Welcome to this CrowdStrike review, where I'll share insights gathered from years of experience in cybersecurity and information technology. Whether you're concerned about ransomware, malicious activities, or simply looking for a robust endpoint detection platform, I'll provide all the details you need. This deep dive into the CrowdStrike Falcon platform and its suite of endpoint protection platforms like Falcon Complete and Falcon Pro will help you make an informed decision.
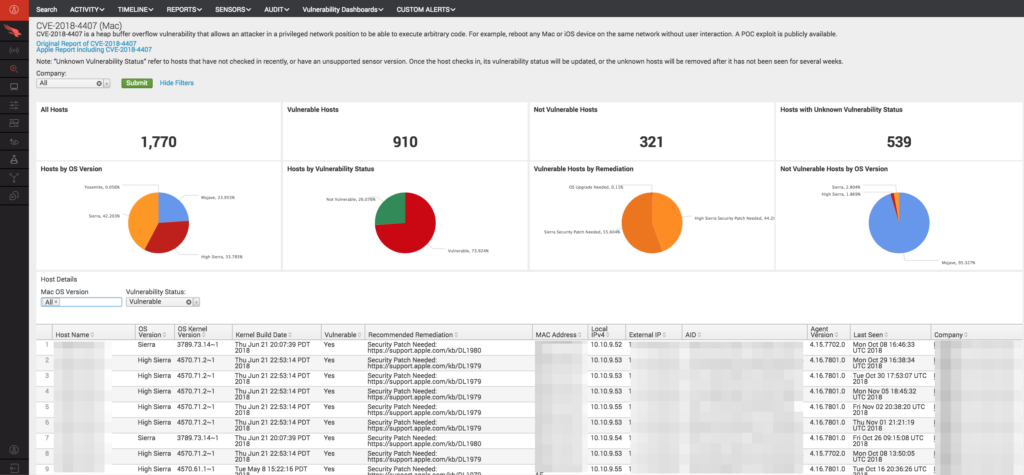
CrowdStrike Product Overview
CrowdStrike provides endpoint protection through its EDR software. Target users are businesses and organizations looking to safeguard their digital assets. The software offers robust defense against advanced threats, streamlining threat detection and incident response. A core strength of CrowdStrike is its ability to mitigate persistent cyberattacks, ensuring businesses can operate without disruption. Noteworthy features include real-time monitoring, threat intelligence integration, and machine learning capabilities.
Pros
- Real-time Monitoring: CrowdStrike constantly observes and analyzes system behavior, ensuring timely identification of suspicious activities.
- Threat Intelligence: The software integrates with global threat databases, offering users insights into potential threats before they become a concern.
- Machine Learning: Leveraging AI, CrowdStrike dynamically adapts its defense mechanisms to new and evolving threats.
Cons
- Interface Learning Curve: Some users find the interface slightly complex, requiring a bit of training to navigate efficiently.
- Integration Challenges: While it supports many tools, certain third-party integrations might not be as seamless.
- Resource Consumption: On certain systems, the software can be a tad resource-intensive, impacting system performance.
Expert Opinion
Having worked with and compared numerous EDR software, I find CrowdStrike among the top tier. Its features, from real-time monitoring to threat intelligence, are commendable. Functionality and support are robust, but where it shines brightest is in its machine learning capabilities. Interface-wise, there's room for improvement, and while its integrations are vast, some can be tricky.
Onboarding is relatively smooth, but all tools have a learning curve. If you're choosing an EDR and value advanced AI capabilities, CrowdStrike should be on your radar. It might not be the best fit for businesses with limited IT resources, but larger enterprises or those under frequent threat will find its offerings invaluable.
CrowdStrike: The Bottom Line
CrowdStrike stands out with its AI-driven threat detection and real-time monitoring. While many EDR tools offer similar features, CrowdStrike's integration of machine learning sets it apart, ensuring it's not just responding to threats but actively learning from them. It also boasts an extensive threat intelligence database, offering users insights few can match.
Another feather in its cap is real-time monitoring, ensuring businesses have an eye on potential threats around the clock. In the landscape of EDR solutions, CrowdStrike offers a combination of innovation and reliability that few can match.
CrowdStrike Deep Dive
Product Specifications
- Real-time Monitoring - Yes
- Threat Intelligence Integration - Yes
- Machine Learning & AI Capabilities - Yes
- Endpoint Isolation - Yes
- File-less Attack Detection - Yes
- Behavioral Analysis - Yes
- Threat Hunting - Yes
- Incident Response - Yes
- Automated Threat Remediation - Yes
- Data Loss Prevention (DLP) - No
- Vulnerability Assessment - Yes
- Cloud-native Architecture - Yes
- Rollback Capabilities - No
- Email Security - No
- Forensic Analysis - Yes
- Asset Discovery - Yes
- Integration with SIEM Tools - Yes
- Multi-factor Authentication (MFA) - No
- Sandbox Analysis - Yes
- Offline Device Protection - Yes
- USB Device Control - No
- Anti-phishing Capabilities - Yes
- Mobile Device Security - Yes
- Customizable Dashboards - Yes
- Reporting and Analytics - Yes
CrowdStrike Feature Overview
- Real-time Monitoring: CrowdStrike constantly scans and analyzes system behavior, ensuring threats are detected as they happen.
- Threat Intelligence Integration: CrowdStrike offers insights into global threats, providing users with a broader context.
- Machine Learning & AI Capabilities: CrowdStrike's dynamic defense mechanisms adjust and learn from evolving threats, ensuring top-tier protection.
- Endpoint Isolation: If a threat is detected, the software can isolate the affected endpoint, preventing further spread.
- File-less Attack Detection: CrowdStrike excels at detecting attacks that don't rely on traditional files, catching advanced threats.
- Behavioral Analysis: The software monitors and evaluates unusual behaviors, targeting potential zero-day exploits.
- Threat Hunting: Proactively search for signs of attacks and compromises within an environment.
- Automated Threat Remediation: Once a threat is identified, CrowdStrike can automatically take measures to neutralize it.
- Forensic Analysis: Post-incident, the software can dive deep into the event, offering insights into how it happened and how to prevent it in the future.
- Offline Device Protection: Even if a device is not online, CrowdStrike ensures it remains protected from potential threats.
CrowdStrike Deep Dive
Product Specifications
- Real-time Monitoring - Yes
- Threat Intelligence Integration - Yes
- Machine Learning & AI Capabilities - Yes
- Endpoint Isolation - Yes
- File-less Attack Detection - Yes
- Behavioral Analysis - Yes
- Threat Hunting - Yes
- Incident Response - Yes
- Automated Threat Remediation - Yes
- Data Loss Prevention (DLP) - No
- Vulnerability Assessment - Yes
- Cloud-native Architecture - Yes
- Rollback Capabilities - No
- Email Security - No
- Forensic Analysis - Yes
- Asset Discovery - Yes
- Integration with SIEM Tools - Yes
- Multi-factor Authentication (MFA) - No
- Sandbox Analysis - Yes
- Offline Device Protection - Yes
- USB Device Control - No
- Anti-phishing Capabilities - Yes
- Mobile Device Security - Yes
- Customizable Dashboards - Yes
- Reporting and Analytics - Yes
Feature Overview
- Real-time Monitoring: CrowdStrike constantly scans and analyzes system behavior, ensuring threats are detected as they happen.
- Threat Intelligence Integration: CrowdStrike offers insights into global threats, providing users with a broader context.
- Machine Learning & AI Capabilities: CrowdStrike's dynamic defense mechanisms adjust and learn from evolving threats, ensuring top-tier protection.
- Endpoint Isolation: If a threat is detected, the software can isolate the affected endpoint, preventing further spread.
- File-less Attack Detection: CrowdStrike excels at detecting attacks that don't rely on traditional files, catching advanced threats.
- Behavioral Analysis: The software monitors and evaluates unusual behaviors, targeting potential zero-day exploits.
- Threat Hunting: Proactively search for signs of attacks and compromises within an environment.
- Automated Threat Remediation: Once a threat is identified, CrowdStrike can automatically take measures to neutralize it.
- Forensic Analysis: Post-incident, the software can dive deep into the event, offering insights into how it happened and how to prevent it in the future.
- Offline Device Protection: Even if a device is not online, CrowdStrike ensures it remains protected from threats.
