Best Cloud Security Tools Shortlist
Here’s my pick of the 10 best software from the 30 tools reviewed.
Finding the right cloud security tools can significantly streamline threat detection and boost compliance, whether protecting sensitive data, securing multi-cloud environments, or automating incident response.
I've independently tested and reviewed various solutions, focusing on what truly matters to you and your team. I believe in providing an unbiased, well-researched perspective to help you make informed decisions.
In this article, you'll discover my top picks for cloud security tools, each chosen for its unique benefits. Whether you're concerned about data protection or compliance, you'll find insights that address your specific needs.
Let's dive into the options and find the best fit for your organization.
Why Trust Our Software Reviews
Best Cloud Security Tools Summary
This comparison chart summarizes pricing details for my top cloud security tool selections to help you find the best one for your budget and business needs.
| Tool | Best For | Trial Info | Price | ||
|---|---|---|---|---|---|
| 1 | Best for securing global device fleets | Free trial + demo available | From $29/month | Website | |
| 2 | Best for managing cloud-based devices and applications | Free trial available | From $8/user/month (billed annually) | Website | |
| 3 | Best for unified SIEM with DLP and CASB | Free demo available | Pricing upon request | Website | |
| 4 | Best range of scanning services | 14-day free trial + demo available | From $99/month | Website | |
| 5 | Best for comprehensive cloud posture management | Free plan available + free demo | From $350/month | Website | |
| 6 | Best for insight-driven defense | Free trial available | From $10/user/month (billed annually) | Website | |
| 7 | Best for proactive threat detection | 30-day free trial + free demo available | From $338.50/year | Website | |
| 8 | Best for zero trust access control | Free plan available | From $5/user/month (billed annually) | Website | |
| 9 | Best for end-to-end identity security | Free demo available | Pricing upon request | Website | |
| 10 | Best for vulnerability management in hybrid environments | Free trial available | Pricing upon request | Website |
-

Docker
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.6 -

Pulumi
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.8 -

GitHub Actions
Visit Website
Best Cloud Security Tools Reviews
Below are my detailed summaries of the best cloud security tools that made it onto my shortlist. My reviews offer a detailed look at the key features, pros & cons, integrations, and ideal use cases of each tool to help you find the best one for you.
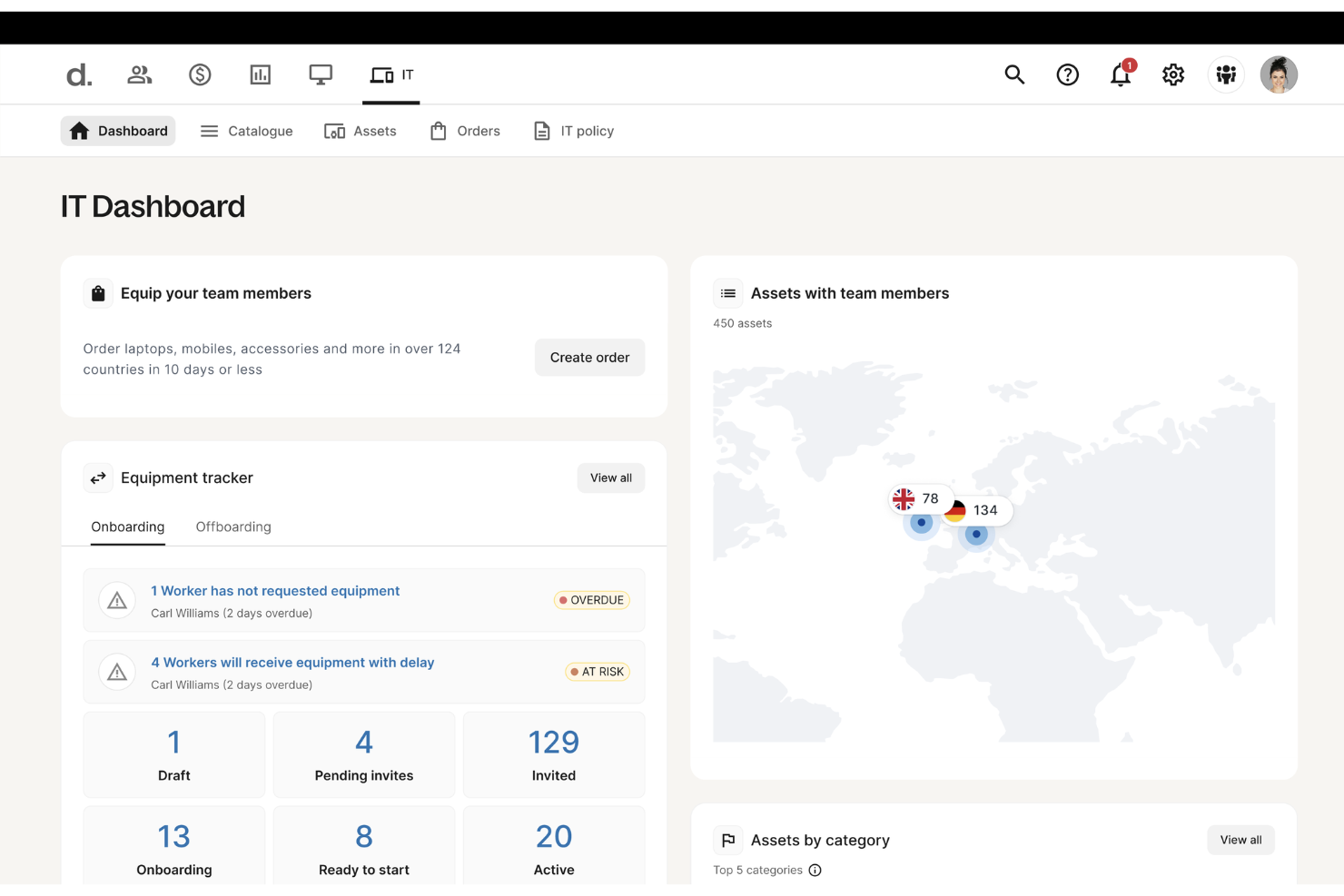
Deel offers a suite of cloud-based security tools designed to protect every device in your organization from cyber threats. Its endpoint protection platform safeguards laptops, tablets, and mobile devices across your global workforce.
Why I picked Deel: I picked Deel because it brings cloud security directly into the workforce management ecosystem, combining endpoint protection with device management and access control. Deel’s cloud-native system continuously detects and prevents malware, ransomware, and unauthorized access in real time—without needing heavy manual oversight. Its automated threat response isolates affected devices instantly, minimizing disruption and data exposure.
Deel Standout Features and Integrations:
Features include automated threat detection that adapts to evolving cyber risks in real time, ensuring every endpoint stays protected. The platform’s lightweight architecture enables instant containment of security threats without slowing down devices or workflows. Deel also offers cross-platform coverage, giving your IT team consistent protection and visibility across all operating systems and device types.
Integrations include BambooHR, Personio, NetSuite, Slack, Google Workspace, Zoom, SAP SuccessFactors, Xero, QuickBooks, Workday, Greenhouse, and Lever.
Pros and cons
Pros:
- Automated containment reduces manual work
- Protects all devices across locations
- Real-time threat detection and response
Cons:
- Lacks broader cloud security tools beyond endpoint management for devices
- Not a full enterprise security suite
New Product Updates from Deel
Introducing Deel AI Workforce
Deel has launched the AI Workforce, a set of specialized agents designed to handle repetitive HR, payroll, and compliance tasks with speed and accuracy. These AI agents don’t just assist—they execute tasks from start to finish. For more information, visit Deel's official site.
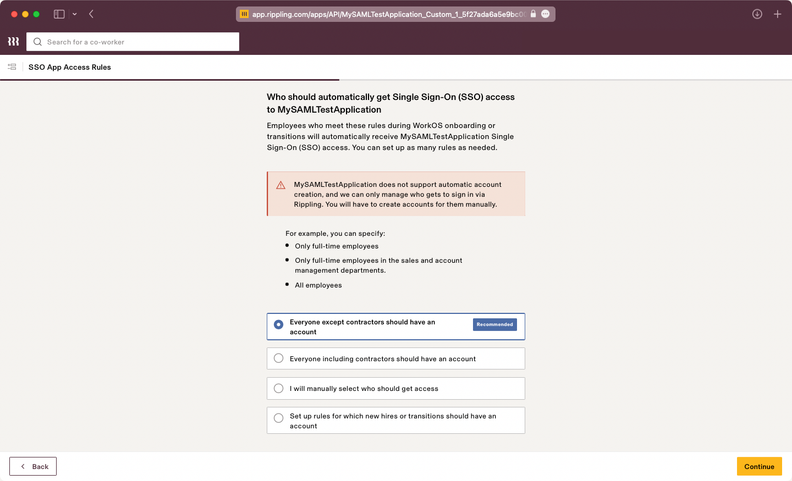
Rippling IT is an all-in-one platform designed to manage your company's IT infrastructure in the cloud. It lets you oversee your team’s devices, applications, and user access from a single location, automating much of the process.
Why I picked Rippling IT: Rippling IT works well as a cloud security tool because it centralizes identity and access management (IAM) for cloud-based assets. You can control which employees have access to what applications and data through role-based access control, and these permissions automatically update when employees change roles. Multi-factor authentication (MFA) is built-in, adding another layer of security for cloud apps. This feature ensures that access to sensitive cloud data and apps is only granted to authorized users, minimizing the risk of breaches.
Rippling IT Standout Features and Integrations:
Features include centralized identity and access management (IAM), allowing control over employee access to cloud-based applications and data. Its role-based access control ensures permissions are dynamically updated as employees change roles, reducing administrative overhead and enhancing security. Additionally, built-in multi-factor authentication (MFA) adds an extra layer of protection, ensuring that only authorized users can access sensitive resources.
Integrations include Slack, Google Workspace, Office 365, AWS, Zoom, Dropbox, and Salesforce.
Pros and cons
Pros:
- Remote wipe protects data on lost or stolen devices
- Multi-factor authentication improves cloud app security
- Simplifies managing cloud-based devices and access
Cons:
- Limited to devices and apps rather than more comprehensive cloud assets
- Complex setup for more granular security policies
New Product Updates from Rippling IT
Assign Identity Providers by Team with Rippling IT
Rippling IT now allows assigning specific identity providers like Okta and Entra ID to different teams, with Rippling’s SSO as a backup for instant rollbacks. More details at Rippling Blog.
ManageEngine Log360 is a comprehensive security information and event management (SIEM) solution that provides log management, threat detection, compliance reporting, and real-time security alerts. It aims to enhance visibility into an organization's network, improve security measures, and provide a user-friendly experience.
Why I picked ManageEngine Log360: I picked ManageEngine Log360 because of its ability to provide comprehensive security coverage for cloud environments. Its integration of SIEM capabilities with cloud access security broker (CASB) and data loss prevention (DLP) features ensures robust threat detection and response. Additionally, the software’s machine learning-based anomaly detection, coupled with real-time analytics, offers dynamic and proactive cloud security, making it an ideal choice for protecting cloud assets and data.
ManageEngine Log360 Standout Features and Integrations:
Features include unified log management and SIEM capabilities, enabling real-time threat detection and compliance reporting from a single console. Its integration with popular IT and security tools enhances visibility across hybrid IT environments, simplifying compliance with regulations like GDPR and HIPAA. Additionally, Log360’s automated log correlation and anomaly detection provide actionable insights to swiftly identify and mitigate potential security risks.
Integrations include Microsoft Active Directory, Office 365, Google Workspace, AWS, Azure, Salesforce, Box, ServiceNow, Jira, Slack, IBM QRadar, Splunk, SolarWinds, Palo Alto Networks, Fortinet, Cisco, and Sophos.
Pros and cons
Pros:
- Compliance with legal regulations
- Incident management console
- Holistic security visibility across on-premises, cloud, and hybrid networks
Cons:
- Logs can be hard to read and understand
- Complex to set up and configure
Intruder is a cloud security tool designed to help organizations manage vulnerabilities and protect their digital assets. It focuses on continuous vulnerability management and attack surface management, offering a comprehensive approach to identifying and addressing security weaknesses.
Why I picked Intruder: I picked Intruder because of its ability to perform various scanning services, including external, internal, cloud, web application, and API vulnerability scanning. These features allow you to monitor your organization's security posture in real-time, ensuring that critical vulnerabilities are prioritized and addressed promptly. Additionally, Intruder's platform offers exposure management by utilizing multiple scanning engines, which helps identify issues that might be overlooked by other tools.
Intruder Standout Features and Integrations:
Features include the ability to prioritize vulnerabilities based on their potential impact, helping you focus on the most pressing issues. Intruder also provides clear remediation guidance, making it easier for your team to address identified problems. Additionally, the platform offers comprehensive reporting capabilities, allowing you to track your security posture over time and demonstrate compliance with industry standards.
Integrations include AWS, GitLab, GitHub, Jira, Azure, Teams, Slack, Azure DevOps, Cloudflare, Google Cloud, Microsoft Sentinel, and Okta.
Pros and cons
Pros:
- Prioritization of issues helps focus on critical threats
- Offers detailed reports
- The platform proactively scans for newly disclosed vulnerabilities
Cons:
- Attack surface monitoring limited to Premium plan
- Some may find the customization options for scans limited
New Product Updates from Intruder
Intruder Partners With DomainTools for Enhanced Security
Intruder has partnered with DomainTools to integrate DNS data, enhancing security. This update helps security teams identify hidden subdomains and uncover Shadow IT risks more effectively. For more information, visit Intruder's official site.
Aikido Security is a comprehensive DevSecOps platform designed to provide full security coverage from code to cloud. It integrates multiple security scanning capabilities, including SAST, DAST, SCA, CSPM, IaC, and container scanning, to identify and manage high-risk vulnerabilities in source code, containers, and cloud environments.
Why I picked Aikido Security: I like its cloud posture management (CSPM), which detects cloud infrastructure risks across major cloud providers. This feature ensures that your cloud environment is continuously monitored for vulnerabilities, misconfigurations, and compliance issues, providing a robust defense against potential security breaches. Additionally, Aikido Security offers Infrastructure as Code (IaC) scanning, which scrutinizes Terraform, CloudFormation, and Kubernetes configurations for security risks.
Aikido Security Standout Features and Integrations:
Features include an innovative approach to detecting attack paths by visualizing potential security vulnerabilities in your cloud infrastructure, enabling preemptive remediation. Its risk prioritization offers actionable insights based on real-time context and potential impact to help teams focus on the most critical threats. Aikido Security integrates with CI/CD pipelines and popular DevOps tools, making it easy to incorporate security checks into development workflows without disrupting productivity.
Integrations include Amazon Web Services (AWS), Google Cloud, Microsoft Azure Cloud, Drata, Vanta, AWS Elastic Container Registry, Docker Hub, Jira, Asana, and GitHub.
Pros and cons
Pros:
- Provides actionable insights and recommendations
- Helps in compliance tracking and reporting
- User-friendly interface
Cons:
- Does not have endpoint security or intrusion detection capabilities
- Ignores vulnerabilities if no fix is available
New Product Updates from Aikido Security
Aikido Security Adds Aikido Attack, GCP Support, and Smarter SBOM
Aikido Security introduces Aikido Attack for AI-driven pentesting, expands support to GCP Organization, and adds VEX to SBOM exports for clearer, more accurate vulnerability insights. For more information, visit Aikido Security's official site.
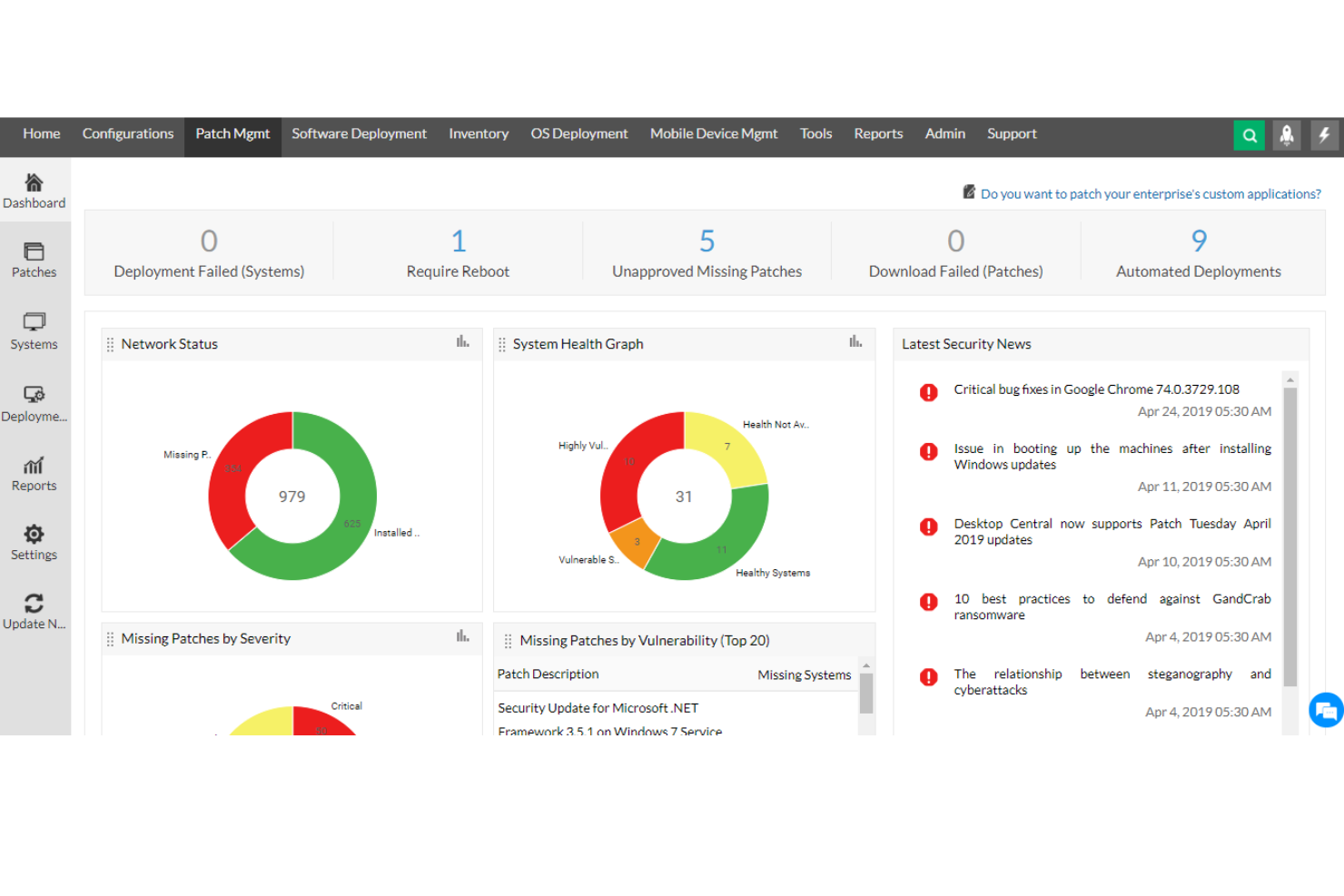
ManageEngine Desktop Central is a comprehensive tool that offers unified endpoint management and cloud security for all devices within an organization, ideal for IT professionals, managed service providers (MSPs), and enterprises of various sizes. Its goal is to assist in managing servers, laptops, desktops, smartphones, and tablets from a centralized location.
Why I picked ManageEngine Desktop Central: The software provides insight-driven defense through its extensive data collection and analytics features, which help IT administrators with actionable intelligence to proactively tackle security threats. A key feature that supports this approach is its real-time system monitoring and alerts. ManageEngine Desktop Central also offers end-to-end visibility and control and data hardening.
ManageEngine Desktop Central Standout Features and Integrations:
Features include endpoint management across devices and operating systems, ensuring seamless administration of desktops, servers, and mobile devices. Its integration with tools like ServiceDesk Plus enables efficient IT operations by connecting ticketing and device management workflows. Additionally, the software provides advanced automation for patch management and configuration enforcement, enhancing security and reducing manual effort.
Integrations include ServiceNow, Jira, Zoho Desk, Zendesk, Jira Service Desk, Microsoft SCCM, IBM BigFix, Slack, Microsoft Teams, Trello, Zapier, ManageEngine ServiceDesk Plus, Microsoft Intune, and more.
Pros and cons
Pros:
- Active directory management
- Patch management for software updates
- Remote desktop management capabilities
Cons:
- Users can feel overwhelmed with a lot of configurable features
- Some advanced features require additional research
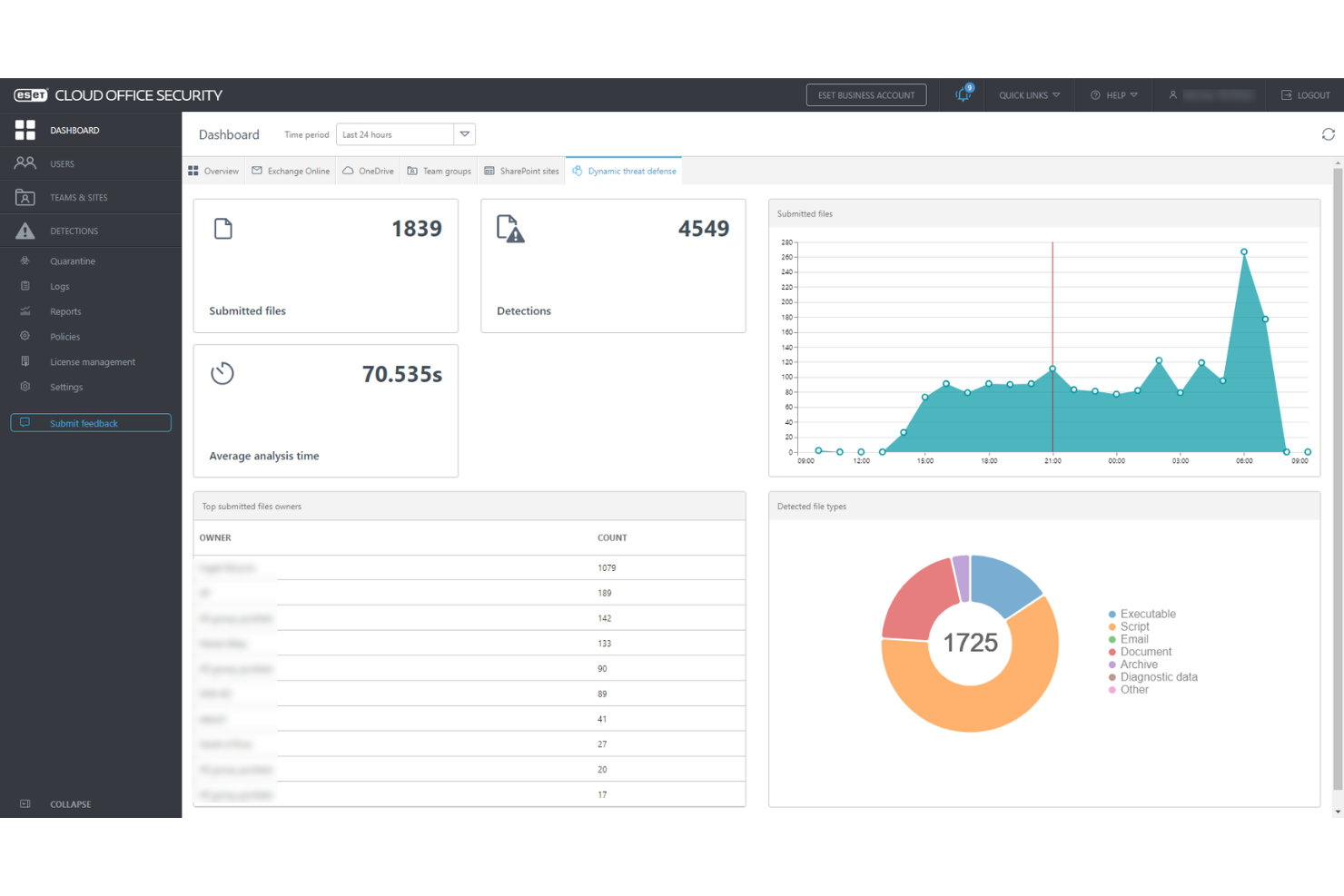
ESET PROTECT Complete is a comprehensive cloud-based security solution designed to provide multilayered protection for business endpoints, including computers, laptops, and mobile devices. The solution features cloud sandboxing technology to counteract zero-day threats and includes full disk encryption to enhance data protection.
Why I picked ESET PROTECT Complete: As a cloud security tool, ESET PROTECT offers robust protection specifically designed to address the unique security challenges of cloud computing. Additionally, the platform's cloud-based console enables administrators to manage security across distributed cloud environments seamlessly, enhancing visibility and control over all resources.
ESET PROTECT Complete Standout Features and Integrations:
Features include a unified security management platform with advanced threat detection and response capabilities, enabling IT teams to monitor endpoints, servers, and networks in real time. ESET’s multi-layered security approach includes endpoint protection, data encryption, and cloud sandboxing, ensuring comprehensive defense against known and zero-day threats. Its integration with cloud-native tools and streamlined deployment makes it particularly user-friendly for organizations seeking efficient, scalable cybersecurity solutions.
Integrations include ConnectWise Automate, Microsoft Windows Defender Antivirus, Microsoft Azure, Datto RMM, NinjaOne, Kaseya VSA, and ATERA.
