations, Snyk easily connects with various CI/CD platforms, source control systems, and container orchestration tools. Its broad spectrum of integrations ensures that developers can incorporate it into their existing workflows with minimal disruption.
Pros and cons
Pros:
- Broad range of integrations with popular development tools and platforms
- Detailed insights into vulnerability origins
- Comprehensive container vulnerability scanning and auto-fixing
Cons:
- Reliance on integrations can lead to potential compatibility issues
- Lack of transparent pricing information
- Might come off as overwhelming for smaller teams or projects
Qualys Container Security (CS) specializes in providing containerized applications with thorough vulnerability assessments and compliance scans. By offering these services, Qualys ensures that developers and organizations are always abreast of potential threats and are in line with industry compliance standards.
Why I Picked Qualys Container Security (CS): When determining which tools to include on this list, Qualys Container Security (CS) stood out due to its emphasis on both vulnerability and compliance scanning. It's not just about identifying threats; it's about ensuring your containerized applications meet the necessary compliance standards.
In my judgment, the dual focus on these two critical areas is what makes it unique, positioning Qualys CS as the best for those in need of robust vulnerability detection paired with comprehensive compliance checks.
Standout Features & Integrations:
Qualys Container Security offers real-time vulnerability management, which not only identifies threats but also provides detailed insights to address them. Additionally, its compliance scanning ensures that your containers meet industry-specific regulations, reducing the risk of breaches and penalties.
On the integration front, Qualys CS supports a wide range of CI/CD tools, enabling developers to embed security checks directly into their development processes. Furthermore, its compatibility with popular container platforms like Docker and Kubernetes ensures an easy and efficient security scanning experience.
Pros and cons
Pros:
- Effective integration with CI/CD tools and major container platforms
- Comprehensive compliance scanning to meet industry standards
- Real-time vulnerability management with detailed insights
Cons:
- Specific advanced features could require additional setup
- Might have a slight learning curve for beginners
- Lack of transparent pricing details
NeuVector offers an all-in-one security solution specifically tailored to containerized applications. Designed to protect containers from their build to their runtime, NeuVector ensures that every phase of a container's life cycle is shielded from potential threats.
Why I Picked NeuVector: I selected NeuVector due to its holistic approach to container security. While many tools focus on just one aspect of container protection, NeuVector distinguishes itself by providing robust defenses throughout the full container lifecycle. This comprehensive strategy is why I believe NeuVector is best for those seeking all-encompassing protection for their container deployments.
Standout Features & Integrations:
NeuVector boasts a set of features that enable automatic container security, deep packet inspection, and vulnerability scanning, ensuring that containers are safeguarded at every stage. The tool also provides runtime visibility, which allows users to monitor and detect any malicious behaviors or vulnerabilities actively.
In terms of integrations, NeuVector works with popular orchestration tools like Kubernetes. It also integrates well with CI/CD pipelines, ensuring that security is enforced from the very first step of the development process. Plus, its compatibility with major cloud platforms facilitates a smooth and protected container deployment across various environments.
