With all the different ways hackers can attack your company's networks and systems, you might be wondering which security measures are best in preventing it? Between vulnerability assessments and penetration testing, you can save precious time from fixing problems later down the road.
Firstly, you need to understand the difference between both as these terms are interrelated, and sometimes you pay for penetration testing services and receive a hundred-page “penetration testing” report outlining flaws found by a vulnerability scanning tool.
Many companies conduct penetration testing that turns out to be vulnerability assessments, therefore the problem is rather common. In this article, I will explain the major differences between these two types of security tests: Penetration Test (PT) and Vulnerability Scanning (VS).
- Vulnerability Scanning
- Penetration Testing
- Key Differences Between Vulnerability Scanning And Penetration Testing
- Why Should You Perform Vulnerability Scans And Penetration Tests?
Related Read: 4 STEPS TO RUNNING A SUCCESSFUL NETWORK PENETRATION TEST
Vulnerability Scanning
Vulnerabilities are like little hurdles that you need to jump over in order for your company's technology infrastructure (firewalls, web applications, etc.). These scans can help identify potential problems with your network traffic and web application security, as well as reveal any flaws that might be exploited by hackers looking for easy targets. A typical assessment will analyze your firewall, web applications, servers as well other devices linked into company technology infrastructure such that it can detect any potential flaws or problems.
The findings of potential vulnerabilities are included in the report. Since the results in a vulnerability assessment report are not accompanied by an effort to exploit weaknesses, some of them may be false positives.
A comprehensive security assessment should include the title and severity (high/medium/low) for each potential vulnerability found. It is important to make sure that you understand which ones are critical before wasting time fixing other less pressing issues because confusion will only lead to more problems down this path!
A good way to organize your security findings is by severity. The most serious vulnerabilities will be reported as "high" in order of how dangerous they are, followed closely with medium-level problems labeled either 'medium' or lower—this makes it easier for you to know what needs fixing first when analyzing the report.
Penetration Testing
Penetration testers are hunters who use their skills to find vulnerabilities in order to secure information. The objective of a penetration test is to discover vulnerabilities and attempt to exploit them and gain access to the system. Penetration tests are used to verify the authenticity of discovered vulnerabilities and may include theoretical discoveries of unexploitable vulnerabilities according to PCI DSS.
Pentesters do this by trying out possible attacks on systems, which can be used for hacking on purpose or just general research. If they successfully penetrate a system with an exploit passed off as legitimate then it will appear within your penetration test report alongside other testing results like discovered exploits and vulnerabilities.
The penetration testing process is an important part of assessing the likelihood that a cyber attack could be exploited in the real world. The tester uses their knowledge and skills to replicate what they think would happen if someone were trying to log into your network with malicious intent, making it possible for them to see how easy or difficult this feat might actually prove against different types of software/hardware combinations.
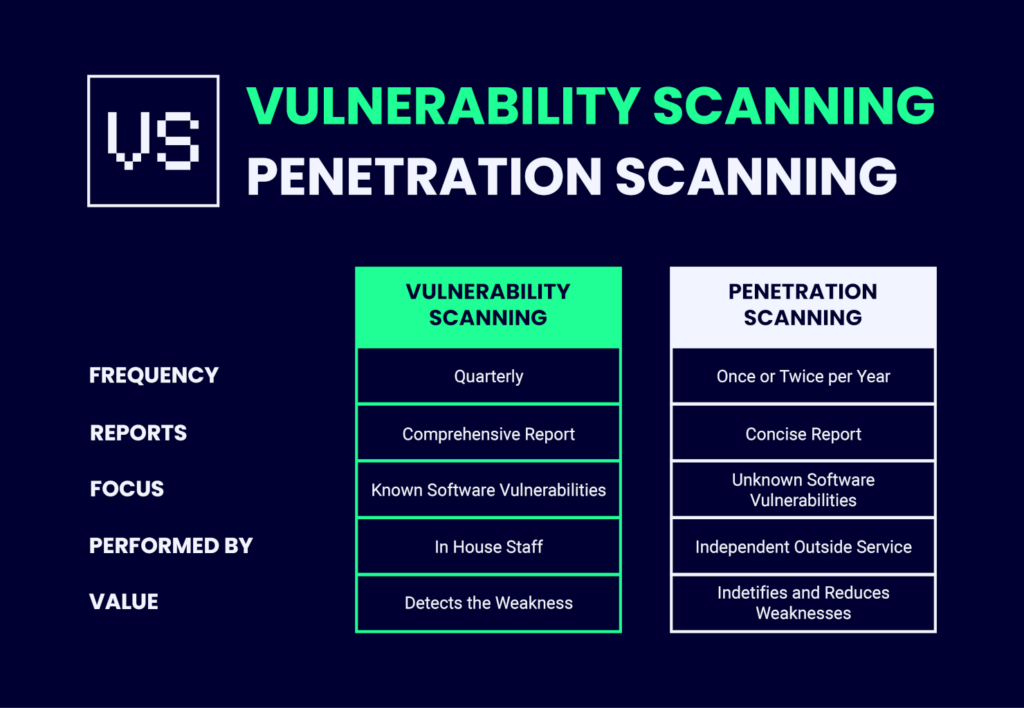
Key Differences Between Vulnerability Scanning And Penetration Testing
Penetration testing vs. vulnerability scanning—how are they actually different?