Pros and cons
Pros:
- Comprehensive reporting tools for in-depth security insights
- Advanced threat detection and response capabilities
- Lightweight system footprint ensures minimal impact on performance
Cons:
- Requires technical knowledge for advanced feature utilization
- Pricing can be high for smaller organizations
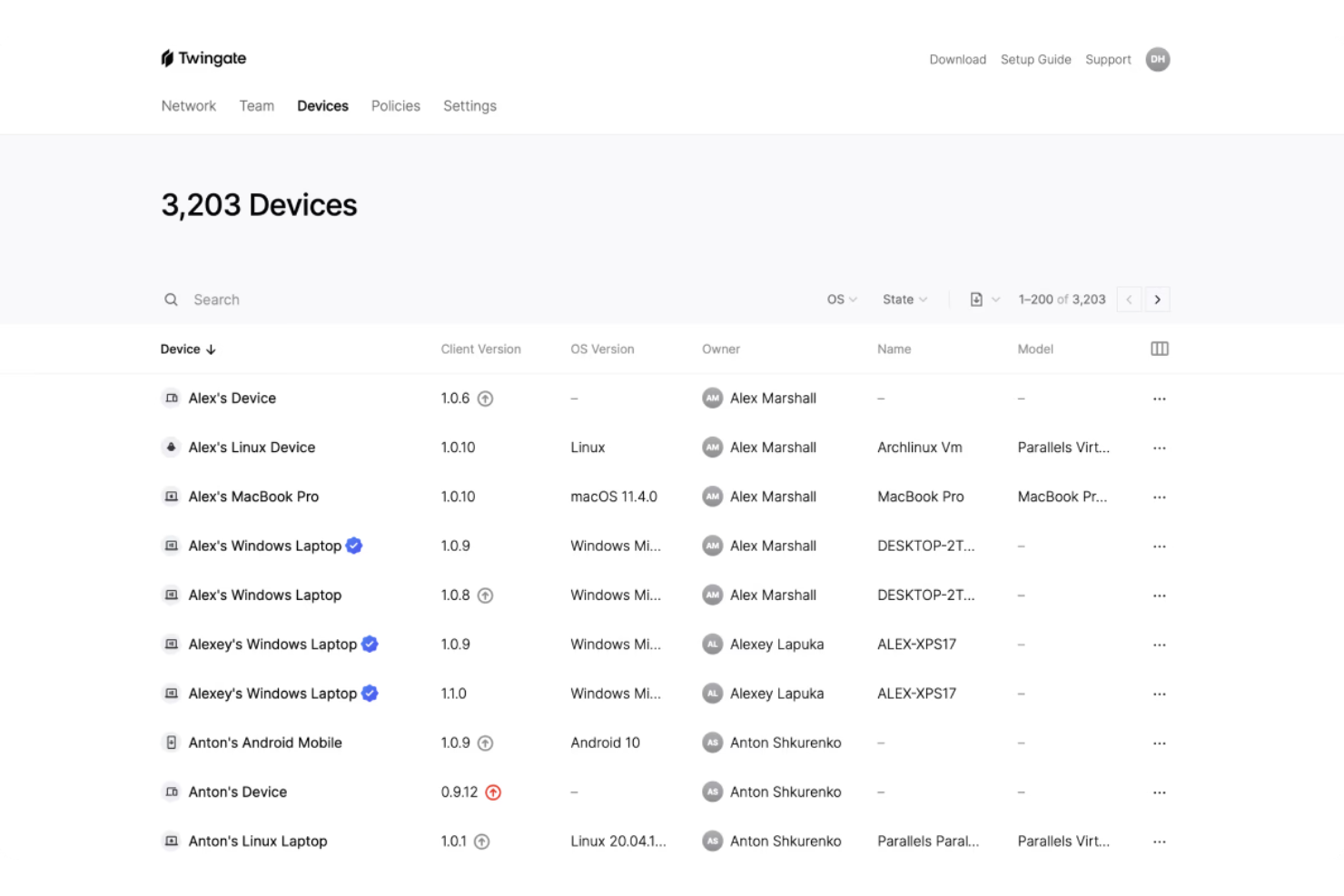
Twingate is a cloud security solution that replaces traditional VPNs with a Zero Trust Network Access (ZTNA) model. It helps secure remote access to private resources by enforcing least privilege access, device verification, and intelligent traffic controls.
Why I picked Twingate: I picked Twingate because of its strong zero trust implementation, which ensures that users only gain access to the resources they need. By authenticating both user identity and device status, Twingate helps prevent unauthorized lateral movement across networks. I also found its automated access controls valuable, as they can simplify the process of granting or revoking permissions in dynamic work environments. For distributed teams, these capabilities make it easier to maintain security without creating friction for end users.
Twingate standout features and integrations:
Features include intelligent device verification that works through integrations with services like CrowdStrike and Jamf, plus DNS filtering and content filtering to reduce exposure to malicious sites. Its orchestration layer can centralize security without requiring network reconfiguration, while integrations with identity providers like Azure AD and Okta make access management more efficient.
Integrations include CrowdStrike, Intune, Kandji, Jamf, Azure AD, Okta, Google Workspace, OneLogin, KeyCloak, JumpCloud, Virtual Machines, and Kubernetes.
Pros and cons
Pros:
- Centralized zero trust orchestration
- Strong device verification controls
- Flexible identity provider integrations
Cons:
- Limited advanced analytics
- Learning curve for setup
CyberArk provides comprehensive and expandable identity security solutions by enabling zero trust and enforcing the least privilege. Access management is a vital aspect of security posture, and CyberArk secures identities throughout the entire Identity Lifecycle, helping you protect what matters most from malicious attacks and unauthorized access.
Why I picked CyberArk: I picked CyberArk because it has intelligent privilege control that protects data in on-premises, cloud, and hybrid settings. Its real value comes from its security-focused identity access management, which reduces cyber risk and provides cloud users with simple and secure access to resources.
CyberArk Standout Features and Integrations:
Features include its advanced Privileged Access Manager, which secures credentials and monitors privileged sessions in real-time, offering protection against insider threats and cyberattacks. Its automation capabilities streamline credential management across hybrid and multi-cloud environments, ensuring scalability for large and evolving IT infrastructures. Additionally, CyberArk’s behavioral analytics provide proactive threat detection, automatically flagging and halting suspicious activities to mitigate risks before they escalate.
