Best Database Security Software Shortlist
Here's my pick of the 10 best software from the 23 tools reviewed.
Our one-on-one guidance will help you find the perfect fit.
Navigating database security requires robust antivirus measures to protect data operations, shield databases from potential threats, and maintain data integrity. Addressing primary pain points like unauthorized access, potential data breaches, and malware is urgent. If you're seeking a solution that guards and improves your database's safety mechanisms, you're in the right place.
What is Database Security Software?
Database security software is a suite of tools designed to protect databases from breaches, unauthorized access, and data corruption. Organizations across industries, from healthcare and finance to e-commerce, utilize these software solutions to safeguard sensitive information.
These systems serve database administrators, IT professionals, and cybersecurity teams, ensuring that data remains secure, access is regulated, and potential vulnerabilities are promptly addressed. This maintains the integrity and privacy of the stored data. The software often includes features like real-time activity monitoring, data encryption, and data masking to prevent unauthorized data access and data breaches. Advanced security features like SQL injection prevention and machine learning algorithms for anomaly detection may also be included. It is essential to choose a solution that fits the organization's needs, considering factors like scalability, operating system compatibility (Windows, Linux), and whether a cloud-based or on-premises solution is more appropriate.
Best Database Security Software Summary
| Tool | Best For | Trial Info | Price | ||
|---|---|---|---|---|---|
| 1 | Best for scalable data backup solutions | Not available | Pricing upon request | Website | |
| 2 | Best for integrated cloud applications and platform services | 30-day free trial | Pricing upon request | Website | |
| 3 | Best for comprehensive database performance monitoring | Not available | Pricing upon request | Website | |
| 4 | Best for automated data protection | Not available | Pricing upon request | Website | |
| 5 | Best for data loss prevention tasks | Not available | Pricing upon request | Website | |
| 6 | Best for user behavior analytics | Not available | Pricing upon request | Website | |
| 7 | Best for data risk analytics and insights | Not available | Pricing upon request | Website | |
| 8 | Best for real-time database monitoring | Not available | Pricing upon request | Website | |
| 9 | Best for threat prevention across all networks | Free demo available | Pricing upon request | Website | |
| 10 | Best for managed security services | Free demo available | Pricing upon request | Website |
-

Docker
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.6 -

Pulumi
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.8 -

GitHub Actions
Visit Website
Best Database Security Software Reviews
NetApp Data Protection offers businesses an effective and reliable way to back up and safeguard their crucial data. Recognizing the importance of scalability in today's dynamic data environments, this tool provides the flexibility to adapt to increasing backup demands while maintaining efficiency.
Why I Picked NetApp Data Protection:
In my journey of selecting data protection tools, NetApp caught my attention due to its clear emphasis on scalable solutions. Having judged and compared multiple tools, I found that NetApp's offerings were distinct in their ability to cater to both small and large-scale data backup needs. It's evident to me that for businesses anticipating growth or already managing vast amounts of data, NetApp is truly the 'Best for...' scalable data backup solution.
Standout Features & Integrations:
NetApp Data Protection prides itself on features such as advanced security, ensuring data is safeguarded from potential hackers and threats. It offers robust data encryption and data masking techniques, heightening the security posture of stored data. The tool integrates with prominent cloud providers like AWS and Azure, making it ideal for hybrid data backup strategies involving both on-premises and cloud database systems.
Pros and cons
Pros:
- Integrations with major cloud providers improve backup flexibility and strategy
- Advanced security measures, including data encryption, protect against various security threats
- Scalable solutions cater to a range of backup requirements from small to extensive
Cons:
- Some users might find the interface less intuitive compared to other tools in the market
- Initial setup and configurations may require a steeper learning curve
- Might be overkill for businesses with very minimal backup needs
Oracle is a titan in the world of database management systems, offering a comprehensive suite of tools that help businesses manage and secure their data. Known for its integration prowess, Oracle brings together cloud applications and platform services under a unified environment, a trait that proves pivotal for many enterprises.
