Best Data Masking Software Shortlist
Here’s my shortlist of the best data masking software:
Our one-on-one guidance will help you find the perfect fit.
If your team needs to use sensitive data for development, testing, or analytics—but can’t afford to risk exposure—you’re likely exploring data masking solutions. Maybe you’re struggling to comply with GDPR or HIPAA, or you’ve found your existing processes are too manual or error-prone to scale. These gaps create real risks for privacy and compliance.
Data masking software helps reduce those risks by replacing sensitive data with realistic, usable substitutes. It allows you to protect customer information, support internal use cases safely, and meet regulatory requirements without blocking access to data where it’s needed.
I’ve worked with SaaS teams navigating these exact challenges, helping them evaluate solutions that balance privacy, usability, and control. In this guide, I’ll walk you through tools that stand out for their practical value—so you can choose one that fits the way your team works.
Why Trust Our Software Reviews
We’ve been testing and reviewing SaaS development software since 2023. As tech experts ourselves, we know how critical and difficult it is to make the right decision when selecting software. We invest in deep research to help our audience make better software purchasing decisions.
We’ve tested more than 2,000 tools for different SaaS development use cases and written over 1,000 comprehensive software reviews. Learn how we stay transparent & check out our software review methodology.
Best Data Masking Software Summary
This comparison chart summarizes pricing details for my top data masking software selections to help you find the best one for your budget and business needs.
| Tool | Best For | Trial Info | Price | ||
|---|---|---|---|---|---|
| 1 | Best for industry compliance | Not available | From $50/user/month (billed annually) | Website | |
| 2 | Best for cloud compatibility | Free demo available | From $50/user/month | Website | |
| 3 | Best for dynamic masking | Free trial available + free demo | From $60/user/month (billed annually) | Website | |
| 4 | Best for real-time protection | Free demo available | From $10/user/month | Website | |
| 5 | Best for enterprise use | 30-day free trial | Pricing upon request | Website | |
| 6 | Best for scalable solutions | Free demo available | From $20/user/month | Website | |
| 7 | Best for database integration | Free demo available | From $10.001/device/month | Website | |
| 8 | Best for data scrambling | Not available | From $25/user/month (billed annually) | Website | |
| 9 | Best for data tokenization | Not available | From $30/user/month | Website | |
| 10 | Best for GDPR compliance | Free demo available | From $30/user/month | Website |
-

Docker
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.6 -

Pulumi
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.8 -

GitHub Actions
Visit Website
Best Data Masking Software Reviews
Below are my detailed summaries of the best data masking software that made it onto my shortlist. My reviews offer a detailed look at the key features, pros & cons, integrations, and ideal use cases of each tool to help you find the best one for you.
BizDataX is a data masking software designed for businesses that need to ensure compliance with industry regulations. It primarily serves enterprise users who handle sensitive data and require secure processing to meet compliance standards.
Why I picked BizDataX: It's tailored for industries with strict data privacy requirements, making it a reliable choice for compliance. BizDataX offers features like rule-based data masking and comprehensive audit trails. These features help your team maintain data integrity while adhering to industry standards. Its focus on compliance sets it apart from other data masking solutions.
Standout features & integrations:
Features include rule-based data masking that allows you to customize masking processes according to your industry needs. It also provides comprehensive audit trails to ensure data processing transparency. Additionally, BizDataX offers high scalability to support growing data volumes.
Integrations include support for Oracle, Microsoft SQL Server, IBM Db2, SAP HANA, PostgreSQL, MySQL, and more.
Pros and cons
Pros:
- Customizable masking rules
- High scalability for large datasets
- Strong focus on compliance
Cons:
- Steep learning curve for new users
- Limited customization options
Informatica Cloud Data Masking is a data protection solution designed for businesses utilizing cloud environments. Its main user base includes organizations needing to secure sensitive data across various cloud platforms, with key functions like data masking and encryption.
Why I picked Informatica Cloud Data Masking: It's tailored for cloud environments, making it ideal for businesses transitioning to or operating in the cloud. The tool offers dynamic data masking, which helps protect data without impacting its usability. It also provides encryption capabilities to ensure data remains secure during transfer and storage. Its ability to integrate seamlessly with cloud platforms makes it a versatile choice for organizations with diverse IT infrastructures.