Standout Functionality
- File-less Attack Detection: While many EDR tools detect conventional threats, CrowdStrike's capability to detect file-less attacks sets it apart. This ensures protection even from the most advanced threats, bypassing traditional methods.
- Machine Learning & AI Capabilities: Though AI is becoming a standard in EDR, CrowdStrike's advanced machine learning ensures its defenses evolve faster than most competitors, offering an edge in proactive protection.
- Behavioral Analysis: CrowdStrike's focus on behavioral analysis, rather than just signature-based detection, means it's equipped to detect new, previously unseen threats. This capability makes it stand out in a sea of EDR solutions that might miss such advanced threats.
- File-less Attack Detection: While many EDR tools detect conventional threats, CrowdStrike's capability to detect file-less attacks sets it apart. This ensures protection even from the most advanced threats, bypassing traditional methods.
- Machine Learning & AI Capabilities: Though AI is becoming a standard in EDR, CrowdStrike's advanced machine learning ensures its defenses evolve faster than most competitors, offering an edge in proactive protection.
- Behavioral Analysis: CrowdStrike's focus on behavioral analysis, rather than just signature-based detection, means it's equipped to detect new, previously unseen threats. This capability makes it stand out in a sea of EDR solutions that might miss such advanced threats.
Integrations
CrowdStrike offers a suite of native integrations with various other tools and platforms. Notable integrations include popular SIEM tools like Splunk and QRadar, aiding in centralizing data and streamlining threat response. Furthermore, CrowdStrike integrates with IT operations platforms like ServiceNow for enhanced incident response workflows. For vulnerability management, CrowdStrike has integrations with platforms like Tenable.
They offer an API, allowing organizations to integrate CrowdStrike's capabilities with their custom tools or third-party platforms. This API provides features like incident data retrieval, endpoint management, and custom threat intelligence feeds. Additionally, a range of add-ons are available that extend the platform's capabilities, including advanced threat intelligence and malware search.
CrowdStrike Pricing
- Pro Tier - $20/user/month (billed annually): This tier offers basic endpoint protection features, suitable for smaller organizations looking to protect their assets.
- Enterprise Tier - $45/user/month (min 10 seats, billed annually): More comprehensive, this tier includes advanced threat hunting, vulnerability assessment, and the aforementioned native integrations.
- Premium Tier - $70/user/month (min 20 seats, billed annually) + $49 base fee per month: The premium offering extends all Enterprise capabilities and introduces priority support, offline device protection, and the inclusion of advanced threat intelligence feeds.
Pricing upon request: CrowdStrike might offer custom plans based on specific needs for specialized requirements or large organizations.
When compared with similar EDR tools in the market, CrowdStrike's pricing can be perceived as being on the higher end. However, given the breadth and depth of features offered, many organizations find the value proposition justified. Potential users should also be aware of additional costs, such as onboarding fees or expenses associated with add-ons, to understand the total cost of ownership.
Ease of Use
CrowdStrike presents a user interface that strives for clarity and simplicity. The dashboard layout is intuitive, grouping relevant information together. However, the depth and breadth of the tool mean there's a considerable amount of data to digest. While the initial onboarding provides guidance, the myriad of customization options can be daunting for some.
Navigating through the myriad features, especially the advanced ones like threat hunting, requires a certain level of familiarity with cybersecurity. This intricacy means new users, or those without extensive EDR software experience, might face a steep learning curve.
Customer Support
Regarding customer support, CrowdStrike offers a range of channels — from email to phone, complemented by an extensive knowledge base. They also provide webinars and tutorials, which benefit new and existing users. However, there are areas where the support could be more consistent. Response times, while generally prompt, can sometimes lag, particularly during peak times.
Moreover, while most interactions with their support team are constructive, there are instances where the depth or clarity of responses falls short of expectations. This inconsistency can be particularly challenging for users seeking timely and comprehensive assistance during a critical issue.
CrowdStrike Use Case
Who Would Be A Good Fit For CrowdStrike
CrowdStrike excels in environments where robust, advanced threat protection is a priority. Typically, businesses and organizations with a considerable digital footprint find the most value in CrowdStrike's comprehensive feature set. These often include sectors like finance, healthcare, and government, where the protection of sensitive data is critical.