Why I Picked Oracle:
In the process of evaluating various tools, Oracle consistently stood out for its comprehensive offerings. My judgment was driven by its established reputation and the opinions of countless industry professionals who laud its capabilities. Among the myriad offerings available, Oracle's distinct ability to integrate cloud applications and platform services set it apart, reinforcing my belief that it's truly the best for organizations seeking integration capabilities.
Standout Features & Integrations:
Oracle is renowned for its advanced security mechanisms, which encompass data encryption, data masking, and a robust firewall, ensuring a formidable defense against potential threats. Additionally, its machine-learning capabilities aid in activity monitoring and flagging anomalies. Integrations are a strong suit for Oracle; it effortlessly connects with cloud giants like AWS and Microsoft's Azure. Moreover, its compatibility extends to various operating systems, including Linux and Windows, thereby solidifying its position as a versatile database management system.z
Pros and cons
Pros:
- Comprehensive integrations with major cloud providers and operating systems
- High scalability catered for both small businesses and large enterprises
- Robust data security solutions with advanced encryption and firewall
Cons:
- On-premises setup requires dedicated resources and maintenance.
- The depth of features can be overwhelming for simple tasks
- Might be complex for users new to database management systems
Best for comprehensive database performance monitoring
SolarWinds Database Management is a robust tool that allows users to monitor, optimize, and improve database performance. With the increasing complexity of database ecosystems, having a solution that offers a holistic view of database health and performance is crucial, and that's where SolarWinds shines.
Why I Picked SolarWinds Database Management:
In my process of selecting database management tools, I was particularly drawn to SolarWinds due to its comprehensive approach to monitoring database performance. Among the plethora of tools I compared, SolarWinds stood out because of its intricate detailing and all-encompassing perspective on database health. I determined that it truly is 'Best for...' those who need an overarching view of their database's performance and want to take preemptive measures based on detailed insights.
Standout Features & Integrations:
SolarWinds offers a myriad of features, from advanced security mechanisms to in-depth activity monitoring. Its ability to identify potential SQL Injection threats and provide data masking ensures data privacy and security. Integrating with a variety of database servers such as Oracle Database, PostgreSQL, and MySQL, it offers versatility to cater to diverse database management systems. The tool also incorporates cloud data functionalities, enabling a smooth transition for those using cloud database solutions.
Pros and cons
Pros:
- Comprehensive monitoring capabilities provide a holistic view of database performance
- Integration with various database servers ensures compatibility and versatility
- Advanced security features, including data masking and SQL Injection threat detection, bolster security posture
Cons:
- May come with a steeper learning curve for beginners due to its extensive features
- Some users might experience challenges with customization and tweaking to specific needs
- The comprehensive nature might be overwhelming for users seeking simpler solutions
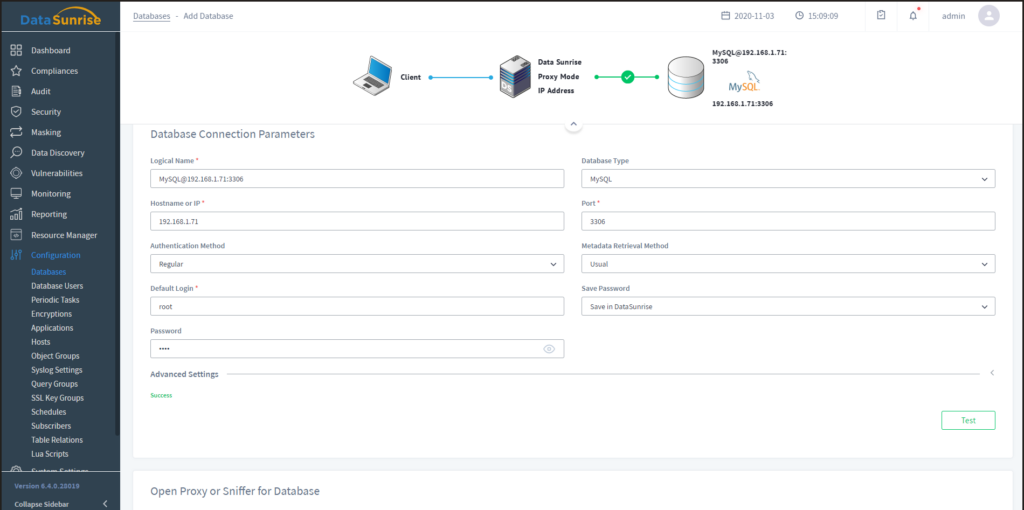
DataSunrise is a leading provider of advanced security products focused on ensuring comprehensive data protection. Through their automated solutions, they address vulnerabilities, prevent data breaches, and guarantee compliance, justifying their standing as the best in automated data protection.