Standout features & integrations:
Features include dynamic data masking, allowing your team to protect data in real-time. The tool's encryption capabilities ensure data security during transfer and storage. Additionally, it offers role-based access controls, giving you the flexibility to manage who accesses sensitive information.
Integrations include Amazon Web Services, Microsoft Azure, Google Cloud, Salesforce, Oracle, SAP, Snowflake, Databricks, MongoDB, and IBM.
Pros and cons
Pros:
- Offers role-based access controls
- Tailored for cloud environments
- Supports dynamic data masking
Cons:
- Limited customization options
- Potential learning curve for new users
Mage Data is a data masking solution tailored for businesses that need dynamic data protection. It serves industries that handle sensitive information and require real-time data masking capabilities to secure data without altering its usability.
Why I picked Mage Data: It excels in dynamic data masking, allowing your team to mask data in real-time as it's accessed. Mage Data provides flexible masking policies that adapt to different data scenarios. Its real-time processing ensures that data remains protected without interrupting workflows. This approach makes it suitable for environments where data access is frequent and needs to be secure.
Standout features & integrations:
Features include dynamic data masking, which lets you protect data in real-time without altering its structure. The tool offers flexible masking policies that can be tailored to different data types and scenarios. Additionally, Mage Data supports real-time processing, ensuring that data security doesn't disrupt your team's operations.
Integrations include Oracle, Microsoft SQL Server, SAP, IBM Db2, PostgreSQL, MySQL, Teradata, Amazon Redshift, Google BigQuery, and Snowflake.
Pros and cons
Pros:
- Supports various data scenarios
- Real-time data masking capabilities
- Flexible masking policies
Cons:
- Requires technical expertise
- Initial setup complexity
Baffle is a data protection solution designed for businesses that require real-time data protection and encryption. It primarily serves financial institutions, healthcare providers, and other industries handling sensitive data, performing key functions like data encryption and masking.
Why I picked Baffle: It offers real-time data protection, ensuring your data is always secure during processing. Baffle employs encryption techniques that don't require decrypting data, providing an extra layer of security. It supports both on-premises and cloud environments, making it versatile for various IT infrastructures. Its ability to protect data without significant performance impact is ideal for businesses with high data throughput.
Standout features & integrations:
Features include dynamic data masking, which allows your team to mask data in transit. Baffle also provides format-preserving encryption, maintaining data usability while ensuring security. Its support for multi-cloud environments enhances flexibility for your data management needs.
Integrations include Amazon Web Services, Microsoft Azure, Google Cloud Platform, Snowflake, Databricks, Oracle, MongoDB, and IBM.
Pros and cons
Pros:
- Supports multi-cloud environments
- No need for data decryption
- Real-time data protection
Cons:
- Limited customization options
- Requires technical expertise
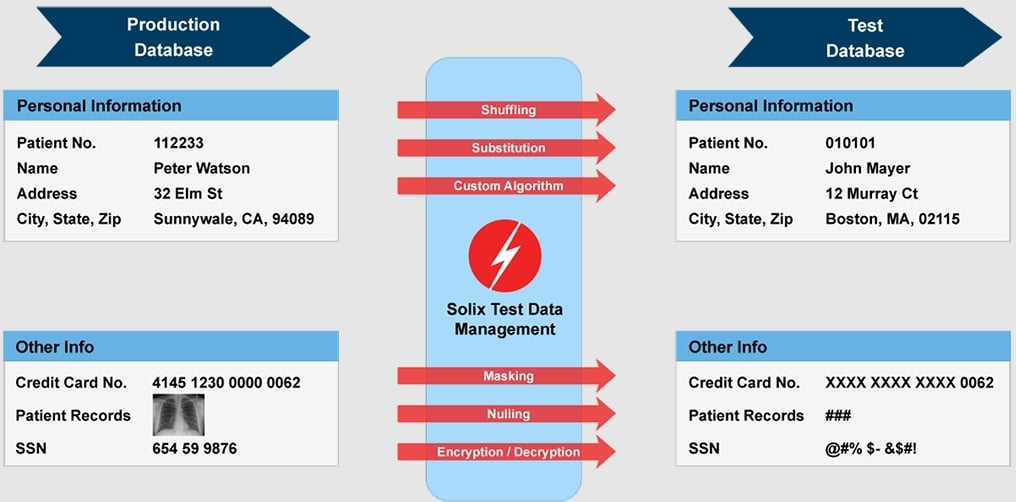
Solix Data Masking is a data protection solution targeting enterprise users who need to safeguard sensitive information and comply with privacy regulations. It performs key functions like data masking, sensitive data discovery, and supports various data environments.