Regarding company size, CrowdStrike is a strong fit for medium to large enterprises, particularly those with diverse, distributed, and dynamic IT landscapes. Teams dedicated to cybersecurity also find CrowdStrike invaluable, as the tool provides a depth of functionality that allows for proactive threat hunting and thorough incident analysis.
Who Would Be A Bad Fit For CrowdStrike
While CrowdStrike offers many capabilities, it's not for everyone. Small businesses or startups with limited IT resources may find the platform overwhelming and the pricing steep for their needs. Industries where cybersecurity is less focused might find the tool's extensive functionalities excessive and challenging to navigate.
Additionally, companies looking for a simple, plug-and-play solution may be disappointed with the required level of engagement and customization that CrowdStrike demands. Finally, organizations without a dedicated cybersecurity team or those with team members who are less experienced in advanced EDR functionalities may struggle to leverage the tool’s full potential.
CrowdStrike FAQs
What is CrowdStrike EDR software primarily used for?
CrowdStrike EDR software is primarily used for endpoint protection to detect and prevent cyber threats in real time.
Does CrowdStrike offer real-time threat monitoring?
Yes, CrowdStrike provides real-time threat monitoring as one of its core features, ensuring that threats are detected as they occur.
Is machine learning a part of CrowdStrike's feature set?
CrowdStrike incorporates machine learning and AI capabilities to adapt its defense mechanisms to new and evolving threats.
How difficult is it to onboard and start using CrowdStrike?
While CrowdStrike aims for ease of use, the platform has various advanced features that can present a learning curve, especially for those new to EDR software.
What types of organizations benefit the most from using CrowdStrike?
Medium to large enterprises, particularly in sectors like finance, healthcare, and government, tend to benefit the most due to the comprehensive and advanced features offered by CrowdStrike.
Does CrowdStrike offer any third-party integrations?
CrowdStrike offers native integrations with SIEM tools, IT operations platforms, and vulnerability management systems.
Is customer support available 24/7?
Yes, CrowdStrike offers 24/7 customer support and technical support, although the quality and speed of responses can sometimes vary.
Can CrowdStrike protect offline devices?
Yes, CrowdStrike provides offline device protection, ensuring that endpoints are secure even when not connected to the internet.
Alternatives to CrowdStrike
- Symantec Endpoint Security: For organizations primarily focused on integrating endpoint security with network security, Symantec offers a more interconnected solution that bridges these two often siloed areas.
- Carbon Black: If you're looking for a solution that emphasizes cloud-based threat analytics and incident response features, Carbon Black provides robust cloud-native functionalities that can be beneficial.
- Microsoft Defender for Endpoint: For organizations already deeply integrated with Microsoft products, Microsoft Defender for Endpoint offers seamless integration and a simplified management experience within the Microsoft ecosystem.
See more alternatives for solving cybersecurity issues in this list of best EDR tools in the market today.
CrowdStrike Company Overview & History
CrowdStrike is a cybersecurity company specializing in endpoint security, threat intelligence, and incident response. It is a publicly traded company listed on the NASDAQ, serving a diverse clientele, including extensive finance, healthcare, and government enterprises. Owned by a wide array of institutional and retail investors, CrowdStrike's headquarters is located in Sunnyvale, California. Notable personnel include co-founder and CEO George Kurtz, a well-known figure in the cybersecurity industry, and board member Gerhard Watzinger, who brings extensive experience in the sector.
Its mission statement emphasizes stopping breaches and protecting enterprises with its cloud-native technology. Founded in 2011, CrowdStrike gained significant attention for investigating high-profile cyber-attacks, including the 2014 Sony Pictures hack and the 2016 Democratic National Committee email leak, solidifying its position as a critical player in next-gen cybersecurity.
Conclusion
CrowdStrike offers a great product with features ranging from next-generation antivirus capabilities to Overwatch services for threat hunting. Its modules are built on cutting-edge artificial intelligence technology, making it a strong protection solution among security software offerings. While it's designed to work exceptionally well on a variety of workstations, including Linux, it's essential to weigh it against your own company culture and work-life balance needs.
CrowdStrike even offers a warranty to back its services. If you're seeking to elevate your managed services and keen on XDR capabilities, CrowdStrike is certainly worth considering. I invite you to comment below and share your experiences with this platform or any questions you may have.