Why I Picked DataSunrise:
In the realm of data security solutions, choosing DataSunrise was a deliberate decision. I selected this tool after judging its efficiency, comparing it to other contenders, and determining that its focus on automation is unparalleled. The tool's commitment to robust automated protection set it apart from others, aligning with my criteria of 'Best for...' automated data protection.
Standout Features & Integrations:
DataSunrise offers a data firewall that actively monitors and protects against SQL Injection threats, ensuring the integrity of data across database servers. Their key management and data encryption mechanisms further improve data security. Notably, DataSunrise has integrations with popular cloud database systems like Azure and AWS and supports various database management systems such as Oracle Database, PostgreSQL, and MySQL.
Pros and cons
Pros:
- Compatible with various operating systems, including Linux and Windows
- Comprehensive activity monitoring and real-time threat prevention
- On-premises and cloud-based automated data protection solutions
Cons:
- The need for regular updates and maintenance to stay ahead of emerging threats
- Its expansive set of features might be overwhelming for small businesses
- May present a learning curve for businesses unfamiliar with automated security protocols
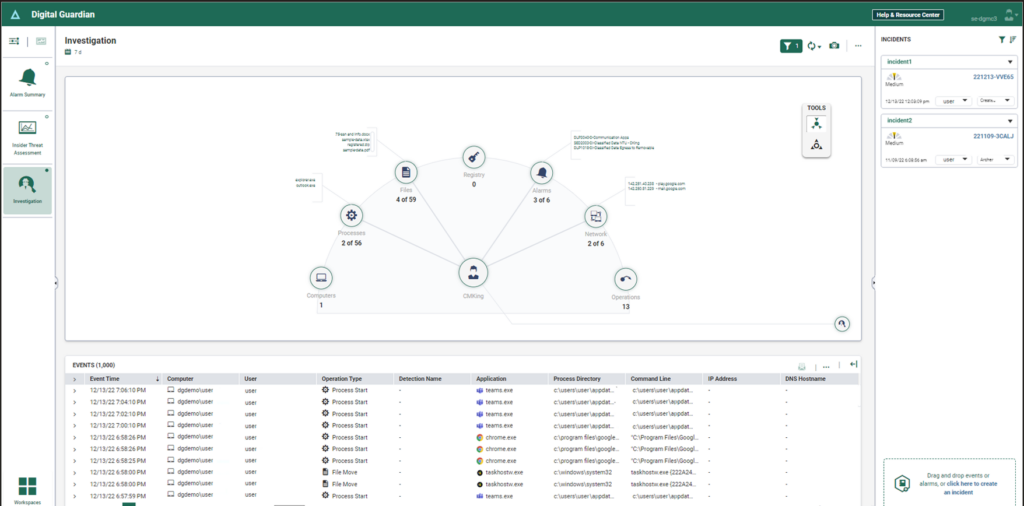
Digital Guardian Data Protection is a leading security suite designed to safeguard sensitive data and prevent potential breaches. The platform's forte lies in its ability to proactively monitor and mitigate risks associated with data loss, making it paramount for businesses seeking a focus on data loss prevention tasks.