Why I picked Solix Data Masking: It excels in providing advanced data masking techniques, crucial for enterprises handling large volumes of sensitive data. Solix Data Masking offers comprehensive sensitive data discovery tools, ensuring you identify all critical data across your systems. It supports multiple data environments, enhancing versatility for your team. Its compatibility with platforms like IBM and SAP makes it ideal for complex enterprise setups.
Standout features & integrations:
Features include advanced data masking techniques that help protect sensitive information effectively. Solix's sensitive data discovery tools ensure your team identifies all critical data. Additionally, it supports various data environments, providing flexibility in managing diverse datasets.
Integrations include IBM, SAP, Oracle, and Microsoft SQL.
Pros and cons
Pros:
- Compatible with major platforms
- Advanced data discovery tools
- Supports multiple data environments
Cons:
- Complex implementation process
- Lack of user-friendly interface
Comforte is a data security solution designed for enterprises that require scalable data protection. It primarily serves large organizations handling sensitive information, focusing on data masking and encryption services to secure data across various environments.
Why I picked Comforte: It offers scalable solutions that grow with your organization's data protection needs. Comforte provides data masking and tokenization features that help secure sensitive information effectively. Its ability to handle large data volumes makes it suitable for enterprises with growing data demands. The tool's focus on scalability ensures your team can manage data protection efficiently as your business expands.
Standout features & integrations:
Features include data masking and tokenization, which allow your team to protect sensitive information without altering its usability. Comforte supports large data volumes, ensuring scalability for growing businesses. Additionally, its encryption capabilities provide an extra layer of security for your data.
Integrations include SAP, Oracle, Microsoft SQL Server, IBM, Teradata, MongoDB, Amazon Web Services, Microsoft Azure, Google Cloud, and Snowflake.
Pros and cons
Pros:
- Effective data masking and tokenization
- Scalable data protection solutions
- Supports large data volumes
Cons:
- No transparent pricing information
- Potential learning curve for new users
Microsoft SQL Server is a relational database management system designed for businesses that require reliable database services. It mainly serves enterprises and IT professionals, focusing on data storage, retrieval, and management functions.
Why I picked Microsoft SQL Server: It's well-known for its smooth integration with various database environments, making it ideal for organizations with diverse data needs. SQL Server provides advanced data masking features that help secure sensitive information. It also offers strong support for transactional processing, ensuring data integrity. Its compatibility with other Microsoft products enhances its appeal for businesses already using Microsoft services.
Standout features & integrations:
Features include advanced data masking capabilities that allow your team to protect sensitive information efficiently. The tool supports transactional processing, ensuring data consistency and integrity. Additionally, its integration with Microsoft services offers a cohesive experience for users already in the Microsoft ecosystem.
Integrations include Microsoft Azure, Power BI, Excel, SharePoint, Dynamics 365, Visual Studio, Active Directory, GitHub, and Teams.
Pros and cons
Pros:
- Supports transactional processing
- Advanced data masking features
- Provides direct integration with SQL Server environments
Cons:
- Limited customization options
- No transparent pricing information
Clonetab is a data masking software designed for enterprises using Oracle e-Business Suite and SAP S/4HANA. It primarily aids in data obfuscation and database management, ensuring data security and compliance.
Why I picked Clonetab: It's known for its advanced data scrambling capabilities, which are crucial for industries handling sensitive information. Clonetab provides multiple scrambling algorithms that integrate with cloning processes. It features a Compliance Manager role, allowing non-DBAs to define rules and maintain data integrity. Its audit trails and monitoring tools enhance transparency, making it a suitable choice for complex data environments.