Integrations are pre-built for Ansible, Jenkins, Git, AWS, Google Cloud Platform, Okta, Microsoft Azure AD, and Ping.
Pros and cons
Pros:
- Extensive functionality with a wide range of optional integrations
- Streamlined processing of authorization requests
- Single admin portal with unified audits
Cons:
- High learning curve before you get comfortable with the system
- Upgrades aren't easy
Qualys is a cloud-based security solution that offers a unified risk-based view, compliance solutions, and critical security intelligence for hybrid environments. I have included it because of the platform's comprehensive vulnerability management capabilities.
Why I picked Qualys: I chose Qualys for its excellent visibility, continuous monitoring, and high accuracy, which helps reduce false positives in cloud security analysis. In my opinion, the tool's true value lies in its ability to detect vulnerabilities from across diverse cloud assets and present them in a single, unified dashboard. Their Vulnerability Management, Detection, and Response (VMDR) solution provides improved risk management and robust patching capabilities.
Qualys Standout Features and Integrations:
Features include a highly configurable platform that allows businesses to tailor their modules for specific governance, risk, and compliance needs. Its Audit Manager automates audit trails, tracks real-time performance, and generates detailed compliance reports to simplify regulatory adherence. The Document Manager ensures smooth collaboration with version control, making managing and maintaining critical documents across teams in regulated environments easier.
Integrations are available natively with AWS, Microsoft Azure, GCP, and other managed service providers like ServiceNow and JIRA. You can also add your integrations into your applications using the open XML APIs.
Pros and cons
Pros:
- Easy to deploy with flexible scanning methods and automated workflows
- Great visibility across cloud infrastructure with continuous monitoring of cloud assets
- Useful and speedy vulnerability assessment
Cons:
- Doesn't have a vulnerability triaging feature, resulting in false positives
- Scanners lack customization
Other Cloud Security Tools
Here are some additional cloud security tools options that didn’t make it onto my shortlist, but are still worth checking out:
- Zygon
For SaaS access security
- Cakewalk
For access management
- OPSWAT Security Score
For quick security checks
- Rubrik
For enterprise data backup and recovery
- Wiz
For medium to large enterprises
- Barracuda CloudGen Firewall
Firewall for cloud and hybrid networks
- CrowdStrike Falcon
For endpoint protection
- Pentera
For automated security validation
- Trend Micro
For extended detection and response (XDR)
- Orca Security
Agentless cloud security solution
- Zscaler
Zero trust solution
- Forcepoint ONE
For enterprises with a hybrid workforce
- Splunk
Unified security and observability platform
- Astra Pentest
For continuous scanning with expert support
- Stream Security
For real-time cloud exposure detection
- UnderDefense
For 24/7 threat detection & response
- CloudFlare
For secure network-as-a-service
- Perimeter 81
VPN solution for network infrastructures
- Cisco Cloudlock
Cloud access security broker solution
- Cyscale
For identity and access management
Selection Criteria for Cloud Security Tools
When selecting the best cloud security tools to include in this list, I considered common buyer needs and pain points like protecting sensitive data and ensuring compliance with regulations. I also used the following framework to keep my evaluation structured and fair:
Core Functionality (25% of total score)
To be considered for inclusion in this list, each solution had to fulfill these common use cases:
- Data protection
- Threat detection
- Access control
- Compliance management
- Security monitoring
Additional Standout Features (25% of total score)
To help further narrow down the competition, I also looked for unique features, such as:
- AI-driven threat analysis
- Multi-cloud support
- Real-time alerts
- Advanced encryption
- Customizable dashboards
Usability (10% of total score)
To get a sense of the usability of each system, I considered the following:
- Intuitive interface
- Easy navigation
- Minimal learning curve
- Customizable settings
- Responsive design
Onboarding (10% of total score)
To evaluate the onboarding experience for each platform, I considered the following:
- Availability of training videos
- Interactive product tours
- Comprehensive documentation
- Access to webinars
- Presence of chatbots
Customer Support (10% of total score)
To assess each software provider’s customer support services, I considered the following:
- 24/7 support availability
- Multiple support channels
- Quick response time
- Access to a knowledge base
- Personalized support options
Value For Money (10% of total score)
To evaluate the value for money of each platform, I considered the following:
- Competitive pricing
- Flexible subscription plans
- Free trial availability
- Comprehensive feature set
- Cost versus benefits
Customer Reviews (10% of total score)
To get a sense of overall customer satisfaction, I considered the following when reading customer reviews:
- User satisfaction ratings
- Commonly mentioned pros and cons
- Feedback on customer support
- Ease of integration feedback
- Overall reliability feedback
How to Choose Cloud Security Tools
It’s easy to get bogged down in long feature lists and complex pricing structures. To help you stay focused as you work through your unique software selection process, here’s a checklist of factors to keep in mind:
| Factor | What to Consider |
|---|---|
| Scalability | Can the tool grow with your team and data needs? Look for options that support expanding workloads and users without a major cost increase. |
| Integrations | Does it work with your existing systems? Check for compatibility with your current software stack to avoid disruptions and ensure smooth operations. |
| Customizability | Can you tailor the tool to fit your workflows? Consider tools that offer flexibility to adjust settings and features to meet your specific needs. |
| Ease of use | Is the tool user-friendly for your team? Test the interface for intuitive navigation to ensure quick adoption by all team members. |
| Implementation and onboarding | What’s needed to get started? Look for resources like tutorials and support to ease the transition and reduce downtime during setup. |
| Cost | Does the pricing fit your budget? Compare subscription plans, hidden fees, and long-term value to ensure affordability without sacrificing key features. |
| Security safeguards | Are there strong security measures in place? Prioritize tools with encryption, access controls, and regular updates to protect your data. |
What Are Cloud Security Tools?