Why I Picked Digital Guardian Data Protection:
After extensively comparing multiple security products, I chose Digital Guardian for its outstanding reputation and specific emphasis on data loss prevention. Its features and capabilities stood out from the competition, especially when determining its effectiveness in preventing unauthorized data access. This tool, in my opinion, is unequivocally 'Best for...' those organizations aiming to prioritize data loss prevention tasks.
Standout Features & Integrations:
Digital Guardian boasts an advanced security framework that integrates with a wide array of operating systems, including Windows and Linux. It utilizes machine learning techniques to adapt and respond to evolving security threats. Furthermore, its integration capabilities span across several providers, making it compatible with platforms like AWS, Azure and database management systems such as Oracle Database and PostgreSQL.
Pros and cons
Pros:
- Broad integration capability with popular cloud database providers and database management systems
- Advanced activity monitoring that leverages machine learning for predictive threat analysis
- Tailored solutions for both on-premises and cloud-based systems
Cons:
- The abundance of features can be overwhelming for smaller enterprises
- Periodic updates required to address evolving security threats
- Might be perceived as complex for businesses new to data loss prevention tools
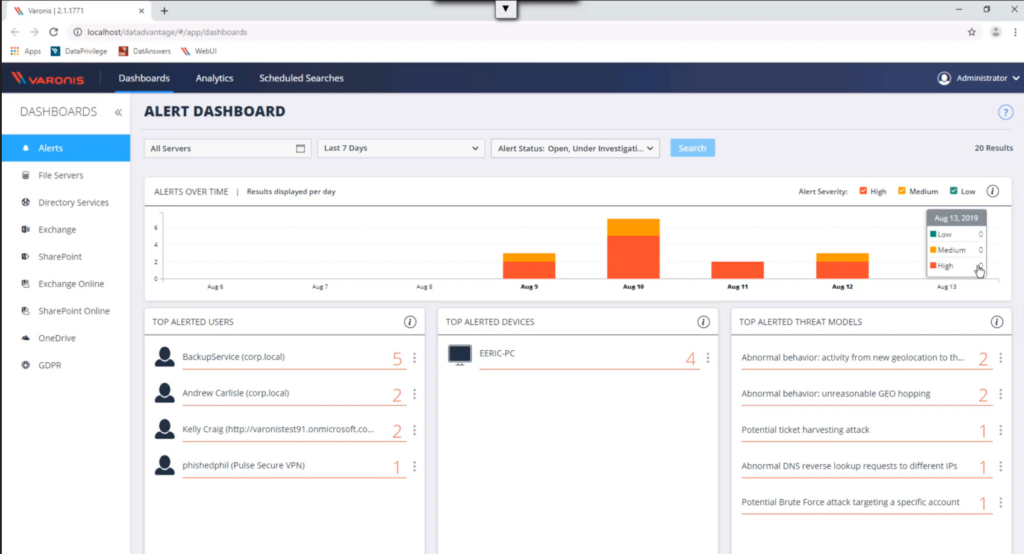
Varonis Data Security Platform is a comprehensive security solution that centers on monitoring and analyzing user behavior to prevent potential data breaches. Given the increasing importance of understanding user patterns to fortify security, Varonis excels at leveraging user behavior analytics as its main defense mechanism.
Why I Picked Varonis Data Security Platform:
In the process of determining the right tool for this list, I gravitated towards Varonis due to its distinct approach to security using user behavior analytics. Many platforms offer generic security solutions, but Varonis stands out because of its specialized focus on analyzing user patterns. I am of the firm opinion that it is 'Best for...' organizations that want to emphasize user behavior analytics for bolstering their security posture.