Standout features & integrations:
Features include database cloning and virtualization, allowing your team to efficiently manage test data environments. Clonetab's CT-ADS provides various data obfuscation algorithms to protect sensitive information. Additionally, it offers audit trails to monitor scrambling activities and ensure compliance.
Integrations include Oracle e-Business Suite and SAP S/4HANA.
Pros and cons
Pros:
- Compliance Manager for non-DBAs
- Advanced data scrambling algorithms
- Easy integration with cloning processes
Cons:
- Limited to Oracle and SAP systems
- No detailed user reviews available
Protegrity offers a robust data protection solution, with an emphasis on ensuring privacy while preserving the usability of data. For organizations needing to maintain operational efficiency in data-driven workflows while still prioritizing privacy, Protegrity offers a compelling option.
Why I Picked Protegrity:
Protegrity stands out due to its balanced approach toward data usability and privacy. Not every data masking solution manages to maintain the utility of data while ensuring privacy - and this is where Protegrity makes a difference.
For this list, I determined Protegrity as the best tool for maintaining data usability while ensuring privacy due to its advanced data de-identification methods, which ensure privacy without hampering data-driven operations.
Standout Features and Integrations:
Features include AI-powered data protection, automatic discovery of sensitive data, and robust de-identification methods such as tokenization, masking, and encryption.
Integrations include cloud platforms like AWS and Azure, databases like Oracle and SQL Server, and big data solutions like Hadoop.
Pros and cons
Pros:
- Broad range of integrations.
- Robust data de-identification methods.
- Offers AI-powered data protection.
Cons:
- Requires technical expertise to implement and maintain
- May be overkill for smaller organizations.
Skyflow is a data privacy vault that concentrates on assisting businesses to comply with GDPR and other stringent data regulations. By leveraging the principles of zero-trust data security and privacy by design, it provides a solid defense for sensitive data and helps organizations maintain regulatory compliance.
Why I Picked Skyflow:
I selected Skyflow for the list due to its specific focus on ensuring regulatory compliance, particularly GDPR. Its unique approach, encompassing privacy by design and zero-trust data security, distinguishes it from other tools. In my opinion, Skyflow is the best tool for businesses aiming to adhere to GDPR and other regulations because it's built to help organizations meet these specific challenges.
Standout Features and Integrations:
Features include data anonymization, encryption, and tokenization, as well as maintaining an immutable log of data usage. It also offers a Privacy API for developers, simplifying the process of building privacy into applications.
Integrations include AWS, Microsoft Azure, and Google Cloud.
Pros and cons
Pros:
- Good integration with existing systems and cloud platforms
- Offers Privacy API for developers
- Strong focus on GDPR and other regulatory compliance
Cons:
- The cost could escalate with the number of data records and API calls
- May require technical expertise to leverage the full benefits
Other Data Masking Software
Here are some additional data masking software options that didn’t make it onto my shortlist, but are still worth checking out:
- SecuPi
For GDPR compliance
- PrimeFactors
For encryption integration
- VGS platform
For data security as a service
- DataSunrise
For real-time database security
- AWS Dataguise DgSecure
For sensitive data discovery
- Oracle Data Safe
For cloud database security
- Delphix DevOps Data Platform
For devops data management
- Oracle Data Masking and Subsetting
For database subsetting
- IBM InfoSphere Optim Data Privacy
For enterprise data privacy
- Voltage Data Security
For encryption and tokenization
- Oracle Enterprise Manager
For enterprise database management
- Microsoft Azure SQL Database
For scalable cloud databases
- HushHush Data Masking
For custom data masking
- Satori Security Data Platform
For dynamic data masking
- Test Data Management (Legacy)
For legacy system support
- Broadcom Test Data Manager
For test data generation
- IRI FieldShield
For data field encryption
Data Masking Software Selection Criteria
When selecting the best data masking software to include in this list, I considered common buyer needs and pain points like data security and regulatory compliance. I also used the following framework to keep my evaluation structured and fair:
Core Functionality (25% of total score)
To be considered for inclusion in this list, each solution had to fulfill these common use cases:
- Mask sensitive data
- Support multiple data formats
- Comply with data privacy regulations
- Provide audit trails
- Enable role-based access control
Additional Standout Features (25% of total score)