Pros and cons
Pros:
- Effective integration with CI/CD pipelines and cloud platforms
- Active runtime visibility and deep packet inspection
- Comprehensive protection across the full container lifecycle
Cons:
- Some features might have a learning curve for beginners
- May require a detailed setup process for optimal configuration
- Pricing details are not transparent
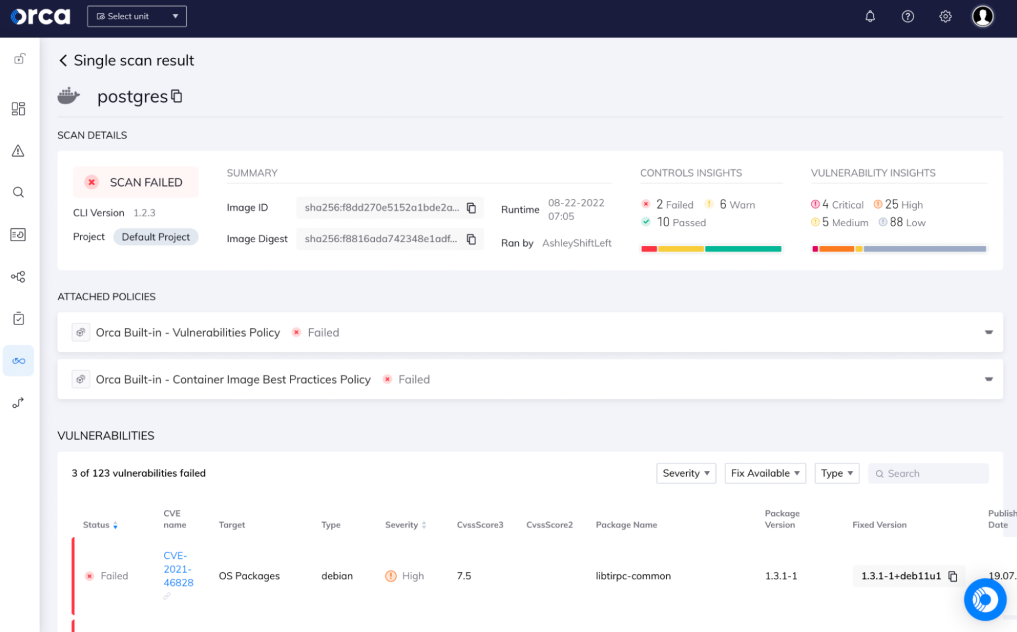
Orca Security is renowned for its unique approach to container and cloud security, leveraging side-scanning technology. This method provides an in-depth view of an organization's cloud infrastructure without the need for agents or network scanning, aligning perfectly with the 'best for side-scanning container technology' description.
Why I Picked Orca Security: In the course of selecting tools, Orca Security's distinctive side-scanning method caught my attention. This innovative approach to container scanning bypasses many of the limitations found in traditional scanning techniques.
The capacity to offer a comprehensive view of vulnerabilities without intrusive agents or tedious network scans led me to judge Orca as the 'best for side-scanning container technology.'
Standout Features & Integrations:
Orca Security's agentless side-scanning technology stands out, eliminating the need for network scanners or credentials. It also provides a full-stack security view from the code to the cloud, covering all layers of the tech stack. Moreover, Orca's risk-prioritized security findings make it easier for teams to address the most pressing vulnerabilities first.
On the integration side, Orca integrates with many popular cloud platforms such as AWS, Azure, and GCP. Their integrations extend to popular CI/CD tools, ensuring that security checks are embedded within the development lifecycle.
Pros and cons
Pros:
- Full-stack security view provides insights across all layers of the technology
- Agentless approach reduces overhead and potential points of failure
- Unique side-scanning technology ensures comprehensive vulnerability detection
Cons:
- Depth of features can sometimes be overwhelming for smaller teams
- While the tool integrates with popular cloud platforms, there might be limitations with lesser-known providers
- The platform's uniqueness might require a learning curve for some teams
Other Noteworthy Container Security Solutions
Below is a list of additional container security solutions that I shortlisted but did not make it to the top 12. They are definitely worth checking out.
- F5 Distributed Cloud App Infrastructure Protection (AIP)
Good for scaling and securing applications in multi-cloud environments
- Kube-Bench
Good for checking Kubernetes configurations against best practices
- Microsoft Defender for Cloud
Good for integrating security within Azure cloud services
- Lacework
Good for comprehensive threat detection across your cloud stack
- ARMO
Good for runtime workload protection across environments
- Trend Micro Cloud Security
Good for hybrid cloud protection across major platforms
- Anchore
Good for in-depth container image inspection and certification
- Red Hat Advanced Cluster Security for Kubernetes
Good for Kubernetes-specific security solutions within clusters
- NetScaler
Good for container traffic management and load balancing
- Mend.io
Good for automating container security compliance
Selection Criteria for Choosing Container Security Solutions
When it comes to choosing software for container security, there's a myriad of options out there. Having navigated this landscape, I've evaluated dozens of container security tools. My primary focus was on tools that provide comprehensive security coverage, ease of use, and the ability to integrate with existing infrastructure. Based on my extensive research and hands-on experience with these tools, here are the criteria that stood out the most:
Core Functionality
- Container Scanning: The tool should be capable of scanning containers for vulnerabilities, both in the images and at runtime.
- Configuration Management: It should help in enforcing best practices for container configurations.