Standout Features & Integrations:
One of the core features of Varonis is its advanced user activity monitoring, which provides real-time insights into any unusual patterns. This is complemented by its data encryption and data masking capabilities that add an additional layer of security. Its integration landscape is expansive, working in harmony with popular cloud providers like AWS and Azure, and is also compatible with database servers like Oracle Database and PostgreSQL.
Pros and cons
Pros:
- Specialized in user behavior analytics, offering a unique approach to data security
- Extensive activity monitoring tools backed by machine learning for improved threat detection
- Compatibility with a broad range of cloud database providers and database management systems
Cons:
- Some features might be redundant for smaller businesses that only need basic security solutions
- Requires consistent updates to adapt to evolving security landscapes
- Might have a learning curve for businesses that are new to user behavior analytics tools
Imperva Data Security emerges as a comprehensive solution designed to safeguard sensitive data while also offering deep analytical insights into potential risks. With the increasing importance of data management and security, Imperva excels by providing targeted analytics that aids businesses in understanding and mitigating potential vulnerabilities, justifying its reputation as the go-to tool for data risk analytics and insights.
Why I Picked Imperva Data Security:
My journey in selecting the right tools was intensive, and Imperva's offering stood out immediately. The choice became clear when I discerned its unparalleled focus on data risk analytics combined with insights that aren't typical of many providers. This unique combination makes Imperva distinctly superior. I've always believed that understanding risks is half the battle in security, and this tool, in my opinion, is 'Best for...' businesses seeking not just protection but also clarity on their data vulnerabilities.
Standout Features & Integrations:
Imperva is lauded for its advanced security suite, particularly its capabilities in data encryption, data masking, and ensuring data privacy in line with GDPR. Additionally, its robust firewall protects against threats such as SQL Injection and other data breaches. Integrations are a key strength, with Imperva linking with cloud databases like AWS and Azure while also offering compatibility with popular database management systems, including Oracle Database, PostgreSQL, and MySQL.
Pros and cons
Pros:
- Comprehensive firewall and security controls, ensuring protection against modern threats
- Broad integration with popular cloud providers and database systems
- Advanced data analytics offering deeper insights into vulnerabilities
Cons:
- As a comprehensive suite, it might be overkill for organizations with limited data management needs
- Some features might have a learning curve, especially for smaller teams
- Might be overwhelming for businesses only seeking basic security solutions
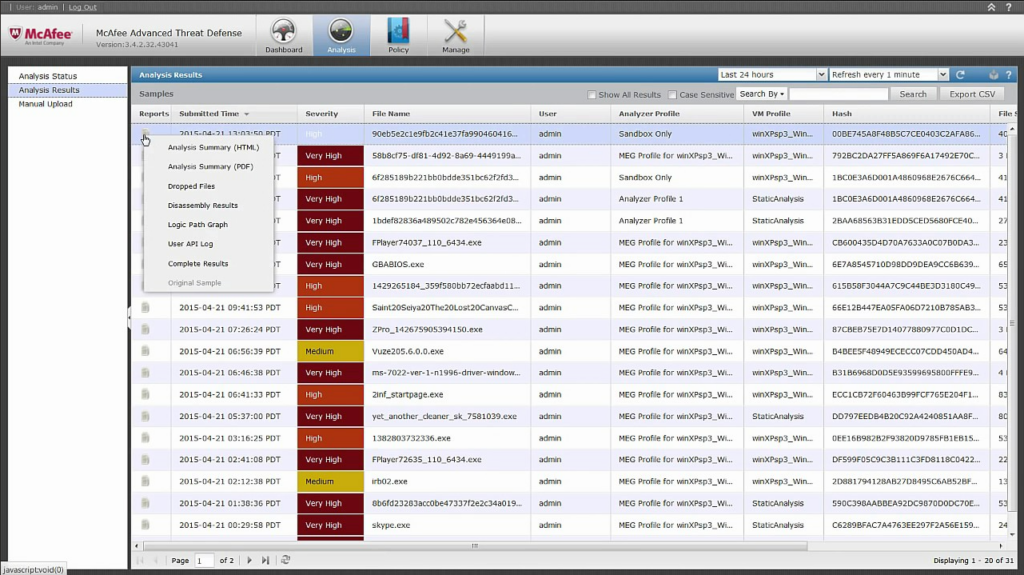
McAfee Database Security is a pivotal tool that ensures databases are shielded from potential threats, providing organizations with a safety net in an era of evolving cybersecurity challenges. Their expertise in real-time database monitoring makes them invaluable for enterprises that prioritize swift threat detection and instantaneous response.