To help further narrow down the competition, I also looked for unique features, such as:
- Real-time data masking
- Dynamic masking capabilities
- Integration with cloud platforms
- Customizable masking rules
- Data discovery and classification
Usability (10% of total score)
To get a sense of the usability of each system, I considered the following:
- Intuitive user interface
- Easy navigation
- Minimal learning curve
- Customizable dashboards
- Efficient workflow design
Onboarding (10% of total score)
To evaluate the onboarding experience for each platform, I considered the following:
- Availability of training videos
- Interactive product tours
- Access to templates and guides
- Responsive onboarding support
- Webinars and live training sessions
Customer Support (10% of total score)
To assess each software provider’s customer support services, I considered the following:
- Availability of 24/7 support
- Access to a dedicated support team
- Comprehensive help documentation
- Responsive live chat and email support
- Regular updates and maintenance
Value For Money (10% of total score)
To evaluate the value for money of each platform, I considered the following:
- Competitive pricing
- Flexible pricing plans
- Feature set relative to cost
- No hidden fees
- Satisfaction with ROI
Customer Reviews (10% of total score)
To get a sense of overall customer satisfaction, I considered the following when reading customer reviews:
- Overall satisfaction ratings
- Feedback on ease of use
- Comments on feature effectiveness
- Experiences with customer support
- Opinions on pricing and value
How to Choose Data Masking Software
It’s easy to get bogged down in long feature lists and complex pricing structures. To help you stay focused as you work through your unique software selection process, here’s a checklist of factors to keep in mind:
| Factor | What to Consider |
| Scalability | Can the software grow with your data needs? Consider how it handles increasing data volumes and if it supports your future growth plans. Look for solutions that offer flexible scaling options without significant performance degradation. |
| Integrations | Does the software integrate with your existing systems? Check compatibility with your databases, cloud services, and other IT infrastructure. Seamless integration can save time and reduce complexity during implementation and everyday use. |
| Customizability | How easily can you tailor the software to your specific requirements? Evaluate if it allows you to define masking rules, adapt workflows, and align with your business processes. Customizability ensures the tool meets your unique needs. |
| Ease of use | Is the software intuitive and user-friendly? Look for a solution that minimizes training time and allows your team to efficiently perform tasks. A simple interface and clear navigation are key to reducing the learning curve. |
| Implementation and onboarding | How smooth is the transition to the new software? Assess the availability of training resources, support during setup, and any potential disruptions. A well-supported onboarding process can make a significant difference in early adoption. |
| Cost | Does the pricing fit your budget? Compare the total cost of ownership, including any hidden fees or additional charges. Ensure that the pricing aligns with the value and features offered, and consider long-term financial commitments. |
| Security safeguards | How robust are the security measures? Verify the software’s ability to protect sensitive data through encryption, access controls, and compliance with industry standards. Strong security safeguards are essential to prevent data breaches and unauthorized access. |
| Compliance requirements | Does the software meet your regulatory obligations? Consider industry-specific compliance needs, such as GDPR or HIPAA. Ensure the tool provides audit trails and reporting features to help you maintain adherence to relevant regulations. |
What Is Data Masking Software?
Data masking software is a tool that protects sensitive information by obscuring it, making it unusable to unauthorized users while maintaining its format. These tools are generally used by IT professionals, data analysts, and compliance officers to enhance data security and meet regulatory requirements.
Masking, encryption, and access control capabilities help with safeguarding data, ensuring only authorized personnel can view sensitive information. Overall, these tools provide a secure way to manage data privacy without hindering business operations.
Features of Data Masking Software
When selecting data masking software, keep an eye out for the following key features:
- Dynamic data masking: Provides real-time protection by masking data as it's accessed, ensuring sensitive information remains secure without altering its usability.
- Role-based access control: Allows you to manage who can view or manipulate data, enhancing security by ensuring only authorized users have access.
