The field of cybersecurity is expanding with the development of innovative tools and technologies to manage and mitigate the range of threats and challenges businesses face today. Two prominent concepts are SOAR (Security Orchestration, Automation, and Response) and SIEM (Security Information and Event Management). Both offer separate but intertwined capabilities designed to increase the efficiency and effectiveness of cybersecurity operations.
SIEM tools can keep your IT infrastructure secure by monitoring and detecting security threats. SOAR takes a more proactive approach. It integrates with various security tools to collect data and allows automated responses to low-level threats. SOAR platforms are designed to streamline and fortify your response to such threats.
The debate between SOAR and SIEM is often drawn, but understanding when and how to utilize them can significantly enhance a company's security posture. In this article, you'll learn the key functionalities of SIEM and SOAR.
Understanding SOAR and SIEM: Definition, Features, and Benefits
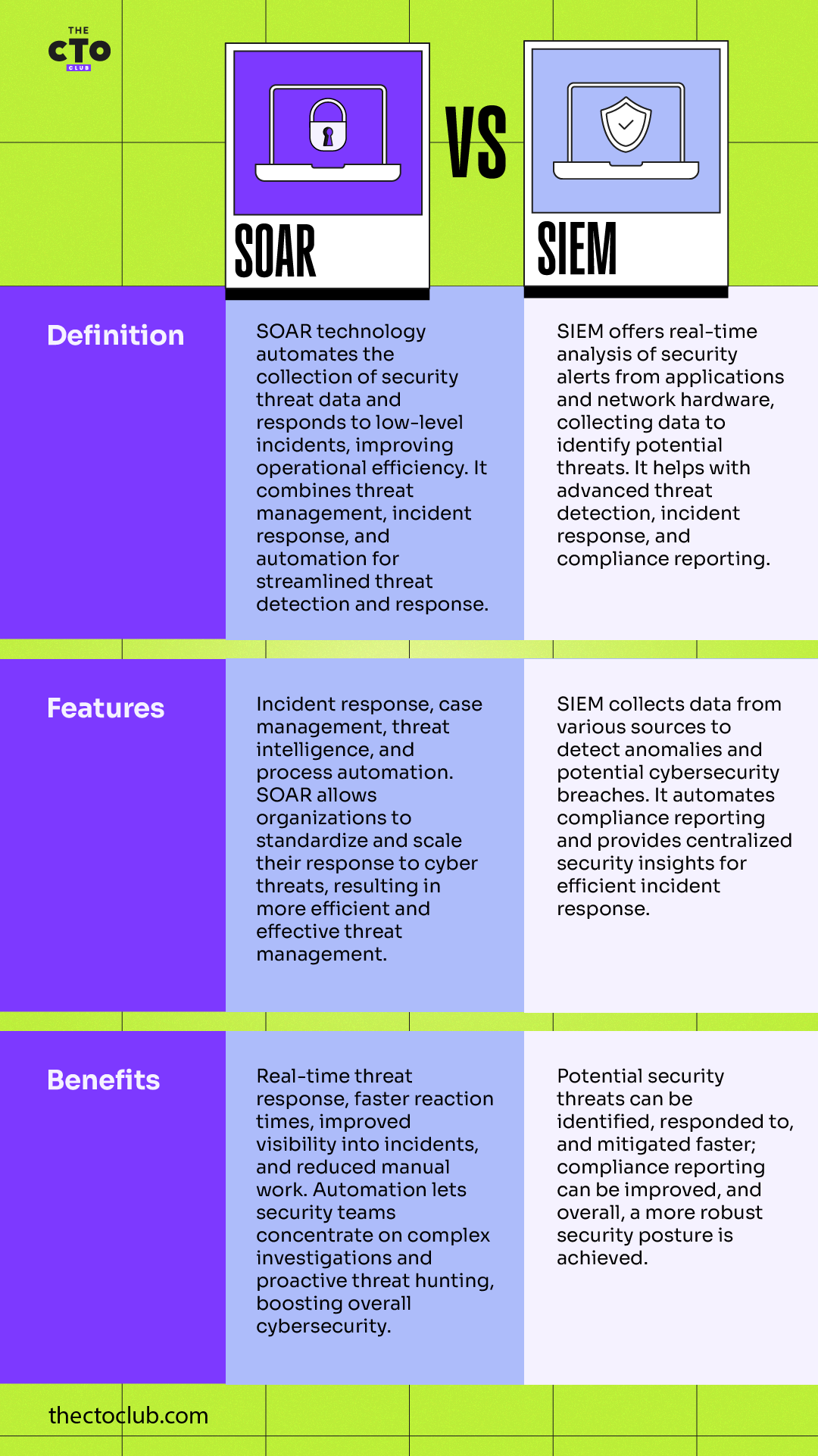
Key Differences
Even though SOAR and SIEM tools seem similar, there are some key differences. SIEM tools focus predominantly on data logging, correlation, and conducting event analysis to identify abnormal and suspicious activities. They highlight the specified events or anomalies but do not take any actions beyond this.
On the other hand, SOAR tools centralize threat intelligence data and provide a comprehensive view of the security environment. They go a step further than SIEM solutions by offering automated response actions. These actions could range from sending notifications to the concerned personnel to take action, to actively isolating affected devices or blocking malicious IPs.
SIEM alone typically requires manual intervention for sorting identified alerts, which can be time-consuming and may cause delays in case of a major threat incident. With SOAR, you can minimize human efforts by proactively automating these processes.
SOAR tools can dramatically decrease response times by triggering specific workflows in response to identified threats, improving security efficiency and efficacy. While SOAR and SIEM can function independently, integrating the two systems may offer a more seamless and effective threat detection and response strategy, facilitating a holistic cybersecurity strategy.
SOAR vs SIEM According to Business Needs
When choosing between SOAR and SIEM for your business needs, it is essential to identify your organization's unique requirements. SIEM solutions excel in data collection and provide invaluable insights into activity patterns, flagging notable events for investigation. If your firm's primary requirement is better visibility into its ecosystems, log correlation, and event alerts, a SIEM solution may be more suitable. It's particularly powerful in environments where compliance regulations necessitate detailed logging and event analysis.
However, SOAR is more oriented toward proactive threat hunting, incident response, and automation. This platform is known for its ability to integrate various cybersecurity tools, allowing for a unified coordination for threat response.
If your business places a premium on fast threat response, detecting and remediating lapses before they escalate, then SOAR might be a better option. The ability of SOAR to create a streamlined workflow, reduce response time, and alleviate the workload for your security team can provide considerable value and efficiency for your business.
-

ManageEngine Log360
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.2 -

Logmanager
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.9 -

SolarWinds Security Event Manager
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.3
Successful Implementations of SOAR and SIEM
One successful implementation of a SIEM system can be seen in this example from a leading healthcare service provider. The company struggled with massive amounts of user logs and alarms, which increased the risks of overlooking critical security events.
By implementing a SIEM solution, the volume of logs was significantly reduced, and important incidents were quickly identified. The system also provided a central location for analyzing and reporting, improving the organization's security posture.
Similarly, SOAR systems have proven essential. For instance, an international banking group was dealing with a high level of cyber threats and false alarms, and conventional methods of threat management were proving ineffective.
The implementation of a SOAR system allowed them to reduce the response time from hours to minutes. By automating repetitive tasks, they could focus their resources on complex threats.
The SOAR platform increased efficiency and accuracy and helped them deal with a fast-moving threat landscape. In both cases, the integration of SIEM and SOAR proved crucial in enhancing their security infrastructure.
The Future of Cybersecurity With SOAR and SIEM
As we venture further into the digital age, we're learning which tools can create a powerful cybersecurity defense system. The sophisticated cyber threats that are surfacing require an equally advanced response; hence, integrating SIEM's event detection capabilities with SOAR’s automated response mechanisms is the future of cybersecurity.
Moreover, future advancements in these technologies will likely be intertwined with cloud security management. As companies increasingly move their operations to the cloud, there will be a greater demand for cloud-compatible SIEM and SOAR solutions that offer real-time threat intelligence and automated responses. It is clear that the combination of SOAR and SIEM will play a pivotal role in defining next-generation cybersecurity standards.
For more on cybersecurity, subscribe to our newsletter for the latest insights!