Cloud security tools are solutions designed to protect cloud-based data and applications from threats and unauthorized access. IT professionals, cybersecurity experts, and compliance officers typically use these tools to safeguard sensitive information and maintain regulatory compliance.
You can deploy cloud cybersecurity tools and cloud directory services across a variety of cloud-based network configurations, such as hybrid, private, and multi-cloud networks. Without them, your data and cloud assets are more vulnerable to unauthorized access and data breaches.
Data protection, threat detection, and access control features help secure environments, ensure compliance, and manage risks. Overall, these tools provide essential security and peace of mind in cloud environments.
Features
When selecting cloud security tools, keep an eye out for the following key features:
- Data protection: Safeguards sensitive information from unauthorized access and breaches, ensuring data integrity.
- Threat detection: Identifies and alerts users to potential security threats in real-time, including those flagged by integrated dark web monitoring tools.
- Access control: Manages who can access specific data and applications, reducing the risk of insider threats.
- Compliance management: Helps organizations adhere to industry regulations and standards, avoiding legal penalties.
- Security monitoring: Continuously monitors cloud environments for suspicious activities, maintaining security posture.
- AI-driven threat analysis: Uses artificial intelligence to predict and analyze potential threats, enhancing protection.
- Multi-cloud support: Provides security across multiple cloud platforms, offering flexibility and scalability.
- Advanced encryption: Protects data with strong encryption methods, ensuring confidentiality and security.
- Real-time alerts: Notifies users immediately about security incidents, enabling swift action to mitigate risks.
- Customizable dashboards: Allows users to tailor their view of security metrics, improving monitoring and decision-making.
Benefits
Implementing cloud security tools provides several benefits for your team and your business. Here are a few you can look forward to:
- Improved data security: Protects sensitive information from breaches with features like data protection and advanced encryption.
- Regulatory compliance: Helps your business stay aligned with industry regulations through compliance management and integrations with cloud governance tools.
- Reduced risk of threats: Identifies and mitigates potential security threats quickly with threat detection and real-time alerts.
- Enhanced access control: Limits unauthorized access with access control features, protecting your data from internal threats.
- Scalability and flexibility: Supports business growth and changes with multi-cloud support, adapting to your evolving needs.
- Quick response to incidents: Enables fast action during security incidents through real-time alerts and monitoring.
- Informed decision-making: Customizable dashboards provide clear insights into security metrics, aiding in strategic planning.
Costs & Pricing
Selecting cloud security tools requires an understanding of the various pricing models and plans available. Costs vary based on features, team size, add-ons, and more. The table below summarizes common plans, their average prices, and typical features included in cloud security tools solutions:
Plan Comparison Table for Cloud Security Tools
| Plan Type | Average Price | Common Features |
|---|---|---|
| Free Plan | $0 | Basic threat detection, limited access control, and entry-level data protection. |
| Personal Plan | $5-$25/user/month | Enhanced data protection, real-time alerts, and basic compliance management. |
| Business Plan | $30-$60/user/month | Advanced threat detection, multi-cloud support, and customizable dashboards. |
| Enterprise Plan | $70-$150/user/month | Comprehensive compliance tools, AI-driven threat analysis, and full access control. |
Cloud Security Tools FAQs
Here are some answers to common questions about cloud security tools:
Do cloud security tools require ongoing maintenance?
Yes, they often need updates, policy tuning, and integration upkeep. Some platforms offer automated updates or managed services to reduce manual work. The maintenance workload depends on the deployment model and complexity of the setup.
Can cloud security tools integrate with existing systems?
Yes, many cloud security tools offer integrations with existing IT systems and software. This ensures a smooth workflow and data synchronization. Check for compatibility with your current systems to maximize efficiency and avoid disruptions.
What types of cloud environments do these tools support?
Most tools are designed to work across public, private, and hybrid cloud environments. Some are optimized for specific providers like AWS, Azure, or Google Cloud. Compatibility can depend on how the tool is deployed and configured.
How do cloud security tools detect threats?
They typically rely on automated systems that analyze logs, network activity, and access patterns. Detection methods can include rule-based engines, machine learning models, or behavioral analysis. The detection logic varies between platforms based on their architecture.
Are cloud security tools platform-specific or cross-platform?
Some are built specifically for one cloud provider, while others support multiple platforms. Cross-platform tools often include centralized dashboards for unified visibility. Deployment requirements and integration depth will differ by tool.
What are the 4 C's of cloud security?
The four C’s of cloud-native security are Cloud, Cluster, Code, and Container. They represent different layers of security needed to protect cloud-native applications. Consider how each layer interacts and supports your cloud environment’s overall security strategy.
How do cloud security tools help with compliance?
Cloud security tools assist with compliance by providing features like audit logs, data encryption, and access controls. They help ensure your organization meets industry regulations. Look for tools that align with your specific compliance needs to avoid potential penalties.
What’s Next
If you're researching cloud security tools, connect with a SoftwareSelect advisor for free recommendations.
Fill out a form and have a quick chat where they get into the specifics of your needs. Get a shortlist of software to review. They'll support you through the entire buying process, including price negotiations.