- Data encryption: Protects data by converting it into a code, preventing unauthorized access and ensuring compliance with data privacy regulations.
- Audit trails: Tracks data access and manipulation activities, providing transparency and helping with compliance reporting.
- Integration capabilities: Ensures compatibility with existing databases and IT infrastructure, allowing for seamless data management across platforms.
- Customizable masking rules: Lets you tailor masking processes to fit specific organizational needs, ensuring flexibility in protecting different data types.
- Data discovery and classification: Identifies and categorizes sensitive information, helping you prioritize and focus on protecting the most critical data.
- Scalability: Supports growing data volumes, ensuring that the software can expand alongside your organization's needs without performance loss.
- User-friendly interface: Offers an intuitive and easy-to-navigate design, reducing the learning curve and helping teams work efficiently.
- Compliance support: Provides features that help meet industry-specific regulations, such as GDPR or HIPAA, ensuring your organization stays compliant.
Benefits of Data Masking Software
Implementing data masking software provides several benefits for your team and your business. Here are a few you can look forward to:
- Enhanced data security: Protects sensitive information by masking or encrypting it, reducing the risk of unauthorized access and data breaches.
- Regulatory compliance: Helps your organization meet industry standards like GDPR and HIPAA by ensuring data privacy and providing audit trails.
- Operational efficiency: Allows your team to work with realistic data without exposing sensitive information, improving workflow and decision-making.
- Risk mitigation: Minimizes the potential for data leaks by controlling access and visibility, safeguarding your company's reputation and assets.
- Scalability: Supports growing data demands, ensuring that your data protection measures can expand as your business grows.
- Customization: Offers flexibility in how data is masked and protected, allowing you to tailor solutions to fit your specific needs and processes.
Costs and Pricing of Data Masking Software
Selecting data masking software requires an understanding of the various pricing models and plans available. Costs vary based on features, team size, add-ons, and more. The table below summarizes common plans, their average prices, and typical features included in data masking software solutions:
Plan Comparison Table for Data Masking Software
| Plan Type | Average Price | Common Features |
| Free Plan | $0 | Basic data masking, limited support, and standard security. |
| Personal Plan | $5-$25/user/month | Customizable masking rules, data encryption, and email support. |
| Business Plan | $30-$75/user/month | Role-based access, integration capabilities, audit trails, and priority support. |
| Enterprise Plan | $80-$150/user/month | Advanced compliance tools, dynamic masking, scalability options, and dedicated account management. |
Data Masking Software: FAQs
Here are some answers to common questions about data masking software:
What is data masking disadvantages?
Data masking can slow down processes because it often runs as a batch job, taking time to complete, especially with large datasets. It can also permanently alter the original data, making it unsuitable for production databases. Consider these factors when deciding on static or dynamic masking.
Which data masking technique is most appropriate?
Data encryption is widely used and effective for data masking. It converts data into an unreadable format that requires a decryption key for access. This technique is particularly useful when sensitive data must be securely shared or stored, ensuring that only authorized users can access it.
What has to be considered during the implementation of data masking?
When implementing data masking, ensure that data integrity is preserved for analysis. Balance security needs with accessibility to avoid disrupting workflows. Consider the complexity of your environment and select tools that integrate well with your existing systems.
Can data masking be reversed?
Data masking can be reversible or irreversible depending on the method used. Reversible masking allows the original data to be restored under secure conditions, while irreversible masking permanently alters the data, making it unreadable without a specific key or process.
How does data masking support compliance?
Data masking helps organizations comply with regulations like GDPR and HIPAA by protecting sensitive information from unauthorized access. It provides a way to anonymize data, ensuring that personal information is not exposed, thus reducing the risk of data breaches and regulatory fines.
Is data masking suitable for all types of data?
Data masking is versatile and can be applied to various data types, including structured and unstructured data. However, it’s essential to assess your specific data needs and choose a masking technique that maintains data usability while protecting sensitive information.
What's Next?
Boost your SaaS growth and leadership skills.
Subscribe to our newsletter for the latest insights from CTOs and aspiring tech leaders.
We'll help you scale smarter and lead stronger with guides, resources, and strategies from top experts!