Why I Picked McAfee Database Security:
In the midst of analyzing various security tools, McAfee's name echoed prominently. What fueled my decision to select this tool over others was its outstanding reputation in security solutions, coupled with the consistent feedback from professionals. McAfee distinctly outshines in delivering real-time database monitoring, making it my top choice for organizations that can't afford to have even the slightest delay in detecting security threats.
Standout Features & Integrations:
McAfee's prowess lies in its capability to provide real-time activity monitoring, ensuring swift detection of misconfigurations, SQL Injections, and unauthorized data access. This is further improved by their advanced security policies and a robust firewall that mitigates potential threats. McAfee Database Security integrates with SIEM systems, enabling businesses to have a comprehensive overview of their security posture. Further, its compatibility with major database servers, including MySQL and Oracle Database, amplifies its versatility.
Pros and cons
Pros:
- Effective integrations with SIEM systems and major database servers
- Advanced security controls against SQL Injections and data breaches
- Strong real-time monitoring capabilities
Cons:
- Certain advanced features may have a steep learning curve
- Predominantly focuses on databases, which might necessitate additional tools for holistic security
- The interface might be intricate for newcomers
Check Point provides a robust security posture for organizations, emphasizing the prevention of threats across varied networks. As cyber threats continue to evolve, Check Point stays at the forefront, making it an excellent choice for those who prioritize comprehensive threat prevention across all network environments.
Why I Picked Check Point:
During my research process, choosing the right tools was paramount, and Check Point caught my attention for its specialized focus on threat prevention. I judged its merits based on comprehensive comparisons, and it clearly emerged as a leader. What makes it particularly stand out is its holistic approach to security, covering every nook and cranny of an organization's network. Given its prowess, I confidently believe it's 'Best for...' ensuring consistent threat prevention across all networks.
Standout Features & Integrations:
Check Point boasts an advanced security suite, with features including a top-tier firewall, SIEM integration, and advanced security protocols against hackers and potential misconfigurations in systems like MySQL. Its integrations are vast, connecting with major cloud providers such as AWS and Azure. Additionally, Check Point supports integrations with database servers, including Oracle Database, PostgreSQL, and more.
Pros and cons
Pros:
- Comprehensive threat prevention across diverse networks, be it on-premises or cloud-based
- Broad integration capabilities, making it compatible with popular cloud providers and database systems
- Adherence to GDPR, ensuring data privacy is maintained while managing threats
Cons:
- For smaller organizations, the breadth of features might be more than required
- Depending on the setup, there might be complexities during the initial configuration
- The wide range of features might demand a steeper learning curve for IT teams
Trustwave specializes in providing advanced security solutions that are tailored to meet the unique needs of various organizations. Their managed security services are designed to offer a comprehensive protection strategy, ensuring that businesses are safeguarded from evolving threats. Their expertise in this particular domain justifies their reputation as the best for managed security services.
Why I Picked Trustwave:
When it came to selecting the right tool for managed security, Trustwave was among the top contenders. I chose Trustwave after thorough comparisons and determining that their approach to security solutions is both innovative and efficient. Their dedication to providing end-to-end managed services makes them stand out from the crowd. Given their longstanding reputation and proven track record, it's clear to see why they are 'Best for...' managed security services.