Scope
The scope of vulnerability coverage is what differentiates them from penetration testing. While a typical pentest will look at only one aspect (in-depth) in order to find vulnerabilities, an assessment typically covers many areas, such as identifying potential threats or risk factors that could lead to system failure if not properly mitigated—this includes understanding how your network works so you know where advertising any modifications made on top of standard security best practices.
Penetration testing is the perfect choice for clients who want to make sure their network security risks haven't been broken, but don’t have time or money on doing thorough tests. These experts will take an "underneath" approach and test if vulnerabilities exist in the order of how deep they go—starting at a surface level all the way down through core servers. It's an approach where depth is more important than breadth because if there are too many holes, it will take longer to fix in the long run.
Automation Level
Automation is a great way to make sure your organization's security stays up to date. Vulnerability assessments are often automated, which means they can be done more efficiently and with greater coverage of vulnerabilities than if you had humans doing it one at a time.
Penetration testing on the other hand combines both automated procedures as well as those requiring human intervention in order to explore problems further—this type of testing would not work with the inflexibility of robots!
Difficulty
The third difference is the difficulty of performing each test and the skill level required of the tester. Automated testing, which is extensively used in vulnerability security assessment, is low-skilled and may be conducted by employees of the security team. However, the company's security staff may discover certain vulnerabilities that they cannot fix and leave them out of the report. As a result, a vulnerability assessment performed by a third-party provider may be more useful to eliminate security weaknesses. Moreover, you will be aware of the security strategy employed by a third-party provider.
On the other hand, penetration testing takes a much higher degree of knowledge (because of the manual nature of the process) and is usually delegated to a penetration testing service company.
Why Should You Perform Vulnerability Scans And Penetration Tests?
Every day, new vulnerabilities are found and reported. While compliance regulations or basic security policies may need at least monthly patching, more regular vulnerability checks are suggested. By accurately depicting their security profile, enterprises may considerably profit.
Depending on the severity of the vulnerabilities, certain exploits may begin to spread rather fast. Zero-day exploits occur more often than we'd like. You expose yourself to possible dangers if you do not conduct vulnerability scans on a regular basis and follow up with a repair.
After establishing a scan frequency and resolving issues as they arise, you'll have a strong baseline of your security and compliance requirements.
Based on the findings of vulnerability scans, it's a good idea to implement penetration testing after a few scan cycles. The benefits of penetration tests for an organization arise from the fact that vulnerability scanners are restricted in their capacity to find specific vulnerabilities on each given asset. The actual danger posed by exploiting vulnerabilities may or may not be completely realized until a penetration test attempts them in a particular context.
Instead of focusing on a single vulnerability, the penetration tester may combine or chain many flaws for more significant changes. When chained with a list of vulnerabilities in appropriate situations, something that may not be graded as serious during a vulnerability check might become the cornerstone of a more devious attack.
The current threat environment is so serious that businesses cannot afford to overlook the value of combining these two complementary strategies.
Conclusion
Vulnerability assessment and penetration testing can be difficult to understand for people who have never done it before, but now you know the difference! While both are important, it’s clear that organizations should focus on having a full spectrum of cybersecurity measures in place rather than just information security.
Have any questions about either type of test discussed here today—let us know below! If this post was helpful, subscribe to The QA Lead newsletter for more definitions, how-to guides, and industry tips.
List of Related of Tools:
- VULNERABILITY SCANNING SOFTWARE QAS ARE USING
- PERFORMANCE TESTING SOFTWARE FOR QA TEAMS
- WEB APPLICATION PENETRATION TESTING TOOLS
- PENETRATION TESTING TOOLS FOR QA
Also Worth Checking Out: