10 Best Vulnerability Scanning Software Shortlist
Here's my pick of the 10 best software from the 20 tools reviewed.
Our one-on-one guidance will help you find the perfect fit.
With so many different vulnerability scanning software available, figuring out which is right for you is tough. You know you want to proactively discover and address security gaps before they can be exploited but need to figure out which tool is best. I've got you! In this post I'll help make your choice easy, sharing my personal experiences using dozens of different vulnerability scanning tools with a variety of teams and projects, with my picks of the best vulnerability scanning software.
What Is Vulnerability Scanning Software?
Vulnerability scanning software is a tool used in cybersecurity to detect security weaknesses and vulnerabilities in computer systems, networks, and applications. It systematically scans these systems to identify potential vulnerabilities like outdated software, missing patches, and configuration flaws, providing a security assessment of the scanned environment.
The benefits and uses of vulnerability scanning software include enhancing an organization's cybersecurity by proactively identifying vulnerabilities that could be exploited by cyber attackers. It helps in prioritizing security risks and guides the remediation process to fix detected vulnerabilities. This software is essential for maintaining compliance with various security standards and regulations, ensuring the organization's digital infrastructure is safeguarded against potential threats. By regularly scanning systems, it supports a robust security posture and builds trust with customers and stakeholders.
-

Docker
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.6 -

Pulumi
Visit WebsiteThis is an aggregated rating for this tool including ratings from Crozdesk users and ratings from other sites.4.8 -

GitHub Actions
Visit Website
Overviews Of The 10 Best Vulnerability Scanning Software Solutions
Here’s a brief description of each vulnerability scanning system to showcase each tool’s best use case, some noteworthy features, and screenshots to give a snapshot of the user interface.
Aikido Security is a comprehensive DevSecOps platform designed to provide end-to-end security for code and cloud environments. It integrates various security scans and features, including vulnerability management, SBOM generation, cloud posture management, container image scanning, and dependency scanning.
One of the key strengths of Aikido Security is its all-in-one platform that integrates multiple scanning capabilities, including Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), Cloud Security Posture Management (CSPM), Software Composition Analysis (SCA), Infrastructure as Code (IaC) scanning, container scanning, and secrets detection.
This holistic approach ensures that all potential vulnerabilities across different layers of an application and its infrastructure are identified and addressed. By providing full coverage from code to cloud, Aikido Security helps organizations maintain a robust security posture. The software also supports compliance with standards such as SOC 2 and ISO 27001:2022 by automating the collection of evidence and generating detailed security reports.
Aikido integrates with Amazon Web Services (AWS), Google Cloud, MS Azure Cloud, DigitalOcean, Drata, Vanta, GitHub, GitLab Cloud, Bitbucket, Jira, Slack, Docker Hub, AWS Elastic Container Registry, GCP Artifact Registry, CircleCI, and Jenkins.
New Product Updates from Aikido Security
Aikido Security's July 2025 Update: NodeJS Safe-chain, Tuxcare Libraries, and IDE Enhancements
Aikido Security's update on July 22, 2025, introduced NodeJS Safe-chain, hardened libraries through Tuxcare, and IDE enhancements, including AutoFix in Visual Studio. More details can be found at Aikido Security Changelog.
Intruder is a cloud-based vulnerability scanner that aims to help businesses of all sizes discover security weaknesses in their online systems. The tool provides continuous monitoring of the network to identify vulnerabilities and reduce the attack surface.
Intruder provides a proactive security monitoring service, which includes regular scans to detect new threats as they emerge. Its network vulnerability scanning checks for over 10,000 vulnerabilities automatically. The tool then prioritizes the results to help focus on the issues that matter most and provide clear information on how to fix them.
Integrations are natively available with Slack, MS Teams, Jira, Github, and Gitlab. Other integrations can be accessed through Zapier and API.
Intruder costs from $196/month/application. A 14-day free trial is also available.
Invicti is a comprehensive web application and API security tool designed to help enterprises identify and fix vulnerabilities in their web assets. It offers automated discovery and security testing for web applications and APIs, integrating seamlessly into the software development lifecycle.
Invicti offers proof-based scanning technology. Unlike traditional scanners that merely identify potential vulnerabilities, Invicti goes a step further by safely exploiting these vulnerabilities in a read-only manner to confirm their existence. This can reduce false positives, saving development teams valuable time that would otherwise be spent on manual verification.
The software's comprehensive scanning capabilities cover a wide range of vulnerabilities, including those in complex applications and server configurations. Integrations include MuleSoft Anypoint Exchange, Amazon API Gateway, Apigee API hub, Kubernetes, Azure Boards, Bitbucket, Bugzilla, FogBugz, DefectDojo, Freshservice, GitHub, GitLab, Jazz Team Server, and Jira.
Acunetix is a web application and API security scanner designed to automate security testing for organizations, providing a robust solution for identifying, testing, and addressing vulnerabilities in web applications and APIs.
One of the most notable features is its AcuSensor Technology, which combines black-box scanning techniques with feedback from sensors placed inside the source code. This hybrid approach allows for highly accurate scanning with a low false-positive rate, ensuring that developers can trust the results and focus on genuine vulnerabilities.
The software is designed to be user-friendly, with a Login Sequence Recorder that simplifies the testing of password-protected areas and DeepScan technology that can interpret SOAP, XML, AJAX, and JSON. These features make it easier for security teams to conduct comprehensive scans without extensive manual intervention.
Best for enterprise vulnerability mitigation
ManageEngine Vulnerability Manager Plus is a comprehensive tool designed for enterprise vulnerability management, offering features such as secure configuration deployment, compliance, automated patch deployment, and zero-day vulnerability mitigation. It goes beyond the capabilities of traditional vulnerability management tools, providing executive reports, antivirus audits, deployment policies, and role-based administration.
Its ability to automate vulnerability assessment, patch management, and compliance management from a single console makes it a standout choice for large organizations with complex security needs. ManageEngine Vulnerability Manager Plus distinguishes itself with its robust capabilities, including detailed insights and reports that streamline the vulnerability management process. Its all-in-one platform for managing network vulnerabilities and its prioritization-focused approach to identifying and addressing vulnerabilities make it an ideal choice for enterprises.
ManageEngine Vulnerability Manager Plus offers a comprehensive Vulnerability Assessment feature that identifies and prioritizes a wide array of vulnerabilities, considering factors like exploitability and severity. Its integrations include Active Directory, Azure AD, AWS, and G Suite, which facilitates the management and monitoring of vulnerabilities across different platforms and services. The software provides tools for vulnerability assessment, compliance, patch management, network device security configuration management, and zero-day vulnerability mitigation.
Best for identifying potential security weaknesses across an organization's network
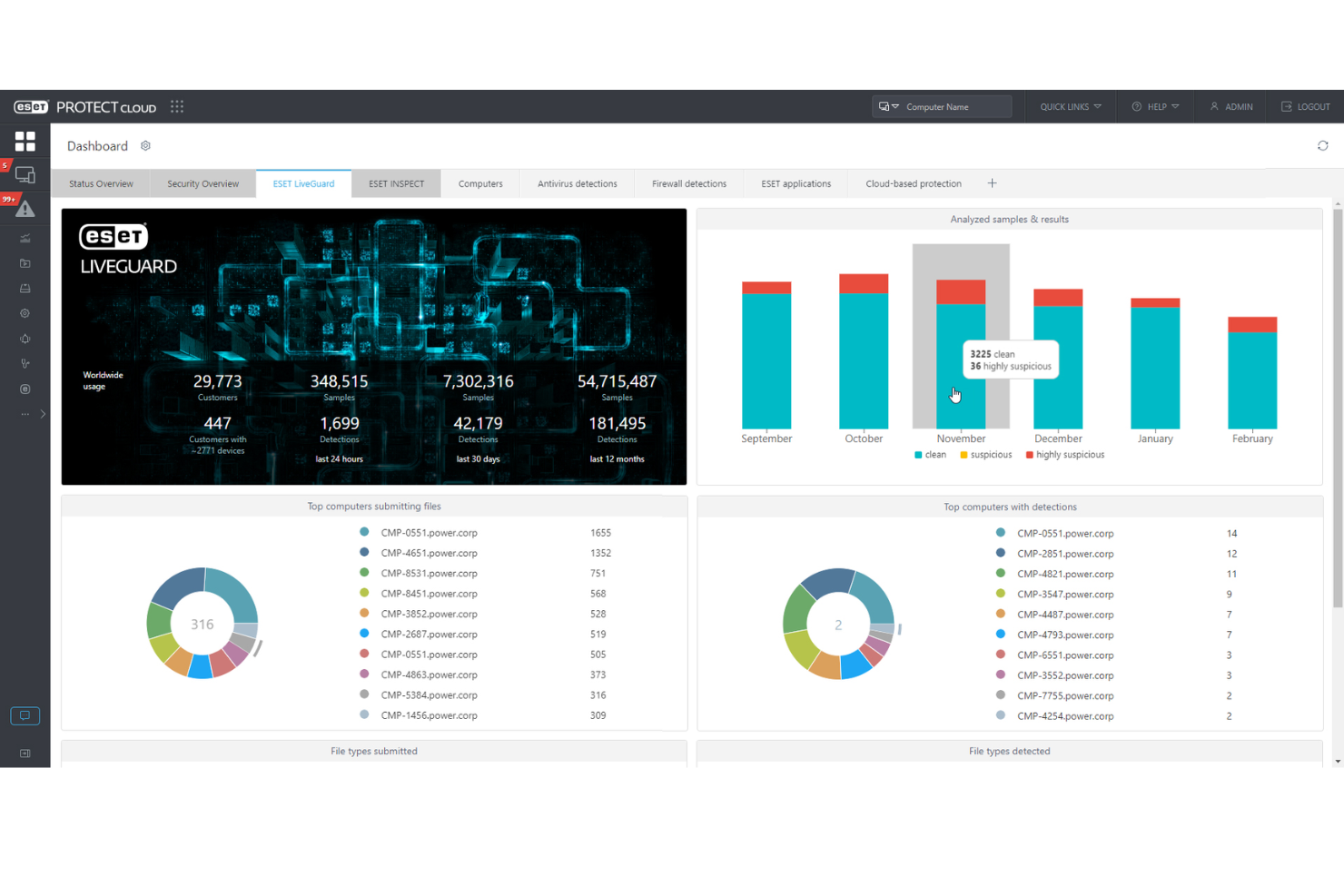
ESET PROTECT Complete provides a robust cybersecurity framework designed to protect businesses from a wide range of digital threats. This solution offers a suite of tools including endpoint protection, cloud sandboxing, and data encryption, aiming to deliver a secure, manageable, and comprehensive defense mechanism against malware, ransomware, and phishing attacks.
As a vulnerability scanning software, ESET PROTECT Complete excels in identifying and addressing potential security weaknesses across an organization's network. It provides detailed vulnerability reports, highlighting areas of concern and recommending actionable steps to mitigate risks. Its scanning engine is both thorough and efficient, ensuring minimal disruption to operational activities while maintaining a high level of security awareness.
ESET PROTECT Complete natively integrates with a variety of tools, including ESET Endpoint Security, ESET Endpoint Antivirus, ESET Security Management Center, ESET Dynamic Threat Defense, ESET Secure Authentication, ESET File Security for Microsoft Windows Server, ESET Mail Security for Microsoft Exchange Server, ESET Full Disk Encryption, Microsoft Active Directory, and SIEM tools.
ESET PROTECT Complete offers pricing upon request + a 30-day free trial.
Qualys
Information security solution that provides deep visibility into global assets
Qualys analyzes misconfigurations and threats across your global tech environment with six sigma accuracy. The system provides real-time alerts on zero-day vulnerabilities, compromised assets, and network irregularities. You can quarantine compromised assets with a single click, buying you more time to investigate and contain an attack.
To protect your IT environment, you need to know which assets are connected to your network. Qualys’ free Global AssetView application helps security teams accomplish this by automatically identifying all known and unknown assets on a network. You can quickly grab detailed information about each asset, including installed software, running services, and vendor lifecycle information. The application also helps with asset organization, enabling teams to categorize assets into product families with custom tagging.
Qualys supports native integrations with AWS, Azure, and Google Cloud.
Pricing is based on several factors, including the number of user licenses, Qualys Cloud Platform Apps, internal web applications, and IP addresses your team will be utilizing.
Best vulnerability scanning software to lower the rate of false positives
New Relic is an all-in-one observability platform that helps you monitor, troubleshoot, and tune your full stack. It allows companies to monitor and enhance their network’s security by identifying possible weaknesses that could be exploited by hackers. With New Relic, you can proactively scan their systems for potential vulnerabilities, getting a comprehensive overview of their security status, which can help in making informed decisions and creating effective cybersecurity strategies.
Moreover, New Relic offers real-time vulnerability scanning, which is exceptionally crucial in today's rapidly-evolving digital landscape where new threats emerge by the minute. With its continuous and automatic scanning, you can quickly detect and resolve any security issues. The platform's vulnerability triage feature gives you information based on criticality. Then, it displays a prioritized list of your vulnerable libraries as well as suggestions on which libraries to update to. This is perfect if you are not sure what to prioritize.
Lastly, New Relic's vulnerability scanning is known for its accuracy. The tool's comprehensive scanning capabilities dramatically reduce false positives, ensuring that the IT team's focus is not diverted by irrelevant alerts. The quality of its reporting also provides teams with all the crucial information needed to address vulnerabilities effectively. By providing a clear picture of the security landscape of a system, New Relic makes it easier.
New Relic integrates with over 600 applications within the categories of application monitoring, infrastructure, security, traffic simulation, logging, AWS, Azure, Google Cloud Services, open-source monitoring, machine learning ops, and Prometheus.
Intruder scans your IT environment to find a variety of vulnerabilities, including misconfigurations, missing security patches, and application bugs. The platform makes vulnerability management simple with threat prioritization and actionable remediation advice that IT and business stakeholders can understand.
IT teams can track how long it takes their organization to remediate vulnerabilities with Intruder’s Cyber Hygiene Score. Scores are determined by the time it takes to fix issues, which is benchmarked against targets set for critical, high, medium, and low-level vulnerabilities. You can quickly retrieve this information from your dashboard, which displays your performance over six months and the average time to fix each issue type.
Intruder users have access to multiple integrations, including AWS, Google Cloud, GitHub, and ServiceNow.
Pricing is based on the number of assets your organization needs to scan. A free 30-day trial is available for Intrudor Pro.
Tenable’s Cyber Exposure Platform helps businesses protect every corner of their web environment, including applications, data, and cloud infrastructure. Tenable is known for developing Nessus, a fully portable vulnerability scanner. Nessus offers comprehensive remote and local scanning capabilities while maintaining low operating costs.
IT teams can scan a broad range of network devices, including firewalls, routers, switches, printers, and storage to identify security vulnerabilities. Nessus also covers cloud applications and instances, such as Salesforce and AWS. Your team can detect various threats, including viruses, malware, backdoors, and web services linking to malicious content.
Prioritizing vulnerabilities is simple with Tenable’s Top 10 Reporting, which assigns a Vulnerability Priority Rating (VPR) to the most critical threats detected during a scan. VPR calculations are based on several criteria, including the vulnerability’s age, the exploit code’s maturity, and how many of your products are affected.
Tenable integrates with Splunk, ARCON, CyberArk, and many other security operations platforms.
Pricing for Nessus Pro starts at $3,390 for a one-year license. Organizations can try Nessus Pro free for seven days.
The Best Vulnerability Scanning Software Solutions Summary
| Tool | Best For | Trial Info | Price | ||
|---|---|---|---|---|---|
| 1 | Best for comprehensive code-to-cloud security | Free plan available + free demo | From $350/month | Website | |
| 2 | Best for proactive vulnerability management | 14-day free trial + demo available | From $99/month | Website | |
| 3 | Best for proof-based vulnerability scanning | Free demo available | Pricing upon request | Website | |
| 4 | Best for hybrid scanning with AcuSensor Technology | Free demo available | Pricing upon request | Website | |
| 5 | Best for enterprise vulnerability mitigation | Free 30-day trial and demo available | $1,195 for 100 workstations and a single-user license | Website | |
| 6 | Best for identifying potential security weaknesses across an organization's network | 30-day free trial + free demo available | From $338.50/year | Website | |
| 7 | Information security solution that provides deep visibility into global assets | Free trial available | Pricing upon request | Website | |
| 8 | Best vulnerability scanning software to lower the rate of false positives | Free plan + demo available | Pricing upon request | Website | |
| 9 | Vulnerability scanner that tracks average remediation time | 14-day free trial | From $157/application/month | Website | |
| 10 | Automates threat prioritization based on in-depth threat analysis | 7-day free trial | From $4,390/year | Website |
Other Options
Here are a few more vulnerability scanning tools that didn’t make the top list.
- CyCognito
For attacker-perspective vulnerability check
- Imperva
Enterprise-grade cybersecurity solution that guards against complex DDoS attacks
- Microsoft Baseline Security Analyzer
Free Windows security scanner with built-in remediation guidance
- Probely
Web app and API vulnerability scanner that’s easily accessible to developers
- beSECURE
Leading provider of governance, risk, and managed security solutions
- Rapid7
Offers external threat intelligence solution with clear and dark web monitoring
- Cyberpion
EASM solution with multi-layer vulnerability assessment engine
- Burp Suite
Vulnerability scanning tool great for crawling JavaScript-heavy applications
- Astra Pentest
For continuous vulnerability scanning & pentesting for 9300+ test cases
- Frontline Vulnerability Manager
SaaS vulnerability management solution for network systems and software
Comparison Criteria
The criteria below will help you decide which vulnerability scanning software tool is best for your business.
- User Interface (UI): A simple, user-friendly interface helps security analysts configure a vulnerability scan quickly and accurately.
- Usability: Good usability makes vulnerability scanning tools accessible to security experts and developers. Increased access enables software teams to implement security testing earlier in the development lifecycle.
- Integrations: The best vulnerability scanners offer a variety of plug-ins and integrations that easily connect with your existing SIEM and CI/CD tools.
- Value for $: The cost of your scanning tool should match the value it brings to your security efforts.
Vulnerability Scanning Tools: Key Features
These key features ensure your vulnerability scanning tool provides the best protection against threats.
- Asset Discovery: To protect your IT environment, you must know which assets are connected to the network. The top scanning tools can detect known and unknown assets that pose a high risk to your organization.
- Threat Intelligence: There are countless cyber threats across the clear, deep, and dark web. Select a scanning tool that provides the latest threat research you need to mitigate attacks.
- Automation: You can send secure products to market faster with scanning tools that automate your security team’s pre- and post-scan operations.
- Threat Prioritization: Your scanning software should help you triage threats, enabling you to quickly contain security issues that pose the highest risk to your business.
What do you think about this list?
Check out other software testing tools to help your team build more secure products. Sign up for our newsletter for the latest insights from top thinkers in the QA industry.
Related List of Tools: BEST SQL EDITORS & HOW TO CHOOSE THE RIGHT ONE