Standout Features & Integrations:
Trustwave offers a robust security suite, including SIEM integration, advanced security controls against hackers, and activity monitoring to ensure real-time response to threats. They have also incorporated machine learning techniques to predict and prevent potential security risks. Trustwave's integrations are extensive; they work with major cloud providers like AWS and Azure and support integrations with popular database management systems like Oracle Database and PostgreSQL.
Pros and cons
Pros:
- Adheres to GDPR guidelines ensuring data privacy alongside threat management
- Wide range of integrations with popular cloud providers and database systems, improving its adaptability
- Comprehensive managed security services that cover both on-premises and cloud-based environments.
Cons:
- The depth of services provided may introduce a learning curve for some IT teams
- Setup and initial configuration might be complex for businesses with simpler needs
- Some businesses might find the extensive features more than they require
Other Database Security Software
Below is a list of additional database security software software that I shortlisted, but did not make it to the top. Definitely worth checking them out.
- Sophos SafeGuard Encryption
For full disk and file encryption
- Fortinet FortiDB
For centralized database vulnerability assessments
- Idera SQL Compliance Manager
Good for SQL server auditing
- Trend Micro Data Protection
Good for hybrid cloud security
- AppGuard
Good for proactive malware blocking
- Spirion Data Protection
Good for sensitive data discovery and protection
- CrowdStrike Falcon
Good for endpoint threat detection
- Cloudera Navigator
Good for big data security and governance
- Kaspersky Data Center Security
Good for safeguarding complex infrastructures
- Qualys Cloud Platform
Good for vulnerability management at scale
- Tenable
Good for risk-based vulnerability management
- Protegrity Data Protection
Good for enterprise data-centric security
- Alert Logic
Good for managed detection and response
Selection Criteria for Database Security Software
In the ever-evolving digital world, ensuring the safety of your database is crucial. With the array of options available, I've taken it upon myself to try and evaluate numerous tools in this category. I've tested each of these tools rigorously and whittled them down to the best ones. What I was really looking for was robust authentication mechanisms, stringent permissions protocols, and advanced firewall capabilities tailored for databases. Below, I outline the specific criteria that mattered most during my evaluations.
Core Functionality
When choosing a database security tool, the following functions are non-negotiable:
- Protection from Unauthorized Access: Ensure that only authenticated users can access the data.
- Data Encryption: Guard data both at rest and in transit.
- Real-time Monitoring: Instantly identify and alert on suspicious activities.
- Vulnerability Assessment: Periodically check and rectify security flaws.
- Audit Trails: Maintain detailed logs of all access and changes made to the database.
Key Features
For a database security software to truly stand out, it must possess these distinctive features:
- Advanced Authentication Protocols: Beyond mere passwords, the tool should support multi-factor authentication to verify user identities.
- Granular Permissions: Ensure that users only access data relevant to their workloads, preventing potential data leaks.
- Database Firewall: Offer a specialized firewall that's adept at detecting and blocking malicious database-specific traffic, different from a typical web application firewall.
- Integration with DbProtect: Harness its capability to identify vulnerabilities in real-time.
- Audit Vault: Store and analyze audit logs securely, ensuring data changes are trackable and anomalies are flagged.
- Support for Multiple Databases: Whether you're using Oracle, Sybase, or any other platform, the tool should be versatile enough to support a range of databases.
Usability
For an experience using database security tools, consider the following usability aspects:
- Intuitive Interface: A clear, organized dashboard that displays alerts, audit logs, and security metrics in a comprehensible manner.
- Role-based Access: Configure the tool so that team members see only what's relevant to their roles, streamlining permissions.
- Easy Filtering and Tagging: Especially crucial when dealing with a multitude of databases, this functionality helps users quickly locate specific data sets or alerts.
- Comprehensive Onboarding: Given the complexity of database security, the chosen tool should have an extensive knowledge base, training program, or learning library to familiarize users with its features and best practices.
- Responsive Customer Support: In the event of any anomalies or issues, it's crucial to have a dedicated support team that can guide and assist promptly.