- Runtime Protection: The tool should offer real-time protection, monitoring container activities, and blocking or alerting on suspicious behaviors.
- Compliance Assurance: It should ensure that the containers adhere to industry-specific compliance standards.
Key Features
- Continuous Monitoring: Constant monitoring of containers for any deviations from the defined security policies.
- Integration with CI/CD Pipelines: Easy integration with continuous integration and deployment pipelines to ensure security checks during the development phase.
- Automated Policy Enforcement: Features that allow automated enforcement of security policies without manual interventions.
- Threat Intelligence: Up-to-date threat intelligence that helps in identifying and countering emerging threats.
- Incident Response: Tools and mechanisms to quickly respond to and mitigate any security breaches or vulnerabilities.
Usability
- Intuitive Dashboard: A clear and intuitive dashboard that offers a holistic view of the container environment, highlighting any potential vulnerabilities or threats.
- Role-Based Access: The tool should offer easy configuration of role-based access, ensuring that team members see only what they need to.
- Detailed Documentation: Comprehensive documentation or a learning library that guides users through the features and best practices.
- Responsive Support: Prompt customer support to address any issues or questions users might have.
- Integration Libraries: A suite of plugins or integrations to easily fit the tool into a company's existing tech stack.
Most Common Questions Regarding Container Security Solutions (FAQ's)
What are the benefits of using container security solutions?
Container security solutions offer multiple advantages:
- Improved Security: They scan containers for vulnerabilities, ensuring images and runtimes are secure.
- Compliance Management: Many tools ensure that containers adhere to industry and regulatory compliance standards.
- Real-time Monitoring: These solutions continuously monitor containers for deviations from security protocols and alert them on suspicious activities.
- Easy Integration: They often integrate smoothly with CI/CD pipelines, reinforcing security during the development and deployment stages.
- Automated Policies: Many tools allow for automated enforcement of security policies, reducing the need for manual oversight.
How much do container security solutions typically cost?
The pricing for container security solutions and other container management software varies significantly based on the features, scale, and brand. Some tools offer a subscription-based pricing model, while others might have a one-time licensing fee or even pay-as-you-go rates.
Can you explain the common pricing models for these tools?
The most common pricing models include:
- Subscription-Based: A recurring fee, usually monthly or annually, for using the software.
- Per-User Pricing: Cost is determined by the number of users accessing the tool.
- Per-Container Pricing: Some tools charge based on the number of containers being monitored.
- Licensing: A one-time purchase granting rights to use the software, often with annual fees for updates or support.
What's the typical range of pricing for these tools?
Prices can range anywhere from $10/user/month to upwards of $500/user/month for enterprise-grade solutions. The cost often correlates with the depth of features, scalability, and brand reputation.
Which are the cheapest and most expensive container security solutions?
From the list provided earlier:
- Cheapest: Kube-Bench is an open-source tool and essentially free, though support or additional features might incur costs.
- Most Expensive: Without specific numbers, tools like Microsoft Defender for Cloud or Red Hat Advanced Cluster Security for Kubernetes typically fall on the higher end given their extensive feature sets and brand backing.
Are there any free options available?
Yes, there are open-source and free container security tools available. Kube-Bench, for example, is an open-source solution. However, while free tools provide valuable insights, they might lack some advanced features or dedicated support found in paid solutions.
Other Cybersecurity Software Reviews
Summary
Choosing the right container security solution is paramount in today's digital landscape. Throughout this guide, I've highlighted the significance of container security tools, dissected their unique selling propositions, and provided insight into the vital criteria for selection.
Key Takeaways
- Diverse use cases, and diverse solutions: Every container security solution offers unique advantages, from full-stack risk assessments to specialized side-scanning technologies. Understanding your specific needs is the first step in selecting the right tool.
- Functionality and usability matter: Beyond core security features, the user experience, including ease of onboarding and intuitive interfaces, plays a crucial role in ensuring that your chosen solution fits easily into your workflow.
- Cost vs. value: While pricing is a significant factor, it's essential to weigh the costs against the value provided. Sometimes, a slightly higher-priced solution might offer functionalities and support that far outweigh its cheaper counterparts.
Final Thoughts
There are many noteworthy container and Kubernetes resources to explore. Let's broaden our knowledge base together.