By focusing on these specific criteria, choosing a database security software that aligns with your needs becomes a more informed and precise endeavor.
More Database Security Software Reviews
Summary
Database security is paramount in today's digital landscape, and with a plethora of options available, it's crucial to make an informed choice. This article delves into the foundational functionalities, standout features, and usability aspects that one should consider when selecting the ideal database security software. With unauthorized access, data breaches, and vulnerabilities becoming increasingly sophisticated, a robust and efficient tool is no longer a luxury but a necessity.
Key Takeaways:
- Core Functionality is King: Ensure the tool you choose offers comprehensive protection from unauthorized access, encrypts data both at rest and in transit, monitors activities in real-time, assesses vulnerabilities periodically, and keeps detailed audit trails.
- Features that Differentiate: Beyond basic functionalities, key features like advanced authentication protocols, granular permissions, specialized database firewall, integration with platforms like DbProtect, and support for multiple databases set the top-tier software apart.
- Usability Matters: A tool's efficiency isn't just about its features but also its usability. Seek out software with an intuitive interface, role-based access, easy filtering mechanisms, comprehensive onboarding resources, and responsive customer support to ensure a user experience.
Most Common Questions Regarding Database Security Software
What are the benefits of using database security software?
Using database security software provides numerous advantages:
- Data Protection: These tools safeguard sensitive data from unauthorized access, ensuring that your data remains confidential.
- Compliance Adherence: Many tools help businesses adhere to data protection regulations like GDPR, ensuring that they don’t face hefty fines or reputational damage.
- Real-time Monitoring: Database security solutions offer continuous activity monitoring, alerting you immediately to any suspicious activities or potential security threats.
- Advanced Security Features: Many come with features such as data masking, encryption, and firewall capabilities to further secure your data.
- Minimized Risk: By detecting vulnerabilities and misconfigurations, these tools can significantly reduce the risk of data breaches.
How much does database security software typically cost?
The cost can vary widely based on the complexity, features, and size of the organization. Prices might range from as low as $10/user/month for basic solutions to over $1000/user/month for enterprise-grade software with advanced features.
What are the common pricing models for these tools?
Database security software can have several pricing models:
- Per User/Per Month: Pricing based on the number of users accessing the software each month.
- Perpetual License: A one-time fee, usually with annual maintenance charges.
- Volume-based: Pricing depends on the volume of data or the number of databases being monitored.
- Freemium: Some tools offer basic features for free, with advanced features available in paid plans.
Which are the cheapest and most expensive software options?
The cheapest options usually come from open-source solutions or smaller vendors targeting SMBs. Examples might include SQLite or MySQL’s basic editions. On the other hand, enterprise-grade solutions from vendors like Oracle or IBM Security Gardium tend to be on the more expensive side.
Are there any free tools available?
Yes, several database security software solutions offer free versions. These typically come with limited features but can be useful for small businesses or individual projects. Open-source solutions like SQLite or the basic editions of MySQL can be utilized without any cost.
Why is there such a broad range in pricing?
The pricing spectrum is broad due to the diverse needs of businesses. While a small business might need only basic features, large enterprises require advanced functionalities, scalability, and additional support, driving up the cost.
Do these tools only support specific databases?
While some database security tools are designed for specific database systems like Oracle Database or PostgreSQL, many others are versatile and support multiple database management systems, both on-premises and cloud-based.
How do I determine which security software is right for my business?
Choosing the right software depends on several factors: the size of your organization, the nature of the data you handle, compliance requirements, your budget, and the specific databases you use. It’s essential to compare features, read reviews, and perhaps start with a trial version to ensure the chosen tool aligns with your needs.
What do you think?
If you've come across a database security software that you believe deserves a mention, or if you've had a particularly good (or challenging) experience with a tool not covered in this guide, I'd love to hear from you. Your insights and recommendations are invaluable, and they help refine and expand the resource for everyone.